Common Network Security Components Used to Mitigate Threats
When considering the deployment of a network or the modification of an existing network, evaluate each network component to determine its security strengths and weaknesses. This section discusses many common network security components.
Hosts and Nodes
A node is any device on the network. This includes client computers, servers, switches, routers, firewalls, and anything with a network interface that has a MAC address. A Media Access Control (MAC) address is the 48-bit physical hardware address of a network interface card (NIC) assigned by the manufacturer. A node is a component that can be communicated with, rather than only through or across. For example, network cables and patch panels are not nodes, but a printer is a node.
A host is a form of node that has a logical address assigned to it, usually an Internet Protocol (IP) address. This address typically implies that the node operates at or above the Network Layer. The Network Layer includes clients, servers, firewalls, proxies, and even routers. The Network Layer excludes switches, bridges, and other physical devices, such as repeaters and hubs. In most cases, a host either shares or accesses resources and services from other hosts.
In terms of network security, node and host security does vary. Nodes and hosts can both be harmed by physical attacks and denial of service (DoS) attacks. However, a host can also be harmed by malicious code or authentication attacks, and might even be remotely controlled by hackers. Node protection is mostly physical access control, along with basic network filtering against flooding.
Host security can be much more involved, because the host itself should be hardened and you will need to perform general network security. Hardening is the process of securing or locking down a host against threats and attacks. This can include removing unnecessary software, installing updates, and imposing secure configuration settings.
Firewalls
Not all traffic on your network is from an authorized source, so you shouldn’t allow it to enter or leave the network. Not all traffic is for an authorized purpose, so you should block it from reaching its destination. Not all traffic is within the boundaries of normal or acceptable network activity, so you should drop it before it causes compromises.
All of these protections are the job of a firewall. As its name implies, a firewall is a tool designed to stop damage, just as the firewall in an engine compartment protects the passengers in a vehicle from harm in an accident. A firewall is either a hardware device or a software product you deploy to enforce the access control policy on network communications. In other words, a firewall filters network traffic for harmful exploits, incursions, data, messages, or other events.
Firewalls are often positioned on the edge of a network or subnet. Firewalls protect networks against numerous threats from the Internet. Firewalls also protect the Internet from rogue users or applications on private networks. Firewalls protect the throughput or bandwidth of a private network so resources are available to authorized users. Without firewalls, most of your network’s capabilities would be consumed by worthless or malicious traffic from the Internet. Think of how a dam on a river works; without the dam, the river is prone to flooding and overflow. The dam prevents the flooding and damage.
Without firewalls, the security and stability of a network would depend mostly on the security of the nodes and hosts within the network. Based on the sordid security history of most host operating systems, having no firewall would not be a secure solution. Hardened hosts and nodes are important for network security, but these should not be the only components of reliable network security. Firewalls can be installed on client and server computers. These host software firewalls protect a single host from threats from the Internet, as well as threats from the network and other internal network components.
In any case, a firewall is usually configured to control traffic based on a deny-by-default/allow-by-exception stance. This means that nothing passes the firewall just because it exists on the network (or is attempting to reach the network). Instead, all traffic that reaches the firewall must meet a set of requirements to continue on its path.
As a network administrator or IT security officer, you choose which traffic is allowed to pass through the firewalls and which traffic is blocked. Additionally, you can also determine whether the filtering takes place on inbound traffic (known as ingress filtering), outbound traffic (called egress filtering), or both. Filtering inbound traffic is a normal function, as many threats exist outside of the network. Don’t forget that sensitive data and company secrets could be sent from a source inside the network to the outside world, which is why outbound traffic filtering is also necessary.
Firewalls are an essential component of both host and network security.
Virtual Private Networks
A virtual private network (VPN) is a mechanism to establish a remote access connection across an intermediary network, often over the Internet. VPNs allow for cheap, long-distance connections when established over the Internet, as both endpoints only need a local Internet link. The Internet itself serves as a “free” long-distance carrier.
A VPN uses tunneling or encapsulation protocols. Tunneling protocols encase the original network protocol so that it can traverse the intermediary network. In many cases, the tunneling protocol employs encryption so that the original data traverses the intermediary network securely.
You can use VPNs for remote access, remote control, or highly secured communications within an untrusted network.
Proxy Servers
A proxy server is a variation of a firewall. A proxy server filters traffic, but it also acts upon that traffic in a few specific ways. First, a proxy server acts as a middleman between the internal client and the external server. Or, in the case of reverse proxy, this relationship can be inverted with an internal server and an external host. Second, a proxy server will hide the identity of the original requester from the server through a process known as network address translation (NAT). Essentially, a proxy server stands as an intermediary in front of another server.
Another feature of a proxy server can be content filtering. This type of filtering focuses either on the address of the server (typically by domain name or IP address) or on keywords appearing in the transmitted content. You can employ this form of filtering to block employee access to Internet resources that are not relevant or beneficial to business tasks or that might have a direct impact on the business network. This could include malicious code, hacker tools, excessive bandwidth consumption (such as video streaming or P2P file exchange), and inappropriate or offensive websites or material.
Proxy servers can also provide caching services. Caching is a data storage mechanism that keeps a local copy of content that is fairly static in nature and that numerous internal clients have a pattern of requesting. Front pages of popular websites, like those of search engines, are commonly cached by a proxy server. When a user requests a page from the Internet that is stored in cache, the proxy server provides that page to the user from cache rather than pulling it again from the Internet site. This provides the user with faster performance and reduces the load on the Internet link.
This type of caching often results in all users experiencing faster Internet performance, even when the pages served to them are pulled from the Internet. Obviously, such caching must be tuned to prevent stale pages in the cache. Tuning is setting the time-out value on cached pages so each expires at a reasonable rate. All expired cached pages are replaced by fresh content from the original source server on the Internet.
Network Address Translation
Network address translation (NAT) converts internal addresses into external public addresses, and vice versa. The network performs this conversion on packets entering or leaving the network to mask and modify the internal client’s configuration. The primary purpose of NAT is to prevent internal IP and network configuration details from being discovered by external entities, such as hackers.
FIGURE 1-3 shows an example of a pathway from an internal client to an external server across a proxy or firewall using NAT. In this example, the external server is a web server operating on the default HTTP port 80. The web server is using IP address 208.40.235.38. The requesting internal client is using IP address 192.168.12.153. The client randomly selects a source port between 1,024 and 65,535 (such as 13,571). With these source details, the client generates the initial request packet. This is Step 1. This packet is sent over the network toward the external server, where it encounters the NAT service.
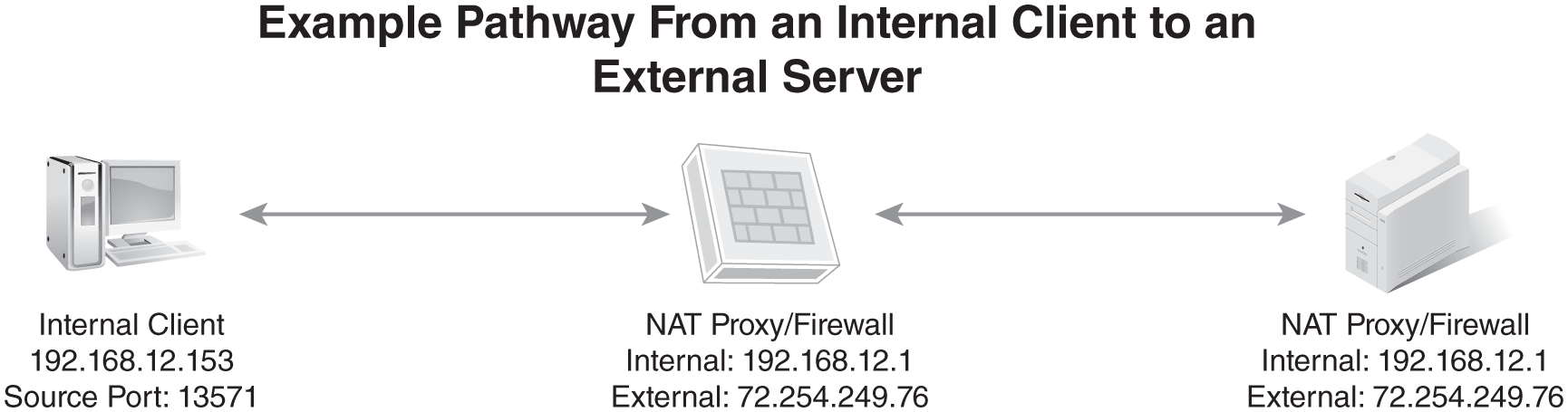
FIGURE 1-3 An example of how NAT functions.
Another purpose or use of NAT is to reduce the need for leasing a significant number of public IP addresses from an Internet service provider (ISP). Without NAT, you would need a unique public IP address for each individual system that would ever connect to the Internet. With NAT, you can lease a smaller set of public IP addresses to serve a larger number of internal users. In many small office/home office (SOHO) networks, all internal network devices can be translated to a single public address.
This consolidation is possible for two reasons. First, the shortage of IPv4 addresses required some networks to consolidate addresses. Second, NAT reserves a specific public address for use by a single internal client only if Static NAT is utilized. Instead, NAT randomly assigns an available public address to each subsequent internal client request. Once the client’s communication session is over, the public address returns to the pool of available addresses for future communications.
Additionally, NAT usually does not employ IP-to-IP address translation, instead using the more granular option known as port address translation (PAT). With PAT, both the port and the IP address of the client are converted into a random external port and public IP address. This allows for multiple simultaneous communications to take place over a single IP address. This process, in turn, allows you to support a greater number of communications from a single client or multiple clients on an even smaller number of leased public IP addresses.
NAT enables the use of private IP addresses while still supporting Internet communications. These addresses are known as RFC 1918 addresses, from the technical specification detailing the protocol. The ranges are as follows:
- Class A—10.0.0.0–10.255.255.255/8 (1 Class A network)
- Class B—172.16.0.0–172.31.255.255/12 (16 Class B networks)
- Class C—192.168.0.0–192.168.255.255/16 (256 Class C networks)
RFC 1918 addresses are for use only in private networks. They are, by definition, unrouteable address spaces. Internet routers drop any packet using one of these addresses. Without NAT, a network using these private IP addresses would be unable to communicate with the Internet. By using RFC 1918 addresses, networks create another barrier against Internet-based attacks and do not need to pay for leasing of internal addresses.
As mentioned, NAT is one of the technologies that has allowed the extended use of IPv4, even after the depletion of available public IP addresses. Now that the transition to IPv6 is underway, NAT is serving a new purpose in translating between addressing schemes, or IPv4-to-IPv6 translation. Many firewall and proxy devices may include IPv6 translation services. This feature is a worthwhile option that you might want to include on a feature list when researching a firewall purchase or deployment.
Technical TIP
An interesting wrinkle on NAT and PAT is that most devices and software products that support PAT actually state in the documentation and in the configuration interfaces that NAT is also supported. It seems that NAT has been redefined to include the functionality of port address translation, even though an official acronym for that specific additional technology already exists. Most certification exams combine the two as well. Questions might use the NAT acronym but actually refer to port address translation (PAT).
The Domain Name System
The Domain Name System (DNS) is an essential element of both Internet and private network resource access. Users do not keep track of the IP address of servers. So, to access a file server on, say, a social networking site, users rely upon DNS to resolve the fully qualified domain names (FQDNs) into the associated IP address. DNS is similar to the address book (contacts) in your smartphone. Instead of remembering people’s phone numbers, you just look up their names; the address book (contacts) associates each person’s name with the number to dial.
Most users don’t even realize that networks rely upon IP addresses to direct traffic toward a destination rather than the domain name that they typed into the address field of client software. However, without this essential but often transparent service, the Internet would function very differently. In such a case, users would need to maintain a list of IP addresses of sites they wanted to visit or always go to a search engine for a site’s IP address.
DNS is the foundation of most directory services in use today, such as Active Directory and LDAP (see the following section). Active Directory is found in Windows operating systems. Thus, DNS is essential for internal networks, as much as it is for the external Internet.
DNS is vulnerable in several ways. First, DNS is a nonauthentication-query-based system. This allows a false or “spoofed” response sent as a DNS query to appear valid. Second, anyone can request transfers of the DNS mapping data (called the zone file), including external entities if TCP port 53 allows inbound access. Third, DNS uses a plaintext communication allowing for eavesdropping, interception, and modification.
You can address some of the faults of DNS with local static DNS mapping in the HOSTS file, filtering DNS on network boundaries, and using Internet Protocol Security (IPSec) for all communications between all hosts. (A HOSTS file is a static file on every IP-enabled host where FQDN-to-IP address resolutions can be hard-coded.) However, these are defenses for DNS, as DNS does not protect the network; rather, it is an essential service that needs protection.
 NOTE
NOTE
A few Internet index sites still exist, but they are not as exhaustive (or current) as most search engines. Think of the difference between the Yellow Pages dropped on your front porch each year versus dialing 411: One is more current and relevant than the other.
Directory Services
A directory service is a network index. It helps users locate resources within a private network. A directory service is responsible for keeping track of which servers (sometimes acting as clients) are online and the resources these hosts share with the network. A directory service operates much like a telephone book does for phone numbers and addresses.
Prior to directory services, less efficient methods of tracking or locating available resources were in service. These included local static or dynamic lists, which networks maintained using broadcast announcements. Only workgroup networks still use these outdated methods.
A directory service is another essential piece of modern networks that does not provide obvious security services. This means directory services need the protection provided by other security services and devices. You should limit access to directory services to authorized and authenticated clients and users of the local network. Your network should ignore all external requests for information, with the exception of valid (organization identified) remote access or VPN links. If possible, you should deploy IPSec so that you protect every internal network communication.
Intrusion Detection Systems and Intrusion Prevention Systems
Intrusion detection systems (IDSs) and intrusion prevention systems (IPSs) have become popular topics of discussion in the IT and security fields. The concept of an IDS is a system that watches internal hosts or networks for symptoms of compromise or intrusion. Effectively, an IDS is a form of burglar alarm that detects when an attack is occurring within the network.
An IDS often serves as a complementary mechanism to firewalls. Once an IDS detects an intruder, it can send commands or requests to the firewall to break a connection, block an IP address, or block a port or protocol. You must configure the firewall to receive these commands and authorize the IDS to send them. Not all IDSs and firewalls are compatible in this manner.
Eventually, the IPS concept appeared, which strives to detect the attempt to attack or intrude to prevent the attack. Once an attempt is detected, the IPS can respond to prevent the success of the attempt rather than waiting until after a successful breach to respond. IPSs do not replace IDSs. Instead, these are often used as a first or initial layer of proactive defense, relegating the IDS to a detection posture against those events that the IPS misses or that internal personnel perform.
IDSs and IPSs are important components of a complete network security solution. However, these are not without fault. IDSs and IPSs can create a false sense of security under certain conditions. Two commonly discussed conditions include unknown zero-day attacks and false positives.
When unknown zero-day attacks threaten the network, an IDS or IPS might not have the mechanism to detect it. Thus, the lack of an alarm could cause administrators to assume that no attacks are occurring. In most cases, the lack of an alarm does mean that nothing malicious is happening. So, this assumption is not completely unwarranted. But if an IDS never triggers an alarm, then you should suspect a poor detection system rather than the complete lack of compromise attempts or attacks. This is a false negative, as no threat was detected even though a threat was present.
False positives present the same issue for the opposite reason, namely too many alarms from benign (or valid) occurrences. After the first initial alarms turn out to be triggered by benign activity, the urgency of responding to alarms diminishes. After additional false positives, an administrator might put off investigating alarms. Eventually, you ignore the alarms altogether. Once this situation arises, you may even treat alarms for malicious events as false positives, once again establishing a false sense of security. But the administrator should instead “tune” the device to reduce the number of false positives on the network. A situation where false positives exist is worse than a false negative because it is easy to be lulled into compliance, believing there is no issue on the network because there is no warning present.
Network Access Control
Network access control (NAC) limits access or admission to the network based on the security compliance of a host. NAC is essentially an enforcement tool to make sure that all hosts connecting to the network have current and compliant security components. With NAC, you can block or restrict access if a computer does not have the latest antivirus update, a certain security patch, or a host firewall, or if the device is unauthorized.
NAC usually operates by placing an agent on each authorized host. When the host connects to the network, the agent contacts the master control program to find current host requirements. If the host fails to meet those requirements, then the NAC prevents the host from accessing the network. A noncompliant host may be granted access only to remediation servers. These remediation servers can provide the patches and updates needed to bring the host into full compliance.
Effectively, NAC is a method to enforce host-hardening rules through an automated systemwide mechanism. With NAC, systems must be in compliance, or attempts to access general network resources are blocked. Access is allowed to the network only after noncompliant systems are updated.
