What Is Network Security?
Network security is the control of unwanted intrusion into, use of, or damage to communications on a computer network. This includes monitoring for abuses, looking for protocol errors, blocking nonapproved transmissions, and responding to problems promptly and accurately. Network security is also about supporting essential communication necessary to the organization’s mission and goals, avoiding the unapproved use of resources, and ensuring the integrity of the information traversing the network.
Network security includes elements that prevent unauthorized access and actions while supporting desirable activities, such as accessing customer records or managing inventory. This is hard to do efficiently, cost effectively, and transparently. Efficient network security provides quick and easy access to resources for users. Cost-effective network security controls user access to resources and services, as long as the risks justify the control costs. Transparent network security supports the mission and goals of the organization through enforcement of the organization’s network security policies, without unnecessary steps or delay of valid users performing legitimate tasks.
Computer networking technology is changing and improving faster today than ever before. Wireless connectivity is now a realistic option for most organizations and individuals. Malicious hackers are becoming more adept at using every means available to steal identities, intellectual property, and money.
Today, many organizations spend more time, money, and effort protecting their assets than they do during the initial installation of the network. Threats, both internal and external, can cause a catastrophic system failure or compromise. Such security breaches can even result in a company going out of business. Without network security, many businesses and individuals would not be able to work productively.
Network security must support workers in their jobs, while protecting against compromise, maintaining high performance, and keeping costs to a minimum. This can be incredibly challenging to achieve; but, with proper planning and execution, many organizations have successfully accomplished this task.
Network security begins with trust.
What Is Trust?
Trust is confidence in your expectation that others will act in your best interest. With computers and networks, trust is the confidence that other users will act in accordance with your organization’s security rules and corporate mission and vision. You trust that they will not attempt to violate the stability, privacy, or integrity of the network and its resources. Trust is the belief that others are trustworthy.
Unfortunately, sometimes people violate your trust. They may do this by accident, oversight, or ignorance that the expectation even existed. In other situations, they violate trust deliberately. Because these people can be either internal personnel or external hackers, it’s difficult to know whom to trust.
So, how can you answer the question, “Who is trustworthy?” You begin by realizing that trust is based on past experiences and behaviors. Trust is usually possible between people who already know each other. It’s neither easy nor desirable to trust strangers. However, once you’ve defined a set of rules and everyone agrees to abide by those rules, you have established conditional trust. Over time, as people demonstrate that they are willing to abide by the rules and meet the expectations of conduct, you can consider them trustworthy.
Trust can also come from using a third-party method. If a trustworthy third party knows each of the entities and states that both are trustworthy, then you can extend conditional trust to each of the entities. Over time, someone’s behavior shows whether or not the initial conditional trust was merited.
Ultimately, network security is based on trust. Organizations assume that their employees, as well as all of the computers and network devices, are trustworthy. But not all trust is necessarily the same. You can (and probably should) operate with different levels or layers of trust. Those with a higher level of trust can be assigned greater permissions and privileges. In terms of networking, permission is the authorization to access an asset, and privilege is the ability granted on the network. If someone or something violates your trust, you remove the violator’s access to the secure environment. For example, organizations terminate an untrustworthy employee or replace a defective operating system.
A common example of a third-party trust system is the use of digital certificates that a public certificate authority issues. As shown in FIGURE 1-1, a user communicates with a web e-commerce server. The user does not initially know whether a web server is what it claims to be or if someone is “spoofing” its identity. Once the user examines the digital certificate issued to the web server from a certificate authority, the user can then trust that the identity of the website is valid. This occurs because both the user and the website have a common, trustworthy third party that each knows.
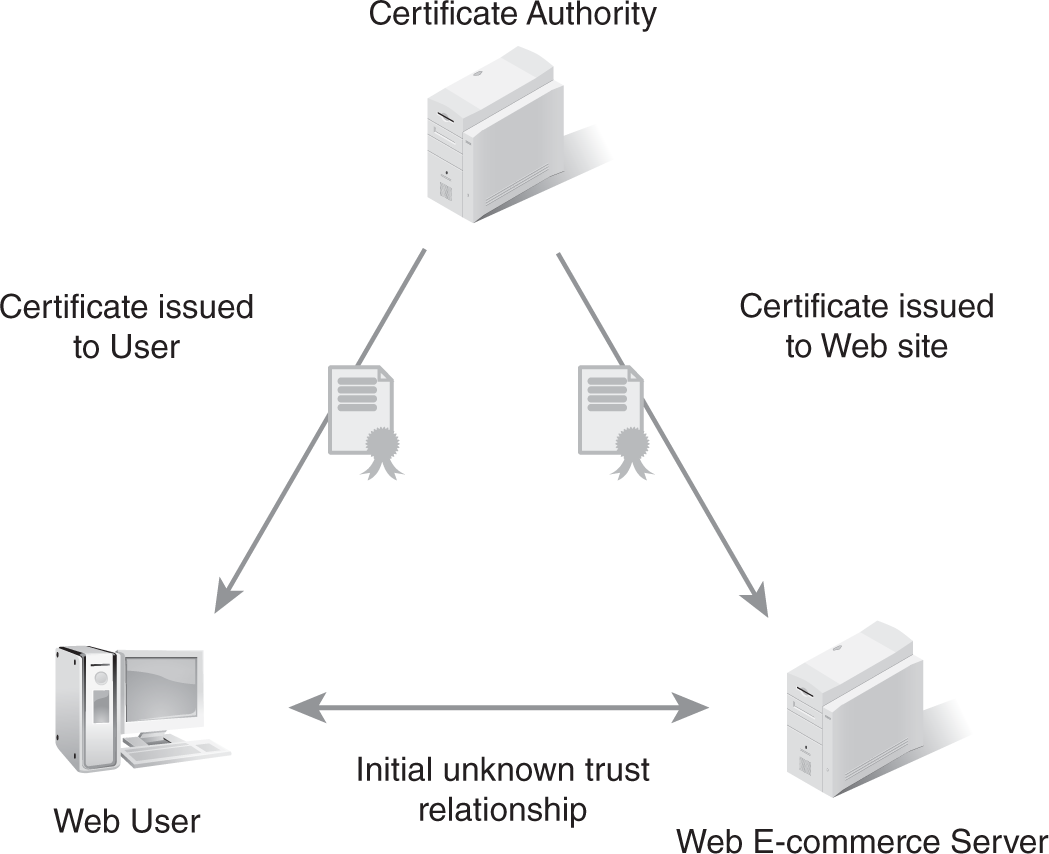
FIGURE 1-1 An example of a third-party trust system.
Who—or What—Is Trustworthy?
Determining who or what is trustworthy is an ongoing activity of every organization, in both global corporations and a family’s home network. In both cases, you offer trust to others on a conditional basis. This conditional trust changes over time, based on adherence to or violation of desired and prescribed behaviors.
If a program causes problems, it loses your trust and you remove it from the system. Similarly, if a user violates security, that person loses your trust and you might revoke access privileges. When a worker abides by the rules, your trust grows and privileges may increase if necessitated by additional job responsibilities or need. In the same way, when an Internet site does not cause harm, you deem it trustworthy and allow access to that site.
To review, trust is subjective, tentative, and changes over time. You can offer trust based on the reputation of a third party. You withhold trust when others violate the rules. Trust stems from actions in the past and can grow based on future behaviors.
In network security, trust is complex. Extending trust to employees without proper background investigation can be devastating. A network is only as secure as its weakest link. You need to scrutinize every aspect of a network, including software, hardware, configuration, communication patterns, content, and the users, to maintain network security. Otherwise, you will not be able to accomplish the security objectives of your organization.
What Are Security Objectives?
Security objectives are goals an organization strives to achieve through its security efforts. Typically, organizations recognize three primary security objectives:
- Confidentiality/privacy
- Integrity/nonrepudiation
- Availability/uptime
Confidentiality is the protection against unauthorized access, while providing authorized users access to resources without obstruction. Confidentiality ensures that data is not intentionally or unintentionally disclosed to anyone without a valid need to know. A job description defines the person’s need to know. If a task does not require access to a specific resource, then that person does not have a need to access that resource.
Integrity is the protection against unauthorized changes, while allowing for authorized changes performed by authorized users. Integrity ensures that data remains consistent, both internally and externally. Consistent data does not change over time and remains in sync with the real world. Integrity also protects against accidents and hacker modification by malicious code, or software written with malicious intent.
Availability is the protection against downtime, loss of data, and blocked access, while providing consistent uptime, protecting data, and supporting authorized access to resources. Availability ensures that users can get their work done in a timely manner with access to the proper resources. Availability, for example, ensures that web resources are accessible, so sales are not lost.
Authentication is the proof or verification of a user’s identity before granting access to a secured area. This can occur on a network or in the physical, real world. While the most common form of authentication is a password, passwords can be accidentally shared or stolen, especially if written down. Multifactor authentication is the method most network administrators prefer for secure logon, as it requires multiple proofs of one’s identity.
Authorization is controlling what users are allowed and not allowed to do. Authorization is dictated by the organization’s security structure, which may focus on discretionary access control (DAC), mandatory access control (MAC), or role-based access control (RBAC). Authorization restricts access based on need to know and users’ job descriptions. Authorization is also known as access control.
Nonrepudiation is the security principle that prevents a user from being able to deny having performed an action. For example, nonrepudiation prevents a sender from denying having sent a message. Public-key cryptography commonly provides nonrepudiation services.
Privacy protects the confidentiality, integrity, and availability of personally identifiable or sensitive data. Private data can include financial records or medical information. Privacy prevents the unauthorized watching and monitoring of users and employees.
Maintaining and protecting these security objectives can be a challenge. As with most difficult tasks, breaking security down into simpler or smaller components will help you to understand and ultimately accomplish this objective. To support security objectives, you need to know exactly what you are trying to protect.
