Why Do You Need a Firewall?
High-speed Internet connectivity has become ubiquitous. Most computer users now have high-speed access at home, at work, and even on the go through mobile devices. Often, these broadband connections are always-on connections. This means computers and networks are online all the time—and exposed to attacks. A drawbridge is easy to cross if it is always down. When a system is always connected, it can be the focus of a concerted attempt to discover its vulnerabilities and breach its security.
How likely is it that a computer will be discovered and attacked over the Internet? It is almost guaranteed. Most systems are detected, scanned, and probed within minutes of obtaining a public IP address. It is technical suicide to connect your system to the Internet before installing a firewall, as well as installing the latest vendor patches for the hardware, operating system (OS), and installed applications.
Does this mean that there are armies of hackers just waiting to find new targets to attack? Unfortunately, yes—but not, however, in the way you might think. Malicious programs, such as agents, bots, and zombies, perform most of the scanning and attacking automatically. Groups of malicious code, known as botnets, scour the Internet for new victims constantly.
With a firewall protecting your system from the Internet, hacker scans will be nearly worthless. Responses to probing packets will be filtered. An outsider will learn little about your infrastructure. This, in turn, means they will discover fewer vulnerabilities, thus wage fewer attacks. Even then, those attacks will be more likely to fail.
Firewalls are not used only for Internet protection. Do not forget that significant levels of threat exist internally. Firewalls stand guard against network segments inside your private network (FIGURE 5-3). Think of a firewall as a tool to prevent abuse or misuse of LAN resources. Each major department, subnet, or other relevant distinction within an organization should have firewall protection. This will ensure that accidental compromises, as well as intentional abuses, are minimized internally. All networks protect against both internal threats and external ones.
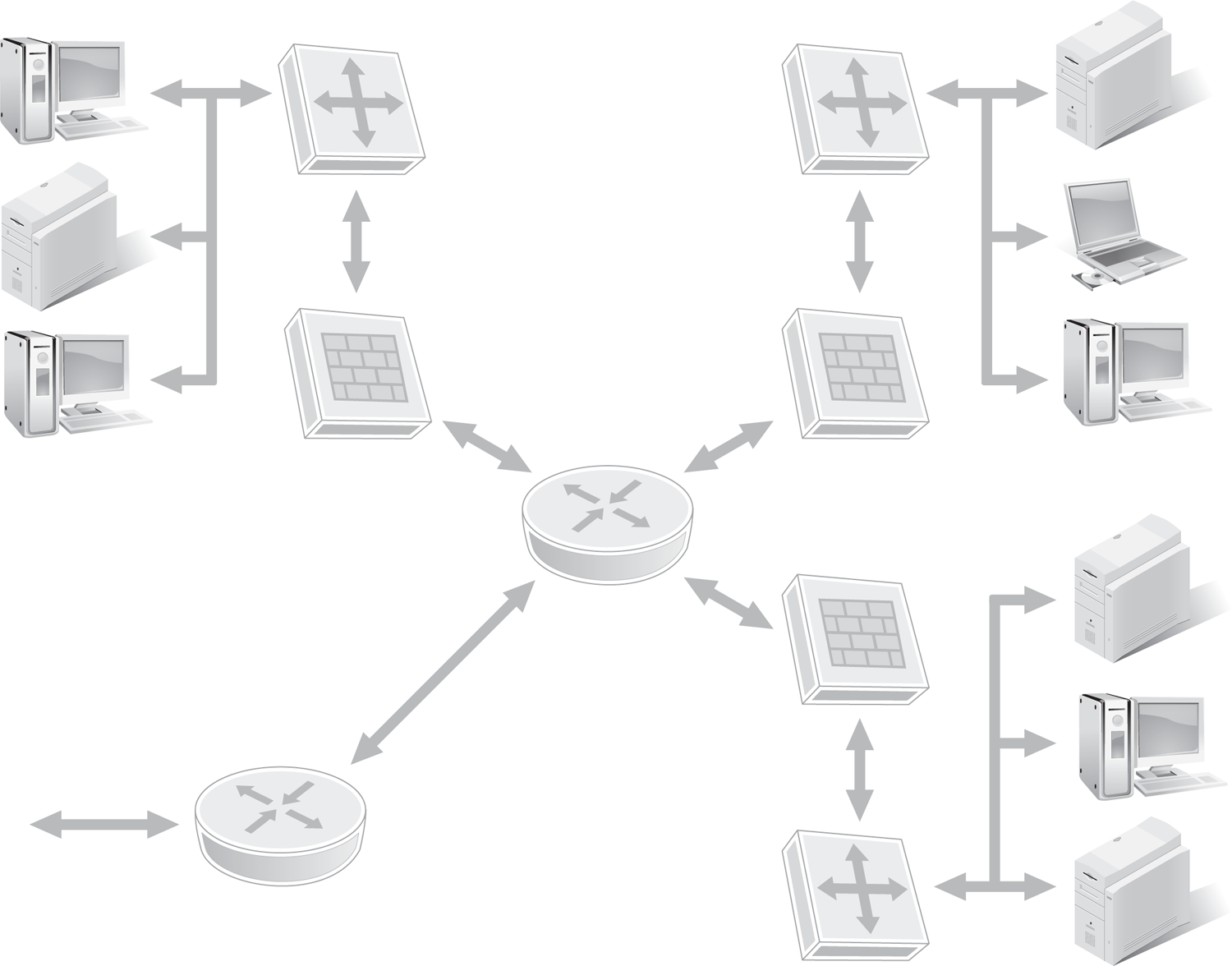
FIGURE 5-3 An example of a private network using firewalls to separate subnets securely.
Although a firewall has its origins in routing, you still want to use a dedicated router for routing and a dedicated firewall for filtering. In many cases, the combination or multifunction devices offer lots of features, but not necessarily best-of-breed performance and efficiency. These may be money-savers for small networks, but they are often cause for expense for larger networks. If a device fails to perform at commercial levels when necessary, the repercussions can cost more in lost revenue and productivity than deploying the proper safeguards in the first place.
Host firewalls protect a host and also protect a network from the host. A host firewall’s job is to filter traffic entering or leaving a single computer system. Attacks and malicious traffic can come from the Internet or from the local network. A host firewall can protect the host against such threats. However, the host itself could be compromised by malicious code or be controlled by a malicious user. In this situation, the host firewall protects the network from the threats coming from the host.
Another way of looking at this is that a host firewall also protects the network from a user in general. A user is the riskiest element in a network infrastructure. Even if every other component—hardware or software—does what it was programmed and configured to do, a user can decide to violate security. Thus, the free will of human users is one of the biggest risks to every computing environment.
Users can be ignorant, make mistakes, be tricked by a Trojan horse, be the target of social engineering attacks, or deliberately perform malicious actions. The security of a host system, including general system hardening, anti-malware scanning, Internet client restrictions, blocking of nonapproved software, and a host firewall, are all designed to protect the network from the risk of human users.
