Individual and SOHO Firewall Options
Firewall options for the individual or for those running a small office range from native OS firewalls to special-purpose devices. Most individuals and SOHO users are concerned about security but do not want to spend more than necessary. Obtaining a reasonable level of security for most home or small office environments is actually quite easy and cost effective.
 NOTE
NOTE
Installing a handful of security tools doesn’t mean that you can throw caution to the wind and randomly explore the entire Internet safely. Instead, by using simple security tools, along with common sense, most threats are either blocked or avoided. Potential exceptions can always affect this rule, of course, such as when a trusted site is compromised and your next visit results in the transfer of malware to your hard drive.
First, an understanding of the common threats facing such an environment suggests that firewall options can be simple and inexpensive. Generally, Internet threats fall into two main categories: passive and active. Passive threats are those you must seek out to be harmed. For example, you have to visit a website to be harmed by malicious code embedded in that site. Likewise, downloading infected content occurs only when you elect to click on a download link. Users can avoid most passive threats by making good and safe choices as to where to go and what to do on the Internet.
To address passive threats, modern web browsers include pop-up blockers, cookie filters (FIGURE 5-8), and malicious site managers to limit exposure. The use of antivirus scanning, an anti-spyware scanner, and anti-spam filters addresses other common threats. Adding a firewall to your security stance protects against most of the passive threats on the Internet that might be casually triggered.
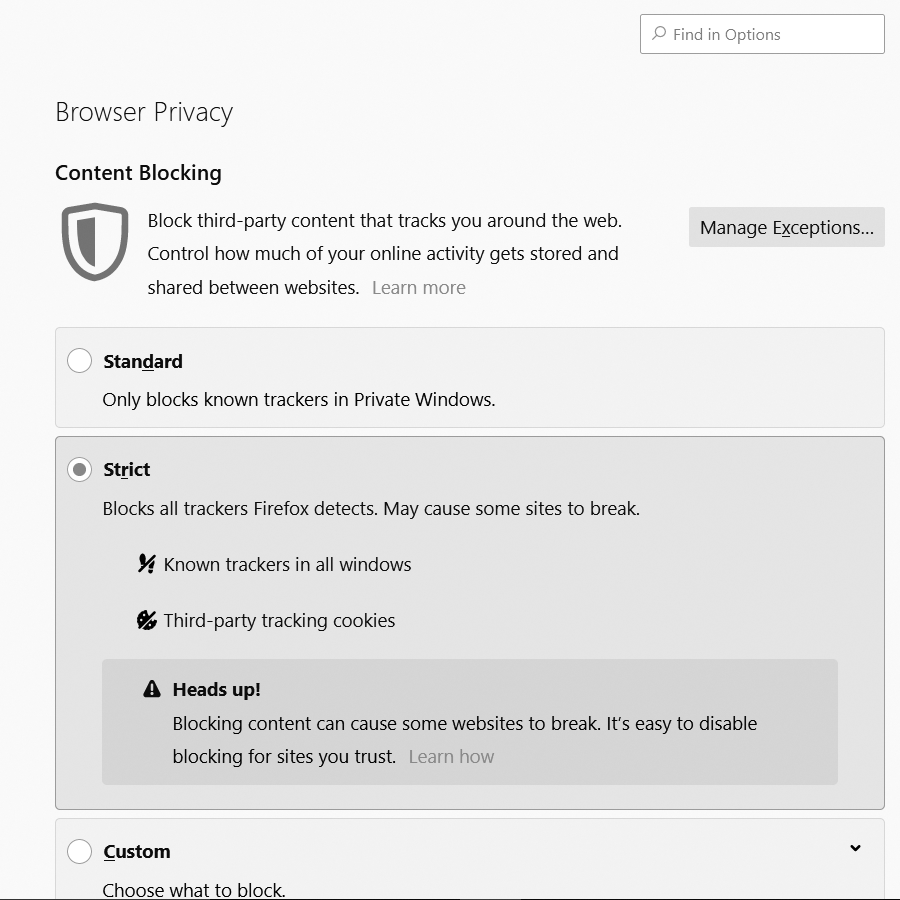
FIGURE 5-8 Privacy section of Firefox’s Options dialog box. Note the cookie settings.
The other category of Internet threat is active. An active threat is one that takes some type of initiative to seek out a target to compromise. This can be a hacker, an intruder, or an automated worm. In any case, an active threat seeks out vulnerable targets. If you do not have reasonable security deployed and an active threat discovers your system, you might be at risk for a compromise.
Fortunately, most individuals and SOHO environments are not significant or primary targets of most hacker activity. There just is not enough value or benefit in spending the time and effort to compromise a moderately secured single computer or small network. If your business is getting lots of traffic and orders, or you happen to be hosting hundreds of systems, then you naturally become a more valuable target to hackers.
In most circumstances, the average home user and most small offices (such as those operating a dozen or fewer computers in a network) can obtain reasonable security protection from very simple and inexpensive firewall options.
The first firewall option to consider is any native firewall of the operating system. Most operating systems include a default or native firewall. If yours does, investigate its features and options before automatically tossing it aside. Many of the firewalls found in the latest releases of operating systems are as good as or better than most commercially available third-party host software firewall options.
One of the best-known examples of a native operating system firewall is Windows Firewall. Windows Firewall made its debut in the Windows OS as part of Service Pack 2 for Windows XP. Since its initial release, Windows Firewall appeared as a standard native feature in Windows Vista, Windows 7, and Windows 10. The feature set and uses of Windows Firewall are discussed later in this chapter.
 NOTE
NOTE
Microsoft changed the name of Windows Firewall in Windows 10 to “Windows Defender Firewall”; however, you will see it referred to as “Windows Firewall” in certain instances.
Other operating systems may or may not have a firewall as well recognized as Windows Firewall, but you should still investigate the standard options and feature set provided natively before seeking out alternatives. After all, you would never custom turbocharge a brand-new car until you had driven it and road tested its standard features.
Most Linux distributions do not automatically come with a native software firewall. When Linux does provide a native firewall, it is not likely to be enabled or configured by default. Due to the wide range of variations in Linux distributions, Linux provides a range of firewalls. Linux firewalls include older products, such as ipchains and iptables, as well as newer options such as PF, Netfilter, and Vyatta.
In addition to the free or native OS firewall options, individuals and SOHOs can use firewalls hosted by Internet service provider (ISP) connection devices, routers, or WAPs. An ISP connection device is any hardware connecting a local network—or even a single computer—to a telco’s carrier network to access the Internet. Most ISP connection devices, including cable modems, DSL modems, satellite modems, routers, and wireless modems, include firewall features. A firewall feature may or may not represent a fully functional firewall. Some are basic filtering tools that block IP addresses, ports, or protocols using a simple blacklist technique.
An ISP connection device may offer wireless connectivity. If the provider does not offer a wireless option or requires you to pay extra for wireless via their equipment, you should consider deploying your own WAP. Most WAPs for consumers and SOHO environments cost under $100 and offer firewall services, as well as wireless connectivity.
The use of native host OS firewalls and a hardware firewall provided by an ISP connection device or WAP is usually more than sufficient filtering security for a home user or a small office network. However, if you want to explore other options or you have a larger, riskier, or more sensitive environment, consider the other firewall alternatives.
Managing the Firewall on an ISP Connection Device
Most ISP connection devices use a web interface. To initiate access to the management interface, open a web browser and enter the IP address of the device where you would typically enter a URL. In most cases, the device’s IP address is the default gateway address, DHCP address, or possibly DNS address of the client’s interface directly connected to a physical port on the device.
Technical TIP
If the ISP connection device provides firewall services, obtain a copy of the most current manufacturer’s user manual for the device. This documentation will provide the best initial information on accessing and configuring the device’s firewall and is usually available online at the manufacturer’s website.
Attempting to open the configuration interface is likely to result in a prompt for authentication credentials. The vendor’s user manual should indicate the device defaults for username and password—which is why it is essential that you change these on your devices—but be sure to record the account information and keep it someplace safe. If not, search the Internet using keywords such as “default password” along with the device name, make, and model. If that fails, try username “admin” with a password of “admin” or “password.” It is shocking how often these are correct. In Linux systems, it is common to use “root” as the username and “toor” as the password.
Your ISP has likely locked down access to the connection device. This is sometimes done as a precaution against the uninitiated, who might cause increased technical support hassles. If you discover that your ISP connection device is locked down, try calling your ISP and asking them to grant you access (often by their revealing the credentials to log into the device).
If they refuse to offer this information, then you have four choices:
- You can accept their refusal as “just how it is” and employ some other device as a hardware firewall.
- You can change ISPs or service providers to a carrier that will grant you access to configure the device.
- You can try to replace the carrier’s device with one that you own and fully control.
- You can seek out ISP and device-specific information on the Internet, which might include bypass or hacking details.
 NOTE
NOTE
Cable providers are generally less likely to allow you access into their connection device, while most DSL providers seem willing to grant at least partial access.
However, be very cautious when choosing this last route; it is often unproductive, probably a violation of the ISP terms of service, unethical, and may even be illegal.
If you are unable to find a legitimate path to accessing the configuration interface of your ISP connection device, hacking the device should be your last and final option. Hacking an ISP-provided device will void your contract and could make you liable for the cost of the device, plus fines and possible legal action. A more ethical solution would be to replace the device with one you own and control, or switch ISPs altogether.
 NOTE
NOTE
Be careful about searching for websites that offer information on how to hack or bypass ISP equipment. Often the sites are booby-trapped with malware to trick the unsuspecting visitor. You may be able to download the instructions, but often it is a Trojan file, which includes malware to infect your system. In addition, some ISP equipment may be leased—not sold—and attempting to access internal features may violate the contract, if not the law.
If all else fails, add your own firewall between the ISP connection device and your first networked system. With this configuration, you are still gaining the benefit of an in-line firewall without violating any contracts or flirting with legal troubles. In most cases, you’ll want to supplement or disable an ISP connection device’s firewall anyway. Thus, if your ISP blocks access to it, just design your security as if the device offered no firewall protection.
Converting a Home Router into a Firewall
Many home routers have sufficiently robust features that you can configure these to function as firewalls. To ensure ease of use (and minimize product returns), these devices are usually shipped with all security features turned off. Because “plug and play” results in immediate connectivity, many users never go back to configure their equipment for security. Thus, hackers and malware are often able to intrude easily into home networks. You can prevent that by understanding what is available in this class of products.
To access a home router, type the IP address of your gateway into your browser. To determine the IP address on a Windows machine, choose Start > Run, type Command, and at the C:> prompt, type ipconfig. Most routers ship with a default address of 192.168.1.1. If you remember, 192.168.X.X is a nonroutable range of IP addresses, which means that traffic inside that address range will not be shared with addresses outside that range. On a Linux system it is a similar process, except the command is ifconfig on a wired system and iwconfig on a wireless Linux device.
Once logged in, consider changing a number of settings (FIGURE 5-9). First, if the router is a wireless device, change the service set identifier (SSID) from the default setting. You do not want to be one of eight access points named “ASUS” in your neighborhood. Why is this important? Most PCs will grab the strongest wireless signal from a known SSID. If you have standard SSIDs—such as ASUS—in your wireless access table, you may find yourself on a neighbor’s (or hacker’s) system someday without realizing it. Another good idea is to change the default IP address range to something other than 192.168.1.X. This creates a custom range for your own network. If you hard-code your internal network range to something like 10.20.30.X, you are less likely to stumble into that situation.
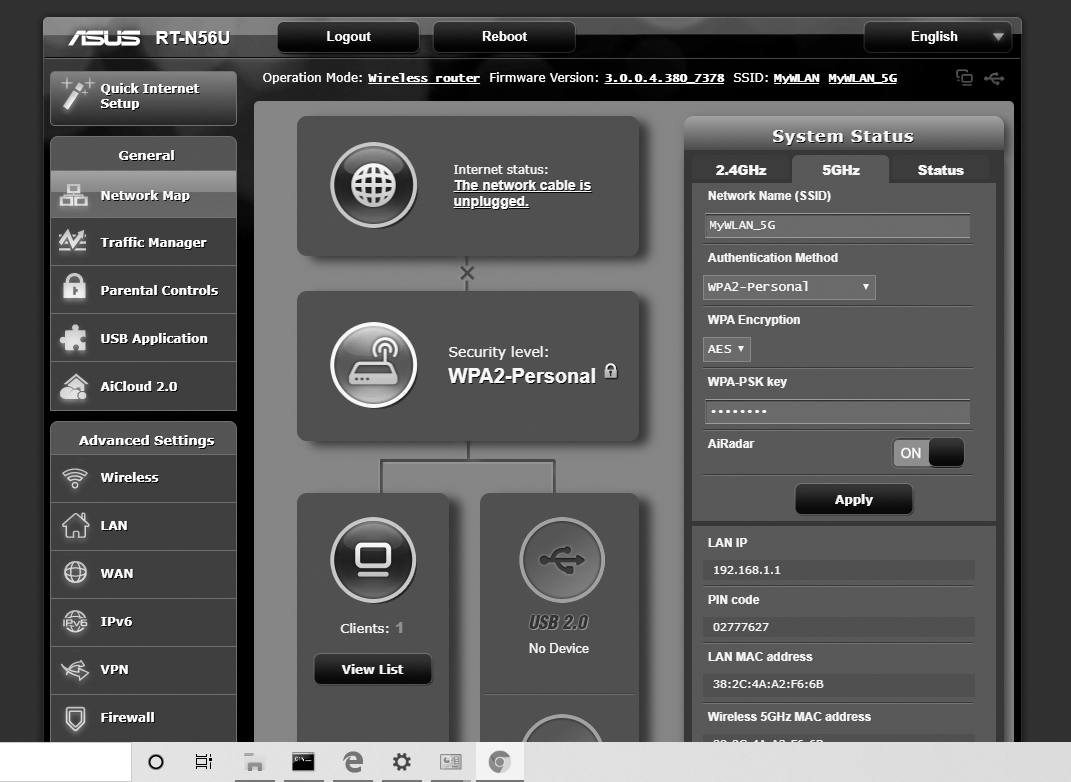
FIGURE 5-9 The initial configuration screen on an ASUS wireless router.
Courtesy of Asus.
Most routers enable Dynamic Host Configuration Protocol (DHCP) by default. You could lock down your network by either hard-coding IP addresses into each authorized machine (and turning off DHCP) or setting a strict upper limit on the number of devices permitted to have DHCP leases (most default settings are 100). If you have five devices, limit the number of connections to five. (Do not forget about the Xbox 360 or PS3—these devices need IP addresses too.)
 NOTE
NOTE
Do not forget to change the default administrator password of your device.
For firewall settings, most routers will have a configuration page to block services or control port access. Determine which ports you need to access the Internet, and then block all of the rest. Note that this setting restricts outbound traffic. So, why block it if it originates from within? Malware, zombies, bots, and other hostile applications usually have to connect to the outside to do any damage or steal your property. If you accidentally download dangerous malware onto your laptop at your favorite coffee bar, and then connect to your home or office network behind the firewall, that malware may have access to all of your peer systems. However, if you are blocking all nonessential outbound traffic, then most malware will not be able to exfiltrate your sensitive information or ask its remote server for instructions on what to do next to your system. Only those applications that use a common port (like port 80) will be able to get through.
Which outbound ports should you block? First, consult your policy, or determine what programs you are using. For the most part, you’ll want to allow the following outbound ports to be open at all times:
- Port 25—SMTP (outbound mail)
- Port 53—DNS (name resolution)
- Port 80—HTTP (Internet access)
- Port 110—POP (initiate request for inbound mail)
- Port 443—HTTPS (secure Internet)
- Ports 465 and 995—SMTP and POP (if using Gmail or other email packages)
- Ports 1024–1035—DCOM ports for downloading files (increase number of ports based on number of systems protected; 10 is usually sufficient for a home network)
Beyond port 1035, you may not need to allow outbound traffic, unless you are using cPanel to access an externally hosted website on port 2083, or port 11371 if you are looking up PGP keys. By blocking all other high ports, you will also quickly hear from coworkers or family members who may have been using some of these ports, which are dedicated to specialty software or gaming. At home, you might want to allow (or set time limits); at work, you probably want to block these ports, as gaming is usually not an acceptable use of company resources.
In general, you should not accept any connections that originate from outside your firewall. Your policy may permit exceptions, such as remote access tools, so be careful about blocking everything. Some home firewalls do not provide a direct way to block specific incoming ports, but most allow you to do port forwarding. A clever way to use this to thwart external attacks is to forward to a nonexistent port. So, for example, if your local network range includes from 10.20.30.40 to 10.20.30.49, you might forward incoming connection requests to port 10.20.30.99—where no device is listening. Ports you might consider forwarding are:
- Ports 20 and 21—FTP-data and FTP. Prevent external connections from downloading your files. If your business requires file transfers, safer alternatives are SFTP (Port 22) and FTPS (Port 990).
- Port 23—Telnet. Prevent external connections from insecurely logging into your internal systems.
- Port 53—DNS. Prevent external entities from poisoning your DNS cache.
- Port 80—HTTP (unless you are running a web server from behind your firewall, which is a bad idea).
- Ports 81 and 82—Often used as “overflow” for port 80. No valid use, so block these.
- Ports 137, 138, and 139—NetBIOS. Often exploited by malware, this provides access into Windows systems.
- Port 443—HTTPS (unless you are running a secure web server from behind your firewall, which is still a bad idea).
- Port 445—NetBIOS for Windows 2000 and later.
- Port 3074—Xbox game port. Do not allow strangers to connect to your Xbox while you’re away. Remember—it “lives” on your internal network.
An excellent way to test your configuration is to go to Steve Gibson’s http://www.grc.com website and run his free ShieldsUP! port scanning tool (FIGURE 5-10). Although the website has an admittedly outdated appearance (at the time of this writing), the tool is legitimate and can be used to scan ports and services, such as Universal Plug and Play (UPnP), often targeted by malicious actors. Most systems end up scoring poorly. If you can achieve 100 percent stealth, you’ve done a great job.

FIGURE 5-10 ShieldsUP! port scan result confirming a well-configured set of home router firewall rules.
