- 1.
Expansion of key lookup tables
- 2.
Implementation of user searching and filtering of scan results
- 3.
Headless communication with remotely deployed Pi sensors
- 4.
Correlation of results from a swarm of Pi sensors
Expansion of Lookup Tables
The Pi Sensor utilizes several key lookup tables that have been compiled for open source websites. They include port, manufacturer, and country lookups.
Port Lookups
The port lookup table is gathered from the IANA at www.iana.org . IANA provides registration services for port numbers designed for a specific purpose. However, many of the port usage descriptions provide only general information regarding port usage. Additional details are necessary to better map port usage to specific IoT and ICS applications. This would allow for more accurate reporting, tracking, and usage of ports by IoT and ICS applications.
Manufacturer Lookup
Looking up manufactures by the OUI suffers from some of the same limitations of the port lookup. The OUI represents the first 24 bits of the MAC address emitted by devices. The OUI is managed by the IEEE. The specific OUI values are purchased from the IEEE and added to the registry. The issue is that the OUI represents the manufacturer but does not define the use or application of the value. For example, identification of which OUI numbers are associated with drones, entertainment devices, computers, home automation, industrial control, cybersecurity devices, and so on is not readily available. If more details and cross-referencing of OUI and a specific category were available, then the ability to track behaviors of IoT devices would be significantly improved. This categorization coupled with a more refined port usage would allow the detection of normal and aberrant communication between IoT devices and between IoT devices and local/remote communicating/controlling entities.
Country Lookup
The expansion, accuracy, and refinement of country lookup would help to identify potential hostile or inappropriate communications between devices. IP addresses are managed by IANA along with five regional Internet registries. Tracking and associating IP addresses to a finer-grained location (i.e., street address or lat/lon location) would provide more detailed location information of potential attackers, botnets, and command and control servers.
Implementation of User Searches and Filtering of Scan Result
One of the immediate next steps to PiSensor is the development of an interface that would allow mining of scan and alert results. This feature needs to engage the user in actively reviewing the results of recording and/or alert results. This interface needs to be interactive and would help pinpoint activities of interest. This information would be used for early indication and warning, alert refinement and digital forensics, incident response (DFIR) activities.
Headless Communication with Remotely Deployed Pi Sensors
ZYMKEY from zymbit
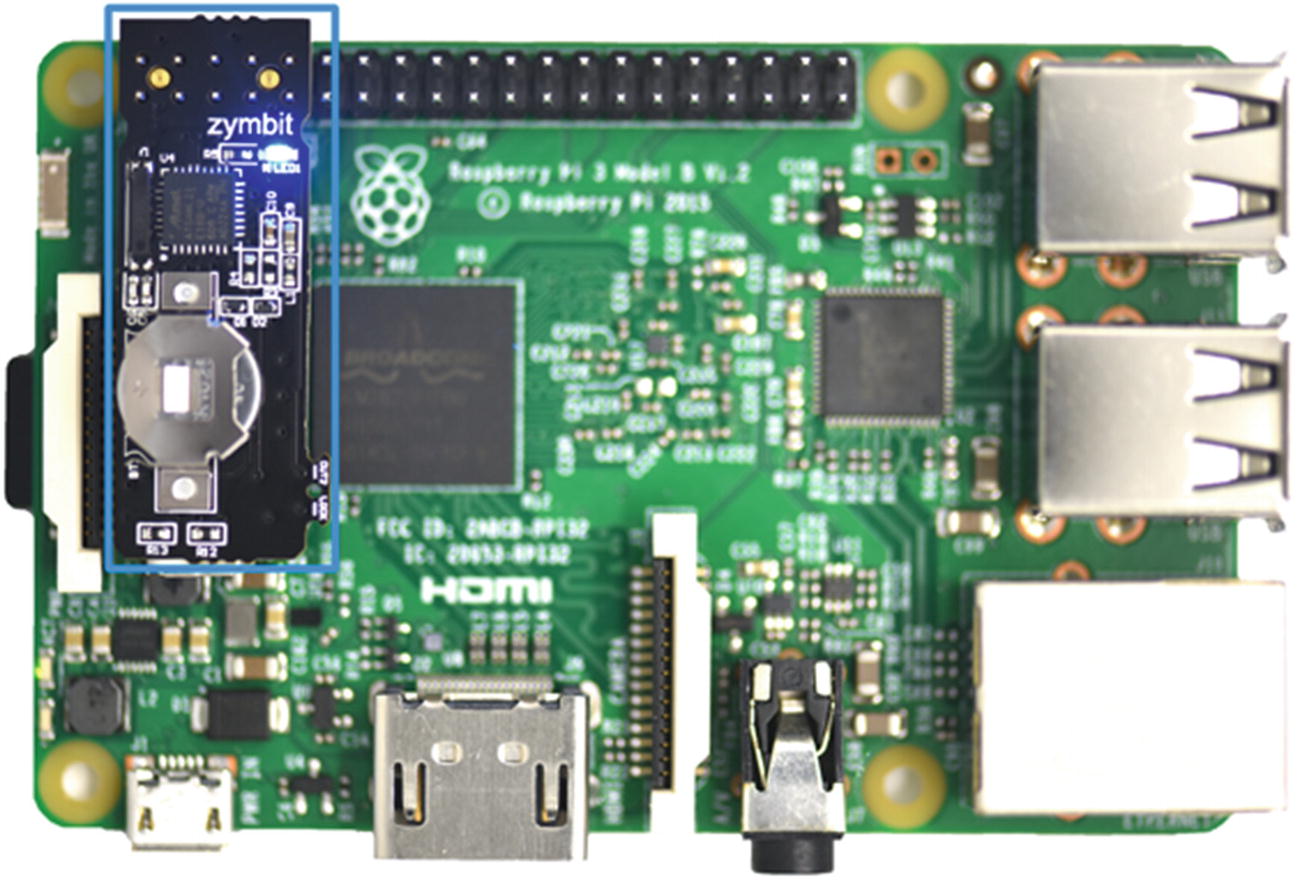
ZYMKEY install on a Raspberry Pi
The ZYMKEY provides a hardware key that connects to the Raspberry Pi I2C bus. The ZYMKEY comes with a Python application interface allowing us to integrate the key into the Pi sensor application. The device includes a cryptographic processing and authentication engine, a secure key store, and tamper detection and response circuits. In addition, when placed in production mode the ZYMKEY binds itself to the specific Raspberry Pi it is connected to and will not operate on a different Pi. This combined with the tamper detection and response and secure key store allows us to perform secure authentication and encryption with a control center.
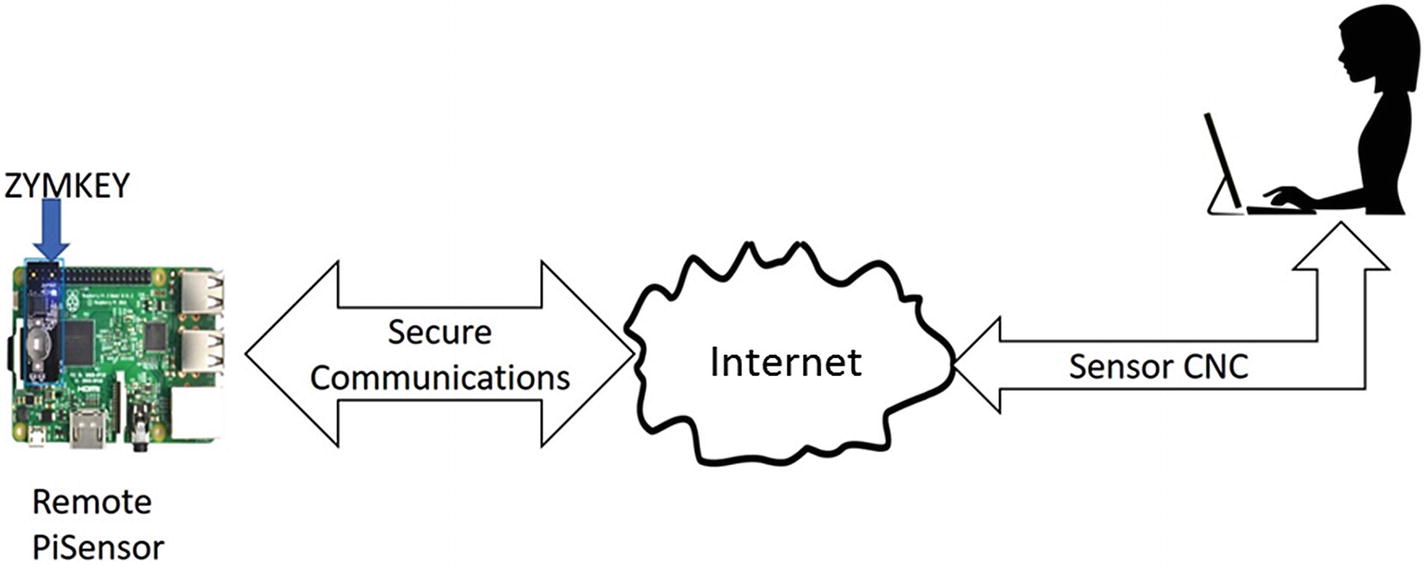
Secure command and control of a remote Pi sensor
Correlation of Results from a Swarm of Pi Sensors
The concept of swarm deployment of sensors is certainly not new. However, doing so with a group of Raspberry Pi’s acting as a swarm of IoT devices is. This final area of future work is still being researched at this point.
The need for this is straightforward. Organizations now need to deploy sensors at numerous locations within a single facility, facilities across town, or across the world, and this need will continue to grow. Consider a hotel with thousands of rooms and hundreds of floors. The ability to detect behaviors and instrument the Pi sensor with various wireless and physical sensing capabilities would provide early indications of nefarious activities or even aid hotel guests in distress. My building a swarm or Pi’s provides not only discrete communication from Pi to a command and control center, but also Pi-to-Pi sharing of information.
Raspberry Pi Sensor: Executing the Sensor on Your Raspberry Pi
The easiest method is to simply download the prebuilt executable for the Pi sensor. The executable is delivered as a Debian package. Download the package file piSensor.deb and then install it.
The second method is to download the source code and execute the PiSensor directly from the Python source: follow the README instructions in the source download.
The piSensor.deb and piSensor.zip are both available as part of the source code for this book. Go to www.apress.com/us/book/9781484236994 and click the source code button.
Summary
This chapter provided a look at the next steps for the PiSensor. If you would like to contribute ideas, write some code, or test future work, please contact the author directly.
Coming up next is the appendix. The appendix provides the complete source code for PiSensor along with samples of hotlist and MAC-LIST text files.
