Chapter 9. Cracking Passwords
Finding a computer to attack is the first step. Breaking into that computer is the second step. Most hackers succeed not as a result of any innate brilliance on their part, but because of ignorance on the victim’s part.
The first line of defense protecting most computers is usually nothing more than a unique combination of letters and numbers known as a password. Passwords are meant to block access to anyone but legitimate users, but they’re actually the weakest link in any security system. The most secure passwords are lengthy, consisting of random combinations of numbers, symbols, and both uppercase and lowercase letters. However, most people tend to choose simple, easy-to-remember passwords. They also tend to use the same password for several different systems (for example, their work computer, America Online account, and Windows screensaver). If you discover a person’s password, you’ll often have the key to a great deal of his or her information, even if it’s stored in several different accounts.
When a computer requires a password that you don’t know, you have several options:
Steal a valid password
Guess the password
Brute-force the password
Password Stealing
If you can get physical access to a computer, the easiest way to steal a password is by shoulder surfing—peeking over someone’s shoulder as he or she types. You can also try poking around the person’s desk. Most people find passwords hard to remember, so they write them down and store them for easy reference, perhaps on a Post-It stuck to their monitor or inside a desk drawer. That’s why hackers often get jobs as janitors. Cleaning offices late at night when no one is around gives them ample opportunity to explore each person’s desk and even experiment with the company computers.
If a hacker can’t find a password written in plain sight, they may try to social-engineer a password out of a gullible user (see Chapter 3) or try default passwords that come with common types of equipment such as Cisco routers. For a list of default equipment passwords, visit the Default Password List (www.phenoelit.de/dpl/dpl.html), CIRT.net (www.cirt.net/cgi-bin/passwd.pl), or another site called Default Password List (http://defaultpassword.com).
If social engineering or default passwords fail, the next best method is to steal the password using one of the following:
A keystroke logger
A desktop monitoring program
A password recovery program
Note
All of these programs require you to have access to the victim’s computer so you can install or run the program without his or her knowledge.
Using a keystroke logger
A keystroke recorder or logger records every keystroke a person types and saves this information in a file that a hacker can examine later. By using a keystroke logger, you can retrieve email addresses, email and instant messages, credit card numbers, and (of course) passwords. Some keystroke loggers can even capture screenshot images periodically so you can see which program someone was using while typing certain keystrokes.
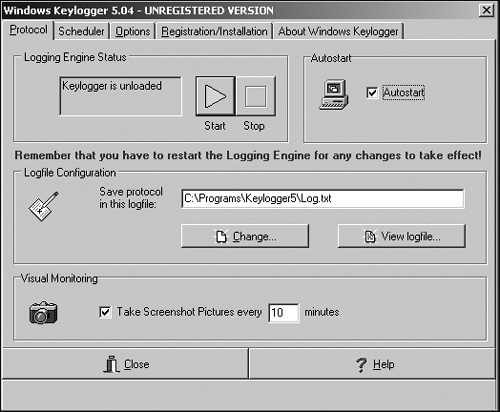
Figure 9-1 shows some of the different options for setting up a keystroke logger, such as where to store captured keystrokes and whether to load automatically when the computer boots up.
Unlike most programs, which display their name and accompanying icon in such places as the Windows Start menu and the Windows taskbar, keystroke loggers hide in the background so victims won’t even know they’re running. Although it’s possible to search through a computer’s memory, the Windows registry, or the hard disk to find a keystroke logger running, victims won’t bother looking if they don’t suspect anything is spying on them in the first place.
Since there’s always a chance that these software keystroke loggers could be detected, and each program only works with certain operating systems, such as Windows, a second alternative is to use a hardware-based keystroke logger. These types of keystroke loggers plug in between the computer and the keyboard.
Of course, a piece of peripheral hardware can be spotted just by looking at the back of the computer, but it’s completely invisible to any software running on that computer. Some people never look at the back of their machine, especially at work. Best of all, hardware keystroke loggers work with any operating system, including FreeBSD, Linux, or Windows XP.
Some popular hardware keystroke loggers include KeyGhost (www.keyghost.com), Hardware Keylogger (www.amecisco.com), Key Phantom (www.keyphantom.com), and KEYKatcher (www.keykatcher.com). To find a software keystroke logger, visitKeylogger.com (www.keylogger.org), which rates the different keystroke loggers by their features and ease of use.
One problem with hardware keystroke loggers is that they can only hold a limited amount of keystrokes, such as 128,000 keystrokes stored in 128Mb. While this may sound like a lot of keystrokes, it’s possible that the user could type 128,000 keystrokes playing a video game, which fills up the keystroke logger’s memory, and then the key-stroke logger won’t have any more room left to hold the 128,001 through 128,009 keystrokes, which may contain the password you want.
Keystroke loggers cause additional problems from a legal point of view. Some people argue that keystroke logging should be treated as wiretapping and made illegal except for court-authorized use. Others believe it’s okay to use a keystroke logger on your own equipment, even if it means spying on other users. Until the courts decide how to categorize keystroke loggers, using one could mean breaking a law that you never even knew existed.
Spying with a desktop monitoring program
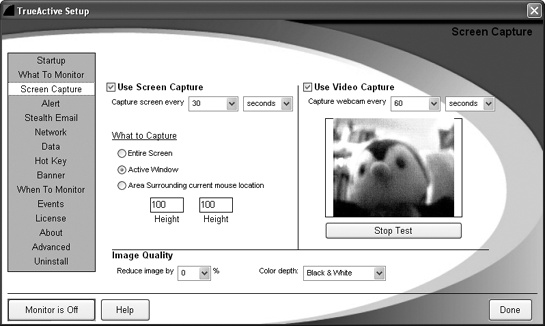
Desktop monitoring programs are extra-strength keystroke loggers with added features. Not only can they record keystrokes, but they can also secretly track which programs a person uses, how long the person uses each program, and every website viewed. To identify who has used the computer at any given time, a desktop monitoring program can also secretly turn on a webcam to watch the person sitting in front of the screen, as shown in Figure 9-2.
To find a desktop monitoring program, try these sites: AppsTraka (http://appstraka.hypermart.net), PC Spy (www.softdd.com), Desktop Surveillance (www.omniquad.com), or NetSpy (www.skysof.com).
You can even install some desktop monitoring programs remotely without ever physically accessing a victim’s computer. To remotely install a desktop monitoring program, you can send a victim a seemingly harmless email message that contains a link for them to view a greeting card. However, as soon as they click this link, they’ll see the greeting card and install the desktop monitoring program at the same time. Now the desktop monitoring program can spy on a victim from afar much like a RAT (see Chapter 5).
Many corporations now use desktop monitoring programs to protect themselves in case employees start sending inappropriate email messages to others under the company’s time. Some corporations have even gone a step further and use desktop monitoring programs to make sure employees are working rather than checking sports scores on the Internet.
Many companies even market desktop monitoring programs as a way to spy on your spouse, kids, or boyfriend/girlfriend to make sure they aren’t doing something you don’t want them to do. Of course, if you feel the need to monitor (spy on) people close to you, you may have a bigger problem than just knowing what they’re doing on a computer.
Using a password recovery program
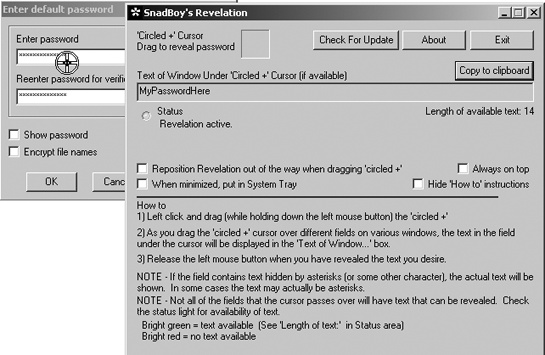
Because typing a password over and over again to access a program can be a nuisance, many programs let users store passwords. For security, the passwords are hidden behind a string of asterisks on the screen. But people often forget their passwords and then can’t access their programs or files. Enter password recovery programs, which can, of course, also be used to retrieve other people’s passwords. By running one of these password recovery programs and moving the mouse pointer over an asterisk-hidden password, you can see the plain text underneath, as shown in Figure 9-3.
Some popular password recovery programs include ActMon Password Recovery XP (www.actmon.com/password-recovery), Password Recovery Toolkit (www.lostpassword.com), Peek-a-Boo Password Viewer (www.corteksoft.com), and Revelation (www.snadboy.com).
Besides restricting access to particular programs, passwords can also block access to individual files such as WordPerfect documents or Microsoft Excel spreadsheets.
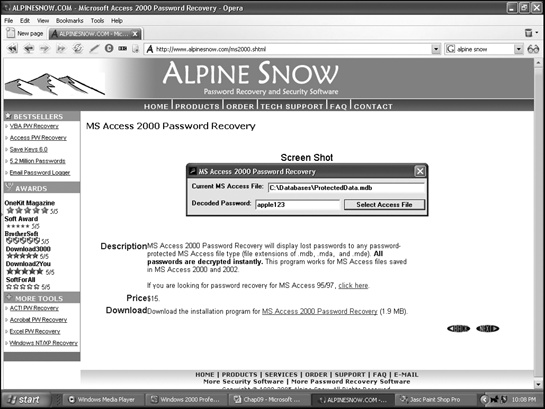
To retrieve or crack password-protected files, get a special program from one of these companies: Access Data (www.accessdata.com), Passware (www.lostpassword.com), ElCom (www.elcomsoft.com), Password Crackers Inc. (www.pwcrack.com), or Alpine Snow (www.alpinesnow.com), which is shown in Figure 9-4.
Dictionary Attacks
Ideally, a password should be a random collection of numbers, symbols, and uppercase and lowercase letters, but few people want to waste time creating a difficult password that they’re likely to forget. Instead, most choose easy-to-remember passwords that are ordinary words. To find such simple passwords, hackers have created special password cracking programs that use dictionary files (sometimes called word lists).
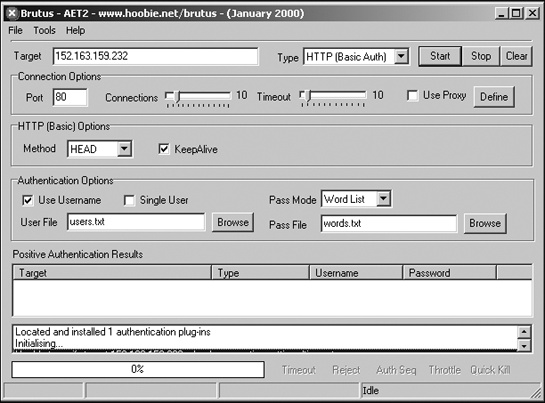
Figure 9-5 shows a password-cracking program called Brutus, which tries to break into a website using two files, users.txt and words.txt. The users.txt file contains a list of common user names, and the words.txt file contains common passwords. By mixing and matching different user names and passwords, Brutus can try endless combinations until it finds both a valid user name and the password that works for that user name.
A dictionary file simply contains common words that people are likely to use as a memorable password, such as names of actors, popular cartoon characters, and rock bands, Star Trek jargon, common male and female names, technology-related words, and other words found in most dictionaries.
The password-cracking program takes a word from the dictionary file and tries this word as a password to access a computer. If the first word isn’t right, the program tries another word from its dictionary file until it either finds the correct password or runs out of words. Of course, a hacker can keep trying different dictionary files; if a password is an ordinary word, it’s only a matter of time before a dictionary attack will find it.
To increase the odds of uncovering a password, some password-cracking programs will try not only every word in a dictionary file, but also subtle variations on each word such as spelling the word backwards or adding different numbers on the end. So even though a password like SNOOPY12 won’t be found in an ordinary dictionary file, the password-cracking program can still uncover this password by manipulating each word in its dictionary file.
One of the most popular password-cracking tools is John the Ripper (www.openwall.com/john), and one of the largest collections of word lists can be found at the Wordlist Project (www.gattinger.org/wordlists), which offers lists in various languages including English, Spanish, Japanese, and Russian.
To find other password-cracking programs, visit Russian Password Crackers (www.password-crackers.com), AntiOnline (www.antionline.com), and New Order (http://neworder.box.sk).
Brute-Force Password Attacks
Dictionary attacks can find passwords that are ordinary words or variations of words, but sometimes a password consists of random characters. In these cases, the only solution is to use a brute-force attack.
As the name implies, a brute-force attack exhaustively tries every possible combination of numbers, letters, and symbols until it finds the right password. So even if someone’s password is as obscure as NI8$FQ2, a brute-force attack will eventually find it (and every other password on that computer).
The main drawback of brute-force attacks is time. You can sit in front of a bank’s combination lock and try every three-number combination possible, but it may take you a long time to find the one that opens the lock. Similarly, a brute-force attack might take a few thousand years to find a valid password.
For this reason, brute-force attacks are generally useless against individual computers protected by strong passwords (consisting of random letters, numbers, and symbols). However, they are still potentially effective on a network. The more people who use a network, the more likely at least one person will have chosen a simple, easy-to-remember password, such as her dog’s name or the first three numbers of her home phone number. A brute-force attack will discover the weakest password into a network, and that’s all a hacker needs.
Passwords: The First Line of Defense
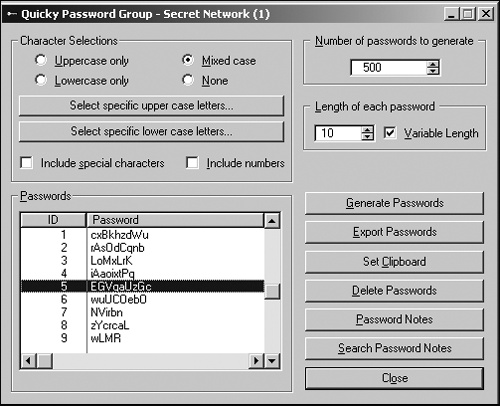
Choosing a unique, hard-to-guess password will probably stop all but the most determined hackers. (It can also stop you if you can’t remember it.) To foil most hackers, just sprinkle your passwords with some random characters (such as symbols and numbers) or use a special program, such as Quicky Password Generator (www.quickysoftware.com), Masking Password Generator (www.accusolve.biz), or RandPass (www.randpass.com), that can create genuinely random passwords of varying lengths, as shown in Figure 9-6.
Of course, trying to remember a random password can be troublesome, so many people create passwords based on meaningful phrases that they won’t forget, such as “IhtP2004,” which can stand for “I hate the President,” followed by an election year. By taking the first letter of a memorable phrase and sprinkling it with numbers or other characters that make sense only to you, you can create a password that’s impossible to guess.
In general, the longer the password, the harder it will be for someone to guess or crack. In Windows NT, passwords are particularly easy to crack since they consist of 14 uppercase characters, divided into two 7-character parts. So rather than force hackers to crack a 14-character password, Windows NT allows hackers to crack a 7-character password twice, which is far simpler to do.
Blocking Access with Biometrics
Another way to block access to a computer is through biometrics, which identifies authorized users through their unique fingerprints, retina scans, voices, or other physiological or behavioral features. Hackers can always steal or guess obvious passwords like sex or password, but it’s much more difficult to steal—and nearly impossible to guess—someone else’s fingerprint pattern.
Biometrics works on the principle that every person has unique characteristics that are impossible to duplicate; even identical twins have different sets of fingerprints. Typically, a biometric security system works by comparing data collected from someone attempting to gain access to the system with a database of authorized data patterns. First, therefore, every authorized user’s biometric data must be stored in a database against which the biometric device can check to decide who to accept and who to reject.
Once you’ve given the biometric device a few samples of each person’s data, you need to test the device to ensure that it can accurately identify individuals. The biggest problem with biometric devices is finding the proper balance between false acceptance and false rejection.
As the name implies, false acceptance means that the biometric device’s criteria accept too much data as valid, so anyone with fingerprints that are somewhat similar to an authorized user’s may be granted access. False rejection means that the biometric device’s criteria are too narrow, which means that even authorized users may have trouble getting it to recognize them and allow them access.
Biometric devices
The most common biometric devices, and the simplest to implement, are fingerprint scanners. To learn more about fingerprint biometric devices, visit DigitalPersona (www.digitalpersona.com), Keytronic (www.keytronic.com), Precise Biometrics (www.precisebiometrics.com), or Ultimaco Safeware (www.ultimaco.com).
Like fingerprints, no two people’s signatures are alike, so several companies market signature recognition devices. For more information about these, visit Communication Intelligence Corporation (www.cic.com) or CyberSign (www.cybersign.com).
Hook up a camera to your computer and, with the right software, you can verify authorized users through facial recognition. Users stare into a camera and the computer recognizes them as authorized users. To learn more about facial recognition, visit the Face Recognition Homepage (www.face-rec.org).
For a face detection algorithm demonstration, visit the Pittsburgh Pattern Recognition site (http://demo.pittpatt.com). This demo allows visitors to upload photographs of different people to see how accurately the facial recognition algorithm identifies the same face in different poses and backgrounds.
Voice Security Systems (www.voice-security.com) uses voice prints to deny or allow access. No two people speak exactly alike, so voice recognition systems train computers to listen to each person’s unique speaking style. (Unfortunately, if that person has a cold, it’s possible that the voice recognition system won’t even recognize a valid user’s voice.)
Iridian Technologies (www.iridiantech.com) offers an even more exotic biometric device that scans the retina of the eye to identify authorized users. Rather than rely on a single biometric measurement, SAFlink (www.saflink.com) goes further, using voice, face, and fingerprint recognition together to identify authorized users with an ordinary digital camera, microphone, and fingerprint reader. Another company, BioID (www.bioid.com), uses face, voice, and lip movement recognition to identify authorized users. Even if someone fools one biometric device, they probably won’t be able to fool the second and third one too.
Defeating biometrics
In theory, no one can duplicate another person’s fingerprint, signature, or facial scan, so biometrics should be the ultimate solution for securing access to a computer, right? Wrong.
Biometrics can be fooled surprisingly easily. That’s why most biometric devices are used in combination with human security guards or surveillance cameras whose footage can be reviewed later. Besides cruder methods like pulling a gun on an authorized user and forcing him to scan his retina or cutting off a person’s finger to get past a fingerprint scanner, there are subtler, less violent ways to trick biometric devices.
When an authorized user puts his fingertip on a fingerprint scanner, the computer verifies his access and he walks away. Of course, an imprint of his valid fingerprint still remains behind on the glass of the fingerprint reader device. Many fingerprint scanners can be fooled by just cupping your hands and breathing over the device, which causes the residue of the authorized user’s fingerprint to reappear. The scanner sees the valid fingerprint again and gives you access.
You can capture a valid fingerprint for future use by simply sprinkling graphite powder on the fingerprint scanner and then sticking a piece of ordinary cellophane tape over the surface. The fingerprint is captured on the sticky side of the tape. Now you can stick this piece of tape over the fingerprint scanner, which will recognize it as belonging to a valid user.
Facial recognition devices are even simpler to fool. Just take a picture of an authorized user, hold it up to the scanning camera, and chances are good that the biometric facial recognition device will think it’s a valid user. (Newer facial recognition systems ask people to turn their heads slightly to verify that the camera is seeing a real person’s face instead of a two-dimensional picture.)
Some retina scanners can be fooled the same way, provided you can get a picture of an authorized user’s retina.
Fooling voice recognition devices can be just as easy. Hide a tape recorder and stand near an authorized user speaking into the microphone. Then play back this recording and you’ve got yourself a valid voice print that the biometric device will recognize. (More advanced voice recognition devices may record dozens of different words and randomly ask the user to repeat one of them. The system might ask the user to say the word bubbles one time, and the word balloon another time, so a recording of a person’s voice won’t work most of the time.)
Perhaps the best way to fool any biometric device is to intercept the data going from the biometric reader to the computer. If you can sneak a hardware device, such as USB Agent (www.hitex.com), in between the biometric device and the computer, you’ll capture the information entered by a valid user. Now you can feed this biometric data to other computers and trick those computers into thinking you must be someone else, which could be the ultimate identity theft technique.
For another tool to intercept data sent across a USB cable, grab a copy of USB Sniffer for Windows (http://sourceforge.net/projects/usbsnoop) or USB Snoopy (http://mxhaard.free.fr/snoopy.html). Both programs can snare data so you can analyze a valid user’s biometric data and then feed it back into the computer later.
No matter how advanced biometric devices may get, there will always be a way to fool them, although it might not be easy. To keep someone from fooling a biometric device, you need a guard to watch over it. Of course, if you can afford to station a guard by your computer, you probably don’t need the biometric device in the first place.
Good Enough Security
There will never be a foolproof way to keep hackers out of a computer, whether you use passwords, biometric devices, or hardware authentication devices that you plug into a computer to verify your identity. But the more difficult you make it to break into, the more likely most hackers will go off in search of an easier target. Unfortunately, if your computer is connected to a network, the easiest target to break into may be the computer right next to yours. Still, it’s important to keep intruders out of your computer because once they get in, finding the hacker and kicking him out is going to take a lot more work.