Chapter 22. Computer Forensics: The Art of Deleting and Retrieving Data
Like most criminals, hackers often bring about their own downfall by failing to remove all traces of their crime. Not only do many hackers leave incriminating notes and printouts of their latest exploits scattered around, but they also can’t resist bragging about their exploits in public chat rooms. Yet even this blatant indiscretion wouldn’t be so damaging if these same hackers didn’t unwittingly leave incriminating evidence stored all over their own computers too.
Recovering Deleted Data
The biggest difference between electronic data and traditional data is that once you store electronic data on any form of magnetic media, it can stay there much longer than you expect. To understand how it’s possible to recover a file that’s been deleted, you need to understand how computers store and organize files on a disk.
When a computer stores information on a disk, it can’t just toss it anywhere, because that would make it difficult to find it again—it would be like throwing your socks on your bedroom floor and then wondering why you can never find a matching pair when you need one. To help organize data, computers divide disks into multiple tracks, which you can think of as circular storage bins on the surface of a disk.
Each track is divided into smaller parts called sectors. A group of sectors is called a cluster. When you save data to your disk, your computer stores your file in multiple sectors. When you add or delete data from a file, the total number of sectors used to store your file grows or shrinks accordingly. Basically, a sector is a tiny box that contains part of a single file.
Ideally, your computer tries to store files as one continuous track, which allows it to retrieve data quickly. However, the more you save, edit, and delete files, the more likely it is that the computer will have to store one part of a file in one sector and another part of that same file in another sector, on a completely different part of the disk. When you defragment your hard disk, you’re essentially rearranging all your files so the data from each file gets stored in adjacent sectors once more.
To keep track of which sectors contain which files, every disk contains a special directory, sometimes called a File Allocation Table (FAT) or a Master File Table (MFT). The FAT or MFT (or whatever name your particular computer uses) lists all the files stored on the disk along with pointers that identify the exact tracks and sectors that contain each file.
When you delete a file, your computer takes a shortcut. Instead of physically destroying the data, the computer simply erases its existence from the disk’s directory, which pretends that the file no longer exists, although the contents of the file are still intact. Only when the computer needs the space taken up by the deleted file will it actually overwrite the old information with new data. This is like taking your name off your apartment building’s directory when you move out, but leaving your unwanted belongings behind in your old apartment. Only when someone else moves in do the old contents of the apartment get thrown out.
If your disk has plenty of extra space available, you could go weeks, months, or even years before the data in those deleted sectors is overwritten. (You can accomplish almost the same thing as overwriting the data, however, by defragmenting your hard drive regularly.)
You can usually retrieve a trashed file by running an undelete utility program right away. An undelete utility simply changes the disk directory to identify any “deleted” files, so that the computer will recognize the files again. Of course, the longer you wait to run the utility, the more likely your computer will have overwritten some, or possibly all, of a particular deleted file’s contents with new data, making it difficult, if not impossible, to recover the original contents.
Some utility programs, such as the Norton Utilities, come with a file-deletion protection feature that saves any deleted files in a special folder so that you can quickly and accurately recover them any time in the future. Obviously, this feature can be a lifesaver if you accidentally delete something important, but it can also work against you by preserving sensitive files you thought you got rid of months ago.
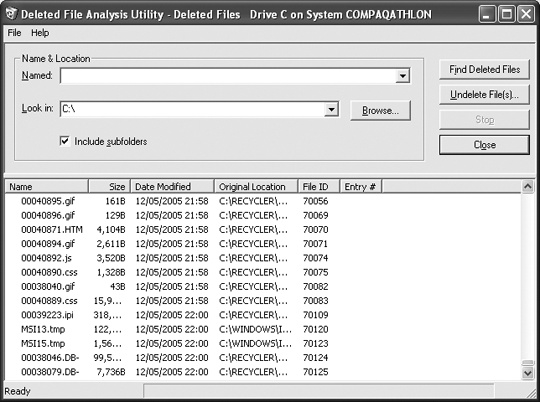
To find an undelete program, try Norton Utilities (www.symantec.com), Active@DELETE (www.active-undelete.com), Restorer 2000 (www.bitmart.net), or Undelete (www.execsoft.com). Executive Software, the maker of Undelete, also offers a free Deleted File Analysis Utility (see Figure 22-1), which examines your hard disk to see how many deleted files may still be recoverable. The results may surprise you.
File Shredders
If you delete a file, wait a day or two, and then try to run an undelete program, there’s a good chance that the operating system will have overwritten all or part of that file’s contents.
If you want to intentionally overwrite old data belonging to deleted files, you can use a special file-shredding program. File shredders overwrite the storage formerly used by deleted files with random characters, one or more times. As a result, even if an undelete program manages to recover the old disk directory entry pointing to a previously deleted file, it will only find random data stored there.
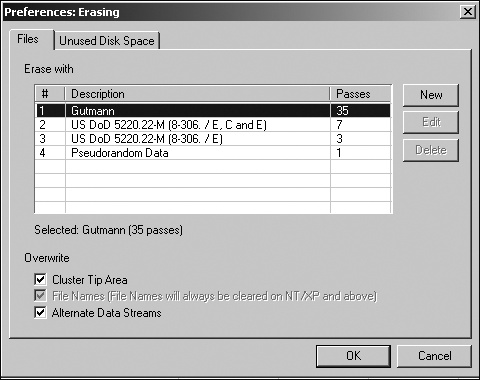
Not all file shredders are equal, however. For example, to defeat an ordinary undelete program and get the job done more quickly, a file shredder may make just one pass at filling your deleted file’s old data area with random data. While this quick wipeout defeats most undelete programs, it will not defeat specialized computer forensics tools. A really good file shredder offers several ways to shred your files that balance speed and security, as shown in Figure 22-2.
Most file shredders make multiple passes over a deleted file for additional security; the more passes, the longer the deletion takes, but the more likely you’ll eliminate all hope of recovery.
The Department of Defense (DoD) even has its own shredding standard, dubbed DoD 5220.22-M (www.dss.mil/isec/nispom.htm), which defines acceptable government standards for deleting computer files. The DoD technique wipes a file seven times, each pass replacing the deleted data with a different set of random data that further obscures the original. Seven passes can destroy virtually all traces of the original file, although theoretically it may be possible to recover some or all of the information later using a magnetic sensor or electron microscope to scan the storage media on an atomic scale.
The Gutmann algorithm is even safer than the DoD data deletion standard, requiring 35 passes over a file’s disk storage areas to wipe away every possible trace of the original contents. For more information about securely destroying data, visit Peter Gutmann’s web page (www.cs.auckland.ac.nz/~pgut001) and read his paper, “Secure Deletion of Data from Magnetic and Solid-State Memory.”
Storing Deleted Data
No matter how many times you’ve deleted a file or what deletion methods you may have used, there will almost always be a way to retrieve it again. The most direct approach is to recover bits and pieces of an overwritten file’s data by analyzing its magnetic traces on the hard disk, as mentioned above. A more practical and much simpler approach is to look for undeleted traces of that file scattered in other places on the computer.
Note
If you’re trying to get rid of data, simply encrypting or deleting a file will never be enough. Encryption and file deletion hide a specific file’s contents, but do nothing to hide or erase information copied from the file into temporary files on your hard disk. For example, Microsoft Word typically creates a temporary copy of your document as an emergency backup, just in case your computer crashes or the power goes out. Then you can recover your work by loading this temporary file. However, if you create a sensitive document and encrypt it, all of your sensitive data still remains inside Word’s emergency backup copy of your file, which anyone can open and read.
Finding data stored in slack space
Under Microsoft Windows, the computer divides magnetic media (hard disks, floppy disks, rewritable CDs, etc.) into chunks of a fixed size known as clusters. When you store a file, the entire file rarely fits in a single cluster, so Windows stores it in multiple clusters. Almost inevitably, the last part of a file won’t completely fill up its cluster, and it’s this extra space that’s known as slack space.
Computers often use the slack space to store information about that particular file. For example, when you open a file (say, for editing) and type anything from the key-board, the operating system may temporarily store your keystrokes in a portion of memory called the keyboard buffer. Without the keyboard buffer, you could type too fast for the computer to react, and it could lose keystrokes. When you close the file, the computer may then clear the keyboard buffer by dumping its contents into that file’s slack space.
If you delete parts of a file, that file’s slack space grows and traces of the previous file version are left behind there. If you delete or encrypt a file, the slack space remains untouched because it is not actually part of the file. Until you overwrite the slack space with random data, any information dumped there can still be recovered.
For maximum security, don’t just encrypt your files but encrypt your entire hard disk. Not only will this protect your files, but it will also encrypt any traces of your data scattered elsewhere on your computer.
Finding data stored in swap files
One particularly vulnerable area of your computer is the swap file. A swap file allocates part of your hard disk for temporarily storing data from its working memory, known as random-access memory (RAM), so that the computer can free up some of this space to use for running programs as needed. Without swap files, your computer would have to store both a running program and any open files it is using in RAM. So, if you opened an extremely large file, that could be enough to gobble up all of your memory and prevent other programs from running. By selectively swapping data back and forth between the hard disk and the RAM, an operating system can run more than one program at a time, even if their total memory requirement theoretically exceeds what’s actually available. (This trick used by the computer to manage running programs is where the name “swap file” comes from.)
So, when you run a program such as a word processor or a spreadsheet, your operating system from time to time temporarily stores some of the associated data, such as the contents of a report or a budget that you’re working on, in the swap file—typically when the program is momentarily idle. When you save or delete the data file, much of the file’s data may still remain in the swap file.
Your history stored in a web browser cache
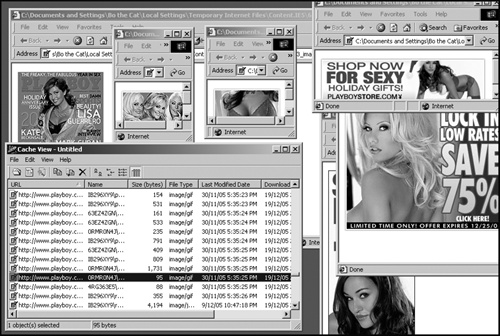
When you search the Internet, your browser stores (or caches) the graphic images from the pages you visit in what’s called the cache directory. That way, if you visit the same website later, your computer can retrieve these graphics from its cache rather than directly off the Internet, which can speed up the time it takes the page to load.
By browsing the cache directory of someone’s browser, you can see which websites they’ve visited along with the graphic images they saw, as shown in Figure 22-3.
To view the cache for Internet Explorer, grab a copy of BCIView (www.debryansk.ru/~kamkov) or Cache Auditor (www.webknacks.com). For other browsers, such as Opera and Firefox, grab a copy of Cache View (www.progsoc.uts.edu.au).
If you don’t want anyone knowing what you’ve been looking at while online, just remember that purging the cache simply deletes the files it contains and won’t physically remove them—anyone can undelete your erased cache directory later. For more security, use a file shredder such as Shred XP (www.gale-force.com), 12Ghosts Wash (www.12ghosts.com), Window Washer (www.webroot.com), or BCWipe (www.jetico.com), which can also wipe the slack space of specified files and delete web cache files as well. For a Macintosh and Windows file shredder, grab a copy of ShredIt (www.mireth.com).
For added protection, use a special cache-cleaning program such as IEClean/NSClean (www.nsclean.com), which works with both Internet Explorer and Mozilla /Firefox, and Cache Cleaner (www.northernsoftworks.com), which can clean the browser cache of the Mac OS X Safari browser.
If you think purging your cache and wiping out temporary files is too much trouble, guess what? That’s exactly what computer forensics experts are counting on when they examine a suspect’s computer.
Hackers can also take advantage of computer forensics by sneaking into a computer and looking for previously deleted files containing firewall or security program logs that can identify what type of firewall or security program is running and possibly how it might work. If you’re a system administrator, just remember that your computer’s log files might be hidden or encrypted, but there’s always a way for a hacker to use computer forensics to find it anyway.
Computer Forensics Tools
Depending on the seriousness of the crime and the importance of recovering the data stored on a disk, computer forensics experts generally rely on four basic tools when retrieving deleted data: file-undeleting programs, hex editors, and magnetic sensors and electron microscopes.
File-undeleting programs
As discussed earlier in this chapter, file-undeleting programs, readily available with programs like Norton Utilities, are often sufficient to catch novices who attempt to get rid of incriminating files, such as pictures of child pornography. But they are only effective if the file contents have not already been overwritten on your hard disk, so undeleting programs are a relatively weak forensics tool.
Hex editors
Hex editors are special programs that let you peek at the physical contents stored on a disk. Programmers often use hex editors to modify or examine files, while hackers often use hex editors to peek inside copy-protected games so they can peel away the security or so they can modify the video game to find and turn on hidden features.
Hex editors can probe the contents of any disk. Instead of forcing you to view a disk’s contents as organized into partitions, directories, and files, as usually shown to the user by an operating system, a hex editor lets you examine the contents of a disk in terms of its physical layout, such as scanning the surface of the storage media from the outer edges of the disk down to its inner edges.
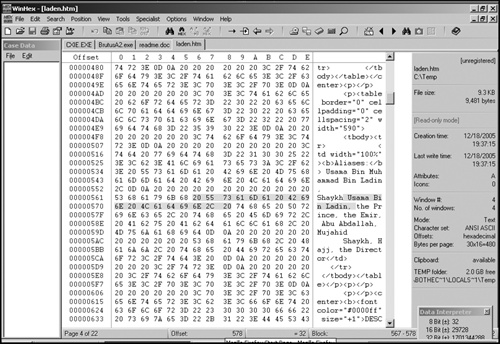
By using a hex editor, computer forensic specialists can identify and retrieve information that can’t normally be accessed by the operating system. As shown in Figure 22-4, hex editors don’t rely on operating system services to open and access “files.” Instead, they display the physical disk area holding the contents of a file, using hexadecimal codes to represent the actual bytes of data.
Using a hex editor to examine an entire hard disk would be like scouring the inside of a skyscraper for fingerprints, so they’re best used for searching only the specific parts of a drive where desired information may reside. Still, hex editors can often recover some or all of the data from a deleted file that you might not otherwise be able to access, such as in the slack space of a file. To see what a hex editor can find on your hard disk, download and try Hex Workshop (www.bpsoft.com), UltraEdit (www.idmcomp.com), WinHex (www.x-ways.net), or VEDIT (www.vedit.com).
Magnetic sensors and electron microscopes
No matter how many times you overwrite a file or format and partition a hard disk, traces of the original data may still remain. File shredders make it progressively more expensive and difficult to retrieve, but not impossible.
Every file you delete leaves residual magnetic traces of itself. Each time the computer overwrites a file’s contents, the disk heads may be aligned slightly differently with respect to the surface of the media, and fragments of the deleted file may remain afterwards. Forensics experts can use sensors to measure the changes in magnetic fields on a disk’s surface and then reconstruct part or all of the bytes in a deleted file, or they can use an electron microscope to do the same thing. Electron microscopes—extremely expensive but available to many governmental organizations—can also measure tiny changes in magnetic fields, left over from the original data, that not even overwriting can completely obliterate.
People may burn their floppy or hard disks, crush and mangle them, cut them into pieces, pour acid on them, and physically manhandle them in a myriad of ways, thinking there will be no possible way of using them on another computer again. However, even the physical destruction of a floppy or hard disk can’t guarantee that the data has been safely destroyed, because government agencies such as the FBI and CIA are able to practice a specialized technique known as disk splicing. Disk splicing entails physically rearranging the pieces of a floppy or hard disk as nearly as possible back to its original condition. Then magnetic sensors or electron microscopes scan for traces of information still stored on the disk surface.
Obviously, disk splicing is a time-consuming and expensive procedure, so don’t expect your local police force to have that kind of knowledge, skill, or equipment. But if you’ve destroyed evidence that might interest the NSA, CIA, or FBI, don’t expect a mangled disk to hide your secrets from the prying electronic eyes of rich and powerful government agencies. In fact, the American government even has a special laboratory called The Defense Computer Forensics Lab (www.dcfl.gov), located in Linthicum, Maryland, which specializes in retrieving information from computers, no matter what condition of the hardware or disks.
The ultimate lesson to learn is that if you don’t want to risk having information retrieved off your hard or floppy disk, your only absolutely foolproof option is to avoid storing it on any computer in the first place.
Commercial Forensics Tools
Identity theft, online stalking, Internet sex predators, cybercrime, and terrorism—these are all activities that promise to fuel the development of new computer forensics techniques compatible with Windows, Linux, and Mac OS X. To learn about some of the tools that law enforcement agencies have at their disposal, visit Digital Intelligence (www.digitalintelligence.com), which sells a unique forensics tool called DriveSpy for accessing physical drives using pure BIOS (Int13 or Int13x) calls, which bypass the operating system. Not only does this allow DriveSpy to access disk partitions created by any type of operating system, but it also ensures that the operating system won’t modify or erase data (e.g., by changing the swap file) during normal use of DriveSpy.
DriveSpy lets you do the following:
Examine hard disk partitions
Copy files to a designated work area without altering file access/modification dates
Undelete files and put them in a designated work area without altering file access/modification dates
Search drives, partitions, and files for text strings or data sequences
Store the slack space from an entire partition in a single file for examination
Save and restore one or more contiguous sectors (the physical area on a disk) to/from a file
For those who need more power than DriveSpy offers, Digital Intelligence also sells dedicated computer forensics workstations, Forensic Recovery Evidence Devices (whimsically dubbed FREDs), and portable versions called Forensic Recovery Evidence Device Diminutive Interrogation Equipment (FREDDIEs). If you see the police hauling a FRED or FREDDIE into your computer room, brace yourself. They’ll be able to copy data from any hard disk or other removable storage device, such as rewritable DVDs; create images of your entire hard disk; connect directly to your computer and monitor any communications that your friends are trying to send to you; examine any visible and hidden partitions for data; and capture video images of the appearance and location of equipment at the scene.
For another peek into the forensic tools that law enforcement uses, visit Guidance Software (www.guidancesoftware.com) to learn about its EnCase program. EnCase can examine MS-DOS/Windows, Macintosh, and Linux computers. EnCase can hook up to a target computer through a parallel cable, scan the hard disk for graphics files (useful for hunting down child pornographers), copy them to another computer, and then display or print the contents of these graphic files.
EnCase can also search text and other files—regardless of what application or operating system created them—to find evidence against criminals or terrorists. Once EnCase finds a file containing a specific word or phrase, it can list or copy those files for further examination.
To learn more about how governments track down criminals using computer forensics, visit the United States–based Electronic Crimes Task Force (www.ectaskforce.org) and the Scotland-based National Hi-Tech Crime Unit (www.sdea.police.uk/nhtcus.htm).
To experiment with some forensic tools on your own computer, grab a copy of Sleuth Kit (www.sleuthkit.org) or F.I.R.E. (http://fire.dmzs.com). Links to more forensic tools are available from Computer Security, Cybercrime, and Steganography Resources (www.forensics.nl), the Talisker Security Wizardry Portal (www.networkintrusion.co.uk), or the Alexander Geschonneck security website (www.geschonneck.com/security/forensic.html).
The next time you get a used computer, use one of these forensic tools to peek into the contents of the hard disk. Many people sell used computers without bothering to wipe out their personal data, which means there’s a good chance you could still find someone else’s financial records, personal information, and even credit card numbers, too. If you’re going to give away a computer, make sure you wipe the hard disk as clean as possible, and then hope that someone won’t get lucky and find some useful information still hidden on your erased hard disk anyway.
Protecting Yourself
Even if you shred files religiously, law enforcement officials, and possibly others, have a variety of computer forensics tools at their disposal to pry out any secrets your deleted files may be hiding. So how can you protect your computer from their prying eyes? Basically, you can’t. While you can make recovering data harder by periodically purging your cache directory and only storing files on removable disks (such as rewritable DVDs) and physically destroying them afterwards, just remember that everything you do on your computer can potentially be recovered and examined later.
To destroy the contents of a hard disk quickly, grab a copy of DiskZapper (http://diskzapper.com), available as a bootable floppy or CD. If you boot up from a DiskZapper disk, the program starts erasing your hard disk right away. It can be a handy tool to have around when you want to destroy data quickly.
If you’re a programmer and want to understand exactly how a file shredder works, download the source code for Eraser (www.tolvanen.com/eraser), written by Sami Tolvanen. Not only is this file shredder absolutely free for anyone to use, but it is also distributed with Microsoft Visual C++ source code, so you can see how it works and even customize it for your own particular needs.
Linux users can download a file-deleting program called Wipe (http://gsu.linux.org.tr/wipe). Like Eraser, Wipe is free and includes C source code so you can look under the hood and maybe even improve the program on your own to wipe out data even more securely.
But don’t assume you can rest easy even if you’ve gone ahead and scoured your hard disk until it’s squeaky clean. Just as every bullet fired can potentially be traced to a specific gun, so everything created by a computer can be traced to a specific machine given the right circumstances and a determined enough searcher.
Edward Delp (http://dynamo.ecn.purdue.edu/~ace), a professor of electrical and computer engineering at Purdue University, has developed a technique to identify the unique “signatures” of printers based on their subtle variations. The United States Secret Service is particularly interested in this technology for tracing documents and counterfeit bills back to specific printers.
Tadayoshi Kohno, a University of California Ph.D. student, has even found a way to identify individual computers over the Internet, as documented in the research paper “Remote physical device fingerprinting” (www.caida.org/outreach/papers/2005/fingerprinting). The technique works by “exploiting small, microscopic deviations in device hardware: clock skews.” Essentially, Kohno’s technique analyzes how a particular computer’s clock timestamps the information it sends over the Internet, which can be used to uniquely identify that specific computer even if it’s behind a firewall or connecting to the Internet through multiple proxy servers.
So, if your hard disk data can be retrieved despite your best attempts to destroy it, and if your printer and your computer hardware can give away your activities, can you ever keep any of your stuff private? The answer is no—unless, of course, you only use someone else’s computer. Will you ever really need to go this far? That answer depends on you.