Chapter 13 Skype Firewall and Network Setup
Solutions in this chapter:
A Word about Network Address Translation and Firewalls
When the Internet began, the creators didn’t envision the type of growth that we are experiencing today. During the last 10 years, the number of hosts on the Internet increased by more than a factor of 50.1 In order for each Internet device, or host, to communicate on the Internet, it must have a unique internet protocol (IP) address. The addressing scheme for the Internet allowed for billions of IP addresses, but now most of them are allocated.
The Internet’s popularity results in a maximum number of available IP addresses. Homes and offices around the world are now connecting many hosts at a single location and it is not possible for every single device to have its own public IP address. To increase the number of addresses available, a new standard called IPv6 has been developed. Until IPv6 is finalized, other methods are needed to allow for the sharing of public addresses among more systems. The most effective solution is called network address translation (NAT), defined in the request for comments 1631 (RFC 1631).
NAT is a special type of router that has several different implementations. One popular method of implementation allows for the use of special, unroutable IP addresses on private or internal networks. The private addresses are translated to a public host address, which allows communication over the Internet. Three blocks of the unroutable, or private, IP addresses are defined in RFC 1597 and RFC 1918. The private addresses are reserved by the Internet Assigned Numbers Authority (I AN A), the organization that is responsible for all IP addresses. The private addresses are represented in Classless Inter-Domain Routing (CIDR) notation as:
- 10.0.0.0/8
- 172.16.0.0/12
- 192.168.0.0/16
These address blocks cannot communicate directly with public addresses on the Internet and must be translated.
NAT utilizes a mechanism in the Transmission Control Protocol/Internet Protocol (TCP/IP) stack called multiplexing to enable these private addresses to establish communication over the Internet. Multiplexing makes it possible for a single device to establish and maintain several simultaneous connections with one or more hosts using different TCP and User Datagram Protocol (UDP) ports. This architecture allows an implementation where a single public IP address can service the needs of an entire network of hosts, a many-to-one relationship.
NAT routers keep a table of internal address and port combinations, as well as the public (global) IP address and port used to establish the remote connection. External hosts do not see the internal address, but instead use the public IP address to respond to requests. When responses are sent back to the external IP address and port of the NAT router, it translates the response and relays it back to the internal address and port that originated the request.
Firewalls are Protocol layer rules engines. A firewall can be hardware or software based, and many routers include basic firewall functionality as an additional feature. A typical firewall provides a list of rules that are evaluated sequentially against the header data in the packet being processed. As each rule is examined against the packet header, the packet will be blocked, or the next rule will be evaluated. This process continues until the packet is blocked or all rules have been examined, in which case the packet is forwarded.
A proxy server is similar to a firewall, but it works at the Application layer. Proxy servers have packet-filtering features. Packet filtering allows examination of the actual data being transmitted within the packet itself. Packet filters are available on Windows XP, Windows 2000, and Windows Server 2003 products as part of the advanced features of the TCP/IP configuration. However, because Skype encrypts the data it transmits, packet filtering is an ineffective means of managing Skype traffic. Proxy servers handle the requests for each protocol, whereas firewalls merely forward the traffic. If the proxy server is disabled, no traffic is allowed to pass. If you disable a firewall, you are turning off all rules processing and allowing all traffic to pass, which is not a recommended practice.
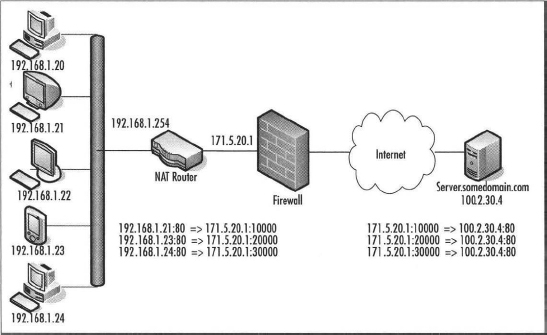
In the preceding diagram, a single external IP address is exposed to the Internet. When hosts on the private network make a request, the following occurs:
- The host initiates a request for the remote destination address and port.
- Since the address is remote, the router handles the request.
- The NAT router adds the entry for the internal host IP address and port to the translation table.
- The NAT router assigns a new port on the external interface IP address for the internal client and adds it to the translation table.
- The NAT router then initiates a connection to the remote host on the external network, through the firewall, substituting a new source port and IP address in the IP packet header.
- The remote host responds to the request to the external address and port.
- The firewall compares the IP address and port with the list of firewall rules. If the IP address passes the IP address test, the port is checked. For Skype, this would be a UDP port, or if UDP is blocked, TCP port 443 or TCP port 80.
- The router uses the translation table to translate the response from the remote host from the external address and port to the original internal address and port of the host that initiated the request.
Home Users
We strongly recommended that home users obtain a basic peer-to-peer-friendly, broadband router with firewall capabilities. In addition to a hardware-based router/firewall, you should always use a software-based firewall on each client machine. Windows XP has built-in firewall software that is enabled by default after you install Service Pack 2. Other options for software-based firewalls include products by McAfee, Symantec, and Zone Alarm. Skype should work right out of the gate on most home networks without requiring any further configuration. For home users, no modification is needed.
Later in this chapter, we discuss how to improve the quality of the communication, which could require minor configuration settings on your firewall.
Small to Medium-Sized Businesses
Small to medium-sized businesses must use discretion to determine whether to use a simple implementation, as discussed for home users, or to provide a more robust firewall solution, such as the Symantec Firewall/VPN Appliance, Cisco Pix, or other SOHO solution. Regardless, we suggest that small and medium-sized businesses use software-based firewalls on each network client to provide an additional layer of security.
Large Corporations
Larger corporations must ensure that the many routers used on the LAN allow Skype traffic over UDP to pass to other clients on the LAN if they want to use Skype effectively.
To better understand how Skype communicates, you need to get a picture of how the Skype network is organized. There are three basic roles in the Skype communication infrastructure. The roles consist of the following:
- Skype client or peer
- Supernodes
- Login servers
A Skype client is your computer running the Skype software. Supernodes are just Skype peer nodes that are not behind a restrictive firewall or a NAT router, and which therefore have unrestricted access to the Internet. Supernodes come and go depending on the needs of the overall network. Any Skype client node can become a supernode if it is not behind a NAT router or blocking firewall and has sufficient CPU and bandwidth capacity.
Understanding the Basics … Avoid Becoming a Supernode
To prevent a Skype client from becoming a supernode, all that is required is for the client to be behind a NAT router or a restrictive firewall (hardware or software).
If a Skype client is behind a NAT router or firewall, the Skype client cannot establish a direct connection to another peer. In these situations, the supernode peers act as relaying agents to help Skype peers behind firewalls or NAT routers establish connections to other peers that are behind firewalls or NAT routers. Skype peers tend to connect to supernodes that are in relative proximity to their locations on the Internet. By connecting to nearby supernodes, Skype reduces utilization and decreases the latency in response times, thus providing a fast and scalable communication network.
Understanding the Basics …
Avoid Relayed Calls or File Transfers
To prevent a Skype call or file transfer from being relayed, the firewall or NAT router must allow a P2P connection.
When Skype starts, it determines whether the client is behind a firewall or NAT router. If there is a firewall or NAT router, Skype determines the best method for communication via the firewall or NAT router using various UDP mechanisms. If no UDP ports are open, Skype will attempt to use TCP port 80, then TCP Port 443. Refer to the basic topology to get a picture of what happens next.
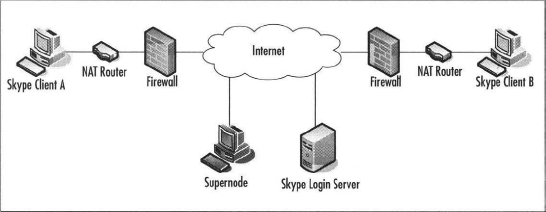
After Skype Client A determines how to navigate the firewall or NAT router, Skype contacts a supernode peer from its supernode list to attempt to log in. If for some reason there are no supernodes listed for the client, the client attempts to log in to the Skype login server. Once the client logs in, the supernode list may be updated with the current active list of supernodes.
Once the connection is established, you can place a call, begin to instant message, or transfer a file. The call starts with a search of the Skype Global Index to locate the target Skype user. Skype Client B will follow the same process to log in. If the target user, Skype Client B, is behind a firewall or non-P2P-friendly device, the supernode acts as the liaison to direct traffic from client A to Client B and vice versa, thus allowing Skype Clients A and B to find and communicate with each other using Skype Clients as relay nodes.
What You Need to Know about Configuring Your Network Devices
We’ll now discuss configuring network devices in various environments.
Home Users or Businesses Using a DSL/Cable Router And No Firewall
To use Skype typical home users will not need to configure anything on their DSL/Cable routers with or without wireless unless they have an older DSL/Cable router that is not P2P friendly. Running NAT Check, discussed later in this chapter, and enabling the Technical Information in Skype’s Advanced options will help you determine if your router is capable of a Skype P2P connection.
Small to Large Company Firewall Users
To provide the best performance on your network, you will need to tune your network to optimize handling of the Skype traffic. Skype leverages the use of UDP extensively to provide the best possible connection quality with its peers. The NAT translation table is a volatile table that ages old connections to free up room in the routing device’s buffer for new connections.
It is important that the NAT routers hold the definition for UDP datagrams sent from the internal network for at least 30 seconds. The delay ensures that there is ample time provided for a response to the original request initiated from the client. The translation table should consistently map the internal host address and port number for UDP traffic in order to be reliably translated from the external address and port used to establish the communication. UDP has very little overhead, but it is prone to loss because it is not guaranteed to be delivered to the destination. Because it has little overhead, UDP is a faster method for communications.
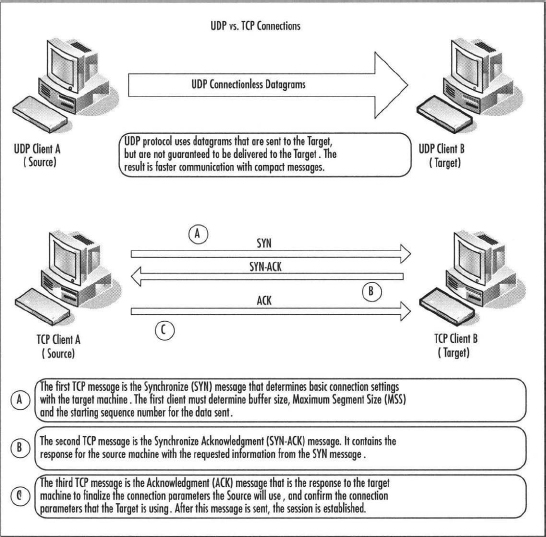
TCP and UDP Primer
TCP requires a threeway handshake to verify that data reaches its destination, whereas UDP just sends that data, and does not require acknowledgment of delivery. Because UDP does not require all of the overhead in the message structure, the messages are smaller, and UDP headers are always the same size. The UDP message structure makes the delivery much faster. Establishing communication sessions over TCP takes three trips instead of the one trip UDP requires. The TCP headers are much larger and vary in size, so there is more overhead to process each TCP message as well.
NAT vs. a Firewall
Remember, a NAT device just translates many internal IP addresses to one or more external routable Internet addresses. A firewall can also provide NAT functionality and includes additional intelligence to apply rules to the traffic that passes through the firewall. NAT devices such as a DSL/cable router may or may not have firewall functionality.
Skype also recommends that the firewall or Internet gateway support IP packet fragmentation and reassembly. Fragmenting the packets allows the stream of data to be broken into smaller packets that can be sent simultaneously over multiple ports to the destination. This packet fragmentation can dramatically improve quality and performance by allowing higher throughput, which in turn allows for more effective bandwidth. Some firewalls detect this type of parallel UDP communication incorrectly as port scanning and will block the host traffic. The result could be a degradation of Skype performance.
Skype references a tool called NAT Check by Bryan Ford. The tool can be located at http://midcom-p2p.sourceforge.net.
The tool can be used to determine how P2P friendly your network is. Ford has described the details on UDP communications over the Internet using NAT in an Internet draft. The paper is located at http://mirrors.isc.org/pub/www.watersprings.org/pub/id/draft-ford-natp2p-00.txt.
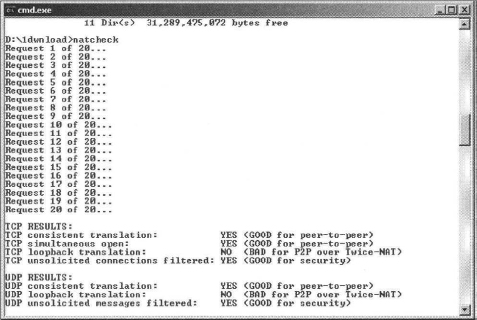
The following example shows the output from NAT Check for a relayed call:
Ports Required for Skype
We’ll now discuss the ports that are required to use Skype.
Home Users or Businesses
Using a DSL/Cable Router and No Firewall
To use Skype, typical home users will not need to configure anything on their DSL/cable routers or within the Skype software.
Small to Large Company Firewall Users
Skype uses UDP and TCP to communicate with other Skype clients. UDP is primarily used to establish connectivity and perform global directory searches. If the UDP ports above 1024 are open outbound, and you allow UDP replies to return through the firewall, you can improve Skype’s voice quality and performance. Opening UDP ports could allow peers on your network to connect more efficiently by providing closer neighbors on the P2P network, thus reducing latency and improving call quality. Allowing more UDP ports also prevents internal contention of port translation in the NAT translation table.
In a perfect world, all outgoing TCP ports would be open through the firewall or Internet gateway. If it is not possible to open all outgoing ports, TCP port 80 should be opened. Using port 80 is a standard practice. When Skype attempts to log on, it first tries to connect using random ports. If Skype cannot connect, it attempts to connect via port 80. If port 80 cannot be opened, Skype attempts to use port 443. There is no guarantee that Skype will work through port 80 if the firewall or proxy server is restricting traffic to the HTTP. By restricting traffic to HTTP, the proxy server or firewall can scan the packets to ensure that the data is actually HTTP data. Skype does not use HTTP and will not function correctly through port 80 if traffic is restricted to HTTP traffic. If you receive errors #1101, #1102, or #1103 the firewall may be blocking port 80.
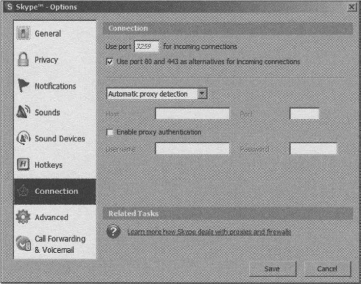
When Skype installs, it will select a random UDP port to communicate. This port setting is found in the Connection tab under Options and is an adjustable setting and stored in the shared.xml file on each computer and could be set the same for all users of Skype. If you want to avoid relayed Skype calls and relayed file transfers, you can open up the UDP port on your firewall that is specified in Skype to allow for better voice call quality and faster file transfers.
Understand that opening these UDP ports changes the normal corporate security policy, and proper approval and risks associated with opening anything on your firewall should be weighed prior to opening these settings. Discuss this issue thoroughly with your information security team on the impacts and what additional layers of security could be implemented to mitigate any risks, such as enabling a client-side personal firewall solution discussed earlier in this chapter. You could allow TCP and/or UDP inbound on the ports listed in Skype options for all clients internal to the firewall. If necessary, Skype will use TCP ports 80 and 443, respectively, to communicate with other Skype peers, and this will create relayed Skype calls and slow file transfers.
In a larger network, you can control the port for incoming connections by modifying Skype’s shared.xml file in the following location:
- <Drive>Documents and Settings<UserName>Application DataSkype folder
Using a text editor, find the <ListeningPort>nnnn</ListeningPort> entry of the shared.xml file, where ‘nnnn’ is the random port number that Skype chose when it was initially installed. By configuring all users to use the same UDP port, you can improve the quality of Skype conversations by opening a single inbound UDP port, if your network security policy permits this. If the traffic inbound on that port is high, you could logically segment the traffic by setting different groups of users to use a specific UDP port and opening multiple UDP ports inbound, while still maintaining some control over what ports are opened and to whom. Visit Dan Douglass’s Web site at the following URL for scripts and utilities to help modify the shared.xml setting in a business environment: www.codehatchery.com/skype.html.
Microsoft Windows Active Directory
In a typical Windows Active Directory-based enterprise, with clients running Windows XP Service Pack 2, you can set a Group Policy that allows you to enable the Skype traffic through the Windows Firewall on all client machines with little effort. This can be achieved via the following steps:
1.Open the Group Policy Object Editor console on the Active Directory Domain controller.
2. Locate the Group Policy setting found in Computer ConfigurationAdministrative TemplatesNetworkNetwork ConnectionsWindows FirewallStandard Profile.
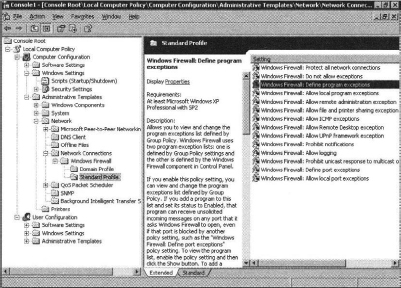
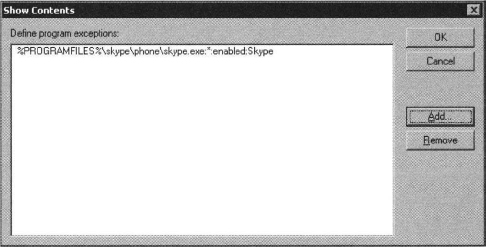
3. Select the Policy Setting for Windows Firewall to enable the Define program exceptions policy.
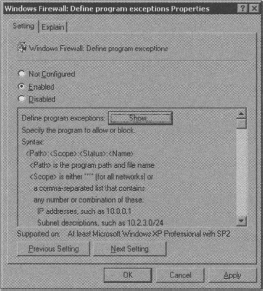
4. Next, click the Show Button that was enabled by the previous step.
5. Add a definition for a Program Exception as %PROGRAMFILES%skypephoneskype.exe:*:enabled:Skype and then click OK.
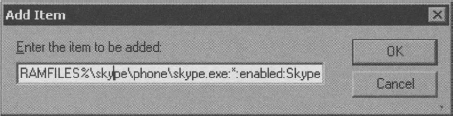
6. Click OK to close the Show Contents dialog box, then click the OK button to close the Windows Firewall: Define program exceptions Properties dialog box.
7. Allow time for the Group Policy to be refreshed. The time varies depending on the network settings. Allowing exceptions for Skype and opening up the recommended ports make it easier for Skype to establish reliable communications outside of your network. Other products, such as Norton Internet Security, McAfee Firewall Pro, and Zone Alarm Pro, have similar functionality. Visit Skype’s Web site at http://web.skype.com/help_firewalls.html for the specific configuration of your product.
The same option can also be manually configured on each workstation in the enterprise by using the Windows Firewall applet in Control Panel.
- Open Control Panel and double-click the Windows Firewall icon.
- Click the Exceptions tab.
- Tick the box next to Skype.
Using Proxy Servers and Skype
Many popular proxy servers are available on the market today. Skype supports HTTPS, SSL, and SOCKS5 proxy standards. Skype can optionally include authentication over proxies if the proxy server requires it. On Windows clients, Skype automatically uses the connection settings in Internet Explorer to identify the proxy settings that may be defined for that user on that computer. It is possible for the user to set Skype to use a manual configuration in the Tools menu, Options, and Connection tab settings. See Chapter 11 “Setting Up Skype in the Workplace” for tips on identifying your proxy server information using the netstat utility.
If you are using a SOCKS5 proxy server, it must allow unrestricted connections to the ports discussed in the “Ports Required for Skype” section of this chapter. Most proxy server solutions provide packet-filtering features. As previously mentioned, enabling packet filtering and restricting traffic over port 80 to only HTTP could cause communication problems for Skype.
Wireless Communications
Many companies implement a wireless network, preferably using 802.11G, that directly connects to the Internet. If you want to then connect to company resources, you would VPN back into the corporate network just as you would from home or a hotel over the wireless network. The wireless network could allow for fewer restrictions on traffic for wireless clients while still allowing for stricter security on the wired devices. Refer to Chapters 2 and 10 for more information on wireless communication with Skype. You should also read the benchmark documents located at the Center For Internet Wireless Benchmarks at the following url: http://cisecurity.org/bench_wireless.html. There you will find valuable information on implementing a wireless infrastructure in a secure network enterprise.
If you are experiencing, high latency or poor voice quality with Skype, you can troubleshoot your connection quality by using NAT Check or Skype’s Display Technical Call info feature found in the Advanced options tab. To enable the tech support feature or edit the Config.xml file manually:
- Exit Skype.
- Locate the Config.xml file located in the <Drive>Documents and Settings<User Name>Application DataSkype<Skype user name> folder and open it with Notepad.exe or a similar text editor.
- Use the ‘find’ capability to locate the setting </DisplayCallInfo>0</DisplayCallInfo>
- Change the value from 0 to 1 and save the file.
- Launch Skype.
Visit Dan Douglass’s Web site at the following URL for scripts and utilities to modify the config.xml file setting in a business environment: www.codehatchery.com/skype.html.
Once you have enabled the Display Technical call info feature, you can make a test call to the Skype Test Call user. Once you have established the call, simply hover the mouse cursor over the user’s avatar (picture), and you will see a tooltip-style popup with connection information:

Note that in this scenario, the relays count is 0 and the roundtrip time is 105ms (1000ms = 1 second). Since the Skype answering machine is open, the connection is very clean, and there is very little latency.
Display Technical Call Information
The following is detailed information about the Technical Call Information popup items shown in the preceding and following examples. An overview of this information is provided in the section titled “Using Skype’s Technical Call Information” in Chapter 6.
Call Status
- 0 = Hosting conference.
- 1 = ROUTING - call is currently being routed.
- 2 EARLYMEDIA - with the pstn there is possibility that before the call is actually established, the early media is being played. For example, it can be a calling tone, or it can be some waiting message (all operators are busy, hold on for a sec) etc.
- ?? FAILED-call failed. Try to get FAILUREREASON for more information.
- 3 = RINGING - currently ringing.
- 4 = INPROGRESS - call is in progress.
- 5 = ONHOLD - call is placed on hold by you.
- ?? FINISHED - call is finished.
- ?? MISSED - call was missed.
- 8 = REFUSED - call was refused.
- 8 = BUSY - destination was busy i.e. pressed hang up button.
- 10 = ONHOLD - call is placed on hold by other party.
- 13 = CANCELED (Protocol 2)
- ObjID: Ignore this information as it is not important.
- Codec: ISAC is most commonly used (G729 and iLBC are also possible)
- Jitter: Network administrators need to look at jitter. Jitter is the variation in the time between each of the delivered packets of data arriving from the source to the destination. This could indicate a bandwidth bottleneck or heavy traffic from the source to destination causing some packets to arrive sooner than others. The common method for reducing jitter is to buffer data at the destination.
- Packet Loss: Network administrators need to be aware of packet loss. This is the total percentage of the packets of data that don’t make it to or from each party in the conversation. This should be low, but will be something if you are using UDP, since delivery is not guaranteed.
- Send packet loss: Network administrators should pay attention to this setting. This indicates how much data is not making it to the destination party in the call. If the Send packet loss is high, it means that something is causing the packets from getting to the remote client.
- Recv packet loss: Network administrators should pay attention to this setting. This indicates how much data is not making it from the other party in the call. If the Receive packet loss is high, it means that something is preventing the packets from getting to you from the remote client.
- Roundtrip: Normal users and Network administrators can get information from this. The higher the number is, the longer it takes for your voice to get to the other party and back. This should be low, and anything about 300ms starts to get choppy, reducing call quality. Look at SessionOut and SessionIN, or run NAT Check to determine why you are relaying.
- BM: This is related to the bandwidth and quality of the audio and is not important.
- SessionOut: Network administrators should look at this if roundtrip values are high. This should say UDP. If it says TCP or RELAY_UDP, then you are not operating at the best performance. In this case look at UDP status remote. If it says remote:Bad, then the remote party is behind a firewall and cannot receive UDP traffic.
- SessionIn: Network administrators should look at this if roundtrip values are high. This should say UDP. If it says TCP, RELAY_TCP, or RELAY_UDP you are not operating at the best performance. In this case look at UDP status local. If it says local:Bad, you could, at your discretion, open up the UDP port as discussed earlier in this chapter to allow inbound UDP traffic.
- Relays: Ideally the relay count is zero (0), and will be when checking Skype voicemail. When relaying is in effect the count will almost always be four (4), but you may see a lower number during the time that the relay connections are being established.
- UDP status: should always be local:Good remote:Good. If either are Bad, look at SessionIn/SessionOut to remedy.
- CPU usage: 35.8% 13.4% Total CPU usage of each processor by all running applications on the local machine. If this is too high, then the machine may be too overloaded to allow Skype to operate efficiently. Other applications will most likely be suffering as well.
The next example is a call to a user on large corporate network where no inbound UDP is allowed back in through the firewall, and there is a very complex network infrastructure.
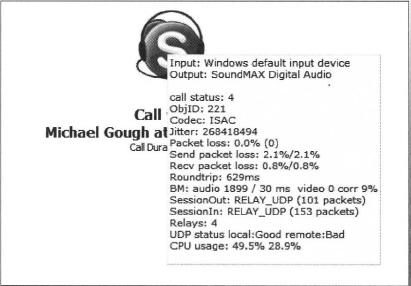
Note the difference in the SessionOut and SessionIn results. RELAY_UDP, and the UDP status remote:Bad show us that the remote location is the problem, and that a relay node is being used to carry UDP traffic for each of the clients. The result of the relays is the long roundtrip time of 629ms, and therefore, there is a delay in transmitting the voice data to the remote client. Basically, it takes more than half a second for everything you say to get to the remote client, so the conversation is choppy and degraded. To improve this connection, the callers can use NAT Check to see if they are able to use UDP and troubleshoot the connection. If it is possible to open the UDP port inbound to the remote client in this scenario, the sessions can use a direct UDP or peer-to-peer connection, and the communication will be improve almost tenfold. See the following example, to the same caller, without the firewall restrictions:
To summarize, if you have a bad connection, each client can run NAT Check and the Display Technical info to see who is having difficulty communicating. The findings can be confirmed with the configuration demonstrated in the previous section. To correct the issue, determine the UDP port the trouble client is listening on. Open that port inbound by defining a firewall rule. The rule should be specific to the client, so it might be something like Allow: WAN * to LAN 192.169.1.21 UDP: 3259, which allows all WAN IP addresses to communicate inbound to the private LAN address 192.168.1.21 over UDP port 3259.
Small to Large Companies
In most large companies, this will not be feasible and may possibly be against the corporate security policy and allowable network practices, but this does remain an option for small to medium-sized businesses that desire better communication quality and have the flexibility to modify their firewall rules. Some firewalls allow rules to be enabled during a specific time frame, and outside of that time window, the rule is disabled. If you wish to limit the use of Skype to only off-business hours, this type of feature would provide better security than leaving the port open all of the time.With any modification to your firewall rules, be sure to check your corporate security policy and with corporate security and your network team to gain approval and to understand the potential risks that are associated with opening any ports on a firewall to an internal client. Additional layers of security should be implemented if this configuration is to be used. If any peer-to-peer communication is allowed, it is recommended that the clients have a personal firewall solution to further protect the systems from malicious activity.
How to Block Skype in the Enterprise
From a security or network administrator’s point of view, the very same features that make Skype connect reliably through a restrictive firewall present a challenge to preventing or blocking Skype traffic on a network. Skype is very robust and can function with access to only port 80. Most corporations allow outbound Web traffic, so port 80 (HTTP) must remain open. Port 443 is the SSL port (HTTPS), and secure Web sites require this port to remain open. It is not as simple as blocking ports to prevent Skype from functioning.
Several tasks must be completed to block Skype in your enterprise. The first step is to block access to the Skype downloads to prevent the executable from even being installed on your client machines. This practice is referred to as black listing. This step is not entirely effective by itself, since some users might already have the Skype client installed or could bring the installation package from home on a CD or thumb/flash drive.
It is good practice to prevent unnecessary applications from accessing the Internet. The best way to achieve that is by blocking all ports on the firewall and then selectively allowing known traffic to pass, the “deny all unless explicitly allowed” mentality. In addition, you may choose to restrict access to all Internet sites except those that have been approved by your organization. This is referred to as white listing, and although it requires more maintenance, it is much more secure.
Another method used to prevent communication over the Internet is to use packet filters. Packet filters examine the data inside the headers of transmitted packets. This information can be used to create rules to dump messages that contain headers that meet the filter criteria. Unfortunately, Skype data is encrypted, so packet filters are unable to examine the information in the data packets; therefore, packet filtering is useless. However, a new hardware device is purported to identify the signature of Skype communication and block Skype traffic based on that identification.
In a corporate enterprise environment, you may have other software solutions that allow the use of application filters on the desktops. This is another effective way to block Skype. The method of policies depends on the platform, but essentially, the concept is the same. When a user attempts to execute a program that is defined as disallowed, the process that monitors the client will prevent the program from executing. An example of this would be to use Microsoft Systems Management Server and define a restriction on the Skype.exe executable. Network Associates and Symantec have similar features built in to their groupware products.
Skype is very effective at finding ways to communicate with other Skype peers. There is no straightforward way to block Skype in the enterprise. The most effective method is to prevent the program from running at all or scan for it on all systems that are not approved and delete it from each system.
Endnote
1. “Number of Hosts Advertised in the DNS.” Internet Domain Survey, July 2005, www.isc.org (accessed October 4, 2005)