Chapter 1
Client-Side Attacks Defined
Information in this chapter:
One of the bigger threats that users will face today is client-side attacks that expose the vulnerability of the end user and his or her system. Over the last five years the amount of client-side attacks has increased dramatically leading to a statement by the SANS Institute that this type of attack represents historically one of the most critical Internet security vulnerabilities in existence.
In the past attackers wishing to cause harm, damage, or expose sensitive data would generally go after the servers themselves using a class of attacks known collectively as server-side attacks. These attacks were successful because in the past, the servers themselves were not as well defended as they are today. With new security advances, methodologies and processes, this is no longer the case. The server-side attack is now severely limited by security professionals putting an enhanced focus on edge security, securing the network and vendors of products writing and producing better products for safeguarding key systems. Because the attack vector has been protected, hackers and attackers had to find a new route in.
Since the server-side (and in adversely the network-side) became the focus and were better protected, the applications used on the servers and the systems in which use the applications became the new target. In sum, applications that exist on the server-side and the vulnerabilities associated with them are better understood and defended, so attackers have shifted their focus to the desktop environment and the weaknesses found there.
Whereas server-side attacks seek to compromise and breach the data and applications that are present on a server, client-side attacks specifically target the software on the desktop itself. Applications such as web browsers, media players, email clients, office suites, and other such applications are all prime targets for an attacker. This also does not encompass many of the in-house developed applications that are widely used in many organizations worldwide. Home-grown or applications built in-house add other items to the mix due to the fact that applications that fit into this category may not undergo any sort of formal security testing. It also doesn’t take into account that a server system is easier to patch, protect and monitor then the many clients that attach to it as well as the even more diverse operating systems that are used. Multiply that by the amount of different applications used and you can see that the problem grows exponentially making this a difficult problem to solve. The wide and diverse range of software present on the desktop in an organization presents a large target for attackers and a major concern for the security professional. In fact for the security professional overlooking the client-side attack is an easy way to miss one of the single most dangerous mechanisms for impacting security in an organization. Figure 1.1 shows an example of a typical client-side attack.

Figure 1.1 An Example of a Typical Client-Side Attack
Note
Servers in the context of this text will refer to the environment that is hosted on a specialized system designed to service users and respond to requests of various types. The server environment can and does include server based applications such as those that provide streaming audio and video, serve documents, and perform ecommerce functions to name just a few. While servers will be covered in this text at various points they are not the main focus of this text as our intention is to focus on attacks on the client-side. The server-side environment represents a tremendous level of complexity and other issues that exceed the scope of this book and therefore will only be covered as they relate to client-side attacks.
In this book we will examine what constitutes a client-side attack, the different types of attacks, how they work, and how to defend against them in the real world. While every type of attack that is available cannot be covered in this text, we will review the most common. In advanced chapters we will highlight more complex attacks. By learning about the most common and more complex attacks, you will gain a better understanding of how these attacks work and in turn be able to protect against them more effectively in the future. It is also important to note that new security flaws are found each day as more and more applications are upgraded, rolled out and created (see Figure 1.2).
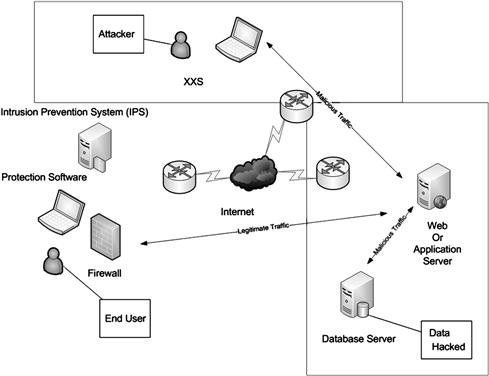
Figure 1.2 An Example of a Cross-Site Scripting (XSS)
Note
In this text we will use both terms “client” and “user” to refer to the recipient on the other side of the connection from the server. In the context of this book “client” shall refer to the system itself to include the carbon-based element operating it while “user” will refer to the individual alone that is operating the computer system. While both the “client” and “user” can be and are victims of attacks both can be targeted in different ways which will be illustrated throughout this text.
Client-Side Attacks: An Overview
While we will cover more about what constitutes a client-side attack in Chapter 2, Chapter 1 provides a basic overview. We will then move on to cover attacks in more detail in later chapters. Later chapters will explain more in depth why the client is susceptible to attacks and how the attacker is able to manipulate the system so easily, whether it be a code flaw or lack of security applied to the operating system as example. It is important for us to first take a high level look at these classes of attacks and what makes them possible. In order to better understand client-side attacks it is worthwhile where applicable to compare and contrast them with their well-known cousins known as server-side attacks (see Figure 1.3).

Figure 1.3 Basic Security Architecture
As mentioned previously attackers have traditionally concentrated their attacks on the server-side and the applications, data, and services hosted there. During normal operation a server-side application and the server itself will expose several types of services that will vary depending on the intended role of the server (i.e. document management or streaming video). Each service that a server exposes to the world is one more potential target that an attacker can exploit for whatever purpose they may have in mind. Even with a simple web-server that hosts static content the possibility of attack is present as there are services running that can be exploited. Add to a web-server the ability to host dynamic content such as Java Server Pages (JSP), Active Server Pages (ASP), or even Hypertext Preprocessor (PHP) and the situation gets even worse as even more services with their potential vulnerabilities are layered upon one another. These server-side scripting languages are often used provide dynamic content are generally embedded directly into the HTML code used to produce the pages you view, which also run scripts that could execute commands as an example (see Figure 1.4).
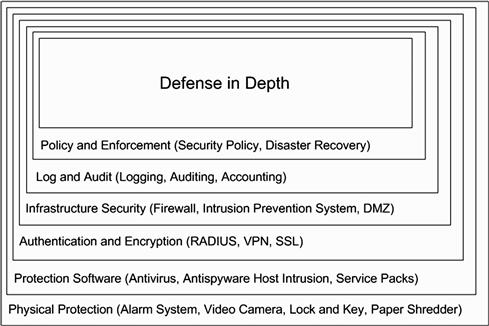
Figure 1.4 Defense in Depth
Note
Remember that even though this book focuses on the client-side attacks it is important to note that server-side attacks are still of strategic value and depending on their desired outcome an attacker may opt to use server-side attacks instead. For example, attacks such as format string, input validation and others may yield useful info from a victim that client-side attacks cannot achieve successfully. Other attacks such as the well-known SQL injection have client-side counterparts that are similar in nature, but achieve different results depending on whether the target is a client or server. Additionally modern technologies such as Google Gears and HTML 5 have not only made the web a more exciting place, but they have also made previous attacks more dangerous and likely.
Never forget that an attacker will typically have multiple tricks in their toolkit and will use whatever is perceived to get the best results at a given time. It is for this reason that you must always properly assess your vulnerabilities and put measures in place to mitigate the risk accordingly.
The list of potential vulnerabilities available on a server and its services is a long one, but some of the more common ones are:
• Malicious HTTP requests: This includes improperly formed or what are known as illegal arguments in an HTTP request. These are generally executed to trick an end user into thinking they are accessing legitimate code, which in reality malicious code (malcode) is being “smuggled” into the equation. HTTP Request Smuggling (or HRS) is used between a client and an application server and commonly executed when there is a proxy system in between.
• Buffer overflows: Vulnerabilities of this type are common in software and regularly exploited by savvy attackers. These are generally executed to produce a Denial-of-Service (DoS) attack to prevent legitimate connections from taking place by flooding buffers with bogus requests.
• Scripting errors and attacks: As will be introduced chapter 2, scripting errors take advantage of handling or coding errors to enact an attack against a client. This can be done via scripting languages such as JavaScript, VBScript, Flash scripting, and others. Cross-site scripting (XSS) is commonly used to bypass security controls by injecting the harmful content on the client-side or end user’s web browser.
• CGI errors and attacks: CGI or Common Gateway Interface programs run on the server, but through clever manipulation on the attacker’s part it is possible to target and compromise a client. These are commonly used to run scripts that are harmful to the client accessing the server.
• Unchecked user input: Malicious actions of this type take place when information that is gained does not undergo any rigorous validation to ensure that it is true and correct.
• Misconfiguration: Misconfigured software that does not have basic steps done to ensure that it is configured to be safe and secure regularly lead to a high number of security incidents with both server and client-side environments. Typically this problem can be the result of improper training or ignorance on the system owner’s behalf leading to problems later.
• Default settings: Leaving the settings in place that come with software when it is “shipped from the factory” has been shown to lead to security incidents as attackers can easily determine and take advantage of well-known and documented defaults in software. Today as more and more security flaws take the spotlight, leaving a system or application wide-open is no longer common practice, however older software or operating system or newer ones made to be “user friendly” generally do not have tight security implemented within them.
• Revealing error messages: Error messages can be both frustrating for a user and provide a great deal of information for an attacker. Under the right conditions an error message should indicate that something unexpected has occurred while at the same time not revealing useful details to an aggressor. Under the wrong conditions an error message can easily reveal information about the configuration of a system and give an attacker pieces of information that will yield a better picture of the how vulnerable a system is.
• Design and code flaws: Design flaws are those defects that were created unintentionally during the design process of an application. These flaws exist due to an oversight during the design process or surface due to unanticipated uses of the application. Many times, the software vendor will release service packs, hotfixes, security patches and upgrades of the code to fix these design flaws but generally only after then are exploited.
Understanding the server-side attack is essential to protecting against a client-side attack because although this book covers how to secure the client, not understanding the role of the server will prevent you from understanding the entire picture of how the attack is actually generated and what you need to do to prevent it. Server-side attacks have a long history of causing problems and concerns for system administrators and companies alike. In the right hands a server-side exploit can deliver a wealth of information and control of a system to an attacker for whatever use they may have in mind. Defenses and techniques have improved dramatically over the years to protect the server from attack, but these attacks still have their place in the hacker’s arsenal (see Figure 1.5).

Figure 1.5 Client Scanning
When an attacker targets client-side applications they are specifically looking for ways to force a client to process malicious code or data from a server based application. In this way a client-side application can be provide information from a malicious server that results in some action taking place that is unintended or unexpected by the end user. It is also commonly hidden from the user. This also shows the key to client-side attacks which is to target those applications that interact with a server in some way. If this interaction is not present attacks of this type cannot take place (see Figure 1.6).
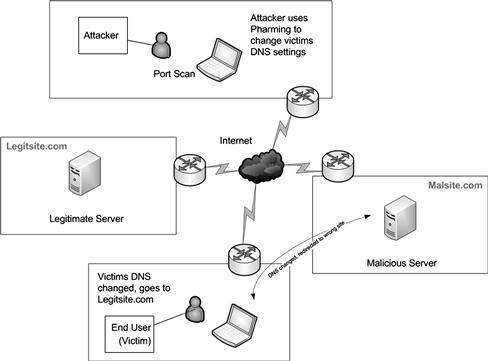
Figure 1.6 A Drive-By-Pharming Attack
Note
Just having an application installed that interacts with a server is not enough for a client-side attack to take place. For an attack to occur the interaction must be currently taking place between client and server. For example, the Windows operating system ships with a File Transfer Protocol (FTP) client used to upload and download information from a FTP server where data is stored. If this FTP client is not actively being used to upload and download information from a server, the client is not necessarily vulnerable. However if this client is currently interacting with a server and being provided information from this server it can indeed be vulnerable to a client-side attack. The same can be said for a web browser, if the web browser is not actively requesting and receiving responses from a server a client-side attack cannot take place as defined here.
Let’s examine one well-known type of client-side attack known as Cross-site scripting (XSS) and how it can be used to obtain information or alter a victim’s experience. XSS is a special form of input validation attack that, unlike other forms of input validation, targets the user of a specific application or site and not the application or site itself. An attack of this type may be used to install software such as a Trojan horse on a victim’s system with the intent of gathering information or performing some other malicious purpose. In the case of a Trojan, for example, installation may take place when a user clicks on a link or even visits a suspect site which in turn uses a language such as JavaScript to initiate the installation. If staged correctly the software can get installed on a system stealthily preventing the user from even being aware of what is occurring. The user may not even have to click on a link, the installation of software in this case could happen just by the very act of loading a web page (see Figure 1.7).
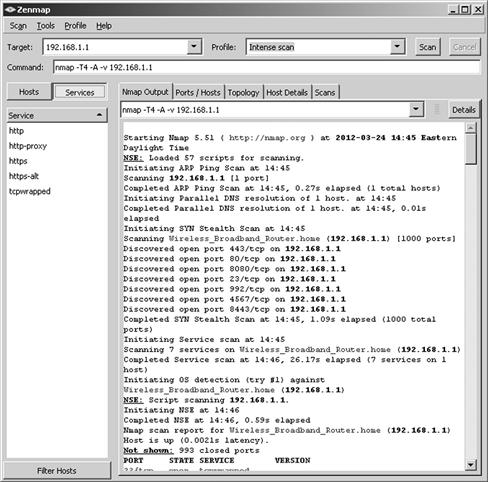
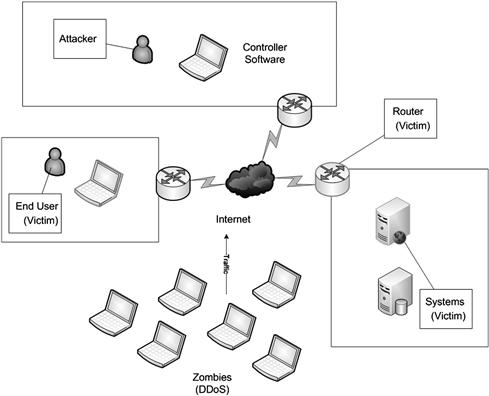
Figure 1.7 An Example of a Denial of Service Attack
Cross-site scripting is a classic scenario for client-side attacking, where the user may execute a script when opening a dynamically generated web page and the attacker is given the power to control the users session. It does this by controlling the session before the cookie expires. The user unknowingly then attaches to a server that the attacker controls. Since the attacker does this through sending the user to the server via a malicious URL, the server can then run script based hacks on the client computer through the controlled web browser.
An example of a malicious URL:
<A HREF=http://elsevier.com/form.cgi?3WE=<SCRIPT>hackers script</SCRIPT>>Click Me!</A>
If cookies are enabled and in use, the attacker can gather information from them such as cached user credentials. To protect against this attack, the producer of the code used in the dynamically created web page needs to either disable scripting in the web browser, which limits the web designer drastically. The other way to protect against this attack is by filtering and using input validation. By filtering all input, you can inspect what is being done and at minimum prevent malicious attacks from the onset. You can also use encoding. Encoding is used to replace specific tags that are deemed malicious.
If you have mostly been working with server-side attacks in the past you could say that XSS attacks are a relative of SQL injections. The difference between these types of attacks is that XSS targets the end user for any number of reasons while SQL injections seeks to alter information on the server itself, specifically databases.
Did You Know?
Cross-site request forgeries (CSRF) is a scripting attack that exploits the trust that a particular web site has with a user. With XSS, the client-side attack exploits the end user, where with CSRF the user exploits the server’s hosted site. Usually the user is “authenticated” to this site. You can try to prevent this attack with an anti-csrf token. It should be noted however that most XSS attacks can thwart this prevention method. When using XSS, the site’s token can be read in a simple response which is why this prevention method is not bulletproof. This type of attack has been seen on two of the world’s largest social media sites, Facebook and MySpace. With MySpace, the Samy worm was launched against the sites Captcha code protection method and was able to bypass it. With Facebook, anti-csrf token were easily taken from the site response.
Another good example of client-side attacks can be seen in email clients where a user receives a message with a malicious payload via a script attached or embedded into it. In these cases a user may receive an email from either a known or unknown source and open it or preview it which in turn runs the code to do whatever the attacker desired. The preview pane (as seen in versions of Microsoft Office Outlook) will automatically launch such scripts because it opens the email for you thus launching the script. Many email worms have been launched this way. An email worm, if so designed can easily attack a system or network on a number of fronts including the disabling of services, collecting of information or outright consumption of resources that are available on the system itself. Worms are one of the worst forms of malware because by nature, they spread from system to system transparently and can infect (and affect) a great number of systems in a short period of time. A typical virus and Trojan Horse attack requires the user to spread the virus manually, whereas a Worm typically spreads itself easily and quickly.
So what applications lend themselves to client-side attacks? Well the simple answer is any piece of software that interacts with a server in some manner. Applications or services that make requests to a server and/or receive responses can be sent malicious responses designed to be harmful. Although the methods of conducting a client-side attack are many, the common target is the end user system and its stored information or data. The applications used on the system are the methods and vehicles used to get to this target. Attackers use many client applications to get to the client-side data and they include:
![]() Web browsers: This includes all web browsers on the market, each are vulnerable albeit with different weaknesses. We will explore the topic of web browsers a bit more in chapter three when we examine the history and strengths and weaknesses of each browser.
Web browsers: This includes all web browsers on the market, each are vulnerable albeit with different weaknesses. We will explore the topic of web browsers a bit more in chapter three when we examine the history and strengths and weaknesses of each browser.
![]() Email clients: As these applications receive requests from a server, malicious responses can be targeted to the client. Additionally email clients can also deliver malicious code or payloads in the form of embedded scripts or email attachments.
Email clients: As these applications receive requests from a server, malicious responses can be targeted to the client. Additionally email clients can also deliver malicious code or payloads in the form of embedded scripts or email attachments.
![]() Instant messaging programs: IM applications have been subject to vulnerabilities of various types including the embedding of links in messages. When a user clicks on the link they may inadvertently open up access to their system to an attacker. Additionally IM applications allow for the transfer of files which can easily allow an attacker to install software on a victim’s system. Typically IM applications used within business organizations such as MSN, AOL and Yahoo bypass security controls implemented (such as firewalls) and allow for unfettered access from the Internet to a client-side system.
Instant messaging programs: IM applications have been subject to vulnerabilities of various types including the embedding of links in messages. When a user clicks on the link they may inadvertently open up access to their system to an attacker. Additionally IM applications allow for the transfer of files which can easily allow an attacker to install software on a victim’s system. Typically IM applications used within business organizations such as MSN, AOL and Yahoo bypass security controls implemented (such as firewalls) and allow for unfettered access from the Internet to a client-side system.
![]() Streaming multimedia players: As is seen with other client applications, media players can run malicious code on the client. Common attacks found in this category are remote code exploits and buffer overflows.
Streaming multimedia players: As is seen with other client applications, media players can run malicious code on the client. Common attacks found in this category are remote code exploits and buffer overflows.
![]() FTP Clients: Attacks that craft malicious FTP responses to a client that is requesting FTP access are possible. FTP clients are also simple to attack because they knowingly log into an FTP server that can deliver a payload that can be executed on a client. For example, a client-side end user may go to an FTP site (server) and download data that contains a payload of malicious nature, such as a Trojan Horse.
FTP Clients: Attacks that craft malicious FTP responses to a client that is requesting FTP access are possible. FTP clients are also simple to attack because they knowingly log into an FTP server that can deliver a payload that can be executed on a client. For example, a client-side end user may go to an FTP site (server) and download data that contains a payload of malicious nature, such as a Trojan Horse.
![]() Any web enabled application or service: The list of potential vulnerabilities that can be exploited on a client are numerous and resemble the ones on a server in many ways. Common examples of these types of applications and services are widgets and web apps installed on the desktop. Microsoft’s Active Desktop which eventually matured into Sidebar is a common way where web applications can be used to deliver a payload or invite attack.
Any web enabled application or service: The list of potential vulnerabilities that can be exploited on a client are numerous and resemble the ones on a server in many ways. Common examples of these types of applications and services are widgets and web apps installed on the desktop. Microsoft’s Active Desktop which eventually matured into Sidebar is a common way where web applications can be used to deliver a payload or invite attack.
Note
It is also worth noting that in addition to the technically based attacks that are mentioned here in this list the all too common social engineering type attack can be employed as well. In this type of attack a human being is manipulated to perform an action or reveal information that they otherwise should not be. Social engineering is commonly used most often, is the easiest way an attacker penetrates a system or network and is always considered first before any technical attacks are considered. What is easier? Calling a user up to get his or her credentials or writing code and trying to inject it, or become the middleman in an attack to capture this data? Another simple form of gathering data is dumpster diving which is simply digging through trash to obtain information. Shoulder surfing is a simple method of looking over one’s shoulder to obtain information. Other simple vectors of attack are password guessing to conduct a password attack. By knowing anything about the user at all (most of which can be found in a search engine), you could guess what someone is using as a credential set for authentication. There are many ways in which an attacker can garner information, the most simple way to protect against these very common attacks is to protect your identity, never post or give up information about yourself without thorough verification and use common sense and due diligence to mitigate these types of attacks.
Why Are Client-Side Attacks Successful?
So why do client-side attacks succeed? The answer is due to a combination of reasons including, but not limited to, lack of effective defenses. Clients can be protected if access from local or internal clients to locations or resources on the Internet is regulated with defenses such as firewalls or proxies. However it is important to remember that some technologies cannot provide protection unless they are combined with other powerful technologies such as an Intrusion Prevention System (IPS) that will provide protection that a firewall cannot. Even more robust filtering solutions are available, but typically these only protect a limited set of client technologies. Firewalls are used to filter and protect from the most common attacks. IPS is used as a second level of protection to filter and protect from attacks by using heuristics which is a method where signatures are downloaded to an engine in order to find anomalies in network traffic. When used together they provide “defense in depth.”
Note
Defense in depth is when many security methods are used together in conjunction to provide many levels of protection in security design. For example, if you just installed a firewall on your network or home computer, you would only have one layer or level of protection. When the firewall is used with IPS, security auditing, strong encryption, strong authentication processes, logging, anti-virus and anti-spyware applications you exponentially raise the level of security applied. You should also consider physical security which is the simple method of locking up what you wish to secure, video monitoring and alarm system.
The main reason client-side attacks are effective is one of opportunity, in this case a common lack of defenses on a client. As any security or IT professional can attest to, the number of systems that actively use protection such as anti-virus is quite low meaning that many systems are left unprotected or without adequate protection. Another common misconception is that when users are victims of client-side attacks, they thought they were protected because they installed such software. This software not only needs to be managed and monitored correctly, it also needs to be updated and run often. Sometimes this software itself is compromised given one a false sense of security.
Additionally users have been shown to possess a lack of common sense or good judgment when visiting websites or downloading software from less than reputable sources. Compare this to the server where the level of knowledge and experience by those who manage these systems is much higher meaning that protection is more than likely present and common sense being exercised. These factors as well as many others all contribute to why it is so easy for client-side attacks to take place. Inadequate protection mixed with poor judgment and/or the most protected client tricked via an amazingly deceptive form of attack make it the most common (and one of the easiest) forms of attacks today. Client-side attacks continue to become more and more problematic each day as there are more clients than servers, the clients are spread out in nature (work from home, internal and external from their places of work, and now mobile).
Note
A contributing factor to user based security issues is lack of knowledge and lack of training. The average user that engages in the downloading of content from sources such as bitTorrent doesn’t give much of a thought to the fact that they are possibly downloading infected content. Although this is a contributing factor, it still does not take away from the fact that educated users are still easily victimized. This just means that between educated and uneducated users, the problem grows exponentially.
It is because of this type of behavior that the organization and the technology industry as a whole must make better efforts in user awareness and education.
Motivations Behind Client-Side Attacks
So why the increased emphasis on attacking a client when servers that hold large amounts of data and services seemingly make more attractive targets? The answer: attackers are likely to take the so-called “path of least resistance” on a wider range of system that are protected far less than their server counterparts. Traditional routes have been increasingly unavailable due to improved server-side countermeasures, while experience has shown that end users are likely to lack basic protection in the form of protection software, have many client-based applications and services installed and missing patches or service packs. Users lacking these protective measures leave themselves open to a myriad of attacks where commonly servers are hardened and generally serving a single service or application Client-side attacks are also successful due to the fact that server-side countermeasures can be tailored to thwart certain threats while client-side measures have to take a one-size fits all approach. Just these two points alone demonstrate the fact that the odds are in the attackers favor and stacked against the client itself.
Note
Although the technical landscape seems to change in information technology, the client is not always the “fat client.” Newer server technologies such as server virtualization offer new vectors of attack. By penetrating a VMware or Hyper-V server, you can now gain access to potentially hundreds of servers all at once. Also, even though the client is easily attacked in a “client-server” model, network infrastructure is also a highly common target. Penetrating a network switch, router or wireless access point (sometimes referred to as a client), can produce more information about a companies or home network than any client or server can. Make sure that you consider all parts of your infrastructure, not just the client, nor the server.
Did You Know?
Just having countermeasures such as an anti-virus, firewall, or antispyware application does not automatically build an “impenetrable” shield around a system. Education and awareness is also key to protecting a system. A lack of ability to recognize strange behavior or visiting sites and locations that are at best questionable can easily render defenses moot. For example, a user who downloads a file and installs it from a less than reputable source may get a plethora of warnings from their antivirus and antispyware and still choose to install it. Even worse the installation of the downloaded file can unknowingly make the client system more vulnerable by disabling the defense systems and open other holes that can be later exploited by an attacker. Make sure common sense and good judgment are used as it will decrease most client-side attacks by a large percentage; however it will not stop all of them.
Another point to make about intent is that client-side attacks continue to grow because of the ability to gather and alter data for criminal purposes. Cybercrime is a common term to distinguish where technology and legal prosecution meet. Criminals may seek to deploy any one of a number of different types of malware with the intent of collecting sensitive data such as account info, credit card numbers, and other info that is commonly present on client systems. Organized crime rings can also opt to seize control of a client system with the intent of using that system’s resources to attack a third party of interest. As with any other attack, the more simple attack vector and one that leaves less of an imprint for prosecution is going to be most favored when considering “Cybercrime.” Cyber warfare is similar in that it’s not always about “stealing,” but about pure disruption and chaos to tie up systems, resources and produce damage and/or harm.
Types of Client-Side Attacks
Now that we have spoken, briefly, about what client-side attacks are, why they are carried out and why they are successful let’s take a look at some of the attacks available. This section will serve as a brief description of the types of attacks available; we will discuss some of these in depth in chapter 2 and later.
For the sake of simplicity and to better help classify the attacks let’s break the attacks into three types: attacks that effect confidentiality, integrity or availability or better known as the acronym CIA. These categories best represent what each attack can impact on a system as well as the areas that a security professional is trying to protect or defend. Keep in mind that these goals represent the very foundation of what information security is built upon and preserving these areas and keeping them in some sort of balance is what every security professional is attempting to do.
Each category can be best described in the following ways:
![]() Confidentiality: Deals with keeping information and resources secret to all but those authorized to interact with them. Those attacks that target information or resources that are restricted to use or access by a specific group or user can be thought of as confidential and should not be disclosed to those outside the group or user.
Confidentiality: Deals with keeping information and resources secret to all but those authorized to interact with them. Those attacks that target information or resources that are restricted to use or access by a specific group or user can be thought of as confidential and should not be disclosed to those outside the group or user.
![]() Integrity: Deals with keeping information in the format that it was intended to be used in. Information that is altered in any way is not considered reliable and cannot be used with any degree of confidence. Attacks in this category seek to modify data that benefit the attacker.
Integrity: Deals with keeping information in the format that it was intended to be used in. Information that is altered in any way is not considered reliable and cannot be used with any degree of confidence. Attacks in this category seek to modify data that benefit the attacker.
![]() Availability: Deals with keeping information accessible and usable at all times by those who need to access it. Attacks in this category seek to disrupt the flow or access of information by users.
Availability: Deals with keeping information accessible and usable at all times by those who need to access it. Attacks in this category seek to disrupt the flow or access of information by users.
Confidentiality Impact
Attacks that target confidentiality are concerned with gaining access to any information or resource that is supposed to be restricted to a specific party or user. For example, information such as medical records, legal records, credit card info, social security numbers, or tax records would be considered to be information that is intended to be kept private. Not surprisingly there are numerous methods by which an attacker can gain access to information that should otherwise be kept private. The following list of attacks and descriptions represents some of the attacks we will see in this book and discuss in chapters two, three, and four:
Warning
In fact some information such as patient information in countries such as the United States are protected by laws such as Health Information Portability and Accounting Act (HIPPA). As such, information of this type not only ethically but morally needs to be kept private, but legally will need to be protected.
Cookies
Cookies are text files that reside on a client which store information that is sent to the client by the server. The information in a cookie is used to store information about a session and is designed to be accessed to track the client or allow for the retrieval of information later on. Applications that use cookies such as web mail clients could have their cookies accessed so the user does not have to provide their credentials each time they would like to access their mail. Cookies contain data that can provide an attacker with information that could allow for a victim to be identified and their session taken over. If an attacker can access the cookie, unauthorized access to the mail account could be obtained as demonstrated recently by several attacks where personal information stored in cookies were stolen, attacks that we will see in Chapter 2.
AutoComplete and Browser History
One of the facts about web browsers is that they store a tremendous amount of information about one’s web activities. Each visit to a web site and the pages contained within is by default stored and recorded in the cache and history on a client system. The amount of information stored on the client can vary depending on the browser and settings involved, but the result is the same which is a goldmine of data that can be retrieved by an attacker. Under the right conditions an attacker can gain access to information including what email service or bank a user uses which can be inferred and used in subsequent attacks, such as phishing and cookie stealing attacks.
Did You Know?
Browsers intentionally store a wealth of information that we, as users, willingly provide to the application to store. Autocomplete can store information including, but not limited to, credit card info, passwords, account info and much more.
Clipboard Attacks
The clipboard is special region of memory used for short term storing of information of the type used in cut-and-paste operations. Access to the clipboard by applications varies depending on the situation. Early versions of web browsers, such as Internet Explorer provided web pages the ability to access the clipboard. In newer versions this access to the clipboard has since been restricted to only allow access if specifically granted.
Social Engineering
This client-side attack is becoming more common with almost every person who has an email address and getting an email. At some point that could lead to a phishing attack. In this type of attack the trust in a web site is used to fraudulently obtain confidential data, such as login or account credentials and bank account information. These attacks are successful due to the fact that the user is presented with a fraudulent, but highly authentic looking web site, usually via SPAM, which appears to originate from a trusted entity, such as a bank. The web site that the user is sent to however is under the control of a malicious party and when the user provides information to the web site such as personal information, the attacker will have obtained this confidential information. Sometimes you may be directed right to the malicious site, otherwise you may be redirected to a malicious site via a script.
Note
A variation of a phishing attack that is quite successful in acquiring information from end users who lack the knowledge to detect them are known as spear phishing attacks. Spear phishing attacks take place when specific individuals are targeted with the intention of gathering information from them that only they may possess; this is in opposition to normal phishing which emails out the message en masse.
An additional form of phishing goes by the term whaling which refers to the practice of targeting phishing emails towards executives or higher-ups in a company.
In both cases the victims are not chosen wholly at random rather they are chosen based on the fact that the information they have may be of greater value than others.
Client Scanning
Applications such as network and port scanners exist that can be used by a malicious web site to retrieve information about the internal network topology, such as existence of web-servers, routers, and hosts. These are tools used to map out a network, its weaknesses and entry points. In reference to client-side attacks, a scanner can be used to not only located client systems, but also find out what services are running, what hot-fixes are not installed and a plethora of other useful information.
There are many other exploits that can be covered on the client-side. For example, a simple and common exploit is running a password cracker or keylogger on the client system.
The relevance to these exploits is two-fold. First, it’s imperative to not solely focus on one attack vector, secondly it’s important to know that payloads from scripts could potentially place one of these tools directly on your client system.
Integrity Impact
Attacks that fit into this category seek to compromise components or communications generally with the goal of allowing an attacker to inject or execute arbitrary code on a client. If an attacker can successfully affect the integrity of these communications and execute the desired code it is possible to carry out a myriad of attacks that will only vary depending on the vulnerabilities presented by the operating system and environment itself. Typically actions in this category are cross-site/domain/zone scripting, drive-by-pharming, hosting of malware, and drive-by-download to name the most common. The following examples introduce some of the attacks designed to target the integrity of the client/server interaction and cause an attack.
Cross-Site/Domain/Zone Scripting
These types of attacks rely on the inherent vulnerabilities present in web pages, namely the ability to run embedded code such as JavaScript. In this attack an attacker will inject code into a web page that will execute when a user visits, downloads and runs on their system. Programming code when run in this fashion can be used to steal personal information as well as run other code arbitrarily such as remote code exploits. The vulnerability stems from the fact that certain web pages are trusted more than others in the context of the web browser allowing code to run with higher privileges.
Drive-by-Pharming
In this form of attack, a script (such as JavaScript) or applets are used commonly on easily configured and deployed broadband routers and computers to create Denial-of-Service (DoS) attacks, steal data, infect system or change name resolution settings. Pharming attacks (or DNS spoof attacks) is a form of client-side attack where the Domain Name System (DNS) settings on a victim’s system are altered or configured to point to a different set of DNS servers. The redirection may be done to send the client to a new set of servers designed to intercept their queries or to redirect them to a different host.
Malware
Malicious software (shortened to malware) is any software that causes damage or lost resources when used on any system it is purposely or inadvertently installed on. In this attack we are concerned with downloading malware specifically designed to alter the system in some way, usually via scripts from a web page visited by a client user. A typical scenario would involve, a malicious web page hosts some sort of malware and uses mass emailing, spam, social engineering or any other method to invite the user to download and execute the malware. A common example of such a technique is to use video codec that contains embedded malware, when the victim visits the site they are informed that downloading the codec is a requirement to view the material (Adult Pornography sites are a common delivery mechanism). Once the victim downloads and installs the malware, the attacker has gained control of the system. Drive-by-download versions of this attack do not even require the user to manually install anything as the malware is automatically downloaded and installed on a user’s system without their knowledge. These attacks usually trigger having a user merely visit a web page.
Availability Impact
The final category of attacks that can take place impact availability of a system and the resources it has available. Actions that can impact availability are those that cause events such as crashes, browser hijacks, Denial of Service (DoS), Distributed Denial of Service (DDoS), pop-ups, and pop-unders, and many other behaviors.
Denial-of-Service (DoS)
When a denial-of-service attack is in play it results in a total or near total depletion of resources that in turn have a detrimental impact on the service or services running. Under the right conditions this form of client-side attack could lock-up or even crash a browser and, in extreme cases, crash the operating system itself. Due to the complexities of browsers, plugins and other features that are available many vulnerabilities present themselves that allow an attacker to launch an attack that can impact availability. The distributed version of the DoS attack is the Distributed Denial of Service (DDoS) attack which is when many infected computers (called Zombies) all launch the same attack against one or most hosts to increase the load on the victim host.
Pop-Ups and Pop-Unders
Anyone who has been using the web for any amount of time has undoubtedly encountered the pop-up window and its cousin the pop-under. Pop-ups by themselves may not be a problem, but if a victim is flooded with a large number of them the situation changes as multiple pop-ups are opened on a system as each open window consumes a little bit of resources available until the system is out of resources completely. These types of attacks, known as pop-up floods are used in various advertising and other schemes to inundate the user and their system with information. While each of these pop-ups open, network and computing resources are consumed, significantly reducing the availability of the client and, in some cases crashing or locking up the browser and operating system. In other cases this type of attack can lead to attacks known as browser hijacking, in which a page cannot be browsed away from and/or pop-up cannot be closed. A commonly used script (JavaScript) would appear as:
var popunder=“http://malicious.com“
var winfeatures=”width=100,height=100,scrollbars=1,resizable=1,toolbar=1,location=1,menubar=1,status=1,directories=0”
if (document.cookie.length > 0) {
offset = document.cookie.indexOf(search)
if (offset != -1) { // if cookie exists
end = document.cookie.indexOf(”;”, offset);
returnvalue=unescape(document.cookie.substring(offset, end))
if (get_cookie(“popunder”)==’’){
document.cookie=“popunder=yes”
Did You Know?
Pop-unders are windows that are designed to open up under the browser instead of over it as a pop-up does. When a pop-under opens up under a browser it may not be seen for some time meaning that a victim will most likely see their system slowdown in increasing amounts until it is unusable.
Image Flooding
Web browsers have the ability to display many types of content including movies, animations, text, and images. Of course just loading content such as images is not a bad thing, in fact it is desirable to have these features, but if used in the wrong way the results can lead to an attack against availability. Web browsers are designed to load these resources from remote network locations, like the Internet, if a web page contains images from only a few different locations there isn’t much of an issue and, in fact, this happens all the time. Change the situation a bit and make the browser load a multitude of images from a large number of locations and a browser can quickly slowdown dramatically to the point of crashing due to the increased amount of DNS resolution requests. Taken to an extreme an attack of this type could easily choke a system and/or network with traffic bringing both to their knees.
Summary
In this chapter we briefly discussed the client-side attack and how it has become one of the bigger threats that an organization will face. This type of attack has become so common and increasingly dangerous that organizations are looking at their application portfolios and the latest vulnerabilities trying to uncover and address weaknesses.
Client-side attacks represent a shift in the way attacks have taken place adding a powerful tool for gaining information from the systems of unsuspecting victims. Client-side attacks may be selected by an attacker as a way to gain information without having to go after the more heavily defended and protected server-side applications. Users have made themselves easy prey for client-side attacks due to a lack of or poorly maintained anti-virus, firewall, or antispyware that is common in this environment.
Finally, the diverse range of applications that is present in most desktop and client environments means a large portfolio of software filled with potential vulnerabilities. Applications such as web browsers, media players, email clients, office suites and other such applications are all prime targets for an attacker wishing to cause harm. For the security professional overlooking the client-side attack is an easy way to miss one of the single most dangerous mechanisms for impacting security in an organization. In this chapter we covered the fundamental knowledge needed to understand not only how a client-side attack takes place, but why and the issues that it causes.
