Chapter 3
Protecting Web Browsers
Information in this chapter:
In this chapter we are going to take a closer look at one of the applications that is a target for client-side attacks more often than just about any other, the web browser. The web browser is a software application that has become so popular and common that it is found on just about every system in existence today across all operating systems. As a utility that is designed to access the wealth of information available on the Internet and present it to the end user the web browser has seen itself become an item that is ubiquitous and indeed considered to be a required component on any device desktop, mobile, or otherwise. This also makes it the most commonly used tool for client-side attacks. Consider the following. As we have mentioned in earlier chapters, the most common method for attacking a client from an outside source is via a web browser surfing the public Internet. Because of the free-nature of the Internet and its worldwide way of connecting people around the world, it is the most common method for conducting a client-side attack. Because we have to consider usability over security, we cannot block all HTTP traffic, nor block all scripting languages from being used. Since almost every device that accesses the Internet today uses a web browser (desktop client, mobile phones, and pads), it’s the primary target for attackers.
So how have attacks changed and how have browsers and browser manufacturers responded to the ever changing attacks? Well that is what this chapter is about, the web browser or, more specifically, the evolution of the web browser over the last few years and the features that have been added to thwart attackers along the way.
Note
This chapter is not meant to extoll the virtues of one browser over another and make a recommendation as to what is the best browser on the market. Rather this chapter is meant to discuss the history of some of the different web browsers and how they have evolved and metamorphosed to deal with changing threats and the Internet environment. As there are many browsers available we can focus on the most common select set of browsers, specifically the browsers that you are most likely to support and encounter.
Common Functions of a Web Browser
So let us first take a look at what a web browser is designed and expected to be able to do no matter the operating system or environment. First of all the web browser is designed to request, process, and render information on screen for the client. Information in a web browser is retrieved through what is commonly known as a Uniform Resource Identifier (URI) which includes the commonly known term known as the URL or Uniform Resource Locator. URLs are commonly noted in the following format:
This can also be expressed as a web address in the format:
In each of these examples http://, https://, or ftp:// represent the protocol and the remaining text represents the address or resource to be accessed. The protocol in use can vary depending on the situation and what the browser supports. Additionally browsers have the ability to access local resources through the use of the file:// switch for accessing the local file system such as with Internet Explorer.
In some situations a web browser will encounter content such as embedded links and other content that it cannot handle directly, in these situations helper or external applications come into play. Take for example links such as the mailto: link, since the browser is unable to handle this content directly it will hand the request over to the local mail application that is configured to send and receive email. Other content such as links that point to files such as PDF or doc files will be handled in much the same way as the files will be downloaded and opened in the application that is configured on the local system to process it, which in these examples would be Adobe Acrobat and Microsoft Word. In cases where a browser encounters content that it cannot process or hand over to an external application the client will be prompted to save the content to the hard drive of their system.
Warning
Since a web browser can call upon many types of external applications such as email clients, media players, and a myriad of other applications it is important to consider the weaknesses of these applications as well. Simply patching and knowing the weaknesses in a browser is a good start, but if the web browser calls upon email clients and video players and these applications have known, or unknown weaknesses that can be exploited the system is still vulnerable to some degree. Browsers tend to exist in this ecosystem of interconnected applications on just about every platform and operating system and as such care should be given to all applications that are called upon via the browser.
A common feature in every major web browser is the ability to process scripts and applets of different types. Content such as JavaScript and VBScript is able to be processed by browsers to add interactivity and richer experiences to the client. Applets such those based on ActiveX and Java are also very common on the web and can be processed by just about every major browser across every operating system. We can also factor in additional technologies such as Ajax into the mix which is supported by most major browsers as well to support dynamic experiences on the client-side.
Did you know?
Ajax is not a single technology but a group of technologies that allow for the development and deployment of interactive web applications. Ajax ties together HTML/CSS, Document Object Model (DOM), EXtensible Markup Language/EXtensible Stylesheet Language Transformations (XML/XSLT) and JavaScript. Browsers that support technologies that are part of the Ajax suite can work interactively with the server to exchange and present data dynamically to the client. As Ajax has become more popular and embraced by the web development community the amount of dynamic content present on the web has increased which of course means that attacks targeted towards content based on this suite have already appeared.
Features of Modern Browsers
Browsing and presenting content is of course the main function of a web browser, a function that all browsers have in common, but each browser offers a different feature set that sets it apart from the rest. In this section we will examine five of the major browsers on the market today and the features and security vulnerabilities that make them unique in the marketplace:
Note
Remember that the following section is not concerned with recommending one browser over another, but is concerned with comparing and contrasting each browser against one another to show their features and how they relate to client-side attacks. Each browser can be said to have its own strengths and weaknesses that set it apart from its brethren. It is up to you, as the administrator and security professional, to decide which browser is best for your own particular environment and needs.
Microsoft Internet Explorer
Internet Explorer is Microsoft’s web browser that was first introduced in 1995 as part of the Windows operating system. Internet Explorer, or IE as it is frequently called, has evolved dramatically since it was first introduced up to its current incarnation which, as of this writing, is IE 9 with version 10 in beta testing.
Internet Explorer has evolved dramatically over the years, but it can arguably be said that the browser evolved the most over its first three or four versions. During these initial releases Microsoft rapidly improved, tweaked, and modified their browser in a successful effort to overtake Netscape’s dominance of the early browser market. While features and enhancements have been added to the product since this time the initial version probably evolved the most rapidly of all the versions since. Originally, when first introduced, IE was riddled with security problems, bugs and flaws. Over the years it has been built into a security powerhouse with various settings and tools that allow for a rich yet safe surfing experience (see Figure 3.1).
Figure 3.1 Microsoft Internet Explorer
Features
As discussed earlier in the book, there is a distinct difference between usability and security. Earlier versions of IE were very lightweight because they did not require a lot to them in order to run the older web sites and content available. As more content became available and the way that content was viewed accessed and manipulated by the browser, more and more security features also needed to be developed and put in place to coincide with this rapid development. Soon, IE (like most browsers became “feature-rich” and/or “bloated” in order to function with all of the emerging web technologies, applications and security threats.
Internet Explorer today has a very large footprint and contains many features, functions and security tools in order to keep it protected. It is also tightly integrated into the operating system excluding the older integration that put it (and the OS) at risk. Today, Internet Explorer includes a rich feature set that includes, but is not limited to the following:
![]() Support for HTML version 4.01, Cascading Style Sheets 4.01, and XML.
Support for HTML version 4.01, Cascading Style Sheets 4.01, and XML.
![]() Partial support for Cascading Style Sheets Level 2 through 2.01.
Partial support for Cascading Style Sheets Level 2 through 2.01.
![]() Support for a Microsoft variation of ECMAScript called JScript.
Support for a Microsoft variation of ECMAScript called JScript.
![]() Integration with the Windows Operating System to include support for scanning and downloading of updates via the Windows Update service.
Integration with the Windows Operating System to include support for scanning and downloading of updates via the Windows Update service.
![]() Full support for ActiveX (something that will be explored in Chapter 4).
Full support for ActiveX (something that will be explored in Chapter 4).
![]() Full support for technologies such as Silverlight (a topic that will be discussed in Chapter 4).
Full support for technologies such as Silverlight (a topic that will be discussed in Chapter 4).
One of the aspects of Internet Explorer that has almost consistently met with criticism is its support, or lack thereof, of some well-established standards. Microsoft has been known to deviate from standards from time-to-time and IE is no different as IE supports a number of non-standard or proprietary extensions that add features not seen in other browsers. These extensions allow IE to display content in different and unique ways which makes for some interesting situations as content that is specifically designed to leverage these extensions will not appear correctly in other browsers. IE boasts several of these extensions that enhance or alter the behavior of technologies such as HTML and CSS.
Examples of one such feature in Internet Explorer that is non-standard is something known as the favicon feature. The favicon feature is used by IE to display an icon representing the current web site; this icon can be used to represent the website in the user’s favorite list and in their history. This feature was originally developed by Microsoft for IE, but it has since been adopted by other major browsers as well. One issue as it pertains to securing your systems against client-side attacks is that when non-standard or proprietary technologies are used, you have to be an expert in and/or specifically work with that vendor to patch up or secure against attack.
To provide security on IE, you must consider the base OS first. In Chapter 10 of this book, we will cover a great many ways you can keep your system safe as it ties in with the browser, however in sum you should always consider authentication, server certificates, and Secure Sockets Layer (SSL) as some of the methods used today to secure your web browser when surfing and accessing web content.
Did You Know?
Microsoft has had at least two different web design and development packages one of which is the well-known, but now defunct, FrontPage. FrontPage was a web design software package that allowed many individuals to make their first foray into the world of web design due to its relative ease of use which was more or less on par with using Microsoft Word or Excel. One of the problems with FrontPage however was its support for non-standard behavior and technologies which led to many cases where a page worked absolutely perfect in IE, but looked different to varying degrees in other browsers. Because of this, there were also unexpected results when publishing the web site you created to the web. Based on the older method of Microsoft’s open natured architecture, you would have to configure New Technology File System (NTFS) Access Control Lists (ACLs), or restrict access, change permissions for files and folders when using Front Page Server Extensions which hosted a large set of security problems. Worse, the platform normally ran on Microsoft’s web server called Internet Information Services (IIS) which too had a great deal of security problems itself.
More relevant to today is the foray into SharePoint Portals. This is Microsoft’s collaborative software that mirrors this same technology. So, just as FrontPage Server Extensions relied on the Windows OS and NTFS, so does SharePoint Team Services. The security of the Web file system is based on the OS while Access Control Lists (ACL) provides secure access to files and folders. In both scenarios, IE is used to connect to and access each technology.
IE, as is common in modern software applications, has a modular design which brings together several components that each offer some specific functionality. In the case of IE, and most other Windows applications, these components are actually a set of diverse DLLs or Dynamic-link libraries that interact with the main Internet Explorer process or executable known as iexplore.exe.
Warning
Developers may already be aware of this fact, but DLLs are a common filetype in the Windows operating system and are used to provide similar features across product types. A DLL that is used by one application may in fact be used by other applications as well, and quite frequently is used by multiple software packages on the same system. It is for this reason that you must consider components that are shared between Internet enabled applications as a DLL that has security vulnerability may not just effect the security of one application, but may in fact effect multiple apps.
The following files represent some of the common DLLs in use by Internet Explorer. Keep in mind that while the following list represents some of the DLLs that are present on a system it does not present them all and, in fact, the list of DLLs can vary wildly from system to system:
![]() WinInet.dll: This DLL handles the communication between the client and the server that is being accessed. Specifically this DLL handles the protocols HTTP, HTTPS and FTP for the Windows OS. This DLL is also used by other Internet enabled applications that communicate over these protocols.
WinInet.dll: This DLL handles the communication between the client and the server that is being accessed. Specifically this DLL handles the protocols HTTP, HTTPS and FTP for the Windows OS. This DLL is also used by other Internet enabled applications that communicate over these protocols.
![]() URLMon.dll: This file is responsible for managing the download of web content from web sites such as files and similar content. This DLL also works in concert with WinInet.dll to manage protocols and download of content for applications.
URLMon.dll: This file is responsible for managing the download of web content from web sites such as files and similar content. This DLL also works in concert with WinInet.dll to manage protocols and download of content for applications.
![]() MSHTML.dll: This DLL is responsible for processing and rendering content to the user. This file is the one responsible for processing HTML ad reading CSS and other information presented in a web page as returned by the web server. The MSHTML file also boasts a complete API that is accessible by developers looking to process custom content via the web browser or other applications. This file like most of the others listed here is utilized by other applications to process web requests.
MSHTML.dll: This DLL is responsible for processing and rendering content to the user. This file is the one responsible for processing HTML ad reading CSS and other information presented in a web page as returned by the web server. The MSHTML file also boasts a complete API that is accessible by developers looking to process custom content via the web browser or other applications. This file like most of the others listed here is utilized by other applications to process web requests.
![]() IEFrame.dll: The purpose of this DLL is to present the user interface for the browser as well as the accompanying windows. Only systems that have Internet Explorer 7 will contain this file as part of their installation.
IEFrame.dll: The purpose of this DLL is to present the user interface for the browser as well as the accompanying windows. Only systems that have Internet Explorer 7 will contain this file as part of their installation.
![]() BrowseUI.dll: This file handles other components such as the browser user interface, including the browser graphical enhancements and parts of the menus and toolbars.
BrowseUI.dll: This file handles other components such as the browser user interface, including the browser graphical enhancements and parts of the menus and toolbars.
![]() ShDocVw.dll: Stores and provides all navigation information and history for the web browser.
ShDocVw.dll: Stores and provides all navigation information and history for the web browser.
The main problem with all of these DLLs linked up and in use is that they open paths into and through your system when you are exploited making them targets for client-side attacks. DLL Hijacking is a common client-side exploit that manipulates the functionality of DLLs. The way Windows systems work is that they load up DLLs into%SystemRoot%/system32 as they are called and needed. Because of older system hacks, Microsoft developed the SafeDllSearchMode setting (registry value). Applications try to load a DLL as needed and if not found on the local system, will search other locations such as connected or mapped drives and shares. This is where a malicious program can hijack the DLL.
So, in sum IE is feature-rich and highly usable but still susceptible to attack either through itself and/or the underlying operating system. New features that will be covered in Chapter 6 such as the User Account Control (UAC) feature can help mitigate problems, however there are still security concerns to consider as it relates to client-side attacks.
Security
Security and Internet Explorer go hand in hand. There are many features available today to provide a higher level of security than any of the versions before it. Some common problems when using IE are, the system is using proprietary code, languages and services. Microsoft, does however make many efforts to continue a strong security posture in relation to IE and the base OS it’s installed on.
One common security issue is the file and folder structure. There are many directories, files and executables that IE uses that can be exploited. Aside from cookies (the most common), DLLs, services and so on, there are base OS files that can be used to an attackers advantage.
index.dat is one of these concerns. IE, much like other browsers, caches most content that are visited and stores the results locally for quicker access later. In IE cached content is stored in a special location known as Temporary Internet Files folder. To speed up access IE also uses a special file known as index.dat which is essentially a database that stores an index of the sites previously visited by the client. index.dat exists on every version of IE since its earliest versions and is generally a file that cannot be easily removed.
Warning
index.dat has been the focus of complaints by various user groups, privacy groups, and security professionals as it keeps a list of previously visited websites and cannot be easily deleted from a system. An attacker, under the right conditions, can access the Index.dat and retrieve a list of websites the victim has visited and carry out a successful invasion of their privacy. Using Internet Options in IE can allow a user to delete files in the temporary Internet Files folder, but the same feature cannot remove the index.dat file as it is kept open and locked by the operating system. Several third-party applications offer the ability to remove this file from a system if the user so desires (and is aware of the files existence in the first place).
In versions of IE from 7 forward the index.dat are dealt with in a more secure manner due to the browser’s new design which overwrites the file with random information designed to obliterate the information in the file.
The best way to secure IE is to secure the base OS as well as IE using the tools it comes with, additional tools and keeping the system up to date. Figure 3.2 shows the fundamental step to take in order to keep your system, as well as IE updated and secure.
Figure 3.2 Hardening the System (Microsoft Update)
Updating your system and all of its components keeps specific security patches current thus keeping your system as secure as possible.
Other IE security features are found in Table 3.1.
Table 3.1 IE 9 Security Features
| Application Reputation | Technology used for allowing an end user to make safer decisions when surfing the web. Stops malicious content more frequently. |
| ActiveX Filtering | Allows you to choose which site you want to use with ActiveX controls. You will only be able to work with ActiveX on sites you “trust” |
| SmartScreen Filter | Is used to help make a decision if a site is safe or considered malicious. It will alert you or block you from such content. |
| Tracking Protection | Online tracking is an issue today and with the use of Tracking Protection and Tracking Protection Lists you can limit exposure. |
| Better support for XSS | Cross-site scripting attacks are common and new enhancements within IE 9 help prevent these types of attacks. |
This added with all of the security features in the previous versions such as Phishing filters, content locking and trusted sites allows for a more secure surfing experience, however as history teaches us, never rest on your laurels. There would be no “new” features out if the landscape did not constantly change. Always remain vigilant when it comes to security, especially protecting the client-side of the equation.
Add-ons and Other Features
IE offers the ability to be added to and extended much like some of the other browsers on the market such as Firefox. Microsoft developed IE to expose an Application Programming Interface (API) that allows developers to design and deploy special software applets called Browser Helper Objects (BHO) that can add additional menus, functions, and other features to the product. BHOs can be used to make the browser do more than it would otherwise including the ability to process new and different types of content including custom files and data.
BHOs offer the ability to mold IE to the needs of a particular environment or need very easily, but it also poses a security risk to the client. BHOs can add all sorts of features due to the fact that by design they have complete and unrestricted access to the local system meaning that a BHO can access the local filesystem, registry, and most other parts of the system without having any reasonable checks on their access. Under the right conditions and attacker could easily create an ActiveX control (something that will be covered in depth in Chapter 4) that installs a BHO in IE and gather information or outright spy on a user reporting the information back to the attacker (see Figure 3.3).
Figure 3.3 Browser Helper Object Vulnerability
Note
BHOs are intended to allow IE to be configured and customized to meet any need that may be required. Due to the access that BHOs get a developer can easily create almost any type of applet to meet their own needs or that of their client. The inclusion of this feature was meant to allow the adding of items such as custom content handlers that can process content that is not available natively in the browser such as SVG files, Flash, or Silverlight files).
BHOs in IE are a powerful feature, but what if you want to disable a few or run without some of them permanently or temporarily? With Windows XP SP2 (service pack 2) or a newer version of the Windows OS coupled with current versions of IE installed, you can view the BHO’s that are currently installed in Internet Explorer. When you manage add-ons, you can stop bad BHO’s from being used. Other applications like BHODemon are also helpful in finding and removing malicious BHO’s.
Additionally Microsoft has added an additional mode in later versions of IE that can be thought of as a “Safe Mode” or more formally a “No Add-Ons” mode that lets IE run without any additional BHOs preventing most potential hazards from occurring.
Warning
Starting with Windows Vista Microsoft also introduced additional security features into the operating system that prevents BHOs and other content from accessing other parts of the system. In Vista and higher a “Protected Mode” is available, and configured by default, that prevents access to anything except the Temporary Internet File folder and a virtualized part of the Registry. Of course, keep in mind that this feature is only useful if it is left enabled which is a potential problem as shutting off the UAC in Windows Vista will disable this special mode.
Another common feature in IE that is of concern to security professionals is the ability for the browser to be embedded inside of other applications. By hosting the MSHTML.dll mentioned earlier in the list of DLLs a developer can host IE inside of their application providing the ability to browse the Internet within the context of their app. This ability can be helpful, but also dangerous as a user may overlook some of the basic common sense practices that they would exercise when using the browser normally simply because the embedded browser does not look like a normal browser.
In IE 7 and later an additional feature that is useful in thwarting a common form of client was introduced, the phishing filter. The phishing filter is designed to block websites that have been known to engage in phishing related activities. With this feature sites that steal information from unsuspecting users are blocked and in later version sites that also attempt to install malware are blocked as well. This is called the SmartScreen filter in IE’s most current version available.
Of course a browser can only do so much in its initial design to block behaviors that could impact security and as such IE includes a robust update capability. Present since Windows 98 and carried through in every version since is the ability for IE to download and install updates to address problems that may impact security adversely. Through use of this feature Microsoft, with due diligence from the system owner, can patch defects and close security holes that hound the OS.
Warning
Microsoft only supports the current operating system and the last two or so releases in Windows Update. Additionally only a few releases of IE are covered in Windows Update meaning if an operating system or the browser is “showing its age” updates will not be available and therefore the security risks will only increase over time.
Known Security Flaws in Internet Explorer
IE has gotten a lot of flak over the years for its security flaws, or at least its perceived security flaws. While some of this criticism has been deserved, much has not been and is likely the result of subjective and not objective analysis or bias against Microsoft. Known bugs in IE have led to a number of problems including the installation of various types of malware including spyware, adware, viruses, worms and plenty of other undesirable behaviors. Over the years these types of malware and other software have used flaws to install themselves and take over a user’s system using something as simple as a web page. These same types of bugs and problems will also be covered in the next sections when we cover other vendor’s web browsers.
Perhaps one of the biggest problems with IE that has been exploited repeatedly is the software based on the technology known as ActiveX. ActiveX allows different types of dynamic content to be displayed in the browser such as movies and other media and information. The problem is that the technology has been somewhat buggy and has been prone to granting too much trust to the applets being installed. Adding to the problem of ActiveX is the software’s ability to prompt a user to install it and the user blindly accepting the installation because they simply wish to view the content. We will cover Active X exploits in Chapter 4.
IE has proven to be a capable and flexible browser over the years, but care should always be exercised to avoid any unnecessary security risks. Many of the features that Microsoft has introduced into IE in order to make it a powerful offering also contribute to it being a security risk. Support for technologies such as ActiveX, componentized design, and a number of flaws have led to the browser being a popular target for hackers and their client-side attacks.
Note
Let’s not forget that IE is also present on several of Microsoft’s embedded operating systems such as Windows Mobile. Windows Mobile is a scaled down version of Microsoft popular Windows operating system. This operating system supports a wide range of applications including IE meaning that many of the problems seen on the desktop are now possible on the mobile platform. In fact over the past few years the attacks targeted towards mobile devices have increased and IE with embedded operating systems only makes these attacks more likely and easier. Chapter 9 covers mobile device client-side attacks.
Mozilla Firefox
Mozilla Firefox, more commonly known as just Firefox, is a web browser that is both free and open source. Firefox was first introduced back in 2003 as the spiritual successor to Netscape Navigator and was an attempt to create a robust, fully feature browser that did not suffer from the perceived problems of “bloat” associated with other browsers at the time. Since it was first introduced it has become a popular choice for the browsing public and widely downloaded and used. Figure 3.4 shows the Firefox web browser.
Figure 3.4 The Mozilla Firefox Web Browser
Features
Over its short lifespan Firefox has evolved quite rapidly to include a number of features that have later been included in other browsers such as tabbed browsing. Features includes in Firefox include:
In addition Firefox, much like IE, can be extended through the use of plug-ins and add-ons. These additions to the browser allow a user to install specialized extensions that customize the browser to a high degree. Making the plug-ins of even more value and power is the fact that they are something that can be created and published much easier than with IE or other browsers leading to a large-scale library of extensions that are currently available. The problem with this is that the ability for developers to easily create them also means less than reputable people can create them leading to vulnerabilities.
Did You Know?
In 2009 and 2010 there have been several instances of plug-ins being published on Firefox’s official library of plug-ins exhibiting behavior that is similar to spyware. In at least two of the cases that were made public, the plug-ins were published and looked legitimate, but they actually reported information back to a third-party with the intention of collecting information about the browsing habits of the user (see Figure 3.5).
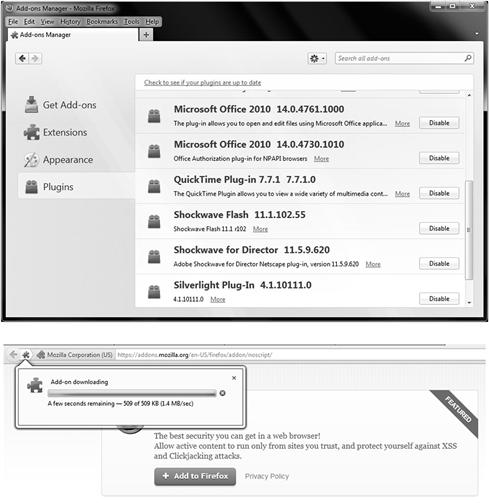
Figure 3.5 The Mozilla Firefox Plug-in’s
Victims that downloaded these plug-ins simply saw a plugin that offered some service published on an official website alongside other official plug-ins and seemed legitimate. By publishing their malicious plugin alongside other official ones on an official website the developers of the plugin were able to widely distribute these to carry out a client-side attack that took advantage of social engineering in the form of trust and also collected data.
Platform Support
Firefox supports a full range of platforms including Linux, Mac OS X, Microsoft’s Windows platform, and other OS’s that follow the Unix model. In fact, Firefox supports operating systems as far back as Windows 95 under certain conditions with certain versions.
Firefox has enjoyed a fair amount of success for its robust standards such as the following:
Security
Firefox offers a range of security measures both natively and through third-party plug-ins designed to enhance the measures already in the product. Out of the box Firefox offers several security measures including:
Among these security features we have several countermeasures for some of the more common client-side attacks, let us explore some of these security features and what they offer in the way of protection. You can configure the browser to be secure, however it is still easy for an attacker to break through the most basic of security. Figure 3.6 shows some of the security settings you can configure within the web browsers settings.
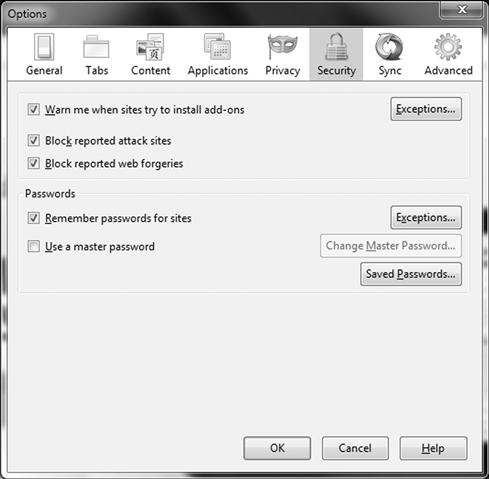
Figure 3.6 The Mozilla Firefox Security Settings
Within the security settings, you can configure many options to keep your browsing safe. Security settings allow you to be warned when sites attempt to install add-ons. Firefox can be configured to stop the installation, warn you, ask you to confirm or prompt you. It should be noted that although this configuration setting may help to mitigate danger, it is not foolproof. You may still be attacked via untrustworthy sites. You can also attempt the block of web forgeries. You can report them as well by going to the Help menu within Firefox. This is similar to phishing attacks.
Lastly, you can configure Firefox to remember passwords for sites. By default you will be prompted to cache credentials, however this is not recommended and a common vector for client-side attacks. If you select “Never,” then the site is added to the exceptions list. You can also configure a master password that protects your information such as digital certificates.
Aside from the basic settings you can configure, there are enhanced features that are available. The first feature in the list, sandboxing, offers a substantial level of protection for applications and scripts running within the context of the browser. Sandboxing is a mechanism used to isolate running processes in such a way that their access to resources is highly restricted. Firefox 3.6.4 runs Plug-ins as a separate process, this way, if there is a security threat that occurs, it will not affect Firefox basic services or processes. Through the use of sandboxing untrusted or suspect code can be run on a system without compromising integrity or security substantially if at all. In the context of Firefox, sandboxing prevents scripts, applets or other web applications from gaining access to resources or parts of the system when such access should not be given.
Note
It is worth noting that IE 7 and above when running on Windows Vista or Windows 7 offers a similar sandboxing model to Firefox. In Microsoft’s browsers and these operating systems code running in the browser has its access severely curtailed. Google Chrome also offers sandboxing.
Another security feature on this list, the same origin policy, is a feature that is used to thwart certain forms of cross-site scripting. In Chapter 2, we saw an example where script from one site was called and executed from another without the user’s knowledge. Using the same origin policy feature code would not be allowed to run in such a manner and therefore preserve the integrity of such situations.
A final feature that is not on this list is more of an administrative or policy feature than anything else, this feature being the “bug bounty.” With Firefox the Mozilla foundation has instituted a program where developers or security researchers that uncover security flaws in the product can report these flaws for a reward. Using this method the foundation hopes to encourage researchers to actively locate and report flaws before attackers exploit said flaws.
Encryption for Communications
Firefox Users can view encryption settings much like any other browser on the market today by going to the Help menu and selecting “About.” Most browsers support the minimum needed to access banks and other sensitive sites which is 128 bit encryption. There are browsers such as Firefox that support higher levels such as 256 bit encryption. You will see a “lock” in the browser window denoting that you are currently encrypting traffic between the browser and the web server hosting the site.
Add-ons and Other Features
Security Plug-ins
Security based plug-ins (or add-ons) are used to bring the browser to a higher level of security. By going to the Mozilla web site and or searching in your favorite search engine, they are easy to find, install and configure. Make sure you download any plugin from a reputable site.
NoScript is one of the most commonly downloaded and used add-ons for Firefox when security needs to be brought to the next level. NoScript is an add-on that will allow active content to only run from trusted sites. This helps to thwart cross-site scripting (XSS) attacks as well as what is known as a click-jack attack.
Note
Click-jack attacks, or click-jacking is an attack where the end user of the web browser clicks on a link that is malicious although they thought it was legitimate and then executes a script or function that commonly causes damage, steals information or takes over the browser itself.
If you go into the add-on’s configuration of your Firefox browser, by selecting to configure the options of NoScript, you can adjust the settings as seen in Figure 3.7. Here you can adjust general settings, configure whitelists, notifications and more.
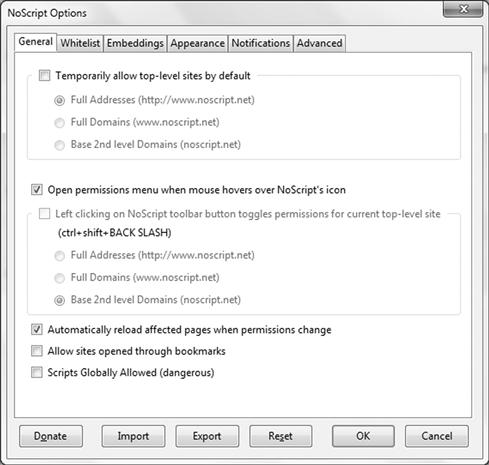
Figure 3.7 NoScript Configuration Settings
In the Advanced tab, you can configure filters and XSS specific settings. Figure 3.8 shows the XSS configurable settings such as configuring exceptions, sanitizing XSS requests and turning cross-site POST requests into data-less GET requests.
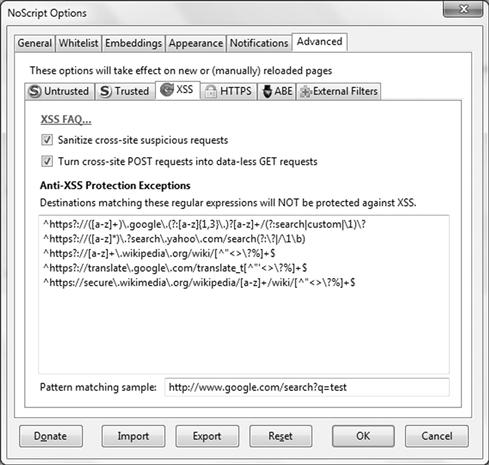
Figure 3.8 NoScript XSS Configuration Settings
Other plug-ins allow you more security, one such add-on being the Request Policy application. This will also give you XSS enhanced security by allowing more privacy settings by not allowing an attacker to gain access to your browsing habits.
Known Security Flaws in Firefox
Just as with any web browser, Firefox is no different—there will always be some form of known security flaw currently being fixed or prospectively being investigated. All versions of Mozilla products stand subject to scrutiny. Mozilla Foundation Security Advisories team-members work closely with developers and the general public to identify and fix common issues that are found. Security bugs are common and by simply patching them, upgrading the browser or both, you can mitigate an attack, however this is a constant process that requires administrators and users to be vigilant in keeping abreast with current security threats and knowing that their software requires fixing. This is not always the case, and something that an attacker bets on when planning an attack. Bugzilla, as it’s called is where you can find and prevent issues as well as know what to do to fix them.
Google Chrome
Google Chrome, first released in 2008, seeks to offer advantages over other browsers in the areas of security, speed, and stability. Chrome offers these benefits by being a no-frills browser. Features that are common in other browsers may not be present in this browser in order to keep the footprint smaller which gives it increased reliability, makes it faster and easier to secure. For example, Chrome has little in the way of an interface as many graphical elements seen in other browsers are discarded in favor of a simple tabbed interface with no extras. An example of another feature not in Chrome that is common in other browsers is RSS support of any kind. Figure 3.9 shows the Google Chrome browser.

Figure 3.9 Using the Google Chrome Web Browser
The Google Chrome web browser is still susceptible to client-side attacks however. Because it touts being secure, does not mean it cannot be used as a vector for an attack. It’s still a web browser and subject to the same attacks any other browser is susceptible to. Because of how Chrome was developed, unlike Internet Explorer as an example, the nature of its openness allows for developers to work directly with the source code which at times makes it more secure and at time, less secure. Chromium (www.chromium.org) is the open source group of developers that help to build Google.
Features
Aside from being one of the fastest browsers available, Google Chrome does offer more under the hood then just a flashing race car exterior. Within it, there are many bells and whistles that make it stable and secure. Much like the other browsers we have reviewed, there is a common theme between all new browser releases no matter who the vendor – they all compete so obviously they are going to offer many of the same features aside from what they claim makes their offering better. For Chrome, these features are:
![]() Translation Services—Chrome has built-in technology that allows for quick translation of any page on the Internet much like Google Translate. This allows for quick altering of any page you retrieve not in your default language of choice.
Translation Services—Chrome has built-in technology that allows for quick translation of any page on the Internet much like Google Translate. This allows for quick altering of any page you retrieve not in your default language of choice.
![]() Omnibox—Different from most browsers, this tool allows you to type either a URL and or a search request into the browser without having to pull up a search engine page first. This makes for faster browsing and searching when using Chrome.
Omnibox—Different from most browsers, this tool allows you to type either a URL and or a search request into the browser without having to pull up a search engine page first. This makes for faster browsing and searching when using Chrome.
![]() Sandbox—Chrome helps to keep stability of your browser by sandboxing problems within specific tabs, meaning that if you have a web page that freezes or has an issue, it will not affect the browser itself or other open tabs.
Sandbox—Chrome helps to keep stability of your browser by sandboxing problems within specific tabs, meaning that if you have a web page that freezes or has an issue, it will not affect the browser itself or other open tabs.
![]() Incognito Mode—As mentioned earlier, most browsers record all of your historical usage, therefore if you wanted to browse without anything being recorded, you can use this mode.
Incognito Mode—As mentioned earlier, most browsers record all of your historical usage, therefore if you wanted to browse without anything being recorded, you can use this mode.
![]() Additional Secure Plug-ins—more plug-ins, add-ons or extensions are available to help customize and secure Chrome.
Additional Secure Plug-ins—more plug-ins, add-ons or extensions are available to help customize and secure Chrome.
Google Chrome helps thwart client-side attacks with enhanced security features. Google Chrome uses a technique that brings the sandboxing feature seen in Firefox and IE to the Google browser. Google Chrome implements sandboxing on a tab-by-tab basis that is designed to prevent malware from being installed from a web page onto a client system. Chrome, by implementing isolation on a tab-by-tab basis, also prevents what happens on one tab from effecting what happens on another. Lastly, the isolation model in the browser prevents any process running on one tab from reading or writing information to another providing added protection from malware that may attempt to gather information that it is unauthorized to access.
Another security feature that puts Chrome on par with other browsers is something known as Incognito mode. In this mode, much like private browsing in Internet Explorer, no information is stored on the client system including history or other information such as cookies. By running this mode clients prevent information that can be read through various client-side attacks from being available for access later.
Note
As mentioned earlier, the Chrome browser was meant to be lightweight, therefore many tools do not come with the native browser, however it should be noted that when extensions are added (such as RSS support), it becomes just as bloated as any browser so do not get confused between the two. If you decide to extend your browser more and more, it becomes no different than any other browser you use.
Security
Chrome offers several security features similar to what is seen in other browsers on the market such as Mozilla’s Firefox including sandboxing among others. One option for securing the browser is to configure the security settings as seen in Figure 3.10. Here you can customize your settings for more control.

Figure 3.10 Securing Google Chrome
When securing Chrome, you can adjust privacy settings, manage certificates and add additional security plug-ins and extensions for tighter and more secure use of your browser.
Much like Internet Explorer’s phishing filter Google Chrome also maintains a list of harmful sites and content. In Chrome two lists of blacklisted sites are downloaded into the browser regularly for both malware and phishing sites. The concept is the same in Chrome as it is for IE, websites that engage in malicious activities relating to malware or phishing can be cataloged and blocked with this feature.
Chrome, much like IE, does not offer a way for users to customize the list of phishing websites nor malware websites. The feed of malicious websites can only be downloaded from Google and used by the browser to block harmful sites and cannot be customized. In an effort to improve security for everyone.
Did you know?
You can troubleshoot problems specific to client-side attacks directly in the browser itself? For example, let’s say you wanted to view the running processes within the browser; you can look at them directly using the Task Manager in the tools menu? Figure 3.10a shows the running tasks that Chrome is currently using. Here you can view them and end any offending task.
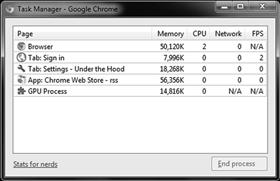
Figure 3.10a Google Chrome Task Manager
You can also look at the scripts embedded within a web page using the JavaScript Console as seen in Figure 3.10b. Here you can really delve deeply into what is going on behind-the-scenes when working with your browser. For example, you can open the console and visit a site such as www.facebook.com and view the many behind-the-scenes scripting that goes on when you visit the site.
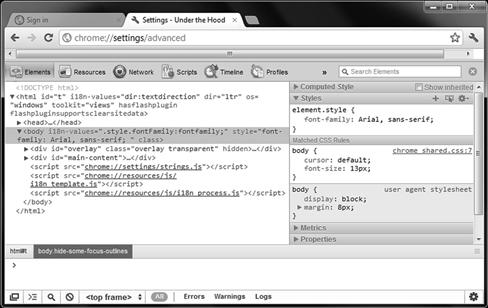
Figure 3.10b Google Chrome JavaScript Console
Here you can go to the cookies section within resources to view one of many different actions taking place when you go to the site (see Figure 3.10c).
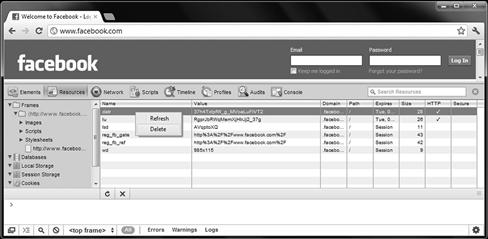
Figure 3.10c Viewing Facebook in the Javascript console
It’s important to note that with this enhanced flexibility, it will be easier for you to mitigate attacks, customize your security posture and be more aware of what actually happens when working with any browser.
Add-ons and Other Features
As, mentioned with other browsers, it’s easy to customize and add additional features to the already inclusive toolset. When adding extensions on to Google Chrome as seen in Figure 3.11, you can build out your browser with many tools, features and services.
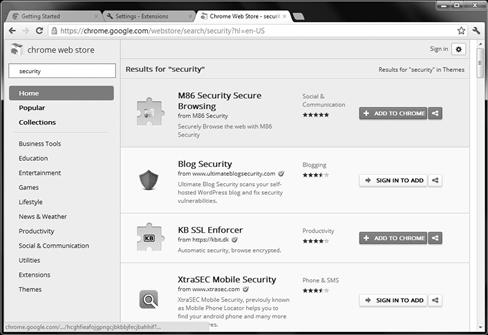
Figure 3.11 Google Chrome Extensions
There are many additional tools, too many to mention that can be used. Much like the other browsers we have already covered, there are many of the same types offered with Chrome that provide similar functionality. Simple search the database and customize as needed. Important to mention is that you always want to add “trusted” tools from reliable sources.
Known Security Flaws in Google Chrome
Just like all browsers, nothing made or created today is completely reliable or impervious to attack. One such known flaw which had been corrected is with the underlying technology used to fuel and power the browser. WebKit (and WebKit2) is a set of classes used with web browsers to help load and render pages. It is primarily used with Google Chrome and Apple Safari; however it is also used with many mobile devices as well.
Because of WebKit, the browser will be more functional, although with more functionality at times comes with more vectors that can be attacked. Such as was the case with Chrome. Webkit years ago had a vulnerability which was exposed as a bug in Java. It could further be exacerbated by a social engineering attack. At that time since Apple Safari used WebKit as well, both were vulnerable. Apple decided to patch this issue and use a newer version of WebKit, whereas Google did not. Eventually they did patch this issue and came out with newer security features on top of it. The Safe Browsing API was also enacted by Google. Chrome version 17 became one of the more secure versions as more and more focus was put on its security.
The point to this is that any browser, new or old, touted as being the most secure is always being made more secure for a reason—there are ways around all security and it’s only a matter of time before these security flaws are found and executed. More so, it’s important to consider that thinking something is secure because it is marketed as such does not make it secure.
You should always consider that a client-side attack could occur and try to remain vigilant in your defense against them. It is the only way to make sure that you stay on top of the constant battle of making and keeping things secure.
Apple Safari
The next browser that we will examine is the browser from Apple known as Safari. Safari, first introduced in 2003 for the Mac OS X operating system became the default and native browser for the Mac OS X operating system. It was then ported to many other platforms to include Microsoft Windows. Safari, much like the other browsers discussed in this chapter, offers many cutting edge features that will be discussed here (see Figure 3.12).
Figure 3.12 The Apple Safari Web Browser
Features
Apple Safari offers numerous features, including the ability to save webpage clips for viewing on the Apple Dashboard (Mac OS X only), a resizable web-search box in the toolbar which uses Google, Yahoo! or Bing, automatic filling in of web forms (“autofill”), Bookmark integration with Address Book, new Bookmark management features, history and bookmark search functions, expandable text boxes, ICC color profile support, inline PDF viewing (Mac OS X only), iPhoto integration (Mac OS X only), mail integration (Mac OS X only), quartz-style font smoothing, reader mode, for viewing an uncluttered version of web articles, spell checking, subscribing to and reading web feeds, support for CSS 2.1 web fonts, support for CSS animation, support for HTML5, tabbed browsing, text search and so much more. As with most browsers available today, Safari is very feature-rich.
Because of Apple’s new dominance in the market, Safari is now becoming a household name. Consider that whenever an iPad or iPhone is used to surf the Internet, the Safari web browser is used by default. Now, since iTunes runs on most Windows systems, Safari becomes even more problematic to enterprises that allow it because with the auto-updater, Safari becomes one of the downloadable options by design.
One thing that can be said about Safari is that it has matured. Much like Chrome, Safari is based on open development and the WebKit and WebKit2.
Did You Know?
Most mobilized owners of Apple devices do not realize that when they surf the Internet, they are using Safari. It is transparent to them because when they get their devices, it comes with Safari. When they launch the browser, it does not highlight the name or versions unless you look under the covers. As we learned earlier with WebKit, there have been client-side attacks that took place because of it. A serious issue that turned up a few years ago was with Safari’s AutoFill feature. Because of this flaw, a malicious website was able to easily gather personal information from any visitors address book when they hit the site. Chapter 9 covers mobile devices, security and client-side attacks in more detail.
Apple Safari enjoys support on different platforms including the Mac OS X operating system as well as Windows versions from XP through Windows 7. Although the web browser has been successfully ported from the Mac OS X operating system to Windows, it is important to note that the same security and features are not available on both platforms mainly due to the tight integration of Safari with Mac OS X.
Warning
This apparent integration (or pseudo integration) is true with Internet Explorer as well. Internet Explorer is offered for Mac OS X and even though the interface and features look the same under the hood the integration is not there. The reality is that Internet Explorer, much like Safari, is integrated with its natural OS so tightly that moving it from one platform to another results in some loss of functionality. Those using browsers such as Safari or Internet Explorer on a system other than its native one should be advised to exercise heightened security practices to compensate for the loss of some features.
Security
As of this writing Safari is at version 5.x which was released in mid-2010 and includes a host of new features that are of interest to those of us trying to prevent attacks against the client. Apple has dedicated some serious resources over the past few releases and years to improving the security of their browser to make it more resistant to attack. Included in these features are a more robust developer program, sandboxing features, and others. Table 3.2 highlights some of these additional security features.
Note
Transport Layer Security (TLS) grew from the original Secure Sockets Layer (SSL) protocol. Both provide secure communication channels over unsecure mediums. They are both cryptographic protocols that use key exchange in order to encrypt and secure transfer of information. All browsers support encrypted communication, however it should be noted that older versions of browsers (in particularly Apple Safari) rely on the base OS to provide it. Newer versions of browser such as Apple Safari version 5.x support it natively within the browser.
Table 3.2 Apple Safari Security Features
| Private browsing | Allows the user to keep their browsing habits private by turning off most features like cookies and auto-fill. |
| Keychain | This solution offers built-in password management via Keychain (Mac OS X only). |
| Transport Layer Security (TLS) | The use of TLS adds a layer of encryption between browser communications. |
| Pop-up ad blocking | This feature will stop pop-ups from occurring by default and warn you when one has been attempted. |
One of the features that means the most and brings Safari in line with other browsers is its sandboxing model. Sandboxing, as we have seen with the other browsers we have covered, allows processes to have their access restricted to specific resources on the system in order to reduce exposure to threats. In Safari the technique is the same as with other browsers, but the implementation is a little different as the ability to sandbox is embedded into the OS and not just the browser. Apple’s developers reasoned that by embedding the ability to sandbox into the OS instead of just the browser other process could take advantage of the feature as well. In essence this means that the browser can isolate processes in tabs and within the browser itself, but the application installed next to the browser on the same system can do some sort of sandboxing too.
Apple Safari can be configured securely within the browser. To configure Safari’s security settings, you need to open the browser and open the browsers configuration parameters as seen in Figure 3.13.
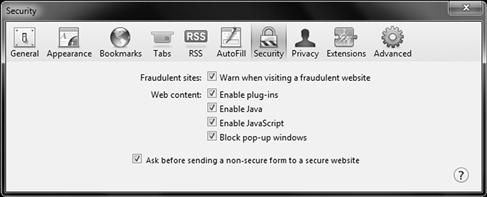
Figure 3.13 Configuring Apple Safari Security Settings
When configuring basic security for Safari, you can configure a warning when a fraudulent site is visited, and ask before sending non-secure forms to a secure website. Other controls for web content are also available, such as enabling or disabling plug-ins, Java, JavaScript and pop-up windows.
Add-ons and Other Features
Apple has also taken a cue from the Firefox community by creating a developer program where third parties can develop their own extensions to customize the browser. Much like the developer community with Firefox there is a potential, and in the case of Firefox a realized, security risk with letting anyone develop extensions. In Safari developers can submit to voluntary registration where they provide information to show that they have been verified and trustworthy. Figure 3.14 shows the listing of extensions that can be added to the browser in order to expand its security, flexibility and functionality.
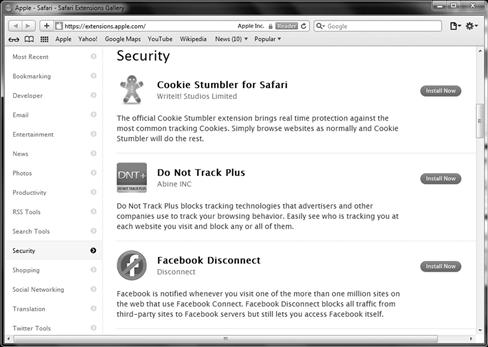
Figure 3.14 Apple Safari Extensions
Known Security Flaws in Apple Safari
Prior version of Safari up to version 4 had a flaw so serious it received the attention of the US Government. At one point, Apple Safari was deemed by the Department of Homeland Security as extremely dangerous for use. United States Computer Emergency Readiness Team (US-CERT) created an advisory that for security reasons, all should be aware that Safari users are open to attack.
This vulnerability in the web browser was a bug that exploited the browsers window. Code could be executed arbitrarily when a unsuspecting user visited a malicious web site or if an HTML-based email be opened within webmail. The attacker would then be able to log user data and place malware on the unsuspecting victim’s host system. With new advances, patches issues and so on, Safari is now far more secure then it has been in the past. With WebKit2 integrated into Safari as of version 5.1, there is more security from client-side attacks.
Opera
Opera is a web browser whose roots trace back to 1994 when it was a research project. In 1996 it was publicly released to the masses. As of 2010, the newest version number (Opera 11) was released and is the current version in use today. It is freely downloadable to whoever chooses to use it.
The Opera web browser has generally set the bar for most other browsers on the market and in some cases, was first to market with specific features found in all browsers today. It’s also touts being one of the most secure. Figure 3.15 shows the Opera Web Browser.
Figure 3.15 The Opera Web Browser
Note
As we will cover later in the book, Opera Mini is also widely used on handhelds and phones that manipulate a web browser.
Opera can be installed on many computer operating systems and devices. For example, it can be installed on Windows, Mac OS X, FreeBSD and Linux. As well, it’s found on many mobile devices such as the iPhone, Android, Blackberry and Windows Mobile. Opera is so widely distributed that it can even be found on the Nintendo DS and Wii game systems.
Features
Older versions of Opera were always feature-rich and as of the release of Opera 11, even more so. With Opera 11, you can use extensions, tabbed browsing (stacking) and a new address field which partially hides some of the URL.
Opera gives you most if not all of the features we listed for the other browsers covered, but as you have seen, each browser development team has their own spin on it. For example, browser tab stacking and how they manipulate the search and input field are two examples of how Opera functions differently. Most importantly, Opera is loaded with security extras.
Security
Opera is a secure web browser and puts a lot of effort into keeping it that way. As we will see when we cover “known flaws,” it’s not impervious to attack. As seen in Figure 3.16, you can configure many of the same security settings as other web browsers.
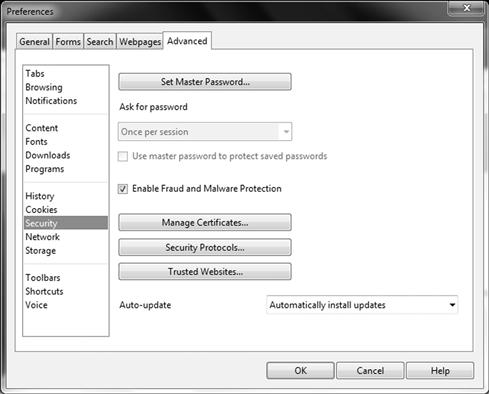
Figure 3.16 Opera Security Settings
When configuring security, you can go into the preferences settings and within security, adjust the Fraud and Malware protection settings, manage certificates, protocols and incorporate a trusted site list. You can also configure the browser to auto-update itself as needed with critical security patches.
Opera’s other security features also include a phishing filter, the ability to delete all privacy data, the use of encryption and add additional security features via extensions.
Add-ons and Other Features
Opera offers a wide variety of extensions that can be used to further expand the use of and secure your web browser. For example, by clicking on the extensions manager, you can view what is currently installed or add new features as seen in Figure 3.17.
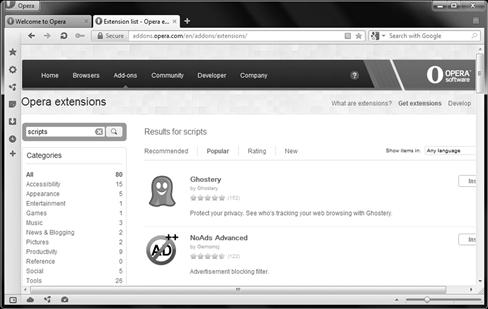
Figure 3.17 Opera Extensions
In this example, we have downloaded and installed Ghostery. This extension is very helpful as it will look at the pages in which you connect to for bugs (called “3pes”). These bugs are commonly known as widgets, gadgets, software used for advertising, tracking and analytics software and more.
When Ghostery finds these, it can transparently deal with them in the background and or present you with its findings. When Ghostery finds these items, it will show you the operators of the software and allow you to block them as seen in Figure 3.17a and 3.17b.
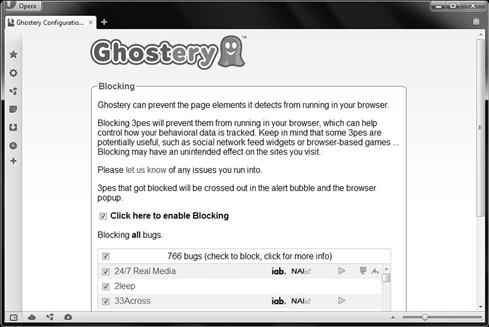
Figure 3.17a/b Opera Extensions (Ghostery)
Ghostery is helpful as it will allow you to block known bug sites when you first install and configure this extension. The list can also be updated automatically or manually.
Other security features and tools can be directly on Opera’s website.
http://www.opera.com/browser/tutorials/security/
Here you can find a security guide that explains the security and privacy features found in Opera, as well as the settings in the browser you can configure. Opera also interactively alerts you to security threats while using the browser; as it detects them it will notify you. You can learn more on Opera’s security page online. Other information you can learn about and implement into your security assessment is Opera’s fraud and malware protection alerts you to fraudulent and suspicious webpages, the use of Extended Validation (EV), as well as tips for safe browsing habits, cookie management and how to keep Opera and other applications up to date.
Known Security Flaws in Opera
Not too long ago (within the past year) a critical flaw was identified with Opera. A critical flaw was uncovered in Opera that could be used to execute arbitrary code on a vulnerable machine.
The “remote bug” which affected every release up to version 11.00 is a vulnerability that allowed a malicious attacker to take full control of a system when a malicious web site was viewed. The issue was based on an integer truncation error within the Opera Internet Browser module “opera.dll.” It took advantage of the handling of the HTML “select” element which allowed an attacker to execute code.
As well, because Opera was supportive of HTML5 (like most other browsers on the market), the WebSocket protocol was used which increase vulnerability. This functionality allowed web servers to send data to a web browser without scripting or refreshing. As we see, no matter how much functionality we try to incorporate or how safe we attempt to make ourselves, there is always a way that a client-side attack can eventually take place, hence why we must always exercise the tightest level of security achievable while still allowing for flexibility of use – a very difficult balance to obtain and maintain.
Web Browsers as a Target
Client-side attacks are commonly carried out between a web browser and a web server. This is because it is one of the easiest avenues of attack as mentioned in the first two chapters. Firewalls and content filters let HTTP in (scripts) and the web browsers are easily exploitable via the web servers they connect to. This is why so much attention was given to web browsers in this chapter. Web browsers are indeed a target, so take care in protecting them as much as possible by not only patching them and keeping them secure, but understanding them as much as possible and educating yourself and end users on their use.
As we can see in Figure 3.18, by simply visiting a web page on a server that is malicious in nature, running an unsuspecting script or downloading and installing potentially harmful software that appears harmless, your browser can be overwritten immediately.
Figure 3.18 A Basic Browser Attack
What’s worse is, if you used Google.com as your homepage for a search engine, how would you really be able to tell the difference if you were “hacked?” In this example, we can see that the browser’s default page is overwritten to drive your traffic to a different location and the page looks nearly identical which is not only misleading but often overlooked by most users.
As we have seen with cross-site scripting in Chapter 2 and some of the vulnerabilities seen here in Chapter 3 for each browser, the web browser is an attractive and tempting target for attackers. This is largely due to the well-known and numerous vulnerabilities present in each browser and the large number of browsers present on different operating systems and platforms and its ability to be openly used between the security systems meant to protect it such as firewalls and content filters.
Web browsers have proven themselves to be both a very beneficial piece of software and at the same time a liability due to the environment it works in. Consider the environment a web browser accesses and how this interaction impacts security on the client. When in use a web browser actually opens a “portal” from a secure environment on the client to an insecure environment such as the Internet. This access essentially means that the insecure and untrusted environment of the Internet is being brought into the environment on the client along with all the potential vulnerabilities associated with this.
Note
When a web browser access content from the Internet and runs it locally a potential security risk is created by the running of untrusted code in a trusted environment. In order to mitigate the risks with such an arrangement one of the techniques we discussed is sandboxing, which is used to prevent untrusted code from gaining unrestricted access to the local system.
Selecting a Safe Web Browser
So which browser is the biggest target? Well that is an argument waiting to happen, but most security professionals and research organizations would tend to agree that Internet Explorer holds this distinction. Internet Explorer lends itself to being the biggest target simply because it has the enviable (or unenviable) position of having itself installed on greatest large amount of desktops around the world. By some estimates the Windows operating system is installed on the majority of desktops worldwide which adds up to a large number of targets that attackers have taken advantage of. Add into this mix the fact that IE is built on the Windows operating system which has been shown time and time again to have numerous defects that lend themselves to client-side attacks in the form of buffer overflows, cross-site scripting, remote code exploits, and many others.
Of course Internet Explorer is not the only browser on the market as we have seen in this chapter, so what about the others? Firefox has rapidly become a target mainly due to its increasing presence on the desktop by users looking for alternatives to other browsers as well as those looking to try a new browser anyway. So if Firefox is a target how vulnerable is it? The reality is that Firefox itself has a number of vulnerabilities present in it and at several times during its inception it has actually had more defects and other security flaws than IE. Looking objectively at the situation one will note that Firefox is vulnerable to many of the same attacks as IE, but Firefox also tends to have its defects and flaws addressed much quicker due to an aggressive effort by the community.
Warning
One of the bigger misconceptions that has been perpetuated on the Internet is the idea that Firefox is the most secure browser around or as some would claim “bulletproof.” One should never become so fanatical about a browser that they believe that it is invulnerable to attacks; this type of thinking can be dangerous. As a security professional you should always strive to be objective and look at the information being presented.
The next browser that is a target is Google Chrome which is the “new kid” on the block. This browser has only been around a short time, but in that time it has taken its share of flak on several fronts. The biggest issue with Chrome that surfaced shortly after release was the perceived issue of the browser reporting information back to Google regarding browsing and other habits. This was later disavowed by Google and later clarified as only being done with the end users consent and even then only specific information is sent. So is Chrome a target? Yes, but maybe not as big of one as IE and Firefox. What may contribute to Chrome being a larger target is the fact that it borrows code from so many different libraries including Firefox and others meaning it may also inherit some of the vulnerabilities of these browsers and libraries as well.
Safari, is another popular browser on the market. Safari, even though it may not have the market share of the other browsers mentioned in this chapter, still is a major target for a few reasons. First, the browser is part of the increasingly popular Mac OS X platform meaning it has become a larger target as the platform becomes more popular. Second, the browser is on other popular devices such as the iPad, iPhone and other Apple devices that mean more targets for an attacker. Because of Apple’s market share growing day by day, Safari will continue to grow in use and become more widespread as time goes on.
Opera is the last browser we covered and just like the others, is equally as vulnerable as the rest. Because of its history in the marketplace and its flexible use among so many operating systems and devices, it’s seen as often as any of the rest of the browsers available.
So in sum, many users use IE because they purchased Windows and it came with it. Many of those same users think that they are safer downloading another browser and take their pick of the many options available. Others install an application or tool (such as an iPhone) and with it inevitably comes a Safari download and install. Regardless, they ALL have vulnerabilities associated with them and as a security professional because there are so many options and so many browsers installed, we need to understand them all in order to prevent being exploited.
Warning
Never forget that the increasing number of Internet enabled devices such as mobile devices and appliances only makes the problem of attacks worse. Think of devices such as the iPad and iPhone that are seeing rapid adoption by the public, with these devices individuals are browsing the Internet from more places and carrying their information with them. With increasing amounts of information being stored on these devices and these devices being Internet enabled attackers have increasingly viewed these devices as targets for attack. Chapter 9 covers mobile devices, security and client-side attacks.
Warning
It should be noted that there are other web browsers out there in the wild. There have been many and new ones are in development all that time. Consider Lynx, Mosaic, Konqueror, K-Meleon, Galeon, OmniWeb, AOL Explorer, Dillo, Dooble, Flock, and so on. Also, between set top cable TV boxes, gaming systems, handhelds, book readers and more, there are web browsers found almost everywhere we interact with the Internet. When using “any” of these browsers, follow the same methodology shown here in this chapter (and this book) to secure against client-side attacks and protect yourself.
Summary
In this chapter we examined the web browser as a primary target for client-side attacks. The web browser is a piece of software which is present on just about every operating system in existence as well as other devices such as cellphones and handheld computers. As a utility that is designed to access and present the wealth of information that exists on the Internet it has seen itself become an item that is ubiquitous and indeed considered to be a required component on any device desktop, mobile, or otherwise.
As a piece of software that has become so common and integral part of modern systems the browser is one of the prime targets of attacks and attackers. Attackers have targeted browsers due to the prevalence of the application and the fact that attacking such a widely used piece of software can easily result in large-scale disruption.
