"Tunnels have been the refuge of many a smuggler!" | ||
| --Samir Datt | ||
In the good old days (and even now), smugglers would need to ship foreign contraband (unauthorized products) across the borders without the border security forces or coast guard finding out. To do this, tunnels were commonly used.
The network world has startling similarities when it comes to shipping unsupported and unauthorized protocols across the network borders. This is done by the means of tunneling. In a nutshell, what a tunnel involves is encapsulating the unsupported (or unauthorized) protocol in the data portion of the IP datagram and then using the IP protocol to send it. Tunneling protocols work mostly at the fourth layer of the OSI model. This means that they replace protocols such as TCP or UDP.
Virtual private networks, or VPNs in short, completely depend on tunneling for their functioning. This chapter will cover the VPN tunnels and functional, confidential, and covert tunneling. We will look at the various tunneling protocols as well as study about the vulnerabilities of the system.
The chapter will cover the following topics:
- Understanding VPNs
- How does tunneling work?
- Types of tunneling protocols
- Various VPN vulnerabilities and logging
Most organizations have private networks just dedicated to organizational use. The network could be a LAN, WAN, or MAN, depending upon the geographies involved and the requirements of the organization. Virtual private networks (VPNs), as the name suggests, are virtual networks that provide the private network experience for users over a public (unsecured) network—the Internet. To clarify, a VPN provides a secure tunnel to connect users outside the private network with their organizational network. VPNs use authentication and encryption for the data sent between the organization and the user outside the network boundaries:

VPNs can also be used to create secure connections between two geographically different offices, such as is in the case of branch offices and the head office. VPNs can play an altogether different role. Whenever a user wishes to access certain resources and does not wish the traffic to be intercepted or the IP address to be identified, the user may use a VPN to access such resources.
VPNs fill a very important need and as a result, are fairly widespread. There are predominantly two types of VPNs, as follows:
- Remote access VPNs
- Point-to-point VPNs
A remote access VPN is used to provide secure organizational network access to remote users over public telecommunication infrastructure such as the Internet. This involves installing a specialized client on the remote user's computer or hand-held device. This client then connects to a VPN gateway on the organizational network. The gateway first requires the remote user's device to undergo identity authentication, then it creates an encrypted network link back to the remote device. This link or tunnel allows the remote user to act as if it was present locally in this network and to reach and utilize the organization's internal network resources such as servers, printers, and so on.
Some remote access VPNs provide secure access to a single application and are designed to be application-specific (for example, SSL virtual private networks), while others provide Layer 2 access (IPSec) to the whole internal network. These typically require a tunneling protocol, such as PPTP or L2TP, running across the IPSec connection.
Remote access VPNs usually comprise two major components.
The first is the Remote Access Server (RAS), also commonly known as the Network Access Server (NAS) (this is different from the Network Attached Storage, which is commonly associated with the NAS acronym). This NAS validates the user's credentials and allows the user to log in to the VPN. The NAS may have its own authentication process or alternatively use an authentication server present on the network to authenticate the remote user:

The second component is the VPN client software. The role of the VPN software is to build a tunnel to the VPN server as well as ensure the encryption of data in the tunnel. A lot of OSs have built-in VPN capabilities. External VPN tools are also available and are quite popular.
Point-to-point VPNs can be between specific locations or sites (in which case, we would call it a site-to-site VPN) or between specific servers/computers such as servers in two different data centers.
In the case of a site-to-site VPN, an entire network in a particular location is connected to another network at some other location (such as a branch office) via gateway devices. No VPN clients are required to be installed on the end user computers at these locations. These computers access the network normally and all the connection requests to the other network are handled seamlessly by the gateway.
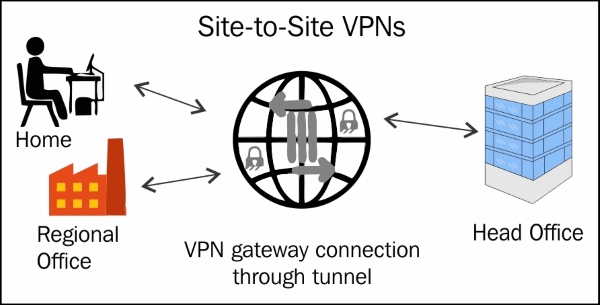
Most VPNs that connect one site to another over the Internet use IPSec. Rather than using public Internet, carrier MPLS clouds can also be used as transport. Connectivity can be Layer 2 (Virtual Private LAN Service) or Layer 3 (MPLS).
Specific computers can also be set up to communicate directly with each other via a VPN. Typically, these could be highly secure servers in geographically different data centers, where the need for security is much higher than that set up for the current network environment.
AAA stands for authentication, authorization, and accounting. These three are the cornerstones of secure access in a VPN environment:
- Authentication: This involves the authentication of a user by the means of a valid username and password. In the absence of an authentication mechanism, any one with a preconfigured VPN client has a direct entry into a secure remote network. User authentication data (usernames and passwords) may be stored on the VPN device or on a separate AAA server.
- Authorization: This is the second stage. At this point, the server has already authenticated the user and now moves on to determine the authorization levels of the user. This determines what the user is permitted to do.
- Accounting: The accounting stage is where a record of all the activity done by the user is maintained. This is the logging stage that is used extensively for security auditing, forensics, and reporting purposes.
The following image depicts the AAA concept:

The key to VPN connectivity and security is the secure tunneling done through public networks such as the Internet. Therefore, let's move onwards to try and understand how tunneling works.
