The process of encapsulating a packet within another packet and then sending it over the network is known as tunneling.
As we are aware, every packet has a header that contains details relating to the IP version, length of the IP header, size of the IP datagram, source address, destination address, flags, and a host of other data. The header length is usually 20 bytes. The remainder portion of the packet is the data. Tunneling involves hiding unsupported or unauthorized packets within the data portion of the IP datagram. In such cases, the available space is less than what it is usually and at times, this can cause a problem in the transmitted data.
Data tunneling is often used to hide the origin of the traffic across the network. The original packet and header is encapsulated and encrypted and an additional layer 3 header is added on top. In this manner, the process of tunneling neatly hides the original source of the packet. At the destination, the trusted computer strips away the original header and determines the true source and decrypts the original header. One important thing to consider is that tunneling, by itself, does not ensure security. In the event that a packet capturing device is enabled, the data encapsulated in another packet may be visible if the packet is not encrypted.
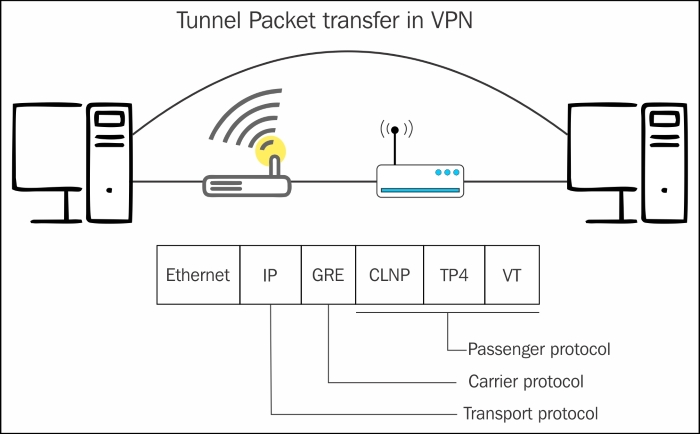
Tunneling involves the following three different protocol types:
- Passenger protocol: This is the protocol that is carried in the main datagram. IP, IPX, and NetBUEI are the examples of the passenger protocols.
- Encapsulating protocol: This is the wrapper protocol, which means the protocol that wraps around the passenger data. The examples are IPSec, GRE, L2F, L2TP, and PPTP.
- Carrier protocol: This is the protocol that is used by the network for data transmission. Information travels over this protocol. IP is the main transport protocol.
The passenger protocol packet is encapsulated and at times, encrypted in the encapsulating protocol datagram. This is then put in the carrier protocol (usually IP) for transmission over the Internet. This allows safe and secure transmission of the protocols that would normally not have been transmitted over the Internet (such as NetBEUI).
At this point, it would be useful for the investigators to note that IPSec has become quite common these days. IPSec provides security services for IP packets by encrypting traffic data. The way IPSec works in tunnel mode is to encrypt an IP packet, then encapsulate it and add a new IP header, and finally send it to the other end of the tunnel. The way various tunneling protocols work with IPSec are listed in the following sections.
SSH or Secure Shell tunneling involves the creation of an encrypted tunnel via an SSH protocol connection. SSH tunnels can be set up as an encrypted channel to transport unencrypted traffic (such as SMB—Server Message Block—protocol on Microsoft Windows machines) over the network. Tunneling, essentially, involves port forwarding. When setting up SSH tunneling, we can configure the local SSH client to forward a local port number to a specified port number on the remote machine. After setting up the SSH tunnel, a local user just needs to connect to the specified local port in order to gain secured access to the remote machine via this port. It is not necessary for the port numbers to be the same for the port forwarding to work seamlessly.
In the earlier SMB example, if we were to mount a Windows machine and access it remotely, anybody intercepting the traffic would be able to have full access to the transferred files. This is because the SMB protocol is unencrypted. However, if we were to use an SSH tunnel to route all the SMB traffic to and from the remote machine, the data would be secured by the SSH tunnel that is encrypted and the data would only be accessible to the authorized user.
SSH tunnels can also be used to bypass firewalls and proxies that are configured to monitor user activity in the organization's perimeter. In an organization that restricts direct web browsing by routing all traffic for port 80 via the proxy (from the perspective of monitoring Internet activity), a local user can access a remote SSH server in order to enable an SSH tunnel allowing port forwarding of a local port (for example, 3001) to port 80 of a remote web server. However, the important thing to note is that this is only possible if the organization policies allow outgoing connections.
An additional point of interest is the aspect of dynamic port forwarding. Some SSH clients allow dynamic port forwarding. This permits the user to create a SOCKS 4/5 proxy. Once this is done, a user can configure their application to use the more flexible SOCKS proxy server. In this case, there is no need to create an SSH tunnel to a single port on a remote server.
