In this chapter, you'll configure your BeagleBone Black (BBB) to run a bridge in the Tor network. This bridge will allow you and others to access the Internet more anonymously and provide an anti-censorship gateway. We'll add a simple hardware control interface to BBB so that we can see and adjust the bandwidth usage of the bridge in real time. We'll call this project BeagleBridge.
This chapter will discuss the following topics:
- An introduction to Tor
- The difference between a Tor relay and bridge
- Obfuscated Tor proxies
- How to download and install Tor on BBB
- How to configure BBB as a Tor bridge running an obfuscated proxy
- How to add hardware controls to adjust the bridge from a front panel
In this project, you will learn how to use Tor, a tool and network designed to protect your anonymity online. Tor originally developed from research, sponsored by the U.S. Naval Research Laboratory, on onion routing (Dingledine, Mathewson, and Syverson, 2004). In onion routing, the client builds a circuit of nodes in an overlay network, which is a network built on top of an existing network. The Tor network is an overlay network that runs on the Internet, although it can run on separate networks. The client sends a message to each node, which is specifically encrypted for that node, asking the node to send it to the next node in the circuit. Each node peels back a layer of encryption and forwards the result to the next hop in the circuit, and hence, the onion analogy. The last node contains the client's actual message, which is forwarded to the destination server.
Onion routing provides anonymity because the destination server does not know the IP address of the client. Typically, when you use your browser to access the Internet, the browser creates a Transmission Control Protocol (TCP) connection that originates from your system and terminates at the website you are trying to visit. The address for TCP is provided by the Internet Protocol (IP). Each IP datagram contains a source and destination IP address. As datagrams arrive at the server, the server can read the source IP address. This is generally useful as the server needs this address to return your data. However, this also means that the server knows your IP address, which is where you live on the Internet. Your IP address alone reveals information about you, such as the country in which you live and your Internet Service Provider (ISP). Geolocating by an IP address can be accurate to the zip code level, when you use United States as an example.
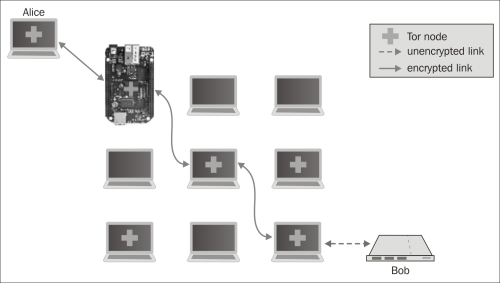
The following diagram shows this routing. In this case, Alice is a client who connects to the first node of her circuit, which happens to be running on your BBB. This BBB unwraps a layer and forwards Alice's communication to the middle node. The middle node does the same to the final (exit) node. The exit node sends Alice's original message to the destination server named Bob. The green arrows show internal Tor connections that are encrypted. The connection from the exit node to Bob is shown as an unencrypted connection because this traffic is not part of the Tor network. From Bob's perspective, the IP originator of this connection is the exit node. However, the true originator is Alice whose IP is hidden by the Tor network.
The response to this information by many individuals is:
"So what? Why do I care if the website I'm visiting knows my IP address?"
The website, which knows the data you requested, now knows your location. This information could be combined with other public information, for example, to conduct a linkage attack. A linkage attack is an attempt at deanonymization by combining information from multiple sources. For example, let's say you are searching for information on a rare medical condition. You post a question on a forum, under a pseudonym, asking for information. However, the website, and anybody passively monitoring your connection (if it wasn't encrypted), knows your general location as well as your question. Your medical condition is most prevalent in Hispanic females in their seventies. Using your IP address combined with knowledge about your medical condition, one can conduct a linkage attack possibly using public census data to reveal your identity.
Tor protects against this kind of attacks by encrypting your traffic through the Tor network and masking your IP address. To the remote website, your IP address will be that of the last node in the Tor network, known as an exit relay.
A wide range of people use Tor for daily Internet access. Individuals who don't want their ISP to collect information on the websites they visit, perhaps because they are seeking information on sensitive topics, use Tor. Government agents and the military use Tor. After all, it's difficult to go undercover online if the IP address you are connecting FROM resolves to fbi.gov. Tor is used by whistleblowers, such as Edward Snowden, to disclose information to the press. It is also used by normal citizens when a government blocks access to the Internet. In late March 2014, when the Turkish government attempted to ban access to Twitter, the number of Tor users in Turkey jumped from around 25,000 to just under 70,000 in about two weeks.
Note
Tor publishes, via a wide range of interactive graphs, numerous metrics on who is using Tor and where they're using it from. The users spike in Turkey can be seen in the graph available at https://metrics.torproject.org/users.html?graph=userstats-relay-country&start=2014-01-04&end=2014-04-04&country=tr&events=off#userstats-relay-country.
Tor relays are the individual nodes in the Tor network. A node is some type of computer that is running the Tor software. These relays route messages throughout the network. Exit nodes, which are the last nodes in the circuit, send the clients' messages to the destination service. One of the interesting aspects of Tor is that most of the nodes are run by volunteers. These relay operators volunteer their bandwidth, time, and energy bill to increase the capacity of the Tor network. The Tor Project encourages individuals to run relays in order to add to the diversity of the network. The motivation behind this recommendation is that it is easier to hide in a crowd—it's difficult to hide in a crowd of one person.
In 2006, in response to an increased Internet censorship, the Tor project added an anticensorship feature called a bridge relay or simply, a bridge (Dingledine, 2006). A bridge is a special form of a relay—it's not listed in the public relay directory. Strong Internet censors were able to block access to Tor through several methods. One method that was effective was to look up all the public relays, which were only a thousand or so at the time, and deny access to those IP addresses. Therefore, bridge relays were created and distributed by less public means in order to allow users to access the Tor network. If a client could access the bridge, which was already connected to Tor, then the client could access the Internet. In this context, less public means a distribution mechanism that does not work via the public relay list.
Censors were still able to block access to Tor; the technique was to identify the traffic patterns generated by Tor and block the connection. In 2010, Jacob Appelbaum and Nick Mathewson of the Tor Project suggested a method to obfuscate the Tor traffic between the client and the bridge in order to thwart deep packet inspection. As the obfuscation mechanism might need to change, and has changed in fact, the Tor Project wanted a generic protocol to allow different obfuscated proxies to run. This abstraction was known as pluggable transport.
In this chapter, we will set up your BBB to run as a Tor bridge, running an obfuscated proxy, using the obfs3 pluggable transport.
Tor is one of the best tools currently available to protect anonymity. However, like all the security tools discussed in this book, there are limits to its protection. First of all, Tor's threat model does not hold up to a global passive adversary. Such an adversary can passively monitor the entire Internet. If an adversary can monitor the entire Internet, then it can correlate the traffic entering the Tor network with the traffic leaving the network and can possibly deanonymize Tor clients. One of the trade-offs of this design is that Tor is a low-latency system, meaning that you can access the Internet using normal protocols such as HTTP without experiencing much delay. This is one of the reasons why diversity in the Tor network is important. If all the relays were in a particular country, it might be easier for that country to monitor the traffic. However, currently it is thought to be difficult, in spite of the recent leaks provided by Edward Snowden, for such an adversary to monitor the entire Internet.
Note
Roger Dingledine of the Tor Project commented on NSA's exploits of Tor with the following:
"The good news is that they [the NSA] went for a browser exploit, meaning there's no indication that they can break the Tor protocol or do traffic analysis on the Tor network. Infecting the laptop, phone, or desktop is still the easiest way to learn about the human behind the keyboard."
The full text and additional commentary is available on the Tor website (https://blog.torproject.org/blog/yes-we-know-about-guardian-article).
Also, Tor will not automatically encrypt all your traffic. If you request information over unencrypted HTTP, the Tor exit node you use will relay this unencrypted information to its destination. A malicious exit node can monitor or manipulate your traffic; therefore, it's always best to use encrypted sessions, such as HTTPS, over Tor. Tor does not protect all your traffic just because you are running Tor. Applications generally need to be configured to use Tor. Even if you set up a transparent proxy on your home network and route all of your traffic through that proxy, the malware or exploits in your browser may leak your identity. This is why the Tor Project recommends that you use the Tor Browser, which essentially is a forked version of Mozilla Firefox that has been patched especially to not leak your identity. Lastly, Tor can't protect your identity if you choose to reveal it. If you decide to log in to Facebook over Tor, you've just told Facebook who you are and that you are using Tor since all the Tor exit nodes are public.
Tip
An easy way to use Tor more securely is to use it only from Tails (https://tails.boum.org/), which is a custom Linux distribution that will boot from various media. Tails is a collection of free software and includes numerous correctly configured tools to help protect your confidentiality and anonymity.
So, why run a Tor bridge on BBB? The impact and benefits of Tor is in the network. The more the Tor servers, the more the resources in the network. Many users in developed nations have high-speed Internet connections that are orders of magnitude faster than in countries where access to censor-free Internet is restricted. A bridge is likely to receive less traffic than a relay, as there are fewer bridge users than normal Tor users. Most likely, the limiting performance factor for your bridge will be your home network's upload speed. This can be a constraining factor if you are running a relay, but as a bridge, you are most likely helping those in precarious Internet situations and any donated bandwidth is appreciated. Lastly, running a bridge on BBB has the extra advantage of a low impact on your electric bill, as BBB will only draw about 460mA when loading a web page according to the BeagleBone Black System Reference Manual.
