Threat modeling and system design is an iterative process. The system we built in this chapter is a good start, but it can be improved. We identified a problem at the beginning of the chapter in that we still had to enter the GPG passphrase from a potentially compromised computer. The code entry on the keypad is currently only protecting the GPG key when the BBB is powered off. It also protects the key if an attacker who doesn't know the code boots the BBB, since the PCR will not have the correct value after the 10-second window has passed. To mitigate against the key logger attack, we would want to enter a passphrase directly into the BBB.
There is a piece of software called gpg-agent, which manages your passphrase per login session. It can support different types of pin entry programs. For example, one pin entry program is X-Windows-based and another supports a command-line interface. You could certainly create your own pin entry program that supported your custom hardware. However, when you create this custom pin entry, you'd want to consider the effect of a potentially weaker passphrase, one composed of only numbers, for your GPG key. This demonstrates the importance of re-evaluating your threat model as new features are added to the design to ensure the correctness of the original assumptions.
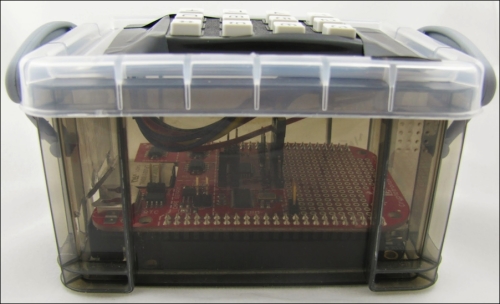
Also, you might want to consider adding an enclosure for your project. Your local hackerspace will be able to help you make a professionally looking enclosure. If you want something on the cheap, find a small translucent container and cut out room for the keypad and the connectors as shown in the following image: