CHAPTER 7: LAUNCHING THE ATTACK
Steps to an exploit
The objective of most attackers is to try to take over a compromised system and assume an elevated level of access. One way to accomplish this is to obtain a command line shell that can be used to execute system commands and run malicious code on the compromised system. There are several types of command shells that are used for local or remote access.
Local shellcode: Local shellcode is used to provide the attacker with access to a local machine that would otherwise restrict the access level of the attacker.
Remote shellcode: Remote shellcode is used to facilitate an attack that the attacker is executing across a network or on a remote machine.
Restricting shellcode: Many firewalls and intrusion detection systems (IDSs) will detect shellcode. Therefore, the attacker must frequently attempt to hide the presence of the shellcode using obfuscation, encryption, or breaking the code into multiple segments.
Writing a shell is beyond many attackers; however, there are several tools that are available to make the job of the attacker easier, such as Metasploit® and SAINT.
These tools will assist the pen tester in locating vulnerabilities and then provide several methods that can be used to exploit the access granted by the system.
Attacking wireless networks
Case study: TJX
TJX believes the intruder may have initially gained access to customer information via the wireless local area networks at two of its US stores. Customer information was stolen from mid-2005 through December 2006, a TJX investigation found. Some stolen information involved transactions dating back to 2002.18
The theft at TJX (which targeted HomeSense and Winners, amongst other stores) led to the compromise of the personal information – credit card and driver’s license details and banking data – of approximately 49 million people. This was an example of a chained exploit. The initial attack against the wireless networks in two stores in Miami, Florida, enabled a further attack against the Head Office itself. This attack demonstrates the importance of enforcing a security standard across the entire enterprise – a security hole in any one location may lead to a breach at other locations.
It has often been stated that having a wireless device in your office is the same as having an ethernet connection in your parking lot. This is not to say that the use of wireless should be discouraged or forbidden. We must secure the wireless access points we provide, just as we would a publicly available network connection.
Evolution of wireless security
Wireless security has been attempted through several approaches. The first approach was to hide the service set identifier (SSID) of the wireless access point. The SSID is the name of the wireless access point and, by default, it is set to be broadcast out. That enables any other wireless device in the area to detect the presence of the device and allow it to attempt to log in. Far too often, the name of the SSID is either left as the default setting or set to a company name. This allows a person to identify either whom the access point belonged to, or “find” it by searching for the default names. The question came of whether or not the SSID should be set to broadcast at all; would it be better for it to rather sit silently and only react when a person that knew its name attempted to associate with it? Hiding the name is a form of “security by obscurity”; it is not very effective, but arguments can be made that it’s better than doing nothing. Another approach taken by some companies was to intentionally broadcast the SSID, so that a legitimate employee trying to log in would know for sure that they were on the correct access point and not end up sending sensitive information over another rogue device.
Another level of security was the use of MAC filtering. The MAC address should be unique to each device; however, the MAC address is passed in the clear when a device attempts to associate with the access point. An attacker can easily determine the MAC address and spoof it to overcome that control. Using MAC filtering also places a heavy workload on the administrators when there are a lot of changes in personnel needing to be able to log in, since the MAC address for each device must be entered into the access table directly on demand.
The first wireless encryption that was available was provided through a standard known as Wired Equivalent Privacy (WEP). WEP used a good algorithm (RC4®), but in a poorly implemented manner. The initialization vector (IV) was too short and could be caused to repeat by flooding the access point with association requests. This made the “cracking” of the WEP key a fairly simple process.
When the vulnerability of WEP was found and disclosed, a quick fix was introduced. The new version was initially planned to be called WEP2, but was re-named Wi-Fi Protected Access® (WPA®) when it was thought that calling it WEP2 immediately after the weaknesses of WEP were disclosed would not inspire confidence!
WPA also used the RC4 algorithm and introduced the MIC integrity check and Temporary Key Integrity Protocol (TKIP). MIC provides some assurance that the packets are not being modified in some way as they are transmitted wirelessly, and TKIP improves the key generation process.
The next step in wireless encryption was the introduction of WPA2.® WPA2 uses the Advanced Encryption Standard (AES) algorithm in Counter mode, and uses CBC-MAC for integrity. This is commonly referred to as CCMP. WPA2 is a secure method of implementing wireless encryption and should be the standard for all organizations.
Pen testing wireless
Wireless devices pose a great risk to an organization if not implemented correctly – and they are often not. The usual problems, which are the same as those for almost all network devices, are: default configurations, weak passwords, encryption not being enabled at all, the continued use of WEP, and the installation of rogue wireless (unauthorized devices). Wireless devices, however, present an entirely new set of risks, as well. A wireless device can be attached to almost any point on a network, and an insecure or rogue device can be placed inside the firewall and provide an open, undefended door of opportunity onto the network for an attacker.
The first step in pen testing for wireless devices is to do the same as most attackers would do: walk around the physical location, detecting any wireless devices. This is often called “war-driving.” Several tools – from Netstumbler® to Kismet® and the Aircrack-ng set of tools – can help detect wireless devices.
The next step is to check whether the wireless devices have default configurations, or if they are located in a DMZ or separate area that would restrict access from the wireless device to the internal network. A valuable resource that can help the administrator or pen tester to learn more about wireless security is the www.wirelessdefence.org website.
Denial of service
As wireless devices become more and more essential in the support of business operations, the impact of a denial-of-service attack increases. Unfortunately, wireless devices share the same radio frequency (RF) bands as many other devices – ranging from microwave ovens to cordless phones and toys. A wireless device is easily affected by other devices operating in the same RF band in close proximity. Common attacks can be the simple jamming of the RF signal.
Another common attack against wireless is the propagation of disassociate or de-auth packets. Sending either of these packets out with the MAC address of the target device will cause the device to temporarily disconnect itself from the network.
IEEE 802.1x and the Extensible Authentication Protocol (EAP)
One of the most challenging problems associated with wireless is in knowing who or what is trying to authenticate. Some of the common methods of authenticating a device are IEEE 802.1x, EAP-TLS, and EAP-TTLS. The older EAP is not recommended for deployment unless very long passwords are used. EAP-TLS and EAP-TTLS support public key certificates that provide server authentication and validate the identity of the supplicant (the wireless device requesting permission to associate) via a RADIUS authentication server.
Network sniffing
Network sniffing is the capturing of traffic traversing a network. Many administrators will sniff network traffic in order to detect traffic problems, bottlenecks and network traffic issues.
If an attacker is able to sniff the traffic, they may find sensitive data that is not encrypted, log-in and password information, and other data related to business operations and error handling.
There are a several good tools available for network sniffing and protocol analysis, as seen in the table below.
| Program | Operating system | Source |
| Wireshark® | Windows® and UNIX | Free from www.wireshark.org |
| TCPDump | UNIX | Free from www.tcpdump.org |
| WinDump | Windows® | Free from http://windump.polito.it |
| OmniPeek® | Windows® | Purchase from www.wildpackets.com |
| Packetyzer® | Windows® | www.network-chemistry-packetyzer.software.informer.com |
| Cain & Abel | Windows® | Free from www.oxid.it |
Figure 26: Examples of packet sniffers and protocol analyzers
Active versus passive sniffing
Passive sniffing is the capturing of data without injecting, deleting or modifying it. Eavesdropping is an example of passive sniffing. A person doing passive sniffing frequently wants to remain unnoticed and sit quietly on the line, capturing data without anyone knowing that they are there.
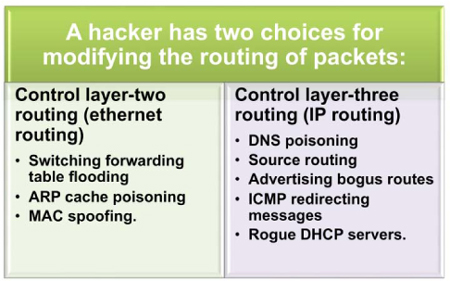
Active sniffing is done to make some change to a system or the data on the network. This may be achieved through efforts such as DNS poisoning, Address Resolution Protocol (ARP) cache poisoning, source routing or MAC spoofing.
ARP poisoning allows the attacker to pose as a legitimate user on the network. The attacker will then be able to capture all the traffic that is being sent to the other user.
DNS spoofing
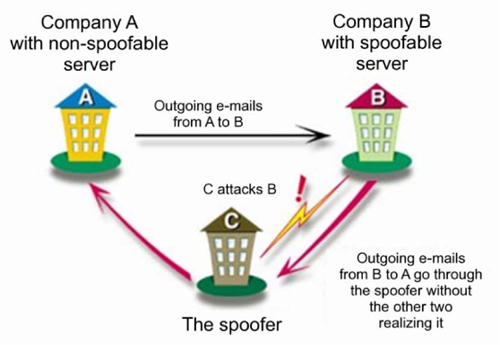
DNS spoofing has been a common attack to divert web traffic to illegitimate sites. The domain name server resolves the web address with an IP address. If an attacker can poison the DNS table, he will be able to have traffic intended for one location sent to another site of his choosing. This method has been used to divert the traffic for one business to another location, causing a denial of service and general embarrassment for the business. In the diagram which follows, you can see how diverting e-mail traffic would allow an attacker to intercept and monitor all traffic going from company B to company A.
Session hijacking
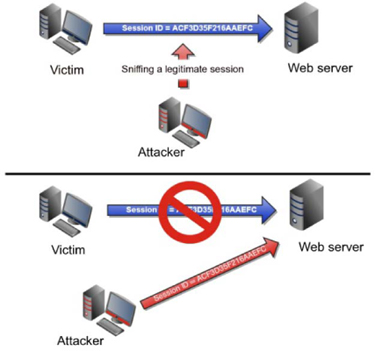
Session hijacking allows an attacker to hijack or take over a legitimate session between two other entities. The attacker sniffs the session ID being used between two parties and then sends traffic to the receiver using the correct session ID. This can fool the receiving session into thinking that they are still connected with the legitimate user that set up the connection initially. The attacker now has access to the receiver as if they are a legitimate user.
Fake SSL sessions
SSL uses certificates to validate the web server being connected to. If an attacker can insert themselves into the middle of an SSL connection that is being set up (execute a man-in-the-middle attack (MITM) through DNS spoofing or ARP poisoning), then they may be able to intercept the certificate exchange and send a fake certificate to the originator – fooling the originator into thinking that they are securely connected to a legitimate site, when they are, in fact, connected to the attacker. This has also been done by creating a fake SSL certificate registered to a name similar to the legitimate name of the organization. One successful attack of this type was carried out by an attacker registering an SSL certificate to a “.org” version of the “.com” address that a company had their certificate registered to.
Intercepting VOIP
In the next few years, we can expect most organizations to move towards the use of Voice over IP (VOIP) for telephone calls. This method provides several benefits to an organization, including better integration between data and voice services and potential savings on long-distance calling. However, VOIP packets can be intercepted as they traverse a network. Tools, such as Cain & Abel, will collect and reassemble VOIP packets, so that the person monitoring the network can listen in on the conversation.
Countermeasures for sniffing
There are several countermeasures that can be used to prevent network sniffing. The first is to use encryption to make any traffic (including VOIP) that is captured worthless. Other precautions are to use an intrusion detection system (IDS) to log and alert staff to any abnormal traffic flows or suspicious traffic. The administrator should also be watching for ARP poisoning. Users should be educated to not accept any certificates that are not from a known source.
Firewalls
Firewalls are used between networks to protect one network from any suspicious activity originating from another, and to prevent any improper traffic from going out of a network.
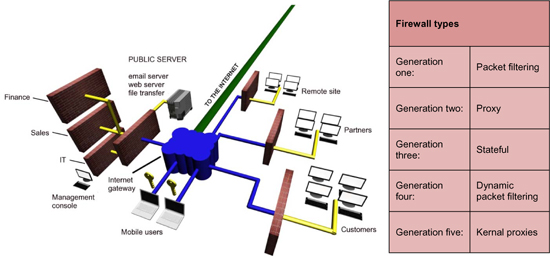
There are several types of firewalls, as seen in the table preceding. A firewall, however, is only as effective as the rules and administration used to set it up.
Network and firewall architecture
Networks should be protected in a layered defense model, with layers of control and defenses to protect the assets of the organization.
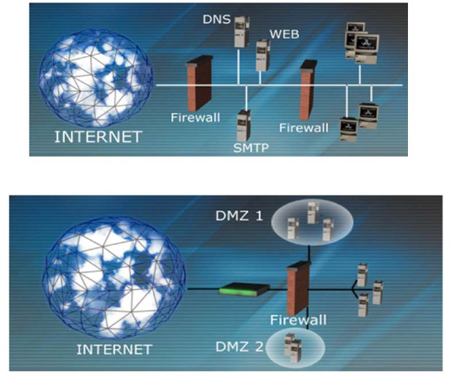
The core principle is that no traffic should be allowed from an untrusted network – such as the Internet – directly into the internal network. A demilitarized zone (DMZ) is an isolated network area that can be used by the organization to provide some restricted or limited services to clients gaining access from the Internet. An extranet is also an isolated network area, but it is usually used for providing services to business partners, and requires additional authentication or log-in (compared with that needed for a DMZ).
Figure 31: Firewall architecture
Circumventing firewalls
There are several methods used to circumvent firewalls, including fragmentation (breaking the elements of the attack into small pieces that may not be noticed by the firewall) and causing subsequent fragments to overlap previous fragments on reassembly. Often, the firewall is “blinded” by using encryption, so that the firewall cannot see what the content of the packet is.
Intrusion detection and prevention systems (IDS/IPS)
Intrusion detection systems are valuable network and host defense tools. An IDS will attempt to notice any suspicious activity (floods, protocol anomalies, or known malicious signatures) and log the event. The IDS may also alert an administrator or signal other devices to a potential problem. The IPS is more proactive and will attempt to stop any unauthorized activity. IDSs and IPSs should be used in combination with firewalls and other defensive tools in a layered defensive model. They may be network-based and used to monitor the activity on a network, or they may be host-based and watch for unauthorized activity on a host.
Key learning points
• Shellcode is often used by attackers to gain elevated system access. There are several types of shellcode, including local and remote shellcode.
• Shellcode can be detected by a firewall or IDS.
• Metasploit and SAINT are two tools used by attackers to gain privileged system-access.
• Wireless security has been provided by disabling SSID broadcasting, MAC filtering, IEEE 802.1x port controls, EAP, encryption and integrity checks.
• WEP and WPA use RC4 for encryption; WPA2 uses Advanced Encryption Standard – Counter with Cipher Block Chaining Message Authentication Code Protocol (AES-CCMP).
• War-driving is enabled by tools like Kismet, Netstumbler and the Aircrack-ng set of tools.
• Denial of service on a wireless can be accomplished by jamming the signal or flooding the network.
Questions
1. What form of integrity checking was used in WPA?
a) RC4
b) AES
c) Michael (MIC)
d) CCMP.
Answer: C
2. An effective measure to protect a wireless from unauthorized access from outside the building is to deploy:
a) Radio frequency (RF) management
b) SSID broadcasting
c) Michael (MIC)
d) RC4.
Answer: A
3. A wireless access point located near a microwave oven may be subject to:
a) MAC filtering
b) Open system authentication
c) ARP poisoning
d) Denial-of-service jamming.
Answer: D
4. Wireless access points operate in the radio frequency ranges of:
a) 900 – 1900 Mhz
b) 2.4 – 5 Ghz
c) 900 Mhz – 2.4 Ghz
d) 2.4 Ghz – 1900Ghz.
Answer: B
5. In order to protect internal networks, it is best to:
a) Place all wireless access points directly on internal networks
b) Have strict policies forbidding the use of wireless access points
c) Disable the wireless modems in all laptops
d) Install securely configured wireless access points in a demilitarized zone (DMZ).
Answer: D