CHAPTER 5: VULNERABILITY ASSESSMENTS
This section is one of the most important areas of concern for the systems, network and database administrators – as well as for the pen tester. Vulnerability assessment is the careful, thorough and diligent review of the target system from all angles and attack vectors. It is through a complete and comprehensive vulnerability assessment (VA) that all the possible means of attack are explored and, from this, the tester will be able to identify all potential attack vectors, potential weaknesses and possible entry points. A pen test without a comprehensive VA is incomplete and will often lead to a false sense of security. The vulnerability assessment will provide invaluable information for the administrators as well. This will assure them of whether there are previously unknown or unidentified holes in their security infrastructure.
Going back to the analogy of a walled medieval city, the pen tester can be seen as the General tasked with planning the attack to take over the city. The General must consider all possible attack angles in estimating the strength of the defenses, determining the best way to attack and deciding which resources are required to launch the attack. The General must walk around the city looking for weak points, examining defensive strategies and considering the best way to proceed. Without proper reconnaissance, the General may attack a point on the city that is well defended and miss the opportunity to attack via a port or gateway that is relatively undefended. A pen tester that only attacks from one angle, or attempts to evaluate a single control, cannot provide assurance to the organization that their infrastructure is adequately protected and that their security controls are robust and effective.
A vulnerability assessment can be defined as the systematic examination of a system to identify areas that may be at risk of an attack. The VA will lead to the evaluation of the effectiveness, completeness and adequacy of the controls, in order to provide the information required by the organization to strengthen their security, plan their security strategy; and by the pen tester to plan the next stage of an penetration-testing attack.
The results of the VA should be a list of potential vulnerabilities with a ranking of the relative risk level for each. Just providing a list of potential vulnerabilities, without providing a list of the relative importance of each vulnerability, can overwhelm an organization with data that is hard for them to sift through, and can make it difficult for the organization to set priorities for addressing the reported vulnerabilities.
The attack vectors
The advantage for a pen tester is that there are many more attack vectors available today than in medieval times. The wall of the city created a defined security perimeter that does not exist in a modern network. A network can be attacked at any level – from a physical to a hardware level, and from communications ports to the whole operating system. In addition, the application itself can be attacked directly through the network and any vulnerabilities in the application can overcome all the other network defenses in place. The problem is that most pen testers forget to assess all the vulnerabilities when they conduct a pen test – they focus on technical issues and web applications, overlooking the many other avenues of attack that could be exploited. Many amateur hackers make the same mistake, but professional attackers and advanced persistent threats (APTs) will test every possible attack angle until they discover an open vulnerability or attack vector.
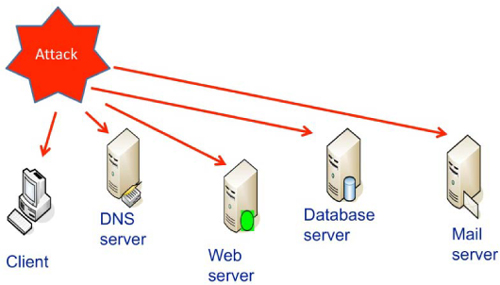
Figure 15: Attack (and test) vectors
A medieval city could usually only be attacked on one plane – the ground or, perhaps, a tunnel under the ground – but a network must be defended at every level, every angle, and in such a way as to not only protect against external threats, but also against internally-based threats or misuse.
Estimates claim that 48-70% of all successful attacks were made possible through an internal factor, such as a misconfiguration, social engineering or employee malfeasance. The pen tester should watch for such vulnerabilities and ensure that the organization is protected from internal threats, as well as external attacks.
Testing for the effectiveness of a security control often consists of three levels of evaluation. The first involves ensuring that the control was indeed implemented as designed. There can often be a mismatch between design and implementation, and this may lead to an undocumented gap in the security fabric.
The second level of evaluation involves ensuring that the control is working correctly – in other words, that it is performing the function that it was designed to perform (i.e. a firewall needs to be tested to ensure that it is, in fact, blocking the unwanted traffic, yet allowing authorized traffic).
The third level involves comparing the effectiveness of the control with regard to minimizing risk. Every control is implemented for a reason – and that is to counter a risk. No organization should implement controls that are not needed, nor should they ignore serious risks and not implement the appropriate levels of control. However, a control that was implemented correctly (according to the design) and is operating correctly may still be ineffective if it is not mitigating the risk as was intended by the designer. This is the true art of pen testing. Trust nothing. Test everything. The fact that a front door is locked is of little value if the backdoor is open; a firewall that is working correctly and according to the design is of little use if it is installed in the wrong place. This is where the skill of the pen tester in finding and enumerating every vulnerability (according to the scope of the project, of course) is proven. As it is written in one document, the task is to discover the information protection needs of the organization. “Discover” is a very accurate and appropriate word. Vulnerability assessment is not just about filling in a checklist or running a tool – it is the voyage of discovery and investigation. In many cases, it is discovery; the organization itself does not know its security needs, vulnerabilities and requirements and it is the knowledge and expertise of the pen tester that will reveal these needs to them.
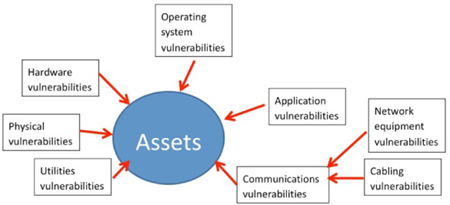
References and sources of vulnerabilities
There are many good sources available that list known vulnerabilities in equipment, protocols, systems, software and configurations. The pen tester should be familiar with these sources and examine the target systems to ensure that these known vulnerabilities are not present on the system. In most cases, it will be found that known problems still exist on the network, and resolving those issues is the first step in enhancing the overall security of the system. After all, if the presence of a vulnerability is well known to the security community, then it must be assumed that attackers know to look for those weaknesses too.
Some of the sources available to the pen tester and administrator that give information about vulnerabilities include:
| Organization | Website |
| SANS | www.sans.org |
| National Vulnerability Database | http://nvd.nist.gov |
| Common Vulnerabilities and Exposures | http://cve.mitre.org |
| Security Focus | www.securityfocus.com |
| Security Radar | www.securitywizardry.com/radar.htm |
Figure 17: Sources of information on vulnerabilities
Using vulnerability assessment tools
There are excellent tools available for conducting a vulnerability assessment, and each tool is an important part of the pen tester’s arsenal. Most of the tools require practice and further analysis, but they can conduct a wide range of tests in a relatively short time, and provide a very good series of tests against common vulnerability lists and industry-leading resources.
Some of the common tools are:
• Nessus®
• SAINT®
• Retina®
• Qualys.®
Reliance on tools
The pen tester must combine their expertise with the use of tools in order to provide meaningful results. A tool is only as good as the user, and the tool can never replace some of the expertise and creativity of an excellent pen tester. A tool will indicate possible vulnerabilities, but many of the issues found by the tool may be false positives (problems that are indicated, but are not really problems); a tool may also miss some important vulnerabilities – false negatives (problems that exist, but were not identified by the tool). The pen tester must review and examine the results generated by the tool to determine which issues identified by the tool are serious, which are of medium concern, and which issues may be put aside for future review, or ignored altogether.
Patch management
Patch management is a never-ending and challenging task for operations and administration staff. New patches may come out from various vendors at unpredictable times and with varying levels of importance. Some patches are released in an emergency scenario – where a serious exploit of a vulnerability in software may be imminent or already known – while other patches may be less critical and only designed to address performance issues or small glitches in an operational function. The administrator is firstly challenged to roll out the patches to the systems – which, of course, firstly means that the administrator must be aware that a patch has been issued. This administrator must then address both the risk that implementing the patch will affect other business operations and the difficult job of arranging for the systems to be brought down for enough time for the patch to be applied.
Because of these challenges, a vulnerability assessment often finds that the patch levels on systems are not up to date. This situation can pose a very serious risk to the organization.
PCI DSS requirements
For organizations that process payment card data (from credit and debit cards), there are industry standards13 that must be met to protect cardholder data and prevent the compromise of sensitive information. These standards provide an excellent summary of some of the actions that an organization can take to create a secure operational environment. The standards include the use of a firewall, demilitarized zone (DMZ) and anti-virus product, as well as the regular (quarterly) review of the security of the organization’s systems. The quarterly vulnerability assessments are designed to ensure that the organization maintains an adequate security posture.
Malicious code
The test of any network or system should also include a review to see if the organization has been infected with some form of malicious code. There are many forms of malicious code that can infect an organization and be used to open backdoors for an attack, capture passwords or other sensitive information, and damage or destroy system services.
Many forms of malicious code spread through e-mail attachments, infected websites or by wrapping themselves in other programs to hide their presence. Once in a system, they may alter registry settings, so that they start automatically whenever the system is started.
More and more, we see that modern malware is not designed to damage systems, but rather to provide a way for an attacker to gather information about a target, or provide the opportunity for the attacker to gain access to the target at any time in the future.
Spreading malware
The original method of distributing malware was via floppy disk (sometimes called the “sneaker-net”). This idea has not disappeared; a lot of malware still spreads via USB sticks or other portable storage media. In the past decades, a lot of malware was spread via e-mail attachments (including that for the attack on RSA). An unsuspecting user that opens an e-mail attachment containing a virus is immediately infected by that virus. Another popular method of distributing malware is by infecting a user that visits a malicious website. Several forms of malware will use more than one method of distribution in order to be more successful.
The Stuxnet worm represented a major development in the evolution of malware, since it targeted programmable logic controllers (PLCs) – a high profile target not previously targeted. Over the next few years, we may see a lot of malware targeting new systems, such as smartphones, SCADA networks, Voice over IP (VOIP), and mobile applications.
Viruses
Early viruses: The first virus, “Brain,” was developed over 25 years ago. Many of the early viruses were boot-sector infectors and would spread by replacing the boot sector of a floppy disk with infected code. Later viruses were more potent and learned to spread via networks and e-mail. A virus traditionally required the user to perform some action to trigger it – such as opening an attachment, or installing a portable media device.
Macro viruses: A macro virus infects via the macro capability of office software – often attaching itself to a document or spreadsheet.
Stealth viruses: A stealth virus attempts to hide its identity by changing subject lines, or altering or encrypting its code.
Polymorphic viruses: A polymorphic virus mutates itself, so that it changes slightly with each infection. By doing this, it attempts to hide from anti-virus engines that are looking for a specific virus signature.
Compression viruses: A compression virus executes when its code is decompressed.
Multipartite viruses: A multipartite virus is one that may circulate in several different ways and may spread more than one type of infection. Code Red and Nimda were examples of viruses that worked in a pair to leverage the security hole created when a system was infected by their pair virus.
Worms
A virus usually required the user’s action to trigger the virus and launch the payload, but a worm usually spread on its own, normally by exploiting a vulnerability in software. SQL Slammer was an example of a worm that exploited a vulnerability in unpatched systems. It spread across the world, infecting over 70,000 machines in the first ten minutes of its life.
Logic bombs
A logic bomb is a type of malware that will trigger at a specific event or a time. A logic bomb can lie dormant on an infected machine for years, waiting for a certain condition to be met before it triggers. Some examples of logic bombs would trigger on a date or when a certain file was created.
Spyware and adware
Spyware is used for surveillance and captures activity on a system. Spyware can record valuable information for an attacker, including passwords, sensitive data and user behaviors. Companies also use surveillance software to record the activity of employees.
Trojan horses
A Trojan horse is a malicious program that is hidden within another program or utility. The Trojan is malicious, but the program it is hidden in appears to be useful or attractive to the user. Trojans are often hidden in documents, music or video files, photographs or bitmaps. The user may be tricked into accepting a Trojan by opening or downloading the seemingly useful program it is hidden in.
Zombies and botnets
A common problem today is the presence of massive, robotically controlled networks (or botnets) that consist of thousands (or, in some cases, over one million) compromised machines. A botnet is created by infecting vulnerable machines with a zombie program, which listens for commands issued by the owner of the botnet from a central command and control centre. The bot-herder or controller of the botnet can use the infected machines to perform various functions, such as the distribution of spam and distributed denial-of-service (DDoS) attacks.
In most cases, the owners of the infected machines that are part of a botnet are not even aware that their machine is a part of an illegal network. A person becomes a part of a botnet when they do not have adequate protection for their machine and it allows an attacker to infect their machine with the zombie agent. It is only through the deployment of security tools and patches that a potential victim can avoid being infected.
Denial of service (DoS) / distributed denial-of-service (DDoS) attacks
A denial of service prevents a user from using their systems or equipment. Many types of malware cause a denial of service – from the old “ping of death” attack that would cause equipment to fail by sending a mal-formed ping packet, to the SYN flooding attacks used to overwhelm networks and web servers.
One of the most challenging attacks to prevent has been the distributed denial-of-service attack. In a DDoS attack, the attack is amplified by using many machines (often in a botnet) to attack a target simultaneously. Such attacks are difficult to prevent or to stop, as was seen in the DDoS attack against the IP addresses for the country of Estonia in 200714. Given the size of botnets available today, it would be very simple to launch an attack against a country or company that would render it totally isolated from web-based communications.
The DDoS attack is one of the new attack vectors being developed. Further information about this can be found in an excellent book by Richard A. Clarke: Cyber War: The Next Threat to National Security and What to Do About It, HarperCollins (2010)15.
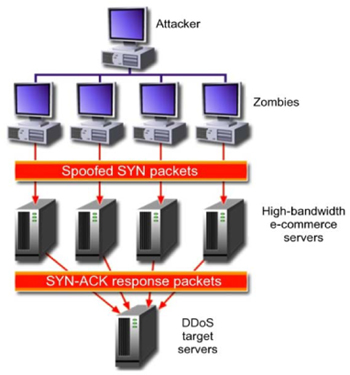
As seen in the above diagram, the attack is “amplified” by having many compromised computers participate in the attack. This makes the attack much more powerful, and also helps hide the true source of the attack.
Liability
If an organization’s machines are used in the perpetrating of illegal activity that may cause damage to another party, there is a risk that the source organization may be held liable for damages caused. Therefore, all organizations must watch for the traffic outgoing from their firewalls to ensure that malicious traffic is not originating from within their internal network. This is where tools, such as Netcat,® which monitors the types of traffic that are passing through the network perimeter of the organization, can be helpful. The organization must also review its registry settings manually to detect any suspicious executables that have been installed into the registry.
Countermeasures
The most effective countermeasure for malicious code is user training. There are no tools or technology that can avoid infection if the users commit an improper act, such as opening a malicious e-mail attachment. The next step is to have a current anti-virus program that is used to monitor network traffic and scan hosts on a regular basis with the latest anti-virus signatures.
Reporting on the vulnerability assessment
The results of the VA and the ranking of the various vulnerabilities can be presented to the organization as a valuable review of their current security posture, or can be used in the next step of the pen test: the actual attempt to exploit the identified vulnerabilities. The report should also include a note of any unpatched systems or other administrative weaknesses.
Key learning points
A vulnerability assessment is one of the most important steps in evaluating the security profile and posture of the organization. Every organization should perform regular reviews and vulnerability assessments of their security and control framework to ensure that they are not vulnerable to new or emerging threats, and that the controls they have in place are working effectively.
The tester should use tools, but combine those tools with their own experience and expertise to ensure that the results of the assessments are accurate and meaningful.
Questions
1. A vulnerability assessment attempts to:
a) Exploit any vulnerabilities in the network or systems found by the tester
b) Focus on key areas of risk and known vulnerabilities in order to be more efficient
c) Discover any weaknesses or flaws in the system being reviewed
d) Leverage the use of powerful tools in order to minimize human involvement.
Answer: C
2. From a security perspective, patch management is important to:
a) Ensure system availability
b) Protect the systems from new or emerging threats
c) Defend the network equipment from application-based vulnerabilities
d) Update all systems to improve performance and functionality.
Answer: B
3. The next step, following the use of a vulnerability assessment tool, is to:
a) Report on the findings of the tool
b) Analyze the results to determine the seriousness of the findings
c) Immediately patch all serious identified vulnerabilities
d) Perform a targeted penetration test.
Answer: B
4. Compliance with PCI DSS requires merchants that handle large numbers of transactions to conduct vulnerability assessments:
a) Annually
c) Monthly
d) Weekly.
Answer: B
5. Common tools used in conducting a vulnerability assessment include:
a) Nessus
b) SANTA
c) Eeye
d) imap.
Answer: A
13 www.pcisecuritystandards.org/.
14 http://arstechnica.com/security/news/2007/05/massive-ddos-attacks-target-estonia-russia-accused.ars.
15 www.amazon.com/Cyber-War-Threat-National-Security/dp/0061962236/ref=pd_sim_b_5.
