APPENDIX 2: ENCRYPTION
Concepts of cryptography
Cryptography is the art and science of transmitting and storing data in a format that cannot be understood by an unauthorized party. Cryptography has been a key part of secrecy used by the military, governments and tradesmen for thousands of years. Evidence of this can be seen in some of the early samples of encrypted writing used to protect intellectual property in ancient Mesopotamia.
Cryptography is used today for more than just secrecy. Modern cryptography leverages the additional benefits provided by public key or asymmetric cryptographic systems for secrecy, integrity, access control, non-repudiation and authentication.
The following is a very high-level overview of cryptography intended to provide the pen tester with an understanding of the basics.
The definitions and operations of cryptography
Cryptography is the altering of a message into a format in a way that protects it from unauthorized disclosure or modification. The original message in its unaltered format can be called cleartext or plaintext. In this format, it is unprotected and, therefore, readable or understandable to virtually anyone that has access to it.
The alteration of the message is performed by a cryptosystem that will transform the plaintext into ciphertext or a cryptogram. This process is known as encryption. The alteration is performed according to some mathematical operation known as an algorithm. Each person that uses the cryptosystem can select their own secret value – the key or cryptovariable (similar to a password) needed to govern the operation of the algorithm and make the encrypted message unreadable to anyone that does not have the proper key. In this way, many people can use the same algorithm and cryptosystem and still know that other people cannot read their encrypted messages. The secret to cryptography is the protection of the key and making sure that unauthorized people are not able to gain access to the key, and, therefore, be able to decrypt the encrypted message.
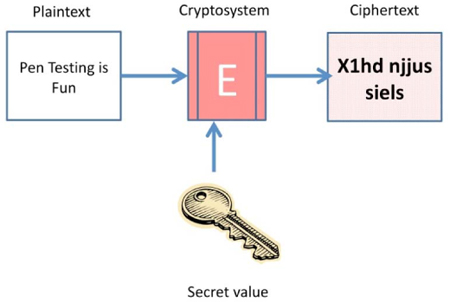
The two most common operations performed by the cryptosystem are substitution or transposition of the data in the message. Substitution is where the value of one letter in the plaintext is exchanged for another letter – for example, the letter “A” in the plaintext is substituted for the letter “D.19”
Transposition is where the same letters are kept in the plaintext, but they are put in a different order. The word “exam” may then be written as “aemx.”
Even the most modern cryptosystems rely on substitution and transposition.
Symmetric algorithms
Symmetric algorithms use the same key for both the encryption and decryption of a message. If a message is encrypted with a key value of “19748652,” for example, then the same key must be used to decrypt the message. Anyone that had that key would be able to decrypt the encrypted message, so the protection of the key is of primary importance.
Symmetric algorithms are relatively fast and provide high levels of confidentiality. Some of the most commonly used symmetric algorithms include the Advanced Encryption Standard (AES), the older Data Encryption Standard (DES), RC4 (a stream-based cipher used in WEP and WPA), and MARS.®
The disadvantages of symmetric algorithms are scalability and key management. For two people to exchange encrypted messages, they must share the same key. For each pair of people that want to exchange messages, a different key is needed. The more people that want to exchange messages, the more keys are needed; this can become an administrative challenge. All of those keys must be protected, stored and transmitted securely to each party in the data exchange.
19 The Caesar cipher operated in this manner – merely substituting the letter in the plaintext with the letter three places over in the alphabet. “A” would, therefore, become “D”; “B” would become “E”, etc.
Asymmetric algorithms
In the mid 70s, the world became aware of a new method of encryption known as asymmetric or public key encryption. Instead of using one shared key to both encrypt and decrypt a message – like symmetric key encryption does – asymmetric encryption uses a key pair. The keys always work in a pair where, if one half of the key pair is used to encrypt a message, the other half of the key pair must be used to decrypt the ciphertext of the message.
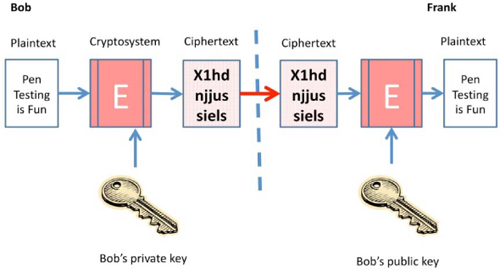
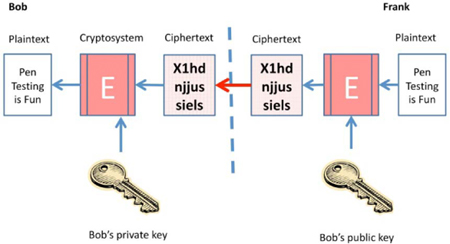
The key pair is comprised of two key halves. One half is the private key, which is owned and used only by the owner of the key pair. The other half of the key pair is known as the public, and can be shared with everyone and anyone. If Bob owns the key pair, he can encrypt a message with his private key. The only key that can open that message is Bob’s public key. To the recipient of the encrypted message, this provides proof of origin. They know, since they can open the encrypted message with Bob’s public key, the message must have come from Bob. This is known as non-repudiation or proof of origin. A message encrypted with a private key is known as a “signed” message. Since it can be said that the owner has “signed” the message, it can be proven who sent the message. A message encrypted with a private key can be decrypted by anyone with the public key. As a result, it is not really confidential – but at least it is known who sent it.
If Frank wants to send a message to Bob confidentially, he will just encrypt the message with Bob’s public key. Since Bob’s private key is the only key that is able to open a message encrypted with Bob’s public key, Frank knows that only Bob will be able to decrypt and read the encrypted message.
Certificates
One of the challenges of public key cryptography is proving that Frank truly has Bob’s public key, and that he has not been sent an imposter’s public key instead. This could happen in the case of a man-in-the-middle attack, where an attacker has managed to place themselves into the middle of the key exchange process. One way to prevent this is through the use of certificates. A certificate is issued by a certificate authority (CA). The CA issues a certificate following the X.509 standard that attests to the correct ownership of a public key. When Frank receives a certificate from a trusted CA, he is confident that the public key that is in the certificate belongs to the owner of the certificate.
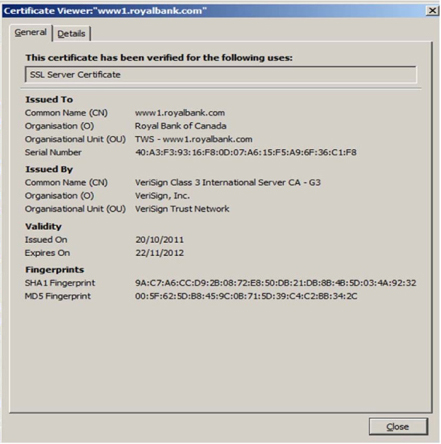
This example shows the public key certificate issued by VeriSign (one of the best-known CAs) to the Royal Bank of Canada (RBC). As can be seen, this is a Class 3 certificate – which means it has met stringent rules for registration and issuance, so that the client knows the certificate is genuine and associated with the Royal Bank. The example also shows that the certificate has not expired, so it is still valid (unless placed on a certificate revocation list – but that is a discussion for another time).
Figure 41: Certificate contents
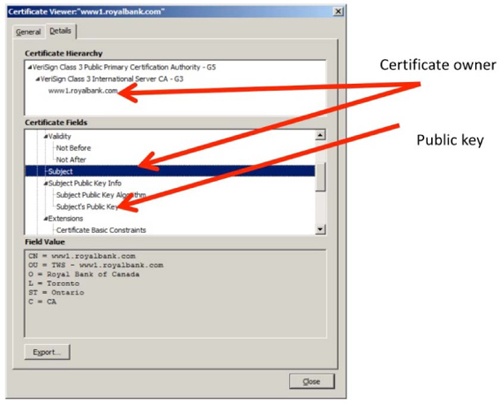
When a user clicks on the “Details” tab at the top of the certificate, they can see the certificate contents. As seen here, the certificate contains the name of the subject – the owner (in this case the Royal Bank) – and the public key of the owner. Clicking on the public key field would display the 2048 bit RSA® public key of the Royal Bank. Now that the user has the public key of the bank, they can encrypt data with that public key and send it to the bank, knowing that no one else can read or alter their message, since only the Royal Bank would have the correct private key needed to open the encrypted message.
Characteristics of asymmetric algorithms
Asymmetric algorithms, such as RSA and Elliptic Curve Cryptography (ECC), are powerful and useful tools in today’s world of network encryption and e-commerce. A user anywhere in the world can communicate securely with a company or government agency by using the public key of the company or agency to encrypt the message they want to send. The key management problem symmetric algorithms have of needing a separate key for every pair of users is solved. One public key is enough for everyone to communicate securely with an entity. If a user “signs” a message with their private key, then the receiving party also knows who sent the message (a benefit known as non-repudiation).
However, there is a problem. Asymmetric algorithms require intense amounts of processing power and time. They are very slow compared with symmetric algorithms, and it would be unfeasible to use an asymmetric algorithm, such as RSA, to encrypt a large message. It would simply take too long to encrypt and decrypt (perhaps even days!)
Hybrid systems
The challenges of asymmetric algorithms being too slow to use effectively, and of managing all the key pairs required to use symmetric algorithms are overcome through the use of a hybrid system.
A hybrid system uses asymmetric algorithms to solve symmetric algorithms’ problem of key management, and employs the speed of symmetric algorithms for bulk message encryption.
In a hybrid system, the originator of a message (Bob) can encrypt the message using a symmetric algorithm (such as AES). This provides fast encryption and very good levels of confidentiality.
Using the public key of the receiver (Frank), Bob can send the AES key used to encrypt the message to Frank by encrypting the AES key with Frank’s public key.
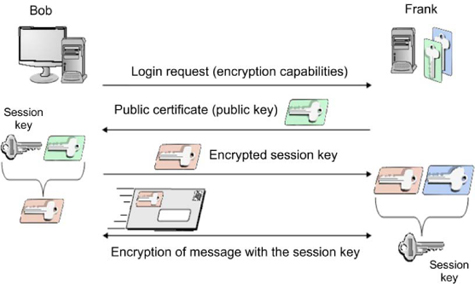
As seen from the diagram, SSL is an implementation of a hybrid system. Bob sends a message to Frank to say that he would like a secure log-in to his web server. Frank replies with his public key certificate, so that Bob knows he is using Frank’s public key – not that of an imposter pretending to be Frank. Bob can encrypt the AES key he will use for this log-in session (hence the use of the name “session key” for this AES key) with Frank’s public key. Even though public key algorithms are slow, the AES key is very short and will not take much time to encrypt and decrypt.
Now both Bob and Frank have the session key they require, they can communicate securely over an untrusted network. This is the process used for many Internet services, such as online banking and shopping. Most virtual private networks (VPNs) also use this type of hybrid encryption to set up a secure encrypted tunnel for two parties to communicate over.
Message integrity
When two parties are communicating, there is always the risk that the message will not be received correctly at the far end. Especially when communicating over a noisy or insecure network, the message may be altered by noise or the intentional actions of an attacker as it moves from one point to another. This is why message integrity checks are so important. When conducting e-commerce, a store needs to know exactly how many products to ship and where to ship them to. A bit of noise in the network may change the data and result in the wrong products being shipped to the wrong places.
Early forms of integrity checks were carried out through parity bits, checksums and check digits, but those can all be altered by an attacker using a man-in-the-middle attack.
Hashing
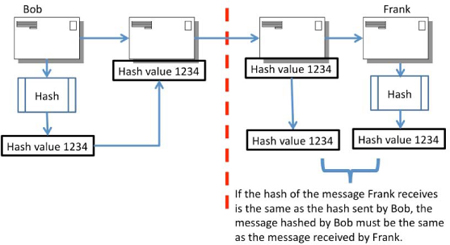
In order to ensure the integrity of a message today, hash functions are used. It will be easier to understand this topic if you remember that hash functions are for integrity – not for encryption. The user of a hashing algorithm, such as MD5® or SHA-1 (or the other SHA variants), will run the message through the hashing algorithm to generate a digest or hash of the message. The hash is simply a small value (in the case of MD5, 128 bits in length) that serves as a fingerprint or representation of the message. A hash is extremely accurate; if one bit of the source message was to be changed, then at least 40% of the hash of that message would be different. In this way, the users of the hash are confident that, if the hash of a message that is received by the receiver is the same as the hash value sent by the originator of the message, then the received message is an exact copy of the original message.
Digital signatures
Earlier in this chapter, it was noted that an advantage of asymmetric algorithms was that they could prove who sent a message and establish the principle of non-repudiation. To repudiate is to deny, so non-repudiation is to have a way to prevent a person from being able to deny something. This is a serious concern in e-commerce, as a person may later want to claim that they were not the person that ordered a product or told a stockbroker to sell their shares. We saw that if a message was “signed” with a private key, the receiver would know who the originator of the message was (since they could validate the signature with the public key of the originator). But we also saw that encrypting or signing a large message with asymmetric algorithms could require days to decrypt it, so that is not a feasible solution.
In the paragraph on hashing, we saw that a hash was a small fingerprint of a message that could prove the integrity of the message. So, what happens when we combine hashing with signing? We get a digital signature. A digital signature proves the source (non-repudiation) of the message, as well as the integrity of the message (demonstrating it has not been altered). Remember that a digital signature is not the same as a digitized signature – a digitized signature is just the scan of your autograph.
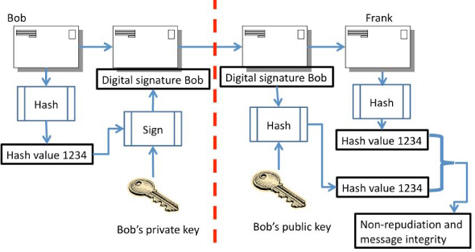
As seen in the diagram, a digital signature is created by encrypting (signing) a hash of the message with the private key of the sender (Bob). The digital signature is then appended to the source message and sent, along with the message, to the receiver (Frank). Please note that the message was sent unencrypted in this example – a digital signature may be used with the encryption of the message, but this is not mandatory. The Digital Signature Standard (DSS) does not address the confidentiality of the message – just the source and integrity of it.
When the receiver (Frank) receives the message and the digital signature from Bob, he will validate the digital signature by opening the signature with Bob’s public key. Then, he will generate his own hash of the received message and ensure that the hash he creates is the same as the hash signed by Bob.
Uses of cryptography
Cryptography has many uses today: for passwords, VPNs, secure e-commerce, and storage and transmission of sensitive information, for example. Cryptography provides many benefits for organizations, but it must be used carefully, and implemented correctly. The pen tester should test the security of the cryptographic implementation and ensure that keys are chosen properly and protected from compromise.
Some of the risks associated with cryptography are also in the way that an encrypted packet may avoid scrutiny from firewalls and intrusion detection systems. Attackers have also held an organization hostage by encrypting the files of the organization and only selling the encryption key back to the organization at a price. Employees can also hide their actions by encrypting files and communications.
There are many ways to attack cryptographic implementations, but the easiest way is always through social engineering or by taking advantage of errors by employees or administrators.