Linux has become a very important player as a mainstream operating system for servers. According to the Netcraft report of most reliable hosting company sites dating from February 2010, 6 out of 10 servers were running some brand of Linux. This indicates the strong position of this Operating System (OS) and the confidence it generates. Some of the reasons for this are:
- Initial price: Linux is open source and therefore free for commercial use
- Stability and Reliability: Linux is a highly stable and reliable platform with all of its elements well tested; any bug is usually quickly resolved by the community
- Security: Linux is, by default, quite secure and is in fact in a much better position than Windows since it is at risk from much fewer viruses and Trojans
- Better utilization of hardware resources
- Availability of commercial support
Another reason for which we are starting with Linux is because Moodle is primarily developed on Linux using MySQL, Apache and PHP, also MySQL (at least until version 5.5) is vastly superior on Linux.
In this chapter we will cover the following topics:
- Securing your Linux—the basics
- Apache configuration
- PHP configuration
- MySQL configuration
- File security permissions
We will try to explain the basic elements of Linux on which you should focus your attention during initial configuration.
A Firewall is a part of a computer system designed to block or permit network communication based on set of predefined rules. The design and operation of the Internet is based on the Internet Protocol Suite, also commonly called Transfer Control Protocol / Internet Protocol (TCP/IP). In this system, hosts and host services are referenced using two components: an address and a port number. For example, HTTP—standard web protocol uses port 80 by default. In general, most services use a limited number of ports. A common technique for detecting running services on a public server is port scanning. It is used by administrators for verification of their security policies and by hackers for obtaining lists of potential targets for later attack. To prevent this and other types of misuse we should block access to all ports except the ones we want to expose to the public. This blocking is done by firewalls. They can be available either as hardware appliances or software service running on the server.
In this chapter and throughout this book, any practical examples offered for Linux apply to CentOS 5 Linux, which is an open source version of Red Hat Enterprise Linux 5 server. Firewall comes as standard in the out of the box product, so we will first show how to enable and configure it for safer functioning of our Moodle server.
- Open the command line prompt, logon as the root to your server and execute command setup.
- In the following screenshot we have several options for configuring various system services.
- Select Firewall configuration option.
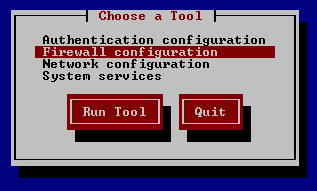
- On the firewall page we can see the following options:
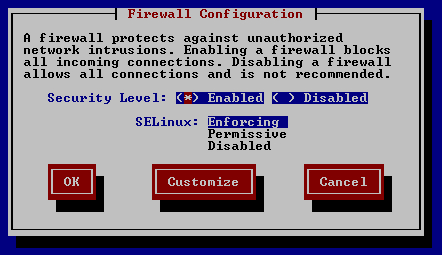
- Set firewall to Enabled, but keep in mind that it will block all incoming connections from the Internet. This is too secure for our use case as we actually need to open a few ports. For this, we need to customize a further Firewall configuration.
- Choose Customize options from the dialog to enter into the firewall customization section.
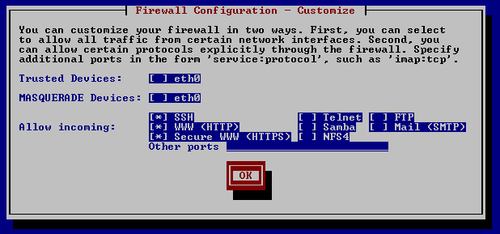
As you can see, we have selected the SSH, WWW, and Secure WWW options. These three are what are usually needed to have properly exposed web-server service. SSH service is enabled because it offers a standard access for remote administration of the server. In case you have another way of configuring your server, you can disable SSH.
In the 1983 movie "WarGames" there is a very characteristic scene with a young Matthew Broderick. In that scene we see him in front of the principal's office waiting for his meeting. On his left side there is an empty seat with a computer terminal linked to the school's computer system. As a young hacker he is keen on entering into the system without being noticed. The curse of forbidden fruit is again at work. In order to enter into the system he needs a valid password. Knowing how people hate remembering passwords, he assumes that it is probably written somewhere near the terminal so that whoever works there will be able to login without too much hassle. He opens a bottom drawer and voila! A piece of paper is glued to the drawer with the latest passwords, ready for use. We also note that all of the passwords are simple dictionary words like effort, points, double, pencil, etc. He later uses that knowledge to enter the school computer system and modify his grades to the desired level.
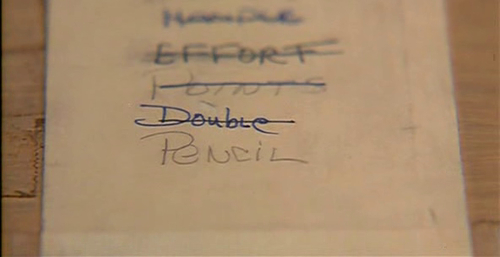
This example from a Hollywood movie is actually based on some real facts. People hate remembering more than two or three passwords, so they try to apply them to all their services and accounts. This is exactly what a responsible administrator must not do. Using simple and standard dictionary words (dog, cat, table), or other personal or institutional names and idioms as your password is a serious security breach. It exposes your system to a possible "dictionary attack".
This example from a Hollywood movie is actually based on some real facts. People hate remembering more than two or three passwords, so they try to apply them to all their services and accounts. This is exactly what a responsible administrator must not do. Using simple and standard dictionary words (dog, cat, table), or other personal or institutional names and idioms as your password is a serious security breach. It exposes your system to a possible "dictionary attack".
Note
Dictionary attack is a technique for defeating authentication mechanisms by trying to determine its pass-phrase by searching likely possibilities.
An example of bad password would be john1975 or master.
An example of good password would be WxIYAURj.
You can generate passwords using one of the free online sites like www.freepasswordgenerator.com.
An important step in securing your Linux server is to determine its primary role. An administrator should know exactly what is installed on his system because otherwise it could be difficult to secure everything available, and overall security will be lower than it should be. You should review the list of packages installed and remove unnecessary packages that do not comply with your security policy. If you do this properly, you will have a lean system that occupies minimal resources and a limited list of packages to update and maintain when security alerts and patches are released. For example, if you do not use FTP, remove it. It is also a good policy not to have any development packages on a production server. Unless you need custom compiled packages, try to build them on a separate machine and deploy them precompiled to all the other production boxes.
All software has bugs, and those bugs can prevent it from functioning properly. Some of the bugs do not directly affect program functioning, but instead create security holes. These security holes can be (and often are) exploited by malicious attackers. It is therefore crucial to update all of your essential packages either from a distribution repository or by manual installation. CentOS offer updates through YUM.
Note
The Yellowdog Updater, Modified (YUM) is an open source command-line package-management utility for RPM-compatible Linux operating systems.
As a responsible administrator you should evaluate all package updates and decide if you should perform the update or not. It is recommended to have a written security policy and procedure to handle Linux security updates and issues. Assuming we will have Moodle installed on a single production machine with Linux, Apache, MySQL, and PHP (also known as LAMP); we should primarily focus on these packages and make sure they are updated accordingly.
