Apache web server is one of the most popular implementations of web server on UNIX-like operating systems. As of February 2010, Apache served over 54 percent of all websites on the Internet. It is a stable and reliable software recommended for both high and small load websites. It is easily configurable and highly flexible because it features modular design which permits to use only parts of the functionality that we really need. This reduces memory footprint and makes server faster to operate and respond. We still must be sure that it is properly configured in terms of basic functionality and security.
When attackers want to infiltrate a website they start first by probing for server information. If not properly configured, a web-server can expose sufficient information to the prying eye that can enable the attacker to find a security hole and access private data or services.
All communication between the web browser and web server is performed according to the Hyper-Text Transfer Protocol (HTTP). This protocol is fairly simple. A client sends a request for a resource and the server responds with an appropriate response which can be either a requested resource, or some other response stating an error or asking for additional user input.
Every request or response contains two major parts—request/response headers and request/response body. The web server can put different information in its response headers. A common example would be something like this:
HTTP/1.1 200 OK Date: Wed, 02 Jun 2010 02:56:36 GMT Server: Apache/2.2.12 (Unix) mod_ssl/2.2.12 OpenSSL/0.9.7d mod_wsgi/3.2 Python/2.6.5rc2 Last-Modified: Tue, 01 Jun 2010 07:43:19 GMT Etag: "22a50e6-4bb8-487f3208173c0" Accept-Ranges: bytes Cache-Control: max-age=86400 Expires: Thu, 03 Jun 2010 02:56:36 GMT Vary: Accept-Encoding Content-Encoding: gzip Content-Length: 5423 Keep-Alive: timeout=5, max=100 Connection: Keep-Alive Content-Type: text/html
The line that is most troublesome is Server. This is because the header web-server can choose to expose additional information about the software it uses. By reading this line we know we are dealing with Apache version 2.2.12 with SSL installed using OpenSSL 0.9.7d, mod_wsgi 3.2 and python 2.6.5rc2. All of that is running under UNIX. This is a lot of information to be available for an attacker. Too much! So let us see how we can disable this detailed expose of the server's software.
ServerTokens directive configures the appearance of HTTP Server response header, and as of version 2.0.44 of Apache, it also controls footer content on the error pages.
This directive can have the following values:
- Prod: Display only the product name (Apache)
- Major: Display product name and major version (Apache/2)
- Minor: Display product name and minor version (Apache/2.2)
- Min: Display product name and minimal version (Apache/2.2.12)
- OS: Display product, minimal version, and operating system (Apache/2.2.12 (Unix) )
- Full (or not specified): Display product name, minimal version, operating system, and any particular modules executed by web-server (Apache/1.3.41 (Unix) PHP/5.2.12RC4-dev)
All main configurations of Apache web server are located in /etc/httpd/conf/httpd.conf. Open a httpd.conf in your favorite text editor and add this line:
ServerTokens Prod
The result of this change is that only the web-server name is displayed. This does not help the attacker much in his preparation for attack since he does not know which version of the software is running, and on what OS it is running on.
There is another thing you should configure in order to minimize exposed information. When we enter an incorrect URL location, the web server usually responds with a message like Page not found. However, it can also generate a page footer that exposes similar information as the Server header.
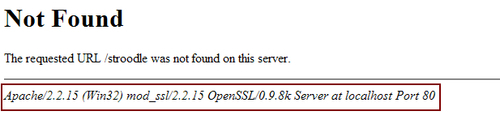
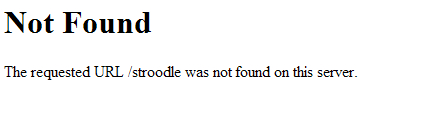
It is also advisable to disable the exposure of this information. You can do this by adding this to httpd.conf:
ServerSignature Off
And this is the result:
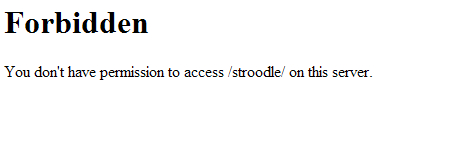
By default, Apache comes preconfigured to allow directory browsing. This is also considered a security breach as it permits insight into our web application structure and file content. To disable this, we must locate the DocumentRoot configuration in httpd.conf and find a line that looks like this:
Options Indexes FollowSymLinks
And change it to:
Options -Indexes FollowSymLinks
We should repeat this in any directory configuration that is located outside the server DocumentRoot. That way if we try to browse some folder we will get a message like this:
Functionality in Apache is added through modules. To reduce the number of potential security holes in your web server, always load minimum number of modules, just the ones that permit your service to operate correctly. Here is an example list of modules:
LoadModule auth_basic_module modules/mod_auth_basic.so LoadModule auth_digest_module modules/mod_auth_digest.so LoadModule authn_file_module modules/mod_authn_file.so LoadModule authz_host_module modules/mod_authz_host.so LoadModule include_module modules/mod_include.so LoadModule log_config_module modules/mod_log_config.so LoadModule expires_module modules/mod_expires.so LoadModule deflate_module modules/mod_deflate.so LoadModule headers_module modules/mod_headers.so LoadModule setenvif_module modules/mod_setenvif.so LoadModule mime_module modules/mod_mime.so LoadModule negotiation_module modules/mod_negotiation.so LoadModule dir_module modules/mod_dir.so LoadModule alias_module modules/mod_alias.so LoadModule rewrite_module modules/mod_rewrite.so LoadModule php5_module /usr/lib/php/libphp5.so
ModSecurity is a web application firewall that can work either embedded, or as a reverse proxy. It provides protection from a range of attacks against web applications and allows for HTTP traffic monitoring, logging, and real-time analysis. It is quite a complex system, and as such goes beyond the scope of this book. For further information refer to the ModSecurity website: http://www.modsecurity.org/.
