Somebody or something open to attack or damage is considered vulnerable. A computer system is considered vulnerable if it is susceptible to the operations that try to disrupt, degrade, steal, or destroy information resident on it. As we explained in the first chapter, the weak points of every server intended for hosting Moodle are operating system, web server, PHP, database server, and Moodle itself. In this chapter we will explain how to properly install and configure all of these elements assuming that the operating system is Windows. By properly configuring all crucial elements of a Moodle server, we reduce the possibility of any security breaches and can offer a reliable and stable platform to our users or institutions. If you do not use Windows, then you can skip this chapter. The content is divided into the following topics:
- Securing Windows—the basics
- File security in Windows
- Recommended installation and configuration of PHP under Windows web server
- Recommended installation and configuration of MySQL
In this chapter and throughout this book whenever we speak about Windows we speak about Windows 2008 server. The reason we choose to focus on this particular version is that it is the latest version with which most of the new servers will be shipped and which also brings numerous performance and security enhancements particularly related to PHP. Because of this choice, web server and PHP configuration sections are not applicable to the previous versions of Windows OS. The rest can be applied to Windows 2003 provided that you have installed at least Service Pack 2.
Windows 2008 ships with an integrated firewall. The firewall is enabled by default and it blocks any incoming connection unless it is the direct response to a previous outgoing request from the computer or unless it is permitted by specific rule created to allow that traffic.
To access the Firewall management console, open Control Panel and start the Windows Firewall Applet. You will see a dialog similar to the following one:
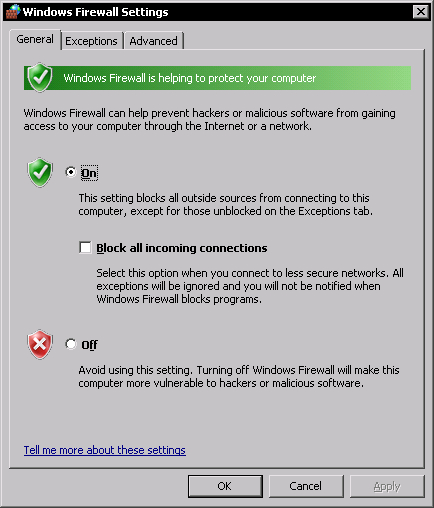
If for whatever reason it is not enabled, enable it making sure that the Block all incoming connections option is not checked.
To permit external users to access the web server we need to open HTTP and HTTPS ports. To do that you should click on the Exceptions tab and check the following options:
- Core Networking
- Remote desktop
- Secure World Wide Web services (HTTPS)
- World Wide Web services (HTTP)
(Not all options are visible on the screenshot we have provided, but just scroll the list up and you will find them).

In case you need to fine-tune the firewall settings go to Control Panel, choose Administrative Tools, and start Windows Firewall with Advanced Security. Another way of doing this is to open Run dialog and enter this in a command line:
%SystemRoot%system32WF.msc
Updating Windows is extremely important. It is the most widespread operating system. Due to the large number of people willing to probe for security holes it is one of the most attacked targets on the Internet. Microsoft issues a large number of patches every month for all supported versions of their OS. They are delivered to the customers through the Windows Update service. By default this service is enabled and you should keep it that way. It is essential that you regularly update Windows because that way you are sure that any security or functional issues are resolved.
We need to configure Windows Update to behave according to our needs. Have in mind that you are preparing a machine that will be used as a service provider. Providing a service means you have certain guaranty about its availability. Due to the way Windows is implemented it is often required to restart the OS in order to fully apply a newly installed update. In the default configuration of Windows Update all updates are applied without user intervention, which means that if an update requires the OS to be restarted it will be done automatically. During the process of restarting the OS our service will not be available and if for whatever reason the update did not go well we may even end up with a malfunctioning server. As a responsible administrator you must anticipate appropriate time for applying updates to the system and notify all users about downtime. To have that kind of control we should configure Windows Update not to download and install updates as they appear in the repository.
To set up Windows Update according to our recommendations open Control Panel and choose Windows Update applet. In the new window, click on the Change settings option and configure the Important updates option by choosing Check for updates but let me choose whether to download and install them. Also uncheck the Recommended updates and Who can install updates options.
More than 90 percent of created viruses are for Windows. That makes it extremely vulnerable to this kind of attack. On a desktop machine anti-virus is a must, but on the server things are a bit different.
A server is a dedicated type of machine which, usually, only serves content to outside users. It is extremely rare that outside users can change anything in the server's backend, and even if that is the case it is usually under controlled conditions. The only person who actually works with server content is you—the administrator. Therefore there is no real need to install any anti-virus product. Installing it can even make things worse, especially with a database, since all runtime checking engines verify files on every access/read/write operation.
Imagine now if that file is a big database being scanned every time a new modification is stored. It may have a notable performance impact on the server. We strongly advise against anti-virus on a web server with MySQL database. However, if you still want to install it or must due to your company security policy, make sure you do not configure it to be too aggressive in its checking or set it up to scan only directories which receive content from outside users.
With Windows Vista/2008, Microsoft introduced a new security model called Mandatory Integrity Control (MIC) which is a version of Mandatory Access Control (MAC). This mechanism is able to selectively restrict the access permissions of certain programs or software components in contexts that are considered to be potentially less trustworthy, compared with other contexts running under the same user account that are more trusted.
There are four Integrity Levels (IL)—Low, Medium, High, and System. By default all standard users are assigned Medium IL. This means that no action that affects system components marked with High IL can be executed by such user. That also applies to Administrator. In order to execute a task that affects any core system element, the user needs to elevate his IL to High. When the system detects the need for elevated privileges it will ask the user for confirmation and credentials to confirm and validate IL elevation. This is handled by User Account Control (UAC).
This security model is applied on all running applications within OS but in this case it is relevant only to the administrator since it is essential to know how to obtain administrator privileges in this OS and thus manipulate the configuration process properly.
Note
To elevate command prompt you need to right-click on the command prompt icon in the Start menu and choose the option Run as administrator.