Chapter 4 – The User Environment
“The afternoon knows what the morning never suspected.”
DBC is the only user when the system first arrives
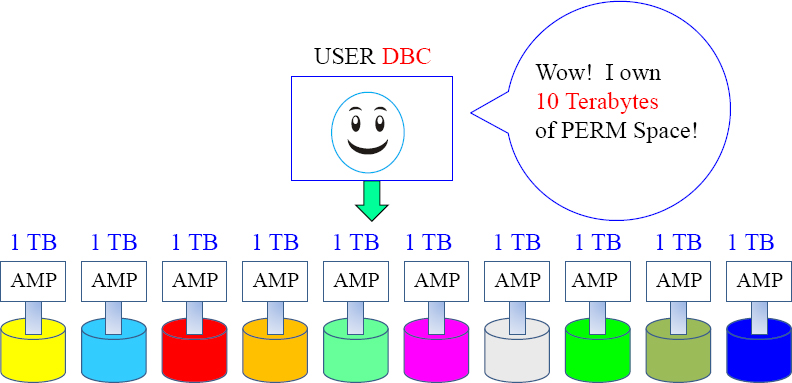
When the system is new and arrives at your company, DBC is the only USER. DBC counts up all the disk space attached to each AMP and considers that PERM space owned by DBC.
User DBC owns all the disk space on day one of your system's arrival. DBC will then begin to allocate space to other databases or users. Think of PERM space like money. If DBC has 10 Terabytes of space, it is like having 10 dollars. If you give away 5 dollars, you only have 5 dollars left. Spool space is more like a speed limit.
DBC will Create Databases and Give them Space
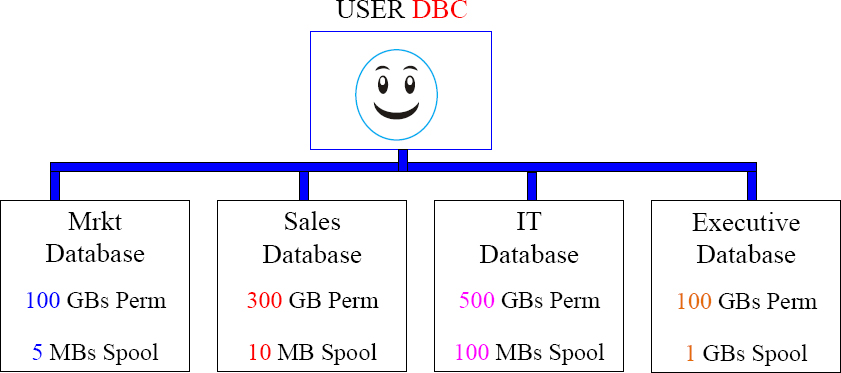
DBC will begin the hierarchy. Anyone above you is your parent, and anyone below you is your child. DBC is always a parent of every database and user in the system. If DBC started with 10 Terabytes, then DBC only has 9 Terabytes left because DBC gave Mrkt, Sales, IT, and the Executive database some of the space.
DBC will create some initial Users
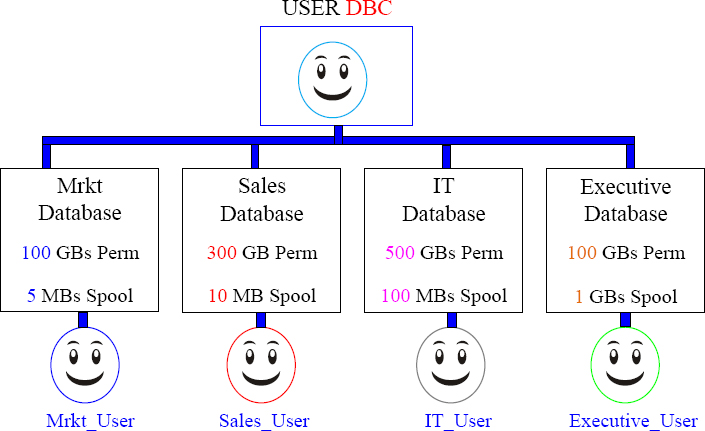
Now that the user DBC has created the databases and some initial users, it can rest. Each user can now create other users and other databases within their own hierarchy. Each database has the space and each user has the control to build their own environment of users, databases, and tables. The hierarchy is just beginning.
A Typical Teradata Environment
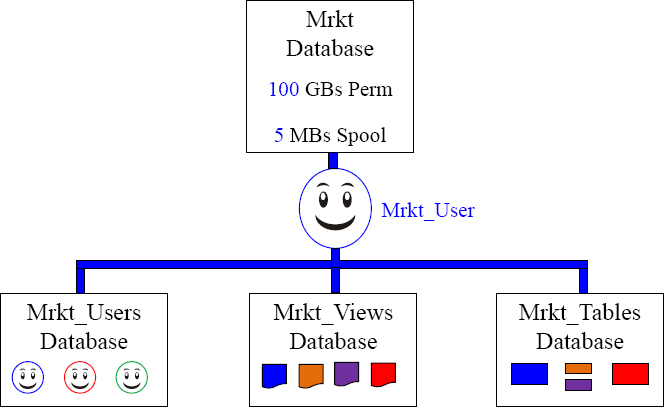
Users in the Mrkt_Users database are given Select and Execute Grants to the Mrkt_Views. The Mrkt_Views database holds the views that access the Mrkt_Tables database. This provides security and allows the users to access the information.
What are Similarities between a DATABASE and a USER?

| A Database or a User can be assigned PERM Space |
| If the Database Marketing is assigned 10 GB of PERM, that means it can hold up to 10 GB of Permanent Tables. | |
| If the User Maria is assigned 10 GB of PERM, that means she can hold up to 10 GB of Permanent Tables. | |
| A Database or a User can be assigned Spool Space |
| If the Database Marketing is assigned 10 GB of Spool, that means all users under marketing can each run 10 GB queries. | |
| If the User Maria is assigned 10 GB of Spool, that means she can run up to 10 GB queries, and any user created under Maria will default to 10 GB queries. |
In Teradata, the only difference between a database and a user is that a user can login and run queries.
Roles
Roles simplify database administration by assigning access rights to tables and other objects, and then groups of people with similar job functions (or roles) can access these objects.
It is as simple as creating different roles for different job functions and responsibilities, and then granting specific privileges (access rights) on database objects to these roles. Then, granting a role or roles to users who share the same privileges.
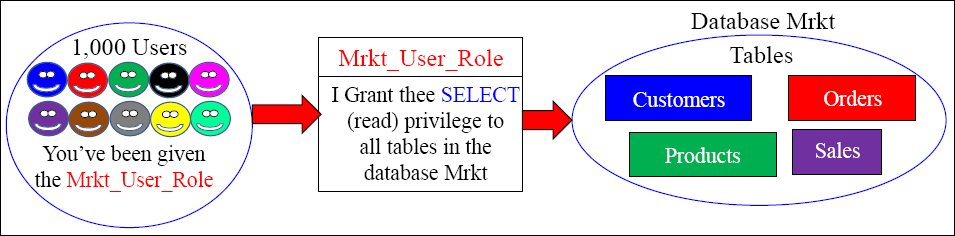
Imagine a thousand users accessing certain databases, tables, views, macros or stored procedures and having to grant each individual user access rights to these objects. Why not instead create a role that provides access to these objects, and then assign everyone needing this access that role. Roles simplify this very important security assignment. This is the way that Teradata prefers to implement Access Rights.
Create a Role and then Assign that Role Its Access Rights
Example
CREATE ROLE Mrkt_User_Role ;
When a role is first created, it does not have any associated rights until grants are made to it.
GRANT SELECT ON Mrkt TO Mrkt_User_Role ;
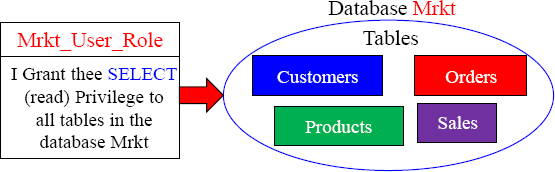
We first create a role and it has no associated rights with it. Then, we grant the rights on the database or objects we want to that role. You can use the Grant or Revoke commands to add or take away rights for a role. Above, we created a role name Mrkt_Users_Role, and then we granted SELECT access to all objects in that database.
Create a User and Assign them a Default Role
CREATE USER Mrkt_User01
FROM Mrkt_User
AS
PASSWORD=abc111
PERM=0
Profile=Mrkt_User_Profile
DEFAULT ROLE = Mrkt_User_Role ;
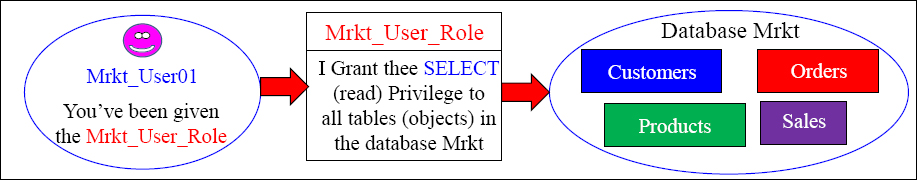
Let's recap. We gave Mrkt_User the right to create and drop roles. Then, Mrkt_User created a role called Mrkt_User_Role. Then, we assigned the SELECT right to the Mrkt database to the Mrkt_User_Role. In our example above, we created a user named Mrkt_User01, and assigned them a default role of Mrkt_User_Role. Now, our user (Mrkt_User01) can run SELECT statements (queries) on all tables (objects) in the Mrkt database.
Granting Access Rights
TeraTom can now use Select queries on the Employee_Table.
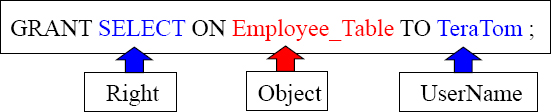
TeraTom can now use Select queries on the Employee_Table and he can grant this right to others.
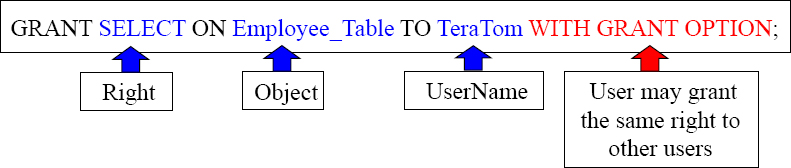
These examples are designed to teach you the mere basics of rights on objects.
There are Three Types of Access Rights
Access Rights consist of Automatic Rights, Implicit Rights, and Explicit Rights. Here is an explanation of each:
- Automatic Rights are often referred to as Default Rights because these are privileges that are automatically given to creators and, in the case of users and databases, each of their created objects.
- Implicit Rights are sometimes called Ownership Rights. Anybody above you in the Teradata hierarchy is considered your parent or owner, and a parent has an implied right over their children. So, these Owners (Parents) have the implicit right to grant rights on their owned objects (Children), either to themselves or to any other user or database. Ownership rights cannot be taken away unless ownership is transferred.
- Explicit rights are privileges a user explicitly grants to another user with an actual GRANT statement. This statement inserts new rows into the DBC.AccessRights table. Explicit rights can be removed by explicitly using the REVOKE statement.
When a user submits a CREATE statement, new rows are inserted in the table DBC.AccessRights and they are removed for an object if it is dropped.
Description of the Three Types of Access Rights
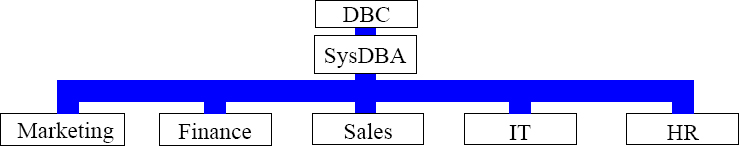
Implicit rights belong to the owners of objects. Owners don't require rows in the DBC.AccessRights table to grant privileges on owned objects. Ownership rights can't be revoked. A parent or owner has the implied right to GRANT privileges over their children. DBC and SysDBA hold implicit roles on all the other databases above.
Automatic rights happen whenever a CREATE statement is submitted, and new rows are automatically added to the DBC.AccessRights table. When the databases above were created, they automatically received all but four access rights on themselves. Automatic rights are removed with REVOKE or DROP statements.
Explicit rights are completely controlled by when a user explicitly and literally submits a GRANT or REVOKE statement. The GRANT statement adds new rows to the DBC.AccessRights table, and the rights are granted. The REVOKE removes them.
Profiles
It is easy to get mixed up between a Profile and a Role. Think of it as “Profiles are for People” and “Roles are for Rights”.
Profiles define system attributes for users (people). By assigning a profile to a group of users, you can rest assured that all group members will operate under a common set of attributes.
Create a different profile for each user group based on system attributes that members share.
If you do set the value of a parameter in the profile, the settings override the settings for the user in a CREATE USER or MODIFY USER statement.
If you do not set the value of a parameter, the system uses the setting defined for the user in a CREATE USER or MODIFY USER statement.
Profile parameters include:
- Account IDs
- Default database
- Spool and Temp space (but not Perm)
- Password attributes
Imagine a thousand users assigned the same amount of spool and temp space, the same default database, and the same account ID. With them all under the same profile, you can make one profile change and all thousand users receive the change. Imagine the nightmare of having to make a change to all thousand users if a profile was not used.
Creating a Profile and a User
CREATE PROFILE Mrkt_Profile AS
ACCOUNT = ('$L_Mrkt&L', '$M_Mrkt&L', '$H_Mrkt&L'),
DEFAULT DATABASE = Mrkt_Views,
SPOOL = 1E9,
TEMPORARY = 500E6,
PASSWORD = (EXPIRE = 120, MINCHAR = 7, MAXLOGONATTEMPTS = 4,
LOCKEDUSEREXPIRE = 60, REUSE = 180,
DIGITS = 'R', RESTRICTWORDS = 'Y', SPECCHAR = 'P'),
CREATE USER Mrkt01 AS
PERM = 0,
PASSWORD = Salesabc,
PROFILE = Mrkt_Profile;
We have just created a profile. We have given them three account options, but the first account listed is the default. Each user assigned this profile will have a default database as Mrkt_Views, and each gets 1,000,000,000 Bytes of spool space and 500,000,000 Bytes of temp space. We have also set quite a few password restrictions.
We have also created a user and assigned them to our newly created profile.
ProfileInfoVX, RoleMembers, RoleInfo and UserRoleRights
SELECT Profile;
Check to see if you have a profile
SELECT * FROM
DBC.RoleMembersVX;
Check to see all the role names, the grantor and the date it was granted
SELECT COUNT(*)
FROM DBC.RoleInfoVX;
Check to see all the roles that you personally have created
SELECT * FROM
DBC.ProfileInfoVX;
Show all information about your profiles
SELECT RoleName, DatabaseName,
TableName, ColumnName, AccessRight
FROM DBC.UserRoleRightsV
ORDER BY 1;
Check to see all the columns above for any roles in the system
The ProfileInfoVX, RoleMembers, UserRoleRights and RoleInfoVX views show you what you need to know about Roles and Profiles. Remember that Roles are for “Rights” and Profiles are for “People”.
Accounts and their Associated Priorities
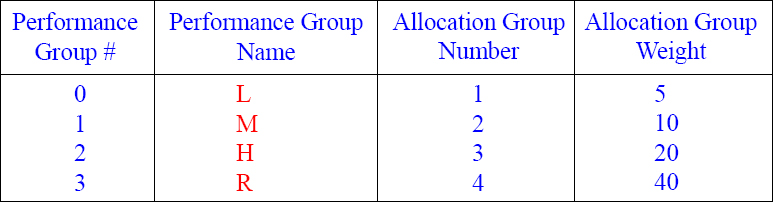
When a User is created, their account has an associated performance priority.
CREATE USER TeraTom AS PERM=0, SPOOL=300e6, PASSWORD=teacher, ACCOUNT=('$L_Training'),
CREATE USER BillyBob AS PERM=0, SPOOL=300e6, PASSWORD=braintrust, ACCOUNT=('$M_Mrkt'),
CREATE USER HiteshP AS PERM=0, SPOOL=300e6, PASSWORD=Callcenter,
ACCOUNT=('$H_CallCenter'),
Each user is given an Account ID and that will determine their system priority and this will be one of the ways the DBAs track the user. In our example above, BillyBob queries run twice as fast as Tera-Tom's queries. HiteshP queries will run twice as fast as BillyBob's queries and four times as fast as TeraTom's queries.
Creating a User with Multiple Account Priorities
CREATE USER SQL00
FROM SysDBA
AS
PASSWORD=abc123
PERM=20000000
SPOOL=5000000
TEMPORARY = 3000000
ACCOUNT=('$Med', '$Low', '$High')
DEFAULT DATABASE = SQL00
NO FALLBACK;

Notice that when this user was created, they also created three different Account IDs. The default Account ID will always be the first one listed, but now the user could login or set their session to utilize one of the other Account IDs. This is done so a user can run queries at different priorities.
Account String Expansion (ASE)
&L This causes the logon time stamp to be inserted into the account string.
&D This causes the date to be inserted into the account string.
&T This inserts the time of day into the account string. This variable allows for one-second granularity, thus causing a row to be written for each individual SQL request.
&H This inserts the hour of the day into the account string.
&I This inserts the logon host ID/session number/request number into the account string.
&S This inserts the current session number into the account string.
CREATE USER TeraTom
FROM DBC
AS
PASSWORD=abc123
PERM=0
SPOOL=5000000
TEMPORARY = 3000000
ACCOUNT=('$MAL&L', '$MBD&D', '$MCT&T', '$MDH&H', '$MEI&I', '$MFS&S', '$MGALL&L&D&T&H') ;
DEFAULT DATABASE = SQL_Class;
The system truncates all characters to the right of the 30th position for Account.
Account String Expansion will place additional information inside your account. After creating TeraTom, we will run queries from all accounts and check out the DBC.AmpUsage report to see exactly how the account string expansion works.
The DBC.AMPUsage View
SELECT UserName (CHAR(12))
,AccountName (CHAR(40))
,SUM (CPUTime) (FORMAT 'z,zzz,zzz.99') as CPU_Used
,SUM (DiskIO) (FORMAT 'zzz,zzz.999') as DiskIO_Used
FROM DBC.AMPUsageV WHERE UserName = 'TeraTom'
GROUP BY 1, 2 ORDER BY 2;
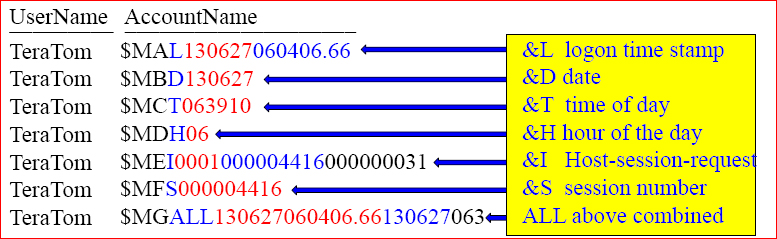
The DBC.AMPUsage report is how users will be tracked in terms of how much CPU and Disk I/O usage they are using on the Teradata system. This example shows how Teradata reports the AccountName when the Account String Expansion (ASE) is used. I have highlighted in colors the values. This report didn't show the CPU_Used and DiskIO_Used values that returned, but the DBAs will run this report to see who is using what resources.
Teradata TASM provides a User Traffic System
“Two roads diverged in a wood and I took the one less traveled by, and that has made all the difference.”

Imagine our highways with only one lane or our roads with no stop signs or lights. Teradata has the most sophisticated traffic system in the industry. Teradata allows for rules, times, delays, green lights to query, and red lights to wait. Why put a long-haul trucker with an oversized load in the fast lane? Marathon runners don't run at the same speed at sprinters, so you need to give your fastest speeds to your tactical queries and slower speeds for your batch processing. Teradata Active System Management (TASM) controls the query traffic so users can take the route less traveled. Your account will be given a priority, and rules will be set up to control system resources.
Teradata Viewpoint
“A man who views the world at 50 the same as he did at 20 has wasted 30 years of his life.”
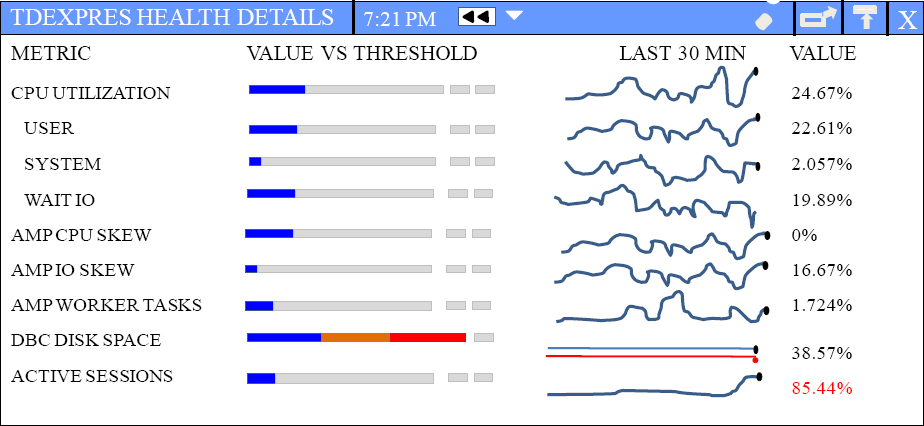
Teradata allows your queries to float like a butterfly and not sting at all! This is because Viewpoint gives the DBA and the users their own view of their Teradata world so everyone knows exactly what is going on with the system.
