Chapter Sixteen
IT Industry: An Overview and Ethical Perspective*
INTRODUCTION
The opening up of Indian economy in 1991 coincided with the information technology (IT) revolution that was sweeping all over the world. This lucky coincidence catapulted India into the league of IT super powers. Indian software houses utilized the opportunities available in global market to the hilt with a rousing start. Indian IT and IT-enabled services (ITES) industry charted a phenomenal double-digit growth of over 28 per cent since the financial year 1999–2000. Its contribution to the national GDP has risen from 1.9 per cent in financial year 1999–2000 to 5.4 per cent in 2006–2007, and is estimated to contribute 7–8 per cent of the country’s GDP by the year 2010. The industry’s revenue through software and services alone is US$ 39.6 billion in the financial year ending 2007, US$ 52 billion in the financial year 2007–2008 and is expected to grow between 20 and 23 per cent in 2008–2009. By 2010, the revenue through software and services alone is expected to reach US$ 73 to 75 billion.1
The Indian IT-ITES industry, besides this impressive economic growth, has also created employment opportunities to the many engineers graduating from various institutes around the country. Today, there are more software engineers in Bangalore than in the Silicon Valley. The direct employment in the Indian IT-ITES sector is estimated to have grown by over a million, from 284,000 in 1999–2000 to 1,621,000 in the year 2006–2007.2 In addition to this 1.6 million-strong workforce employed directly in the industry, Indian IT-ITES is estimated to have helped create an additional three million job opportunities through indirect employment like telecom, power, construction, facility management, transportation, and catering, to name only a few sectors. It has also induced increased expenditure of employees on food, clothing, utilities, recreation, health and other services. The Government of India has recognized the potential of the IT-ITES industry and understood its direct and indirect influence on the socio-economic realm, and has offered a lot of sops in terms of tax holidays, special economic zones, etc. The IT industry has enabled India leapfrog from an agrarian economy to an economy operating at the leading edge contemporary technology. This has in turn developed a lot of entrepreneurial activity that was not so common in India earlier. Many graduates from top universities like the IITs have shunned fat pay checks from global brands and started their own ventures. Quite a few of them have achieved a decent success competing with established companies both in India as well as abroad. It is quite an interesting story to observe how such a young and happening industry looks at ethics in its business transactions. To understand the business ethics of Indian IT-ITES industry, it is helpful for us to have an overview of its structure and its unique characteristics.
STRUCTURE OF IT-ITES INDUSTRY
The IT-ITES industry of India can be divided into two major categories: (a) IT services and (b) IT-enabled services (business processing outsourcing centres and high-end R&D centres).
It Services
IT services, popularly referred to as IT, form the dominant sector of the industry in terms of revenues as well as size. This particular sector of the industry can be understood in terms of the value chain of services it offers to its customers.
Value Chain in IT Services According to John Del Vecchio and Mike Trigg, a value chain is “a string of companies working together to satisfy market demands”.3 Value chain consists of one or a few primary value (product/service) suppliers and many others that add on to the value ultimately presented to the buyer. The value chain in the IT industry (Fig. 16.1) refers to a whole gamut of activities ranging from the introduction of a strategy, to the installation, usage and support of the solution, in a descending order.
IT Services Tier I: Consultancy and Product Development At the top of the chain are the consultancy and product development activities. A consultant works closely with the client company, identifying the various parameters of the business issue. The dynamics of the operations are captured, the market forces are identified and strategies are formulated backed up by action plans. The consultancy can cover the whole organization of the client or focus on one particular business unit/area/product. In many cases, it is like partnership or association. The other activity at the top end is the product development activity (e.g., Microsoft and Oracle). Microsoft, a single corporation, controls close to 5 per cent of the business in this value chain.
Examples of players at this level are IBM, Computer Sciences Corporation (CSC), Electronic Data Systems (EDS), and pure consultancy companies like BCG, McKinsey and KPMG. None of the Indian IT companies has a significant place in this top slot. Infosys has entered into this top tier and is trying to establish itself.
IT Services Tier II: Infrastructure Management and Systems Integration Infrastructure management and systems integration is a key activity to implement an IT strategy. Infrastructure is the foundation on which a strong IT function is built to meet the desired standards for security, reliability and availability, optimal performance and cost.
In an organization, IT is a complex mix of technologies, platforms and applications. Systems integration brings together the diverse systems, applications and platforms for smooth information flow, taking in its stride, the fast paced technological innovations.
Viant, Sapient and Exodus Communication are some of the players at this level, besides the omnipresent IBM, CSC and EDS. Infosys Technologies and Wipro Technologies are two Indian IT companies that have marked their presence at this level.
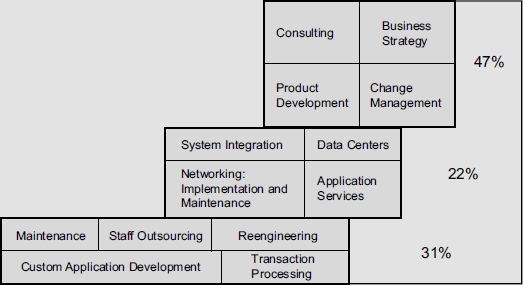
Fig. 16.1 IT Services Value Chain: Share of Each Layer in Global IT Services Market
IT Services Tier III: Application Development and Maintenance The last level in the value chain has activities like custom application development and maintenance. Custom solutions enable enterprises to derive competitive advantage, to fill gaps in the functionality provided by commercial packaged applications, to address business processes that are unique to them for which no solutions are available readily. Many companies that operate at level two also operate at the level three. All the Indian IT companies are major players at this level.
The revenue share of the top tier in the value chain is 47 per cent of the total IT market while systems integration garners 22 per cent, IT outsourcing has 18 per cent and the custom application development is left with 13 per cent.
It-Enabled Services
Outsourcing a certain function of business is in vogue for the past few decades. For instance, a firm can use an external accounting professional to prepare its financial statements on a specific contract. Business process outsourcing (BPO) is the practice of contracting a third party, by an organization, to carry out a specific activity or process of its business. Broadly, BPO operations can be of two types: outsourcing front office or back office processes. Front office operations include customer service, marketing, etc. Examples of back office operations are logistics, supply chain management, etc. Of late, national and continental boundaries are crossed to outsource processes to companies based in other countries.4 For instance, US-based companies would get their payroll activities and airlines would have their ticketing documentation done in India.5 Another very popular area sometime ago was medical transcription. Besides such low-end transactions and documentation activities, many financial institutions have set up captive units in India, like Citigroup Global Services (formerly eServe) of Citibank and Scope International of Standard Chartered, which take up the complete processing of various financial transactions of customers worldwide. These units are involved in key business processing areas rather than low-level transactions as earlier.
Business processes can be categorized into core and non-core areas, depending on the primary objective of the company. In case of a financial institution, preparing a financial statement by a financial expert is a core area while printing or translating such a statement is a non-core area. If we consider the case of a high-tech company manufacturing computer chips, the design, development and prototyping of a new chip is the core area while mass production and testing of that chip can be non-core. For a documentation company, (which probably is contracted by another firm to carryout document management), preparing contents of the documents is core activity while printing/dispatching can fall into the non-core area. Even though the definition of core and non-core areas is subjective, what really demarcates them is the cost involved and the value addition they bring to the company’s primary business goal.
Excitement increased when outsourcing moved from non-core areas to core areas as well. We have giants like GE and Intel getting some of their research done in India. NASSCOM sources predicted in 2002 that by 2008, IT services and back-office work in India will swell fivefold, to a US$ 57 billion, with the annual export industry employing four million people and accounting for 7 per cent of India’s gross domestic product.6
The common thread running through all these outsourcing activities is the information technology and hence ITES is a better description to cover all of them.
UNIQUE CHARACTERISTICS OF THE IT-ITES INDUSTRY
The fact that IT-ITES industry basically belongs to the tertiary sector of the economy puts forth the challenge of delivering an intangible product. But there are a few characteristics unique to this industry, when compared with the rest of the services sector. Three major factors that set this industry apart is the nature of the technology, the work force that is harnessing this technology and finally, its output, namely, information.
Technology and the Medium of Operation
Consider the basic activity of developing a software program. It would start with an individual writing a piece of code of self-consumption.7 At this stage, as it is purely for personal use, the usability and accuracy need not necessarily be high, and it is surely not generic. Whenever required, the author would quickly change or enhance the software. If this simple program has to be used by others also as a software tool, it has to be made generic. It ceases to be simple anymore but evolves into a ‘product’, by scaling over a wall of complexity of generalization, usability and higher quality as it has to deliver the expected results more accurately and frequently. In an orthogonal dimension, it this simple piece of software is treated as a building block or as a component in a larger software application, it has to scale over another wall to evolve into a ‘system’. In this case, the complexity is in terms of its interface or protocol, through which other components of the larger system can communicate with. When the simple ‘program’ scales both of these walls, it evolves into a complex ‘programming systems product’. Hence, it becomes increasingly difficult to be controlled in terms of accuracy, efforts, quality and hence, the cost. But the world is still charmed by the craft of software development. Software programming offers opportunity to unleash creativity at its best, while working with a tractable medium. The medium is so flexible that we can polish or completely rework at our whims and fancies. Frederick Brooks aptly describes the medium as being “only slightly removed from pure thought stuff”.8 Besides the creativity and tractability of the medium, the job offers tremendous learning opportunities—theoretical and practical put together, due to its non-repeating nature. On the other hand, the job demands perfect performance, the most difficult part in learning to program. Probably, as only few areas of human activities demand such perfection, it is nearly impossible to adjust to this requirement of perfection.
It is a heady combination of the joys of the craft mixed with the challenge of its woes, which attracts the best of intellectuals towards it. This brings us to the next unique characteristic of IT industry, namely, its workforce.
It Industry’s Workforce
Human resource is the most valuable asset in an IT company. An IT company is identified more by the intellectual capital than by tangible assets as in the case of other industries. Infosys has set a trend by publishing human resources as one of the four intangible assets in its balance sheet, besides the intellectual properties, internal and external assets. In fact, the industry views human resource management so important that major IT companies have placed their senior most executives in charge of this function. Infosys, for instance, has appointed one of its senior-most executive and ex-CFO, T. V Mohandas Pai as head of human resources. Earlier Pari Sadasivan had made a similar non-linear move taking over as VP-HR at IBM India after 20 years in operations, and as head of Global Delivery, China.9
When the Indian IT industry started to take shape, there was a huge demand for people with good analytical and arithmetic skill. During the late 1980s and early 1990s, engineers were hard pressed for jobs as growth in the secondary sector of the Indian economy was not impressive due to sluggishness in the manufacturing industry. The growing demand of engineers for the IT sector was supplied by the numerous engineering institutions. Irrespective of the branch of engineering, Indian IT companies recruited fresh engineering graduates. This predominance of young technologists has set a peculiar work culture in an industry, grappling with the new medium of work to create a new kind of output, namely, the information processing tools.
A recent NASSCOM survey on the Indian IT industry revealed some interesting facts. The median age of the software professionals was 28.9 years. In Infosys, the average age of employees is around 26 years. While 7 0 per cent of the work force were in the age group of 26–3 5 years, 81 per cent of all software professionals had a graduate degree or above. Seventeen per cent were MTechs, MBAs, CAs, or ICWAs; 69 per cent were BTechs, BEs or MCAs; 14 per cent were diploma holders or graduates.10 This phenomenon of high-volume recruiting has recently picked up after a couple of years lull during the early part of the decade. An estimate says that around 400 people were employed every day by the ITES-BPO sector alone, during the period 2004–2005.11
Besides their age and qualifications and the crucial role played in their companies, it is a well known fact that the income levels of these professionals are quite high when compared with many other industries.
In essence, what we have in IT-ITES industry is a predominantly young, intelligent, rich workforce, who, knowing very well that they are the heart of the industry which employs them, can easily set their own standards of ethical behaviour.
It Industry’s Output Process: Information and Tools
What is such a workforce, using a highly tractable medium, creating? They make software programs that control satellites, enable telecommunication, automate factories to produce and dispatch goods, manage financial transactions involving parties at multiple geographical locations in real time, help doctors treat patients, to name a few. In other words, they create tools and processes that generate information which is the life and blood of today’s economy. Information systems integrate people, processes and data using hardware and software, to generate on-demand information, and make it accessible to the right person at the right time to enable him/her make a right decision. It is redundant to state that organizations the world over have understood the importance of information and have started leveraging IT to grow. The IT industry is catering to this need of harnessing the power of information. Its products and services place an IT company in a critical position with respect to its customers.
ETHICAL PERSPECTIVE OF IT-ITES INDUSTRY
Is there any uniqueness of ethics in IT-ITES industry? Besides the aspects common to the other industries, IT-ITES industry has something very unique in the ethical realm due to its three factors elaborated above, namely, the medium of work (technology), the workers who use it and the output they create. The following discussion is not to show the IT industry in a bad light, as unethical. The very fact that companies and individuals the world over have reaped the benefits of IT, proves beyond doubt, the professionalism and fidelity of the IT industry. It is only to point out the areas in which the IT industry is uniquely susceptible to unethical practices.
One way to categorize the possible unethical practices is on the basis of:
- Information handling
- Dealing with intellectual property rights, and
- Working culture and environment in the organization.
Like any other organization, an IT company also has various stakeholders like its shareholders, customers/clients, employees, governmental bodies and society at large. The unethical practices categorized above can be carried out by
- IT/ITES organizations towards their clients/customers.
- IT/ITES organizations towards their employees.
- Employees of IT/ITES organizations towards their own organizations.
- Employees of IT/ITES organizations towards their clients/customers.
- IT/ITES organizations/employees together with their clients/customers harming the other stakeholders (share holders, legal authorities and the society at large)
BOX 16.1 CYBER MAFIA STALKS INDIA INC.
Cyber crime is now a bigger threat to India Inc than physical crime. In a recent survey by IBM, a greater number of companies (44 per cent) listed cyber crime as a bigger threat to their profitability than physical crime (31 per cent). The cost of cyber crime stems primarily from the loss of revenue; loss of market capitalization, damage to brand and loss of current customers, in that order.
Indian IT executives believe more strongly than their global peers that cyber crime is more costly to their organisations than physical crime. Sixty-seven per cent of the local chief information officers (CIOs) who took part in the survey perceived cyber crime as more costly, compared to a global benchmark of 50 per cent.
The global survey, conducted among over 3,000 CIOs or other individuals qualified to answer questions about their company’s IT practices, includes 150 respondents from India. The respondents were drawn from healthcare, financial, retail and manufacturing industries.
The report also says that the threat of cyber crime now comes from a number of new sources. Around 91 per cent of Indian IT executives, compared to 84 per cent of their global counterparts, believe that organised criminal groups possessing technical sophistication are replacing lone hackers. And, alarmingly, more than three-quarters (78 per cent), compared to 66 per cent of global businesses, perceive that threats to corporate security are now coming from inside the organization.
Indian firms ranked loss of revenue (75 versus 72 per cent of global businesses) as the highest cost associated with cyber crime, followed by loss of market capitalisation (72 versus 47 per cent of global businesses). The other costs by India Inc include damage to brand/reputation (65 per cent); loss of current customers (64 per cent); loss of employee productivity (60 per cent); loss of prospective customers (57 per cent); and cost of restoring service (53 per cent).
In the light of the growing cyber crime threat, 69 per cent of Indian businesses believe they are adequately safeguarded against organised cyber crime (compared to 59 per cent of global businesses). Upgrading their firewall (62 versus 28 per cent of global businesses) and implementing vulnerability/patch management systems on the network (31 versus 19 per cent of global businesses) were the two key initiatives undertaken by Indian firms to tackle the threat of cyber crime.
Source: The Economics Times, Chennai edition, 29 March 2006.
The following discussion lists out some typical cases that fall into one or many of these categories of possible unethical practices. Many such cases have been reported in the press in recent times (Box 16.1).
Information Security
Five major kinds of unethical practices fall under this category. At the lowest level, we find employees showing scant respect to information security processes. For instance, most IT companies, especially those working in the domains of banking, financial services and insurance (BFSI) have a rule not to share passwords with others, even with colleagues. Most of the employees do not take this seriously, even though they are reminded at frequent intervals about its importance. For fresh employees, the password is just a string of characters to unlock a computer—nothing more. But the fact is that once the computer system is unlocked, a wealth of information is available, which can be misused by unauthorized access.
Similar violation of information security can be seen in case of call centre operators, who force customers to part with confidential information like credit card numbers, when it is not really required. Most of the banks which issue credit cards advise their customers not to reveal such information over phone. But this is not honoured in many cases.
On a higher level, we hear cases of sharing confidential information about clients and customers with unauthorized people. Numerous cases of BPOs of leading banking institutions in Pune, Delhi, Hyderabad and Bangalore, where embezzlement of large amounts of funds happened, fall into this category. Typically, an employee who has access to important customer information like credit card or account numbers can sell them to unauthorized persons, who by fraudulent means steal the money from the customers. However, there have also been instances of data being lost due to extraneous factors (Box 16.2).
It is not only confidential information like credit card numbers: even information like tax data, education data, medical data, census data, insurance data, lifestyle data, credit data, email ids, etc. are freely shared with other parties like telemarketing companies (Box 16.3). In March 2006, NDTV has broadcasted a program of candid camera, on which a private detective, successfully got hold of the private information of mobile phone usage of a famous TV anchor for a paltry sum of money paid as bribe.15
On a similar front is hacking. Hackers disrupt the flow of information on the Internet by destabilizing the servers on which Web sites are hosted. They either publish false information or direct the visitors to other sites. They also can plant viruses that can infect the computers of the visitors. Employees working in Web hosting service companies can part with important customer information to unauthorized parties, which can lead to such issues.
There are some incidents of crucial electronic data lost, not necessarily due to intentional fraud but as a result of other factors. CitiFinancial, a unit of Citigroup Inc. announced on 6 June 2005, that a box of computer tapes with account information for 3.9 million customers had been lost in shipment. The company does not know whether the box was stolen and is treating it as lost. The data contained names, addresses, Social Security numbers and loan-ac-count data. Thankfully, there is no evidence of the data being misused, at the time of announcement. Such information is an increasingly valuable commodity in a world of electronic commerce, with Social Security numbers serving as a key for access to financial accounts, leading to potential risk of financial assets.
Till June 2005, it was estimated that about 6 million US consumers would have lost their personal data within a span of six months. The breaches would have occurred due to lapses by federal agencies, universities, banks, other financial institutions, data brokers and data-storage companies. Earlier, in May 2005, a data storage company lost information on 600,000 current and former employees of Time Warner Inc. In February 2005, Bank of America Corp. reported that it had lost tapes containing data on 1.2 million federal employees, including some US senators.
BOX 16.3 SNIFF CYBER FRAUDS
Phishing today is the biggest threat for internet banking. The term was coined by crackers attempting to ‘fish’ for accounts from unsuspecting AOL members. Phishers set up fake Web sites and e-mail addresses and spam e-mail inboxes with official-looking messages that read something like this: ‘Your account with our bank has encountered a problem and requires you to login and confirm some details’.
Once you click on the link provided in the e-mail, it directs you to a location that is close to the original site, generating an official facade. Once you have finished submitting your personal details, it will be sent to a person in a remote location who will do as he/she pleases with the provided information, which could include withdrawing money from your bank account or purchasing things in your name. The Anti-Phishing Working Group received over 20,000 unique phishing reports in May 2006 from the world over. This number does not account for the thousands of unreported incidents.
Security experts insist that online money transactions are on the rise (with almost 20–30 per cent users preferring online transactions). You need to be more suspicious of an unsolicited email than of a stranger knocking at the front door, caution experts. Srikiran Raghavan, regional head, RSA Security asserts: “Banking sites should adopt a two-factor authentication as a comprehensive defence”. Two-factor authentication means the user is asked to identify himself at more than one level. “Most common implementations of a two-factor authentication are provided by a compact electronic device that displays a number. Entering the displayed number into the system that you attempt to login proves that you are in possession of the card”, details Raghavan. The number displayed by the card changes every 30 or 60 seconds. The system that you are authenticating to, knows the number which should be on the individual’s screen. If the numbers match and password is correct, the one is authenticated. To increase security, the electronic device can be protected with a PIN number.
Most credit card applications are made online and about 50 per cent of mortgages, home equity loans and car loans are being signed online. Banks, both private and public sector, along with several financial institutions have reportedly invested lakhs on building safer security systems, in the hope that customers gain confidence in their systems.
While two-factor authentication has been applied successfully by banks in Hong Kong, the UK and other developed countries, Indian banks have just begun toying with the idea. Security companies are busy facilitating security standards for those who are already hooked on net banking and are paying bills or managing mutual funds and retirement funds online.
Useful Tips to Protect Yourself
- Do not submit personal financial details
- Banks never ask for personal details in e-mail communication
- Do not reveal your banking passwords, user IDs to anyone
- Never rely solely on “https://” prefix or a padlock icon
- Address bar can mislead. Phishers can spoof information
- Moving mouse over a link does not show the real URL in the status bar. It can be easily changed.
Source: Business Standard, Chennai edition, 11 July 2006.
On a much higher scale, we have cases of IT employees/organizations helping their clients to practise unethical transactions. While implementing IT systems, the software engineers can incorporate or avoid features that unethically hide or window-dress information that can be harmful to the customers/employees/other stakeholders of the clients.
One case of particular interest in this context is about a project in which an IT company was commissioned to develop and deploy a data retrieval and archival system. The client company had already a system in place but it wanted an enhanced one. As in the case of most of the projects, this also was running late. The client suddenly called for abandoning the project citing delay as the reason. But on deeper probe, it came out that the client was uncomfortable with one of the strong data retrieval features built into the new system. The new system can archive data, especially e-mails six years old while the older version had a limitation and could only retrieve data that were more than about one month old. The client company was nervous to store so much data. It knew that subpoenaed e-mail would play a part in any litigation against the company. With the old system, it could present a plausible excuse for why the data simply could not be presented. The new system exposed them to a possible threat. The IT company, in this case, to salvage the project, removed from the software, the ability of storing 6-year-old data. It can be argued that this is not an unethical practice as the IT company is supposed to deliver what the client requires. But seen in the larger context, it can be treated as unethical practice.
Cookies are another example through which important confidential information can be secured by unauthorized means. A cookie is a message stored in your computer by a Web server (Web site) when we visit it the first time. The message is then sent back to the server every subsequent time we visit the site. The main purpose of cookies is to identify users and possibly prepare customized Web pages for them. When you enter a Web site using cookies, you may be asked to fill out a form providing such information as your name and interests. This information is packaged into a cookie and stored. The server can use this information to present you with custom Web pages. As in the case of any technology, this also can be put to unauthorized usage by storing private data and later using it.
Intellectual Property Rights
Software piracy is one of the major issues causing huge losses to the IT industry. Ironically, some of the IT-ITES companies themselves use pirated versions of licensed software. Especially, in countries like India, Pakistan and China, software installation is nothing but copying some files from a CD into a hard disk. No one would take time to read the end user license agreement (EULA). Not many of them take efforts to ensure if they are authorized to use that particular software or not, before installing.
This is rampant in case of operating systems, development environments like compilers, office automation products and e-mail programs. Small IT companies may not use pirated software for their business blatantly. But it is quite common in such companies to buy only one license and install on ten computers, which is illegal. Some single-license agreements allow installation of a particular software on two computers, provided only one of them is at use at a given point in time. This is for the benefit of users working from different locations, with one computer typically being a desktop and the other a laptop. But it is quite common to violate this EULA, by installing the software on both the computers and have different users avail them simultaneously, but paying for only one license.
Another common area of unethical practice is illegal use of intellectual properties like algorithms, source codes, trade secrets and business logic. One of the most important components of a software program is the core logic that models the business rule of that particular application domain. It is invaluable information in the hands of a competitor. It is very easy for such information to be passed on by an employee, formally or informally.
There was a case few years ago when an employee of a prominent CAD/CAM system development company sold huge portions of source code illegally.
No employee is supposed to take source code of the programs of the organization he or she works for. At a lower level, it is quite common for employees taking home such source code segments in the name of back up or example programs, with or without disingenuous intentions.
At the organizational level, some companies might have got access to source code of some other company for enhancement/customization. It is possible that the IT company which has bought the source code, can exceed the brief as stipulated in the code sharing agreement and reverse engineer the program to gain access to the business logic and intellectual property of the vendor company. This is technically easy and has happened in some cases.
Work Culture and Environment
Most of the recruitments into IT companies are done at the campus level. In many cases, unethical practices start right at the time of recruitment tests. In the name of question banks, question papers of recruitment tests are leaked within the campus (as tests are conducted in various batches) or to other campuses which are on the recruiting list of the company.
Such unethical behaviour continues in employment, in terms of wasting company’s time and resources by browsing the Internet for non-business purposes, sending frivolous mails/instant messaging, gaming during business hours, researching/toying with technology totally unrelated to the task assigned by the company. Even though this can be seen in other industries, such behaviour is more common in an IT company as the employee will be always with his or her computer. This can also lead to another offshoot of claiming overtime compensation, which is not really required to complete the task assigned.
Another issue that plagues the IT industry is employee attrition. Young people with focus on making money or growing in designations at a high pace, resort to job hopping. This results in default of the commitments made to the customer if the employee leaves in the midst of a project being executed. The organization needs to spend time, money and efforts to recruit, train and deploy another person in place of the one who has left. Even though it is explicitly stated that 1–3 months’ notice is to be given to quit the job, it is quite common for the employee to terminate his or her work abruptly. Such breach of employment agreements is very rampant in IT industry.
At a relatively lower level, the young employees in an IT company do not think twice to claim allowances like house rent allowance (HRA) and medical bills with fraudulent bills to get income tax exemption. Even though such issues can be seen in other industries, these are more common in IT industry due to the less rigid financial and accounting procedures.
IT companies compete among themselves for customers as well as for employees. Poaching employees from competitors is quite common in IT industry. Even though this is not illegal, it has set an unprofessional culture in the industry and employees do not have any remorse of leaving in the middle of their commitments, as it is encouraged by the poaching companies themselves.
Commitment to their customers on one side and employee attrition on the other force IT companies to resort to various means and mechanisms of retaining the employees. Some times, these can be unethical. There are some cases where the full salary offered at the time of recruitment is not given. Instead, a significant portion of the salary is withheld by the company and disbursed only if the employee stays with the organization for a stipulated period of time. This is clear violation of the employment agreement by the employer. In some other cases, the employee should deposit some amount of money with the company as security to get appointment. Some companies also resort to the unethical and even unconstitutional practice of forcing new recruits to sign a bond agreeing to work for the company for a minimum period of say, three years, which takes away the person’s right to choose a better career.
In the name of increasing the productivity, long and odd hours of work are quite common in IT-ITES industry. Employees might have failed to finish the task in stipulated time due to the complexity of the task. But in some cases, it is the aggressive bidding of completion time by the companies to their customers that results in unrealistic estimations and plans.
Another area of conflict is monitoring the employees without informing them. In the name of information security or reducing wastage of time, some companies can resort to scanning e-mails of employees or planting spying programs without giving prior information to the employee. This amounts to a breach of privacy of the employee. Shuva Mandal, of Fox Mandal, a law firm, has already dealt with a few privacy cases in BPOs. According to him “Employee-employer disputes related to privacy are on the rise. Both are becoming conscious of their rights, even while companies are not defining privacy well”.16
IT companies have certainly brought in a world-class infrastructure and working environment to India. But there are still some cases where the working conditions are not ergonomic. Video operator’s distress syndrome (headaches, depression, anxiety), cumulative trauma disorder (associated with mental stress, eye strain, skeletal injuries) and carpal tunnel syndrome due to repetitive stress on hand/wrist are common work related disorders among the IT-ITES professionals. Employees also do not bother about such issues in the beginning of their careers as they are quite young. Only when they become older do they start experiencing the ill effects. Indian IT companies have a long way to go in terms of employee training on such issues and Occupational Safety and Health Administration (OSHA) compliance.
KEY WORDS
Global Market • Software Engineers • Contemporary Technology • Value Chain • Product Development • Strategies • Complex Mix of Technologies • Packaged Applications • Ticketing Documentation • Uniqueness of the IT Industry’s Workforce • Secondary Sector • Unlock a Computer • Information Security • Embezzlement • Cookie • Intellectual Properties • Customisation • Frivolous Mails/Instant • Unconstitutional Practice • Distress Syndrome.
FURTHER READINGS
1. The Washington Post, 7 June 2005, available at www.washingtonpost.com/wp-dyn/content/article/2005/06/06/AR2005060601682.html
2. Citigroup press statement, available at www.citigroup.com/citigroup/press/2005/050606a.htm
3. “Net Firms Make Secret Bank Offers,” Deccan Chronicle, Chennai edition, 16 July 2006.
4. “Banks Employ Strong-arm Tactics to Collect Dues,” Deccan Chronicle, Chennai edition, 17 July 2006.
Case Study-1
MPHASIS CASE: IF INDIVIDUALS DO NOT COMPLY, SAFEGUARDS ACHIEVE LITTLE1,2,3
In April 2005, India woke up to its first reported BPO scam. As the authorized e-banking service providers to Citibank, MphasiS-MsourcE, handles confidential details of various account holders of Citibank. Five employees of MsourcE (the BPO arm of MphasiS BFL), unit supervisor Maurelene Fernandes, Bijoy Alexander, and former customer care executives Ivan Thomas, Siddhartha Mehta and Stephan Daniel are said to have identified glaring loopholes in the MphasiS system, devised a modus operandi to siphon off funds, roped in friends like John Varghese, from outside and executed the fraud over four months. They allegedly pulled off a financial fraud worth nearly half-a-million dollars (US$425,000 at last count on April 20). The victims were Citibank customers in the United States.
MODUS OPERANDI
The prime accused in the scam, Maurelene and Ivan, allegedly got the confidential information of password/personal identification numbers (PIN) of five account holders. About a dozen bank accounts were opened with the help of documents allegedly forged by John and co-accused Anand Karnavat, an ICICI home loans agent. They then started transferring funds from the customer accounts to these, by a series of electronic transactions. The actual customers had no clue about the transfers done in their names, as fictitious email accounts were created to divert the confirmation messages of any e-banking funds transfer.
HOW IT CAME TO LIGHT
Neither Citibank nor MphasiS detected anything after the first illegal transfer in November 2004. One of the account-holders seemingly complained to Citibank, which alerted Citigroup Investigative Services (CIS). CIS, the recipient banks and police’s cyber crime cell of Pune together laid a trap. On 1 April 2005, Ivan and a co-accused, Shailesh Bhulewar, came to check about a transfer in a Rupee Co-operative Bank branch in Pune and promptly fell into the trap.
The cyber crime, which could only have happened in a globalized world, was believed to be the first of its kind to have come to light in India, and lead initially to the arrest of 12 persons. Police investigation showed that the money siphoned off could be more than Rs 15 million.
HIGHLIGHTS OF THE CASE
No computer geeks or hackers were involved in this fraud. They were not breaking through firewalls or decoding encrypted software. Instead, they are said to have identified glaring loopholes in the system.
Second, none of the accused had any prior criminal backgrounds. So a background check also would not have helped in this case. Also noteworthy is that their ages range between 25 and 30 years.
Kiran Karnik, President, NASSCOM, sums up the essence when he says that no matter what systems are in place, data security depends upon the individual.
Case Study-2
CREDIT CARD DATA FRAUD
An employee of HSBC Electronic Data Processing India Pvt Ltd (HDPI), HSBC’s BPO arm at Bangalore was charged with stealing data of its 20 customers in the United Kingdom. The employee, Nadeem Kashmiri (24 years) who was absconding for some days, was finally arrested. The incident came to light, following complaints by customers on unauthorized withdrawal of money from their accounts. The loss estimated was close to UK£ 233,000. Within the Indian outsourcing industry this unfolding saga has been observed with a mixture of alarm and frustration; alarm because such security breaches are extremely damaging to the industry’s reputation, and frustration because of a widely held belief that these incidents grab far more attention when they happen in India than they might elsewhere. Such stories of cyber fraud committed by Indian workers feed basic fears about globalization in the West.1
MODUS OPERANDI
Nadeem who worked at a call centre in Bangalore, somehow managed to make a surreptitious note of various account details,2 allegedly sold personal data, security information and debit card information of some of the customers in the U.K to a person named Ershad of the United Kingdom, who in turn made fraudulent transactions through ATM and debit cards and telebanking services. Nadeem who has allegedly got Rs 4,000 for each account data he passed on to Ershad, got the money transferred into a friend’s bank account in Bangalore. He had got Rs 80,000 and the entire amount was still in his friend’s account, at the time of investigations.
HIGHLIGHTS OF THE CASE
Most of the BPO companies make use of the services of placement agencies for their recruitment purposes. English-speaking skill is the only criterion many of these placement agencies look for, in such cases. Nadeem Kashmiri, was recruited by a placement agency hired by HSBC and had obtained the job on the strength of forged mark sheets. When The Hindu made random enquiries with some employees of call centres, they claimed that many of their colleagues were college dropouts who had managed to get the job on the basis of forged certificates.3
FALLOUT OF THE CASE
This data fraud case, like the Mphasis case, had a predictable fall out. At a time when Indian BPOs were making a strong attempt to enhance their business with claims of cheaper and better customer service, stories like this were bad news for the industry. In the aftermath of the HSBC story, industry analysts predicted that the BPO industry could slow from 45 per cent growth witnessed in 2004–2005 to 28–30 per cent in 2005–2006, due to the growing concerns about security, coupled with high employee attrition rate. Besides, though Indian BPOs have maintained comparatively better security generally, the failure in the HSBC case has got a disproportionate amount of bad media attention. It has also brought to light the fact that this kind of story made news internationally because of an underlying reluctance in the West to accept globalization and the consequent movement of jobs to a developing country like India, which has a strong competitive advantage in the services sector. From the Indian side, it is necessary that there should be greater vigilance exercised in ensuring data security. With cases of deceipt such as the HSBC case on the rise, Nasscom needs to take efforts to build a National Skill Registry of IT Workers, thereby creating a database of employee records where prospective employees have to disclose criminal records and give true information about their past records.
Case Study-3
CYBER CRIMES—THE GLITCHES AMIDST THE GLOW*
INTRODUCTION
Information technology has changed our lives like nothing else in the past. The rapid growth of Information and Communications Technology has created a forum for the exchange and use of tremendous amounts of information, goods and services over the Internet. Information and Communications Technology are opening up new opportunities in the delivery and enhancement of services in a wide range of applications including business, finance, healthcare, education, and government sectors. Even individual users have access to information pertaining to almost any domain with the ever-increasing number of search engines and Web sites available on the Internet, which give highly specific information on any area of interest. On the positive side, this is a technology that shrinks the globe several folds and provides equal opportunities to anyone who is adequately skilled to access and use this ocean of information appropriately and legally. But on the flip side there is a danger—a danger of allowing people to access and use this information for unfair means. In the course of the next few pages, we will look at some of the more dangerous crimes that could victimize users in cyber space.
WHAT ARE CYBER CRIMES?
The benefits of Information Technology to governments, organizational groups and individual users can only be fully appreciated if security concerns are sorted out with solutions to deal with the illegal use of technology—an act which has significantly increased the list of disadvantages of using Information Technology. This act has been rightly termed ‘cyber crimes’. Cyber crime refers to the act of misusing technology for acquiring power or publicity, as a tool for revenge or just for the mere thrill of accessing information that is not intended for one’s personal use. According to Dr Rusell Smith, electronic crimes essentially fall into three categories, namely,
Crimes committed through the use of computing and communications technologies: These would include the transferring of electronic funds without due authorization, electronic manipulation of share markets, and the propagation of misleading advertising information or offensive content.
Crimes directed at computing and communications technologies: This category of crimes would include the hacking of computer systems, spreading of viruses, vandalism of computer resources, or theft of telecommunications and Internet services.
Crimes in which computing and communications technologies are incidental to the commission of crime: Encrypting data to avoid detection of unlawful activity, reading illegal communication, and cloning of mobile telephones for criminal activity fall under this category of cyber crimes.1
Thus, cyber crimes can take numerous forms; computer viruses, worms and trojans, information hacking, child pornography, intellectual property crimes, Internet relay chat (IRC) crimes, financial crimes, net extortion, online gambling, e-mail spoofing, cyber defamation, cyber stalking, illegal traffic and sales of illegal products, and Internet phishing to name a few.
The cyber crime world is thriving and is among the largest illegal revenue earning industries today. A study in the United States has reported that global cyber crime had churned out more money than drug trafficking and that there has been an annual 200 per cent increase in the volume of spam mails since 2002. The report also suggested that spyware Web sites have almost quadrupled in the year 2005.2
Just as the use of Internet can be realized by individuals, groups or companies and the society/government, the misuse of Internet technology could also affect either individuals or corporate undertakings/groups and governments/societies at large.
Thus, the categorization of cyber crimes against individuals, organizations and society/state is as follows:
- Crimes against individuals, which could include sending viruses through emails, child pornography, password hacking to get information illegally, misusing bank account information of individual and the like.
- Crimes against organizations, which could include intellectual property crimes, Internet phishing, cyber defamation, net extortion etc.
- Crimes against society and/or the State, which could include cyber terrorism, threat mails and so on.
Let us see each of these crimes in detail.
Computer Viruses
The unauthorized access, corruption, manipulation and destruction of digital information are probably the biggest threat to the world of computers. Digital data corruption is being carried out by certain destructive software called viruses.
The name ‘virus’ for software comes from the English analogy for a being which can infect the human body and the immunity system—and something that becomes communicable by spreading from person to person. In this definition, if we were to replace humans with systems, that explains, more or less, the working of a computer virus.
In other words, a virus can be defined as any software that is written with a malicious intent of damaging a system’s software or the user’s peace of mind or both. A computer virus is a program that can infect other computer programs by modifying them in some way or the other. The working of the virus depends on how it has been programmed and to the category to which it belongs. People may however use the term to indicate any sort of program that tries to conceal its true function and spreads onto multiple computer systems. Simply put, in a layman’s language, a virus is a curse in disguise. It is a set of instructions developed to harm/replicate and spread across computer systems, generally with the victim being oblivious to its existence.
Computer viruses usually spread by attaching themselves to programs like word processors or spreadsheets. When an infected file is activated or when the computer is started from an infected disk, the virus itself is also executed. An example could be a virus that is sent via e-mail and has been programmed to attach itself to all outgoing mails from the recipient’s mail box. This would mean that even without the owner’s knowledge he or she would be sending the virus-attached email to all his or her contacts.
Mr Niraj Kaushik, Country Sales Manager, Trend Micro India, observed that there were at least 30 virus outbreaks in different parts of the world everyday in 2006, as compared to the two to three major outbreaks that used to take place every month in 2005. According to Mr Vijay Mukhi, of Nasscom, cyber crime is now ruled by the professional mafia which does not want publicity. He also notes that viruses have become stealthier, are invisible and are customized for a specific target.3
Password Hacking and Information Theft
Technology, though it provides us with various means of securing information, also shows various ways of breaking the security. For security reasons, there are explicit needs and means to authenticate people before letting them use an application. Passwords are typical examples of how man has always wanted to keep his access into an information domain as secure as possible—be it an ATM or an email box. A password is a technique used to authenticate a person. It is a mechanism of telling the system that if the person with this name/number furnishes this value for a password (in an email application, for example, where there is a check on the username-password pair), then he or she is an authenticated user of the system.
In spite of these measures, hacking is a process of cracking one’s password or ‘credential’ information to probe into his/her domain. It is a highly unethical and illegal act which could be carried out at various levels. We use the term at varying levels here because friends could challenge each other against figuring out one’s password or a spouse could be deliberately given the password and asked to check e-mails. Though these are acts that should be strictly avoided, they cannot be termed as ‘unethical’ since the subject knows about such use of information. Hacking becomes an unethical issue when it is done to gain unauthorized access into someone else’s information domain, without his or her knowledge by breaking his or her password. That is why, users have always been warned against the selection of weak passwords, like names (for a username in an email application) or date of birth (for a PIN number in an ATM application), which are easy for the hackers to crack.
Child Pornography
Child pornography as the name implies, is an illegal form of pornography involving children, or minors. While the laws that govern this category of crime would differ from country to country, most countries prohibit any kind of visual depiction of sexual activities involving children. Paedophiles, as the criminals are called, usually use false identity to trap children/teenagers. They could then contact these children in chat rooms or forums meant for interaction with other children. While doing so, they could befriend the innocent users and extract details from them, which are then used to contact them and establish some sort of relationship with them. Once they have got the contact information, paedophiles could either send pornographic images or text to the victim including other child pornographic images in order to help these victims shed their inhibitions. After these kinds of communication for a period of time, paedophiles may in fact chart out a meeting with the victims and force them into being objects of pornography themselves.
In these kinds of crimes, parents are partly to be blamed as they are unaware of the activities of their children and also the technology that they use. Most parents, at least in the Indian context, are not aware of the Internet technology and the dangers that it could pose to their children. Though today, many schools have an orientation programme for the parents about these kinds of child abuse techniques that one has to watch out, we still have a long way to go before people are fully aware of the ways in which technology can be misused.
Intellectual Property Crimes
Intellectual property crime or IPC is a term used to indicate counterfeiting and piracy related crimes. IPC refers to products that are copied illegally without the permission of the trademark or copyright holder. Fake goods that are produced and are made to have the look-and-feel of the original to misguide the consumers into buying them are examples of this type of cyber crime. Some of these goods are also sold at attractive prices so that consumers, who are not aware of the original cost, would be easily misled into buying these articles. IPCs can include trademark, patent and copyright infringement.
Many view this category of crime as relatively harmless because the users of the fake product are not victimized in this situation; in fact they get a good deal for the money. When it is a T-shirt or a book that is counterfeited to commit these crimes, the effects are not very disastrous. But take for instance, the case of fake drugs that could be a potential killer. The fact is that, the impact of this crime could have more serious repercussions than any other form of crime. Counterfeit goods are produced with little or no consideration for the health and safety of the consumer or the producers. The hidden costs borne by the legitimate producers, and the trade as a whole poses a threat to legitimate economies. Pirated books and drinks, for example, are so easily available in our country. Forged notes in circulation, trademark violation, software piracy are all other examples that belong to this category of crime. When these crimes happen over cyber space, they are usually less ‘visible’ and hence become more dangerous.
Pirated software falls under this category of criminal offence. The copyright infringement of software could be done in many forms. These include, creating an illegal copy to sell it or rent it to someone, or to simply keep it as a backup. Renting and reselling of original software without appropriate permission also falls under this category of crimes. In the ‘cyber crime’ perspective, software piracy can include the act of using office equipment to share private files or reproduce copyright material, downloading pirated software that are online and the use of such software. These are serious crimes that not only waste the company’s resources, time and money, but could also make the business prone to hackers and other cyber criminals.
To combat this menace, Tata Consultancy Services (TCS), Hyderabad, is developing the world’s first anti-piracy system for Internet service providers (ISPs). The company has already developed the basic modules of this technology solution that will help ISPs detect downloading of illegal programs by individual users, and then alert the program developers to it. It is also designed to recognize legal and illegal versions of the programs being download by the individual users. Accordingly the ISPs can alert music or movie companies and subsequently initiate appropriate action as per the latest instruction. Currently, Internet piracy of films and music round the world is estimated to be around US$ 6–7 billion.4
Recently, the cyber crime cell of the Central Crime Branch registered a case against an American couple John David Mangan and his wife Susan Mangan, for committing offences under the intellectual property right. They were charged of allegedly stealing the intellectual property of a local firm with which they were associated. They have been accused of enticing some of the key employees of the complainant firm to collect confidential information, business practices and training methods and also conspired to obtain a photograph of the complainant’s electronic server room and physical set-up with a possible intent to further penetrate their information network.5
Internet Relay Chat Crimes
Internet relay chat (IRC) servers are chat services that have chat rooms in which people from anywhere in the world can come together and chat with each other. This technology emerged as a result of the limitations of the existing programs that provided synchronous communication. The idea was to provide group communication, which is, letting more than two people communicate over the internet at the same time.
It must be understood that this technology is used by a heterogeneous crowd. This means that people who use IRC services are in reality breaking the geographical and cultural barriers while doing so. Users access the system from all over the world to interact with people from cultures that they might not have the chance to learn about through any other direct means. But the users of IRC do not generally use their real names. They usually choose a nickname to interact. Thus, essentially there is nothing that one user knows about another—beyond the fact that they have access to the Internet. The ill effects of this technology can lead a victim to be probably befriended over a chat and tricked to deliver facts that could be used for illegal purposes—an act that is termed ‘identity theft’. One would not have forgotten the kidnap of a 16-year-old boy, Adnan Patrawala from Mumbai, in 2007. The teenager was found murdered a couple of hours later. Police investigations suggested that the plan to kidnap the young boy was plotted on a social networking Web site that millions of users access today— Orkut. This is perhaps the most recent and frightening example of how cyber networks are turning into terrorist webs in these days.6 IRC is not the only means for identity theft though. It could be done using any of the other techniques as well.
Identity theft occurs when a person appropriates another’s personal information without his/her knowledge to commit theft or fraud. Identity theft could be thought as one of the first steps that could lead to the scheming of other types of frauds. Typically, the victim is made to believe that he/she is passing on personal information to a legal firm, sometimes as a response to an e-mail asking him/her to update some relevant information. Other forms of crimes that could be committed over IRC include verbal attacks on other users, illegally loading the server and thereby attempting to slow down the working of the client computers.
Though IRC has the potential to affect users of the system in many and often opposing ways, computer enabled communication can provide a way of learning social skills in a friendly environment even for people who are generally introverts. A disadvantage of internet chats would be alienation from the physical world and minimal needs for ‘real-world’ relationships. The cross-cultural nature of IRC can break the barriers of caste, creed and culture; but may also provide a forum for expressing one’s hatred against a group of people. Thus, this technology in particular has to be used, keeping in mind certain ethical issues and sentiments which if ignored, could make for more menace than a means of communication.
Spoofing and Phishing
Spoofing generally refers to the dissemination of e-mail which is forged to appear as though it was sent by someone other than the actual source. Phishing is the act of sending an e-mail with a false claim to be a legitimate business. The objective is to persuade the recipient into divulging sensitive information by directing the author to visit a fake Web site (see Box 16.3).
Phishing and spoofing are similar, in the sense that they both refer to false documents that are sent through the electronic media. In fact there are several kinds of spoofing and one type, namely “webpage spoofing” is generally used synonymously with phishing. Thus, spoofing or phishing as a cyber crime could include sending of false e-mails that claim to be from an established legitimate enterprise, and/or the URL to a Web site that has been duplicated to contain the look and feel of the original firm, in an attempt to trick the user into revealing private information that could probably be used for another type of crime (the identity theft that we have already discussed earlier). The e-mail could either ask the user to reply with the details or in many cases could ask him to access the duplicate Web site (which is made to look like the original firm’s web site) to furnish confidential information that the firm already knows.
Financial Crimes
The implications of cyber crimes for business are far reaching. E-commerce is one domain which has got the potential to change the way the world looks at business. But on the other side of the coin, is the danger of insecurity of information in cyber space, which has the potential to cripple the rise of e-commerce as a technical giant in its capacity. It is very easy for a cyber criminal with sufficient technical knowledge to hack systems and gain information which is not meant for him or her. Even with the implementation of firewalls and any number security scans at every possible level, there are instances of information misuse, which was done more for destructive purposes before, but are increasingly being done for financial purposes today.
Companies offering financial services over the Internet—and specifically those providing financial transactions over Web pages need to take steps to identify and mitigate opportunities for financial crimes/frauds. Cyber frauds can rob banks online by manipulating information or illicitly gaining access to intellectual property. For instance, HSBC, a large British financial services firm has commenced legal action against one of its erstwhile employee Nadeem Kashmiri, who has been accused of illegally diverting the funds belonging to HSBC’s clients to private accounts. Nadeem had been working at HSBC’s global service centre in Bangalore. The fraud was uncovered by HSBC’s own security teams and it was reported that a small number of UK-based customers were affected by the fraud. The bank has since contacted all the affected customers and reimbursed their loss in full. The bank has since then put strict procedures in all its centres to protect customer records and has ensured that the data security measures in their overseas centres are exactly the same as in the United Kingdom.8
Other types of financial crimes include the unauthorized use of a credit/debit card or card number, to fraudulently obtain money or property, in debt elimination schemes and investment fraud schemes. It is worth a mention here that these crimes are usually a consequence of identity theft.
Other Crimes
Internet extortion involves information theft and subsequent threats for either money or products or other favours from the organization. It could be very serious when the hackers actually begin to control various databases of different enterprises, promising to release the control back to the company if funds or jobs in some cases are received as ransom.
Cyber stalking, as the term implies, is the use of Internet technology to contact, harass or threaten another user in an unsolicited manner. Though some may feel that there are no chances of causing physical damage, the consequences of these kinds of threats could be disastrous in certain circumstances. It is distressing for a person to be threatened that his or her name would be used in a crime if they do not oblige with the conditions put before them. There are many ways in which cyber stalking can be carried out, and the damages caused to the victim could be physical, emotional, and psychological.
Cyber defamation includes any act that can cause damage to another person’s name or reputation in society. It could be Web sites that furnish incorrect information about a person or group of people, untruthful mails sent about them, and blogs that discuss business firms and so on. Any information released over the internet which has the effect of injuring that person’s status, good name, or reputation in society can be included in this category of crimes. They represent greater harm than the conventional crimes, and are of a nature that is quite different from them.
There was an instance reported where a data thief actually offered a bank account for sale, in the United States. He has been alleged to have sold an account with a US$ 31,000 balance for US$ 400. The online trade in stolen financial data is thriving.9 And so are auction sites that sell illegal articles online. In India, for instance, there are sites that apparently sell cocaine using other names.10 There are hundreds of Web sites all over the Internet that offer these kinds of services, including online gambling. In spite of numerous instances of criminals being caught indulging in these kinds of illegal cyber sales and punished in the past, a whole lot of such Web sites still do exist.
Cyber Terrorism
To quote from an article by Kevin Coleman: “Cyber terrorism is the premeditated use of disruptive activities, or the threat thereof, against computers and/or networks, with the intention to cause harm or further social, ideological, religious, political or similar objectives, or to intimidate any person in furtherance of such objectives”.11
Cyber terrorism refers to the use of information technology to harm society and its well-being. This means that the term cyber crimes and cyber terrorism are not to be treated at the same level of severity or scope. Cyber terrorism, as the name implies, is a much more serious act, where there is a terrorist component involved. It takes a serious dimension since the information that is involved and hacked/stolen becomes more critical. For instance, if hacking a password to cause defamation to a rival is one form of crime, sending e-mails to government bodies with bomb scares and threats would certainly be a threat to the country at large. Such cyber terrorist activities could include establishing a network over the Internet to implement illegal activities online, using code language to communicate and implement the illegal traffic of drugs and other products, sending scare and threat mails to high-profile personnel and the like. The laws that deal with cyber terrorism are not the same for all the countries, and at least in the Indian context, there is enormous room for debate about these rules.
Cyber terrorists usually operate across boundaries, which means that they could collapse a country’s economic wellbeing or cultural peace from a remote area in some other part of the globe. To terminate or reduce such cyber crimes, universal laws and technical know-how is essential. Thus, a combination of political oneness among countries regarding this form of terrorism, along with universal laws and a technical workforce should work in tandem to see the end of such cyber terrorism.
THE FAST-CHANGING FACE OF CYBER CRIMES
A Symantec Internet Security Threat Report released in March 2006 affirms attackers have moved away from large, multipurpose attacks on network perimeters towards smaller, more focused attacks on client-side targets.
According to the report,12,13 which covered the period from June to December 2005, there were 1,896 new vulnerabilities recorded in the second half of 2005—the highest recorded number since 1998. There was also an average of 7.9 million phishing attempts per day—an increase of 39 per cent over the first half of 2005.
Cyber criminals are now moving towards a combination or blend of threats involving spyware, phishing and the like, as against single threats which were predominant in the past (see Table 16.1). Phishing, however, continues to be the primary threat. Anil Chakravarthy, Head (India Technical Operations), Symantec says, “Blended attacks are on the rise and it is difficult to classify these attacks under any particular category”. Says Chakravarthy: “We are preparing for a world where the risk is not to the machine but to an extended environment that is the infrastructure, information and transaction”.14
Table 16.1 Changing Face of Cyber Crime
| Area of Concern | Previous | Present |
|---|---|---|
Nature of the criminal |
Internet addicts in their teens, 20s and middle ages |
Professionals from the real world and terrorists |
Nature of the crime |
Propagation of viruses, worms or trojans to threaten individuals, identity theft through spoofing and phishing |
A combination of threats, both online and offline |
Motive of the crime |
For attention, revenge and destruction |
For money |
Nature of the victims |
Individual Internet users |
E-business solutions and e-commerce organizations |
Nature of security |
Machines and servers |
Entire infrastructure, interaction and information |
Source: Adapted from “Mafia Invades Cyberspace,” by Sapna Agarwal, Business Standard, Chennai edition, 1 August 2006.
PROTECTION FROM CYBER CRIMINALS
We perhaps already know of the following ways of protecting ourselves from cyber criminals.
- Any computer application should have a provision for authenticating the intended users with the help of passwords. Passwords by themselves have a set of rules that should be followed. For instance, passwords should be difficult to guess or hack and should be changed frequently. They should not be written down anywhere or confided to others.
- Check and audit systems within the company or group for illegal software. Also, check for intruders within the system. Check for upgrades or patches in software products.
- A firewall is either dedicated or running on another computer, which inspects network traffic passing through it, and denies or permits passage based on a set of rules.15 Firewalls are the most common and most frequently used measure to ensure the security of a system or application. Firewalls can be implemented in hardware or software or both. Apart from this, the network configurations should be monitored for defects or trespassing. This could greatly enhance the security of the systems.
- In data-sensitive applications, the most common method of protection is encryption. Encryption’s drawback is that it does not protect the entire system, an attack designed to cripple the whole system, such as a virus, is unaffected by encryption.
- Virus scan software is readily available off-the-shelf. This software helps in detecting viruses of other infected files within the system. These applications should be executed frequently to defect viruses within the system.
- E-mail filters and specifically spam filters could be used in emails to enhance the security of this kind of Internet communication.
- If you are unsure about the safety of a Web site you are about to access or about an e-mail that you receive, do not access/open such files or sites. You could be a probable victim of a cyber crime.
Apart from these measures, the eradication of cyber crimes would involve a whole lot of activities ranging from and including identity management, data privacy and digital security, the protection of critical information systems and, of course, an enforceable legislation to punish the offenders (Box 16.4).
According to Arvind Sharma, Director of the Institute of Development and Research in Banking Technology, “New technologies had opened the door to an increasing number of security threats. However, security surveys show that most of these threats are launched from within an organization. To defy insider attacks, all organizations should focus on developing specialized skill-set among employees; training and awareness could help avoid many of the problems related to security”.16
ETHICAL ISSUES
Crimes are unethical at any level. It becomes worse when one uses a tool that is primarily intended to bring societies closer, as the very means of committing the crime. That is the reason why, of late, experts consider cyber crimes to be more dangerous and damaging than physical crimes. For example, a recent IBM survey reports that Indian IT executives believe more strongly than their global peers that cyber crime is more costly to their organizations than physical crime. The report also says that the threat of cyber crimes comes from a number of different places, most of which are from new sources that companies have to be mindful of.17
BOX 16.4 OFFENCE SECTION UNDER IT ACT
The different sections under the IT Act which deals with cyber offences/crimes are listed in the table below. The power to investigate all offences under this Act is given to the Deputy Superintendent of Police.
Offence |
Section Under IT Act |
|---|---|
Tampering with computer documents |
Sec. 65 |
Hacking with computer systems, Data alteration |
Sec. 66 |
Publishing obscene information in electronic form |
Sec. 67 |
Unauthorized access to protected system |
Sec. 70 |
Misrepresentation or suppression of material |
Sec. 71 |
Breach of confidentiality and privacy |
Sec. 72 |
Publishing false digital signature certificates |
Sec. 73 |
Damage to computer system |
Sec. 74 |
Computer-related crimes covered under Indian Penal Code (IPC) and Special Laws
Threats by e-mail |
Sec. 503 IPC |
Derogatory/offensive e-mails |
Sec. 499 IPC |
Forgery of electronic records |
Sec. 463 IPC |
Bogus Web sites, cyber frauds |
Sec. 420 IPC |
E-mail spoofing |
Sec. 463 IPC |
Web-jacking |
Sec. 383 IPC |
E-mail abuse |
Sec. 500 IPC |
Online sale of drugs |
NDPS Act |
Online sale of arms |
Arms Act |
Source: V. Shiva Kumar (2003) Cyber Crime—Prevention and Detection www.cidap.gov.in/documents/ Cyber%20Crime.pdf and Common LII (2000). Indian Legislation: Information and Technology Act 2000, www.commonlii.org/in/legis/num_act/ita2000258/
The IT domain gives ample scope for unethical behaviour—be it the curiosity to find a friend’s password and hack his or her inbox, or the extortion of banks after an identity theft; only the intensity of the crime varies. The fact remains that we tend to become unethical very often when we interact with computer systems in general. Several examples could be furnished to prove this point. When we are desperate to get some information from a friend’s desktop while he or she is away, do we not try to log into the system by attempting a few passwords that he would have probably furnished? This is probably an action that may be condoned considering the fact that it is practised very often; but there is no doubt that it is unethical nonetheless. Another example is the use of pirated software in several organizations in spite of the fact that internal audits and checks are in place.18
Learning the techniques to play around with information and technology is not a very difficult thing to do, at least for people who have the technical ability but a lack of ethical inclination. Extortion of banks, for instance, not only loots the financial resources of the victim but also his/her peaceful state of mind. If it is an organization at large that is affected, these organizations probably do not speak up for fear of negative publicity. They may refuse to admit to their inadequate defenses since it may ruin the public trust and reputation that the enterprise has otherwise.
The deployment of human firewalls is perhaps the most important step towards ensuring foolproof network security in an organization. The weakest link in the security chain is human and therefore emphasis should be made to strengthen this link, by setting up departmental firewalls to compliment individual firewalls that are not adequate.19 “Without the cooperation of people, none of these solutions will work properly. Human error could cause major security problems and most of the online threats arise from lack of awareness”.20 The intolerance to cyber crimes is steadily growing and Internet users are becoming more aware about and defensive against cyber crimes.
CYBER CRIMES: RECOMMENDATIONS FOR THE BUSINESS SECTOR
The effects of cyber crimes in business could be devastating! The crimes that are committed against business groups or organizations could have adverse effects on the way people look at technical enhancements to their business. Especially at this point of time, where new e-businesses are emerging every minute, measures that would help these businesses combat these crimes are of utmost importance. As mentioned earlier, crimes such as defamation and extortion over the Internet may not only create a potential for financial losses but could also ruin the reputation of the firm in more than one aspect. Thus, the need of the hour for business concerns is to take specific and immediate action to create awareness about the dangers of cyber space. Appropriate measures to analyse/recognize probable threats to the information domain in cyber space and steps to mitigate them could be the only solution to such business issues.
Preventing business systems from hacking is just one step to prevent criminals from robbing information. Hacking is not the real problem, whereas the crimes that are committed as a consequence of identity theft should be treated more seriously. The increasing rate of criminals who use the security loop holes to break into the information domain or offer their services for a significant fee (as was met with in the case of the criminal who sold bank accounts) or stalk the firm for a ransom should be viewed as much more serious issues to tackle.
Business intelligence should include risk assessment, mitigation plans, measures to step up cyber security using specialized tools, training programmes to create awareness for employees and most of all a business analysis wing that includes criminal intelligence analysis. This is where the concept of ethical hacking comes into the picture. Ethical hacking is the process of using tools and techniques to attack a security system for the sake of its owners, seeking vulnerabilities that a malicious hacker could exploit. While their unethical counterparts use hacking to cause problems for users, ethical hackers use the same techniques to probe into domains and report loopholes in the implementation of security in the network.
Infiltration is another problem for businesses that is as dangerous, if not more, than Net extortion. Knowing one’s customers has become the keyword in business alliances today. Apparently the danger of this crime is more pronounced when businesses operate across many countries. Even the countries that are technically in the forefront, and are economic giants face problems of infiltration, and hence there is a growing need for a thorough background check before getting associated with partners.
Everything said and done, any measure that is aimed at controlling the occurrences of these crimes would not be complete without efficient awareness programmes, not only at the intra-organization level, but also at an inter-organizational level. This means that business firms should share their learning and ‘best practices’ with other firms and law enforcement agencies. Firms should work in tandem with the government and the legal system to ensure that no violation of rules happen in their domain.21
CYBER CRIMES IN THE INDIAN CONTEXT—INDIAN LAWS GOVERNING CYBER CRIMES
Though there is a growing awareness about cyber crimes among our countrymen and about the measures that can be implemented to prevent them, one cannot deny the fact that India is still very susceptible to Internet frauds. This is obvious from the many incidents that are reported day after day by the media. A whole lot of cyber thefts, e-mail threats not sparing even the President of the country, spoofing and credit card frauds has been the cause of a set of new laws to be enforced by the Indian legislation. In spite of this, the preparedness of Indian users (and specifically companies that use the Internet for business needs) to address cyber crimes have been rated as low. In India, compared to other sectors, the risk posed to the financial sector is the highest according to the findings of KPMG’s survey titled: “India Fraud Survey Report 2006”. According to this survey, just 24 per cent of the respondents had the relevant physical and logical access controls to tackle serious cybercrime issues. Topping the radar of risks are banking, insurance, mutual funds and asset management companies followed by NBFCs/investment banks. Information communication and entertainment sector follow in the pecking order.22
India enacted the IT Act (Box 16.4) in May 2000 based on the UNCIRAL model recommended by the general assembly of the United Nations, to become part of a select group of countries which have put in place cyber laws. Eight years down the line, law enforcement agencies are still groping in the dark on how to use the Act effectively. Still worse, there are very few cases that have been registered under the IT Act, not with-standing the exponential growth-rate of cyber crimes, including usage by terrorist outfits. The National Crime Record Bureau counts only 68 registered cases in 2004 while it was a measly 60 in 2003. It is estimated that an average of around 300 cases are registered under the Act in Bangalore and about one-third of it in Chennai annually. The cyber crime cells have the jurisdiction to deal with offences under sections 65, 66, 67 of the IT Act which pertain to tampering of computer source documents, hacking of computer systems and publication of obscene information in electronic form. “Other crimes conducted with the help of the computer fall under the Indian Penal Code and are handled by local police”, points out Mr. Shivanand Reddy, Hyderabad Superintendent of Police (cyber crime cell). According to his Bangalore counterpart, Mr. Uttappa, “The IT Act as a law is 60% adequate and if used along with IPC could be more effective”. Apparently, court procedures and geographical boundaries happen to be the most important road blocks to ensuring cyber security.23
As in 2007, the year 2008 also saw a rise in security threats in the cyber scene, spyware and rougeware. The list of cyber crimes that are emerging with the dawn of technical inventions are limitless, and are getting uncontrollable. The most worrying five among them being:
Bot and Botnets: This refers to a network of computers that are automated to perform spamming activities. The only consolation in this calamity is that India is not seen in the map of Botnet hosts and controllers at present.
Phishing: This crime has been a great cause for concern in the past few years and continues to be a growing phenomenon.
Vishing: This crime involves the stealing of personal and financial details (identity theft) of unsuspecting victims using VoIP (voice over Internet protocol) calls.
VoIP refers to a category of hardware and software that enables users to avail the computer as the transmission medium for making telephone calls by sending voice data in packets using the Internet rather than traditional circuit transmissions.
With VoIP telephony getting more and more popular in the Indian markets, this crime certainly has to be looked out for in the coming years.
Rootkits: These programs capture the ‘root access’ or in other words, take control of the system without being detected by any scanner.
Mobile malwares: These tools can be installed in mobile handsets to spy the activities of mobile users. The India mobile scene is unprotected, leaving it open for attackers to take advantage.24
Apart from the laws that govern cyber crime, the highly commendable trend in the Indian context is the training of police personnel planned by the Central Intelligence agencies along with internal security experts in the Union Home Ministry. Training is being given to police personnel of the intelligence wing and anti-terrorist squads of various states, in intercepting and breaking coded messages that different terrorist groups exchange. Probably, this kind of training, overlapped with an awareness of exchanging such information over Internet applications could provide the ideal ground for identifying criminals more efficiently.25
The cyber crimes mentioned in this chapter do not form an exhaustive list. There are many more forms of crimes, and appropriate measures that are emerging to protect ourselves against such crimes.
CONCLUSION
The case study elaborates on the various categories of cyber crimes that are prevalent in cyber space, the fast-changing and worrying trends in the cyber criminal world, the laws governing them in our country, the preventive measures that can be suggested to different kinds of users and the evolving crimes to look out for in the forthcoming years.
There are two sides to the golden coin of technology. On the one side, lies a plethora of opportunities that could make the world a more challenging and interesting place to live in, giving room for enormous information sharing, tremendous growth of businesses and innumerable answers to our problems, be it any domain. It is an information repository, telephone, entertainment medium, business mediator and much more rolled into one. There is however, a huge ‘but’ in the midst of the above mentioned fact, which otherwise makes the Internet seem like a green pasture. The pleasant view of the Internet is only for people who think straight, who are thankfully, the much greater section. For the other section of society, the proportion of which is on the rise and is eating into the space of the first category, the Internet is a tool to attain wealth and/or power, a tool to cause damage to name or property or to take revenge, or just a pleasure tool to misuse and enjoy. They see the other side of the coin—the dimension that is not meant to be touched or used.
The responsibility lies with every Internet user to do something, big or small to stop the occurrence of such unethical things. The least we can do is to be aware of what could probably happen to us or our company and to implement measures to save our information on the Internet. Taking a step further, we could keep our friends and associates informed too.
DISCUSSION QUESTIONS
- What are cyber crimes? Classify them based on (a) the modus operandi, (b) the targeted victims and (c) the type of crime
- Differentiate between the terms spoofing and phishing. Furnish examples from the real world.
- Discuss the legislations pertaining to cyber crimes. What are your suggestions to make Indian legislations more effective to combat cyber crimes?
- What are the factors that contribute to the tremendous increase in cyber crimes? Enumerate some of the measures that can be adopted to prevent them.
- Though technology is extremely useful for organizational efficiency and productivity, it can also be easily misused. Comment.
- Explain some of the ways and means of protecting ourselves as individuals from internet crimes.
- The deployment of human firewalls is perhaps the most important step towards ensuring foolproof network security in an organization. What is your take on this statement?
- What is cyber terrorism? Why is it becoming a matter of enormous concern in today’s global scenario?
- What are your recommendations to the business sector to help themselves from the devastating effects that cyber crimes could cause to their information security?
- What are some of the latest incarnations of cyber crimes that have emerged in the last one or two years? Furnish examples from your own experience or from what you have heard/read.
FURTHER READINGS
1. http://cybercrime.planetindia.net/
2. www.interpol.int/public/TechnologyCrime/Default.asp
6. www.ic3.gov
