Overview
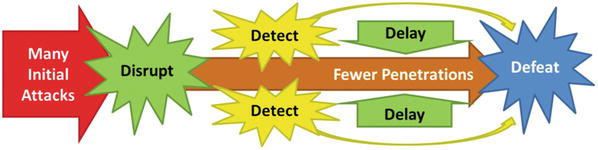
- A good cybersecurity architecture alone is not going to stop cyberattackers who are targeting an enterprise and attempting to defeat its cyberdefenses.
- Cyberdefense capabilities need to be applied in ways that disrupt, detect, delay, and defeat targeted cyberattacks.
- This chapter describes
- the art of cyberdefense;
- how to apply enterprise cybersecurity capabilities to counter unknown, but anticipated, advanced threats;
- the sequence of steps attackers will take; and
- practical challenges involved with deploying a program that is effective while also being cost-effective.

Topics
- Attacks Are as Easy as 1, 2, 3!
- Enterprise Attack Sequence in Detail
- Why Security Fails Against Advanced Attacks
- Business Challenges to Security
- Philosophy of Effective Defense
- Elements of an Effective Cyberdefense
Attacks Are as Easy as 1, 2, 3!

- From a single compromised endpoint computer inside the targeted enterprise network, attackers can exploit common vulnerabilities to gain administrative privileges.
- Flaws are inevitable.
- Systems malfunction.
- People make mistakes.
- Defenders do not detect the attackers on the inside.
- Attackers will eventually succeed in obtaining administrative privileges, regardless of the defenses.
- Attackers can use such privileges to access, modify, or destroy whatever data they choose.
- Cybersecurity Goal—Make advanced attacks more challenging than 1, 2, 3!
- Deploying both preventive and detective controls can make the attackers’ job more difficult.
Enterprise Attack Sequence in Detail
Context
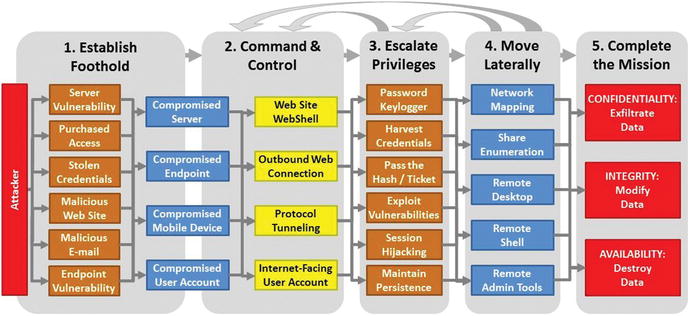
- Targeted attacks methodically work through victim defenses.
- The attack sequence gives defenders opportunities to successfully defend the enterprise by tracing the attack backward and identifying the data attackers might want to steal, modify, or destroy.
- Attackers might target data on servers, on endpoints, over the network, in backups, or on its customers’ or business partners’ systems.
- Attack steps are not always executed exactly in sequence.
- This process does not deal with distributed denial of service attacks.
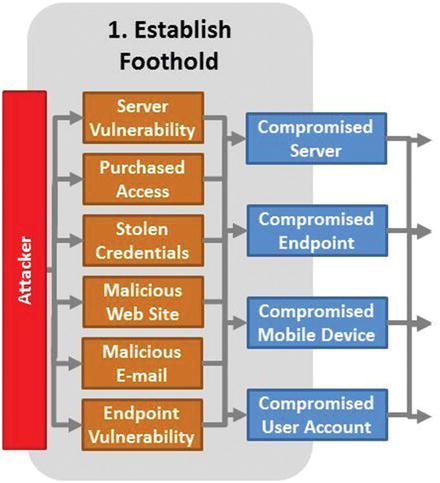
Attack Sequence Step 1—Establish Foothold
- Foothold gives the attacker the ability to access enterprise resources and is often obtained by the following:
- Server vulnerability
- Purchased access
- Stolen credentials
- Malicious web sites
- Malicious e-mail
- Endpoint vulnerabilities (home networks, improperly configured public Wi-Fi networks)
- Foothold generally consists of the following:
- Compromised server
- Compromised endpoint
- Compromised mobile device
- Compromised user account
- From the foothold, attacker moves on to the next attack step.
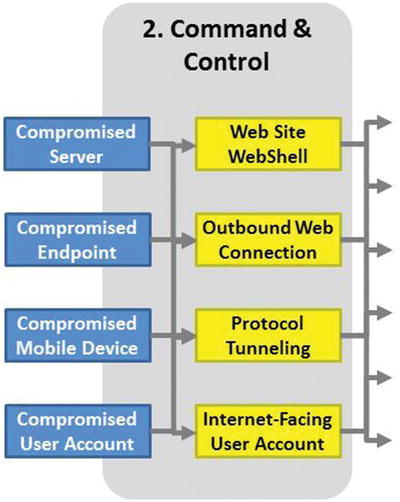
Attack Sequence Step 2—Establish Command and Control
- From the foothold, the attacker can execute commands.
- Attacker may escalate privileges or move laterally before establishing command and control (C2).
- Generally, attacker establishes C2 connectivity sooner rather than later to manually control the activities within the victim systems.
- Main C2 methods include the following:
- Web site webshell
- Outbound web connections
- Protocol tunneling
- Internet-facing user accounts
- With C2, the attacker can install and operate additional malware and tools beyond those used to establish the foothold, obtain additional privileges, and move laterally.
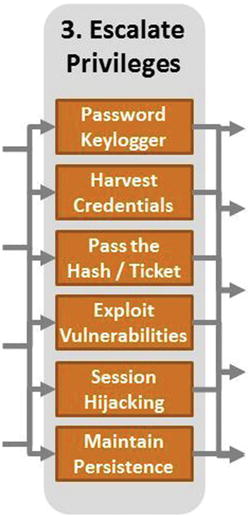
Attack Sequence Step 3—Escalate Privileges
- By escalating privileges, attackers can take control of additional servers and endpoints closer to the attack goal.
- Escalating privileges can involve gaining control of systems administration accounts that have permissions to log on to a large numbers of machines.
- Common escalation techniques include the following:
- Password keylogger
- Harvest credentials
- Pass-the-hash or pass-the-ticket
- Exploit vulnerabilities
- Session hijacking
- Maintain persistence
- Generally attacker goes through several cycles of privilege escalation and lateral movement.
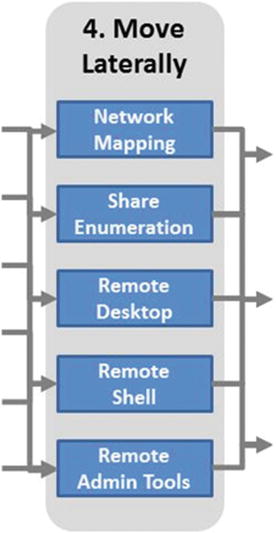
Attack Sequence Step 4—Move Laterally
- Attacker moves from computer to computer to expand the foothold.
- For example, go from a regular user computer to endpoint administrator privileges to file server to e-mail administrator to e-mail server to domain administrator to enterprise domain controller servers …
- Moving laterally includes the following:
- Network mapping, share enumeration
- Remote desktop, remote shell
- Remote administration tools
- Attacker moves around and may not install malware on all systems touched.
- If attacker has control of privileged network accounts, attacker may switch to using systems administration tools already built into computer operating systems and permitted on the network.
- Attacker may get control of the enterprise without the enterprise’s knowledge.
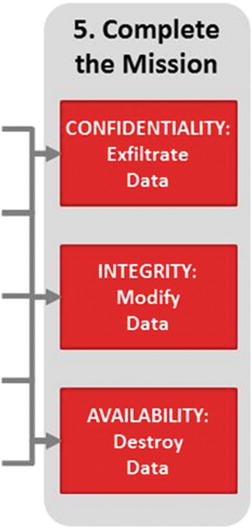
Attack Sequence Step 5—Complete the Mission
- Completing the attack mission includes the following:
- Confidentiality: Steal data, which might include logon credentials, credit card numbers, and financial or health care accounts for identity theft.
- Integrity: Modify data, which might include changing records to steal money by either altering financial records or using compromised credentials to access financial institution online and move money out of victim accounts.
- Availability: Destroy data, which might include (1) ransomware that encrypts victim’s data and is used for blackmail, (2) denial-of-service attacks that render the enterprise’s Internet services inaccessible, or (3) availability attack to distract defenders or cover up the attack after the real heist has been completed.
- After this step, the victim is left to pick up the pieces and figure out what just happened.
- Many victims do not even know that the attack has taken place until weeks or months later.
Why Security Fails Against Advanced Attacks
Context
- Why can’t IT simply stop attacks from gaining a foothold in the first place?
- Why can’t computers be secure against attacks?
- Why are complex operating systems impossible to secure perfectly for an extended period of time?
- Answers are complex and include the following technical challenges:
- The failure of endpoint security
- The “Inevitability of ‘the Click’” challenge
- Systems administration hierarchy
- Escalating attacks and defenses
Technical Challenge 1—The Failure of Endpoint Security
- Modern operating systems are too large and complex to be fully protected.
- Security statistically reduces the percentage of compromised endpoints, but cannot eliminate them altogether.
- Endpoints are always susceptible to being compromised.
- Rules of thumb for # of compromised endpoints



Technical Challenge 2—The “Inevitability of ‘the Click’”1
- With only six messages in an e-mail phishing campaign, there is an 80% chance one recipient will click on an attachment or link related to e-mail.
- Large enterprises send thousands or millions of e-mail messages.
- The probability of at least “one click” in an e-mail phishing campaign increases significantly as more e-mails are sent during the campaign.
- Conclusion #1—Enterprise endpoints and servers will be compromised.
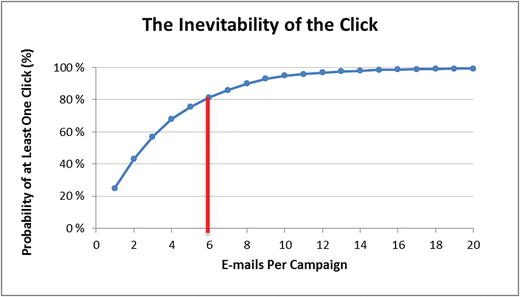
- Conclusion #2—Enterprise must layer its defenses so endpoints mostly likely to be compromised first are not the most critical ones.
Technical Challenge 3—Systems Administration Hierarchy
- Data center applications are complex and difficult to protect well.
- Application functions
- are layered upon each other;
- can be connected to the network;
- often allow privileged access through systems administration account usernames and passwords; and
- further down the stack can generally bypass security of layers above.
- Data center layers are often network-connected along with computer hardware intergrated Lights-Outs (iLO) interfaces.
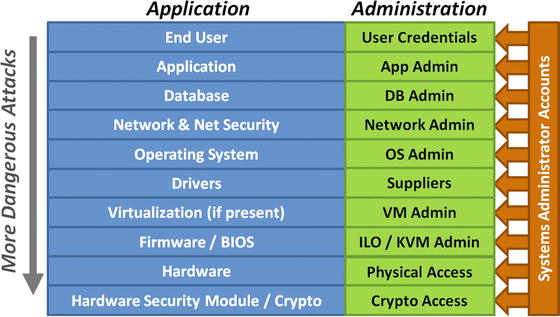
- When an endpoint gets compromised, the attacker has an opportunity to access the enterprise’s systems administration channels and bypass most of the enterprise security measures.
Technical Challenge 4—Escalating Attacks and Defenses
- For every defensive capability, there is a corresponding attacker tool, technique, or procedure.
- There is no perfect or unbreakable defense.
- Real-world attacks often use relatively simple attack methods.
- Viruses
- Spear phishing
- Published vulnerabilities
- Credential theft
- Web site compromise
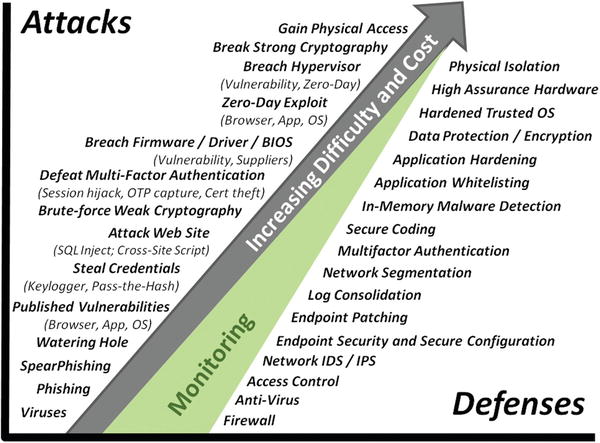
- Even with data encryption, high-assurance hardware, and physical isolation, enterprises remain open to more basic formats of attack.
Business Challenges to Security
Context
- In addition to technical challenges of building effective enterprise defenses, what are the associated business challenges?
- Security programs fail, in part, due to business considerations rather than technical considerations.
- For an enterprise security program to be effective, the enterprise needs to understand its business and properly phrase its security needs in terms of business costs and business value.
- Business Challenges include
- tension between security and productivity;
- maximum allowable risk;
- security effectiveness over time; and
- security total cost of ownership.
Business Challenge 1—Tension Between Security and Productivity
- Security and productivity are often diametrically opposed.
- Security measures tend to drive up costs, slow down progress, and add steps.
- Vendors often claim their security technology is seamless and invisible to users, but it requires installation, upgrades, and operation.
- It is almost impossible to add security to an enterprise without impacting productivity in some way.
- Technologies limiting access to systems and data require an ongoing effort to grant and revoke accesses on an ongoing basis.
- Productivity is impacted when people cannot do their jobs while waiting for access.
- Costs can be relatively small, but if a company makes $1B per year, reducing productivity by 1% costs the company $10M in lost productivity.
- The costs of security are offset by the costs of incidents that occur when security fails, but these amounts are difficult to estimate.
Business Challenge 2—Maximum Allowable Risk
- Enterprises continually try to minimize costs to include security.
- Budget cuts often drive security to reduce costs and operate uncomfortably close to a cybersecurity disaster.
- Green Zone: Security budget may be bloated and probably needs to be cut.
- Yellow Zone: Security budget is about right, but enterprise feels somewhat uncomfortable regarding the security risks being managed.
- Red Zone: Security budget may be too low and can result in multiple breaches.
- Since some security costs are mandated by regulation, why would there be pressure to reduce security costs?
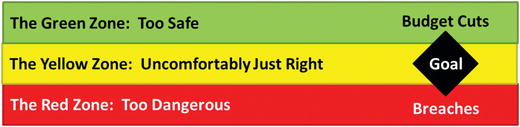
- Money spent on security is money taken away from growth, profits, or shareholders.
- Cutting the security budget and balancing security capabilities against risks encompass the concept of maximum allowable risk (in other words, how much security risk is acceptable?).
- Enterprises use metrics (such as probes, attacks, and intrusions), in part, to show management how the security risks are being stopped/mitigated.
- Metrics help everyone understand how close the enterprise is operating to a potential cybersecurity disaster.
Business Challenge 3—Security Effectiveness over Time
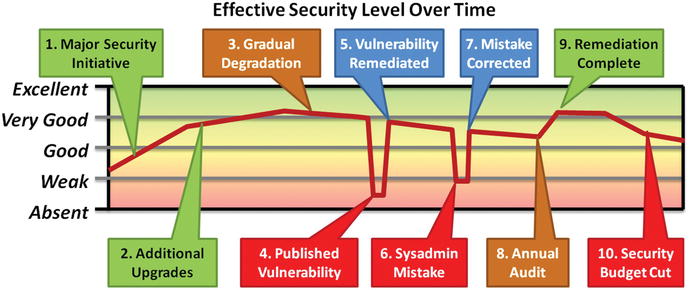
- An enterprise’s security posture effectiveness is not static and is subject to factors within and outside of its control.
- Emerging vulnerabilities , setbacks, and mistakes impact security effectiveness.
- Audits/projects identify and remediate security program issues.
Business Challenge 4—Security Total Cost of Ownership
- Total Cost of Ownership (TCO) consists of multiple cost components.
- Installing, maintaining, and operating enterprise security controls
- Maintaining/initiating an incident response capability and restoring normal operations
- Remediating lost productivity due to not having necessary privileges, requesting access, or processing policy exceptions.
- Prevention Security Profile vs. Detection and Response Security Profile
- Prevention suggests large numbers of security controls resulting in large amounts of lost productivity due to requesting permissions, re-certifying accesses, and interacting with security controls.
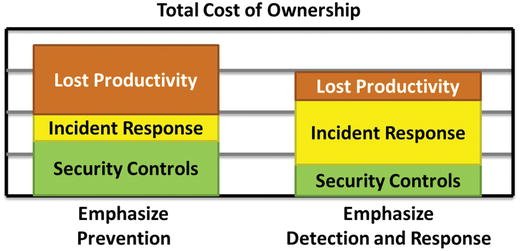
- Detection and response suggest the enterprise will have cheaper controls and less lost productivity due to fewer personnel maintaining firewall rules or re-certifying accesses permissions, but they will require more incident response resources.
- It is important for an enterprise to consider TCO when evaluating its cybersecurity program.
Philosophy of Effective Defense
Context
- What makes up an effective cybersecurity program?
- How do defenses work in the physical world, law enforcement, and warfare?
- What real-world defense examples can IT incorporate into an effective cybersecurity defense?
- Nowhere outside of IT do people rely exclusively on technologies such as walls, doors, and gates to stop attackers.
- Perhaps this physical world observation is a hint as to what an enterprise needs to do when implementing an effective cybersecurity program.
- Defense examples include the following:
- Mazes vs. minefields
- Disrupt, detect, delay, defeat
- Cybercastles
- Nested defenses
Defense Example 1—Mazes Vs. Minefields
- What is more scary, a maze or a minefield?
- Many people enjoy navigating a maze.
- No one wants to walk across a minefield.
- Enterprise IT defenses often look like mazes.
- Firewalls block network traffic.
- Network protocols use accounts for authentication.
- Access controls restrict who can see individual IT systems.
- Like neighbor fences, such defenses amuse determined attackers who have tools and techniques for every defense.
- Attackers can see every obstacle clearly and have time to figure out a way around it.
- Minefields look like a walk across a field, but the mines cannot be seen.
- If there are enough mines, the probability of safely walking across the field is slim.
- Attackers do not know which steps are safe and which ones are not safe.
- An attack is significantly more challenging.
 Photo credit: Floresco Productions/Getty Images.
Photo credit: Floresco Productions/Getty Images. Photo credit: Charlie Bishop/Getty Images.
Photo credit: Charlie Bishop/Getty Images.
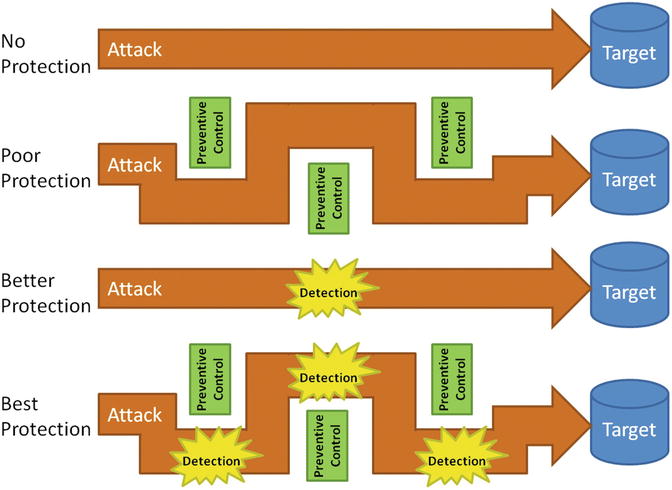
- When an enterprise only contains preventive controls, attackers eventually figure out a way to defeat each control.
- Detection provides an opportunity to respond to the attackers and repel them.
- Combining preventive and detection controls
- slows attackers down;
- gives enterprise more time to detect and respond to the attack before it is successful; and
- leverages the advantages of both mazes and minefields.
Defense Example 2—Disrupt, Detect, Delay, Defeat
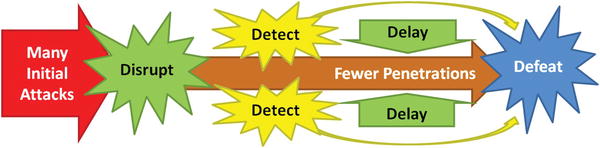
- US Army Field Manual 100-5, Operations, makes the following two statements:
- The purpose of the defense is to “retain ground, gain time, deny the enemy access to an area, and damage or defeat attacking forces.”
- “A successful defense consists of reactive and offensive elements working together to deprive the enemy of the initiative.”
- Consider the four Ds of an effective cyberdefense.
- 1.Disrupt attacks to make them more difficult and deter less-determined attackers.
- 2.Detect attacks so defenders can learn about them and prepare a response.
- 3.Delay attacks in progress via obstacles requiring attackers spend time working around them.
- 4.Defeat attacks as quickly as possible and before they can accomplish their objectives.
- 1.
- Defeating cyberattacks involves removing the attackers from the enterprise and sending them back to their starting point.
- It is unlikely an enterprise will be able to catch the attackers.
Defense Example 3—Cybercastles
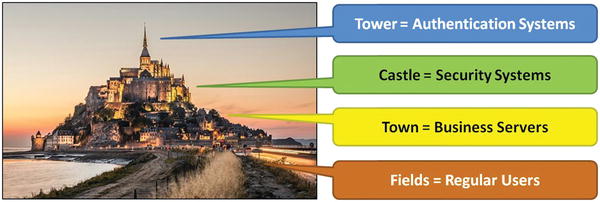
Photo credit: Jimmy Nilsson/EyeEm/Getty Images.
Enterprise defenses can be viewed in terms of security zones with progressively increasing security.
- 1.Fields were where the food was grown, but were almost completely indefensible. Attackers traveled across the fields at will, but such travel did not guarantee a successful attack. Fields are like business computers that are almost impossible to defend.
- 2.Town was better protected than the fields by a fence or low wall, which was easily scaled. Town is where commerce occurred. Town is like the enterprise business servers.
- 3.Castle was designed for protection with high walls and layers of defenses. The person who controlled the castle protected the town. Castle is like the enterprise security systems where most key business occurs.
- 4.Tower was designed , along with enclaves and keeps, to be the place where the weapons were stored and battles were fought, even when the initial castle defenses were breached. If defenders controlled the tower, enclaves, and keeps, they could eventually retake the castle, town, and fields. The tower is like enterprise authentication systems that enable an enterprise to beat back attackers who have taken control of everything else. Once an enterprise loses control of authentication systems , its position is extremely precarious.
Defense Example 4—Nested Defenses
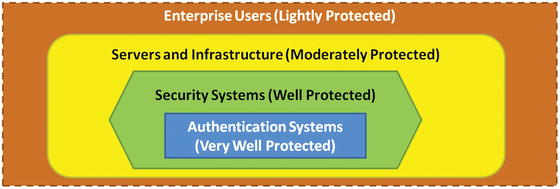
- During cybersecurity defense planning, the enterprise can establish four security zones with corresponding security scopes.
- In some cases, the four zones are simply different parts of a single enterprise security scope.
- Security controls may be tailored to balance the need for security with the business need for operational flexibility.
- This approach integrates security policy, network segmentation, endpoint protection, and other capabilities to deliver appropriate protection to different enterprise zones.
- The nested security perimeter forces the attackers to penetrate progressively better protected perimeters to take control of the enterprise.
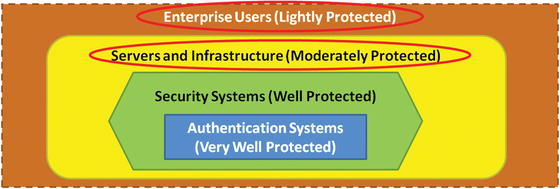
- Enterprise users are like medieval town fields where most of the productivity takes place and are the hardest to protect.
- Key protection challenges include users surfing the Web, receiving e-mail, taking laptop computers home or on the road, and allowing mobile or BYOD devices.
- Detecting compromised user endpoints and containing them before they can do significant damage may be significantly easier and cheaper than trying to harden them from compromise in the first place.
- Servers and infrastructure are like the medieval town where most of the enterprise business and commerce lie.
- These systems are the ones most worth investing to protect.
- However, these systems are moderately difficult to protect because of the large amount of activity, upgrades, and connectivity.
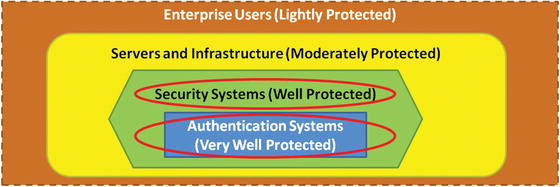
- Security systems are like the medieval castle that protect the rest of the enterprise.
- When the security systems are running on the same operating systems, using the same accounts with the same network connectivity as everything else in the enterprise, they become no harder to hack than any enterprise servers or endpoints.
- Smart attackers will compromise security systems as quickly as possible so they can take control of the rest of the enterprise.
- Authentication systems are like the castle tower with centralized authentication.
- The authentication systems are the keys to the kingdom.
- With control of the systems, attackers can issue themselves credentials, grant permissions to the created credentials, and take permissions away from legitimate system administrators.
- Authentication systems must be treated as if they cannot be compromised. Any breach of their integrity must be detected and dealt with immediately.
Elements of an Effective Defense
Context
- What is the goal of an effective cyberdefense?
- Simply stated, the goal is to take the onus of perfection off of the defender and push it back onto the attacker, where it belongs.
- With an ineffective cyberdefense, the defender has to do everything perfectly to protect the enterprise.
- With an effective cyberdefense, the attacker has to do everything perfectly to attack the enterprise.
- Defensive techniques that are particularly effective at disrupting, detecting, delaying, and defeating common attacks to include the following:
- Network segmentation
- Strong authentication
- Detection
- Incident response
- Resiliency
Effective Defensive Technique 1—Network Segmentation
- Network segmentation
- It is the oldest effective defensive technique.
- It has been used for decades to protect classified military and civilian network.
- Stuxnet attack demonstrated that even isolated, air-gapped networks can be attacked.
- Segmentation and network isolation
- They make the attackers’ job orders of magnitude more difficult than attacking a monolithic, fully connected, and unmonitored internal network.
- In legacy networks, Internet-facing DMZ servers are isolated, but everything else is in a single “trusted zone.”
- In fully segmented networks, each major function is isolated from the others.
- In general, the network segmentation model should be as follows:
- Nested (cybercastle analogy)
- Integrated into the enterprise security scope architecture (risk assessments)
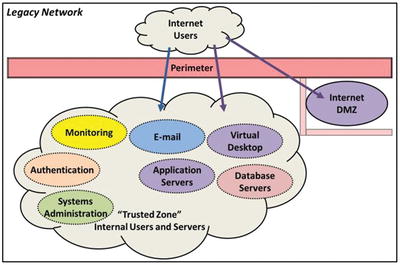
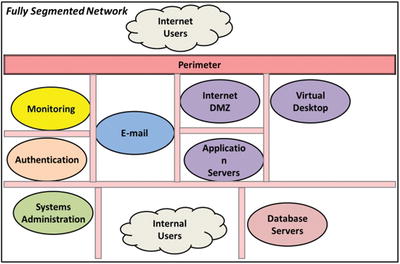
- Systems in different security scopes should be segmented at the network layer.
- In between network segments, the enterprise should have its full range of network protection capabilities such as firewalls, IDS/IPS sensors, network recorders, and data leakage protection technologies.
- Well-segmented networks
- allow legitimate network traffic to follow straightforward patterns that are easy to protect; and
- allow traffic to follow patterns that can be monitored so security can respond to malicious patterns.
- The best defense is the one that detects the attackers and alerts defenders so they can respond.
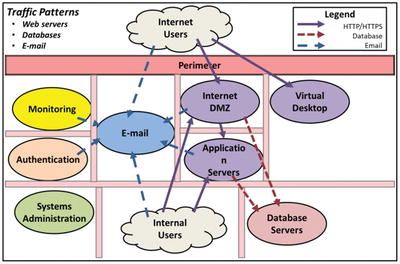
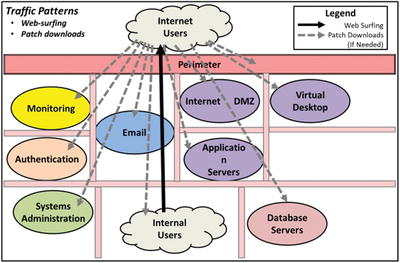
Effective Defensive Technique 2—Strong Authentication
- Traditional authentication
- Consists of a username and password
- Relatively easy for attacker to find such credentials
- Strong authentication
- Involves users proving who they are over a network or on enterprise computers by combining something they have with something they know
- Requires the attacker to physically steal the token used for secondary authentication or clone the token
- Is strong authentication foolproof?
- Absolutely not!
- Subject to “session hijacking” where attackers take control of the user’s computer and then wait for the user to log on before sending illicit commands
- Overall significantly reduces the odds of a user’s credentials being used without the user’s consent or knowledge
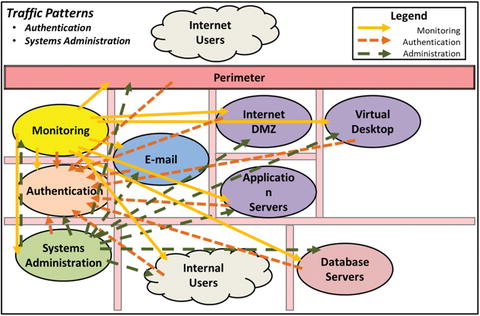
- Segmentation protects security scopes (and business functions) from each other.
- Network security methods can detect attacker attempts to move laterally across the segmented network.
- Strong authentication coupled with solid network segmentation contributes to an effective cyberdefense.
Effective Defensive Technique 3—Detection
- In many cases, an enterprise may not care if an attacker gains control of a single enterprise system or a single user account from the Internet or even inside the environment—particularly over a short period of time.
- What makes these attacks insidious is the following:
- If the attacks are allowed to progress for hours or days or weeks or months, undetected and unchecked
- If attackers gain control of enterprise systems administration systems
- If the enterprise simply blocks attackers, they will continue to pound on enterprise defenses over time until they can get around the block.
- Given enough time, attackers will eventually defeat every obstacle the enterprise can put in their way.
- Design enterprise controls focus on detecting the adversary activity first, and then preventing it. In other words, think of the Audit First Design Methodology .
- Just as a minefield is most effective when the mines are arranged in haphazard, unpredictable patterns, an enterprise’s detective controls are most effective when they are somewhat arbitrary and hard to predict.
- Simple, but effective, detection rules include the following:
- On segmented network
- Detect port and network scans that extend from one segment to the next.
- Detect systems administration protocols such as secure shell or remote desktop when they originate from servers.
- For privileged accounts
- Send administrators a daily report showing all the computers where their accounts were used, along with an admonition to report any suspected account abuse.
- Alert
- on the use of network administration tools or scanning tools from workstations such as ping or traceroute;
- on the use of highly privileged network or service accounts on machines outside of the datacenter;
- on changes to static web content on Internet-facing servers;
- on outbound web connections other than patch downloads from Internet-connected servers; and
- on protocol anomalies in standard web traffic such as domain name service or simple mail transfer protocol.
- The goal of detection is to look at the attack sequence and design detection to alert multiple times before an advanced attack can succeed.
Effective Defensive Technique 4—Incident Response
- Some cyberattackers penetrate cyberdefenses no matter how well the defenses are designed, implemented, or maintained.
- Detecting cyberattackers is not going to save an enterprise if it does not have anyone
- responding to those alerts;
- investigating them to filter out false positives to identify the real attacks; and
- repelling those attacks so that business can continue.
- Incident response can be done by
- an enterprise response team that is always on standby; and
- a third party who is kept on retainer or otherwise engaged.
- It is critical the enterprise perform incident response to repel attacks when they occur and send the attackers back to their starting points.
Effective Defensive Technique 5—Resiliency
- Perhaps the most important property of an effective cyberdefense is resiliency.“Resiliency is the enterprise’s ability to withstand attacks that successfully compromise endpoints, servers, and accounts without those attacks resulting in the attackers gaining complete control. ”
- Resiliency means the following:
- Defenders have ability to dynamically respond to cyberattacks by containing them, remediating them, or isolating them
- Attacker’s plan is disrupted and defenders have time and room to maneuver in response to the attack.
- Resiliency includes the ability to
- rapidly rebuild compromised servers or endpoints;
- reset user credentials and obtain detailed logs of user account activity of accounts that may have been compromised;
- rapidly restore data or applications from backups that are known to be good and free of infection or malware; and
- isolate sections of the enterprise, or even the entire enterprise, from the Internet so attackers lose the ability to control their foothold.
- Resiliency gives defenders options in an incident response (that is, agility) that makes it possible for defenders to outmaneuver their attackers.
- Defenders can take control of the situation, achieve rapid containment, and remediate incidents before adversaries gain administrative control and complete their objective.
Footnotes
