Overview
- This chapter describes how the enterprise can use iterative assessments and prioritization to select, plan, resource, and execute progressive improvements to its cybersecurity posture.
- The cybersecurity program utilizes the following management tools:
- A framework for managing a cybersecurity program
- A quantitative method for assessing the program and identifying strengths and weaknesses
- Ongoing operations and cycles of improvements
Topics
- Enterprise Cybersecurity Program Management
- Assessing Security Status
- Analyzing Enterprise Cybersecurity Improvements
- Prioritizing Improvement Projects
- Tracking Cybersecurity Project Results
Enterprise Cybersecurity Program Management
Context
- Enterprise cybersecurity program management involves the following processes:
- Risk management
- Control management
- Deficiency tracking
- Process improvement
- Measurement
- Enterprise cybersecurity program management also involves an ongoing cycle of the following:
- Assessing threats and risks
- Making progressive improvements to mitigate threats and risks
- Collecting metrics from security operations
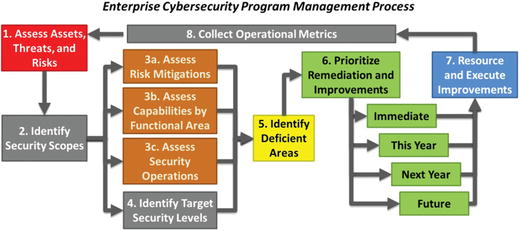
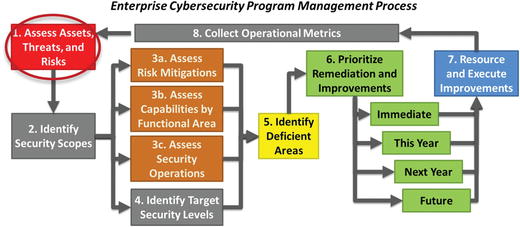
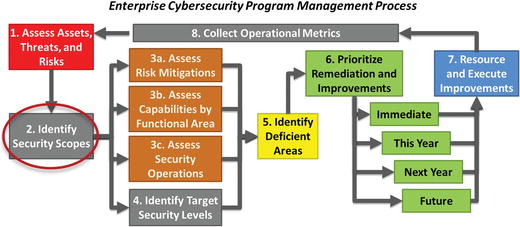
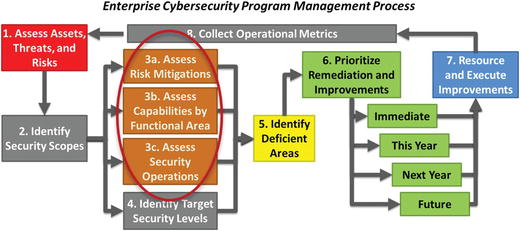
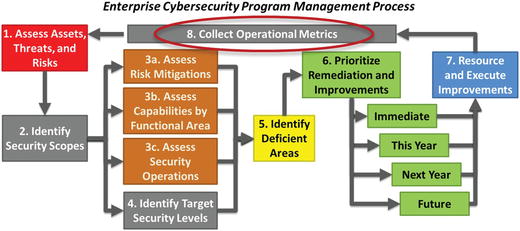
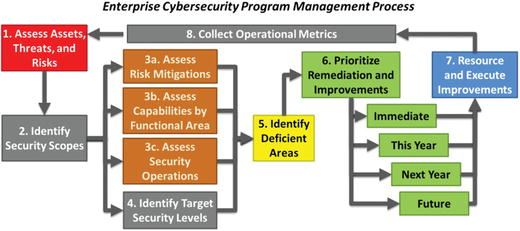
- This management process consists of the following major steps:
- 1.Assess assets, threats, and risks
- 2.Identify security scopes
- 3.Assess risk mitigations, capabilities by functional area, and security operations
- 4.Identify target security levels
- 5.Identify deficient areas
- 6.Prioritize remediation and improvements
- 7.Resource and execute improvements
- 8.Collect operational metrics
- 9.Return to Step 1
- 1.
Step 1: Assess Assets, Threats, and Risks
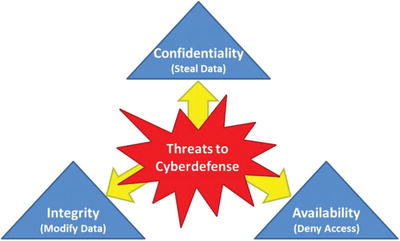
- Step 1 involves assessing enterprise IT assets, threats, and risks.1
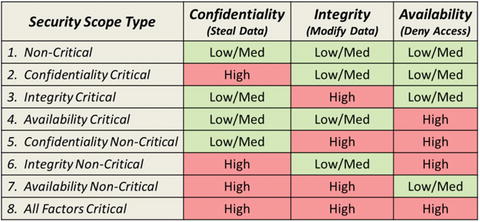
- Considers the missions of potential attackers
- Breach confidentiality
- Compromise integrity
- Disrupt availability
- Produces an output that is an understanding of the enterprise assets to be protected and the threats against those assets
- Assets may be corporate data, customer data, or critical services such as power generation or healthcare delivery.
Step 2: Identify Security Scopes
- Step 2 groups the enter prise assets identified in Step 1 and groups the threats and risks against them into security scopes for protection.2
- Cybersecurity capabilities should be tied to security scopes.
- Multiple scopes may use the same security capabilities.
- Scope boundaries are important for ensuring the right levels of capabilities are employed in the right places.
- Scopes enable the right balance between restrictive security and permissive operations must be achieved so that the enterprise can operate efficiently and effectively.
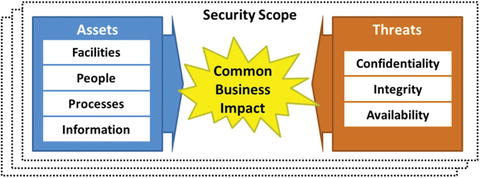
- Scopes are useful in identifying regulated data and systems for ensuring regulations are adhered to in a practical and economical manner.
- Challenges
- Enterprise must keep track of which policies, rules, and controls apply to which scope, potentially increasing complexity.
- Enterprise mitigates with a limited number of scopes aligned with the its regulatory obligations and cybersecurity architecture.
- Systems that cross scope boundaries, such as data interconnects and systems administration consoles, present challenges.
- Compensating controls may be necessary to ensure the interconnections do not become security vulnerabilities.
- Allowing these systems to receive e-mail, surf the Web, and run office productivity applications may open them up to targeted attacks.
- The goal, in part, is t o ensure the defensive measures applied to each scope are appropriate and economical.
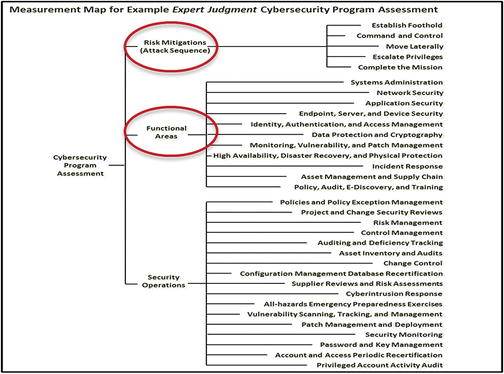
Step 3: Assess Risk Mitigations, Capabilities by Functional Area, and Security Operations
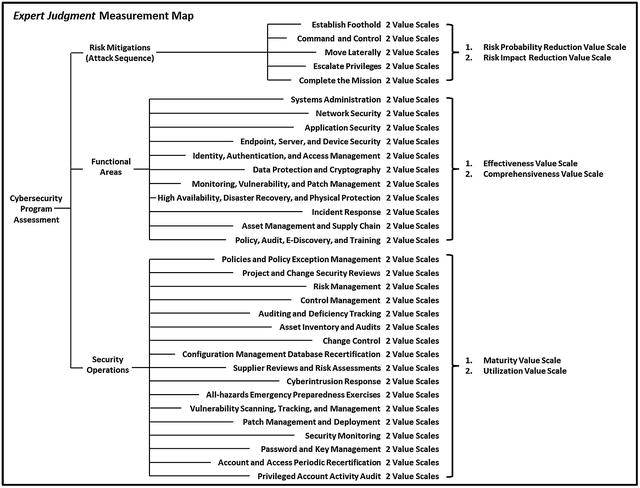
- Step 3 assesses the security of the security scope(s) in terms of the following:
- Risk Mitigations
- Use the attack sequence to evaluate enterprise’s ability to disrupt, detect, delay, and defeat attacks
- Consider each potential attack scenario and then aggregate the results
- Capabilities by functional area
- Examine the 11 functional areas and calculate corresponding Object Measurement (OM) scores
- Look out for functional areas that are deficient when compared to other functional areas
- Security Operations
- Examine the 17 security operational processes
- Assess the enterprise’s ability to perform these processes to operate its cybersecurity systems
- Once the scores are calculated, they can be aggregated and compared for evaluation and further analysis.
- If a security scope is inadequately protected, then specific improvement activities can be considered.
- The graphic depicts a p otential measurement map to be used to assess
- risk mitigations,
- capabilities by functional area, and
- security operations.
- The overall enterprise cybersecurity program assessment score can be tracked over time to show quantitatively how the cybersecurity posture evolves as improvements are implemente d.
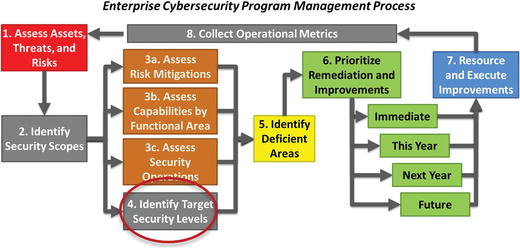
Step 4: Identify Target Security Levels
- For each security scope and associa ted assets, Step 4 involves using the risk assessment methodology to identify the target security levels and understand if the scope’s current security is adequate, inadequate, or even excessive.
- Target security level
- Represents the business tolerance for potential compromise within the scope
- Is used to balance the severity of the threats with the business desire for flexibility and unobtrusive security that does not impeded business agility
- Security scopes
- Limit the number of systems and people who are subject to the most stringent security protection
- Help prioritize cybersecurity resources toward the areas where they will deliver the greatest enterprise benefits
- Simplify the cybersecurity process by reducing the attack surface of vulnerable systems
- It is not cost-effective or practical to deliver “perfect” security to every part of the enterprise.
- Different parts of the enterprise require different levels of protections and different preventive, detective, forensic, and audit controls.
- The security infrastructure requires the greatest level of protection so it can successfully protect the rest of the enterpr ise.
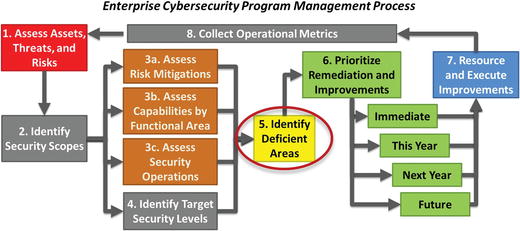
Step 5: Identify Deficient Areas
- Step 5 identifies which ar eas are deficient and require improvements when compared to the target.
- The target security level for the security scope may be too high or too low.
- If additional security capabilities might be necessary, after considering the associated costs and potential operational trade-offs.
- If a different security scope is required, the evaluation can be reconsidered.
- Some functional areas are likely to stand out as being considerably weaker than other areas.
- Weaker areas should be prioritized for improvements first since cybersecurity gaps are the most likely to be exploited by potential attacker s.
- After the most deficient functional areas are addressed, the next improvement phase involves bringing all areas up to the target level of security.
- This phase often involves a comprehensive effort to improve risk mitigations, security capabilities, and security operations.
- At this point, the enterprise should understand its “as-is” cybersecurity posture.
Step 6: Prioritize Remediation and Improvements
- Step 6 prioritizes remediati on and improvement efforts and is influenced b y the following factors:
- Bringing deficient functional areas up to target levels of security
- Implementing improvements that rely on other improvements as prerequisites
- Availability and skill levels of available staff and contractors
- Cost of improvements
- The goal relies on the enterprise
- addressing deficient enterprise cybersecurity functional areas first; and
- working on bringing all functional areas up to the target cybersecurity level in a balanced manner.
- Improvements can be grouped into categories.
- Immediate improvements that can be done immediately using readily available staff and budget
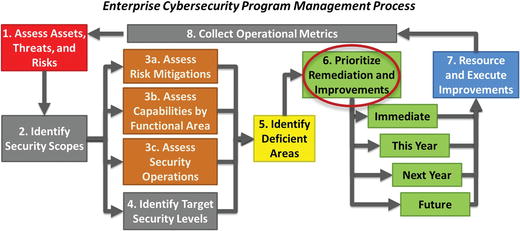
- This-year improvements that can be done within the current year using resources that are obtainable in the year or after minor prerequisites or other dependencies have been addressed
- Next-year improvements that should be done next year, after completing the immediate and this-year projects, and obtaining budgets, approvals, or satisfying other prerequisites
- Future improvements that are a lower priority or will require obtaining budget, hiring staff, and so on
- Improvements can be further prioritized and subgrouped.
- At the highest level, the groupings are helpful to start aligning cybersecurity priorities with business financial cycles so that work can be resourced and executed.
- Projects and tasks will move around on the priority lists.
- Having a “big picture” story to tell leadership is important.
- Where the enterprise is
- Where it is going
- How it is going to get there
- Business leadership wants to understand that such prioritized improvements are not just spending money.
- Maintaining the cybersecurity strategy grouped into these categories simply makes it easier for security to manage and explain its priorities and plans to enterprise leadership.
Step 7: Resource and Execute Improvements
- Step 7 involves the followin g tasks that are conducted in parallel against each category grouping of improvements:
- For immediate improvements, cybersecurity leadership directs the work and supervises its progress.
- For this-year improvements, cybersecurity leadership works on lining up resources, shuffling priorities, or completing prerequisites so that the actual improvement can start work within the current year.
- For next and future improvements, cybersecurity leadership starts framing project plans and resource requirements so that they can be considered and budgeted in future fiscal years.
- Many times, improvements are pushed back because they are too big or expensiv e to execute in a foreseeable timeframe.
- It is helpful to break such improvements into smaller pieces.
- Alternatively, it may help to link such improvements to other business needs to garner support from multiple departments.
Step 8: Collect Operational Metrics
- Step 8 collects metric s as the enterprise executes it improvements and operates it security program.
- Metrics
- Span all functional areas
- Give particular attention to metrics measuring the signs of security incidents and near-incidents, or indicators of attacker activities indicating the presence of anticipated threats
- Give enterprise leadership visibility into the following:
- What threats are
- Where threats are coming from
- What can result if threats are not stopped
- Even relatively crude metrics like “The enterprise was scanned a million times last month,” can be useful if metrics are tracked and trended over tim e.
- Metrics are used in a variety of ways.3
- 1.how external frameworks influence the selection of security scopes and controls for Threat, Assessment, and Validation audits.
- 1.
- In this study guide, “metric” means the following:
- A standard or unit of measurement or formula used to quantify something, and/or
- The values the standard or formula may assume
- Metrics are expressed in terms that make sense to the intended audience; otherwise, they may misconstrue results.
- Metrics need to have benchm arks.
Return to Step 1
- After collecting operational metrics, the cybersecurity program management process returns to Step 1 and the cycle repeats.
- Assess ➤ Prioritize ➤ Execute ➤ Operate
- Should iterate multiple times each year
- Updates its threat assessment
- Takes stock of completed security improvements
- Identifies new security improvements to implement
- Lines up future security improvements for execution when resources become available
- As the cycle iterates, se curity projects move through the various priority categories until they are executed.
- Projects get inserted into the categories due to incidents, new threats, or IT projects requiring additional protections.
- Accommodating the day-to-day realities with new projects provides the enterprise a flexible framework for managing its overall cybersecurity program.
- This process provi des the ability to report on immediate activities and the “big picture” strategy at any time.
Assessing Security Status
Context
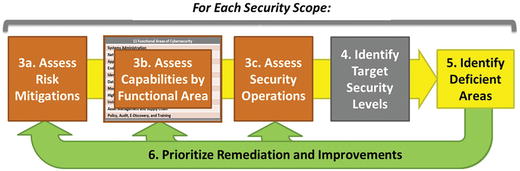
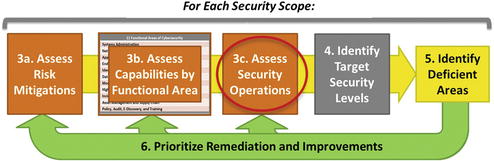
- After Step 1 and Step 2, Step 3 ass esses the overall security posture and status within each scope.
- The graphic depicts the next level of detail for assessing the enterprise’s overall security posture.
- For each security scope, the enterprise
- can consider if it needs to protect primarily confidentiality, integrity, or availability;
- considers the appropriate balance of preventive, detective, forensic, and audit controls to deliver the desired protection; and
- has substantive discussions with business leaders to understand the proper balance of cybersecurity vs. business utility to deliver the most appropriate and cost-effective p rotection.

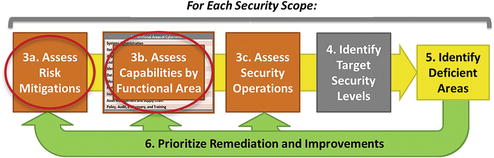
Cybersecurity Program Steps 3a, 3b, and 3c
- Step 3a: Assessing Cybersecurity Risk Mitigations
- What is the effectiveness of risk mitigations within the security scope?
- What are the abilities of the risk mitigations to disrupt the attack sequence of anticipated attacks?
- Step 3a considers
- the attacks to be countered;
- the controls being deployed against the attack sequence; and
- the effectiveness of the resulting mitigations.
- Object Measurement methodology can be used to measure the effectiveness of these mitigations.
- Step 3b: Assessing Cybersecurity Capabilities by Functional Area
- Step 3b assesses the functional areas using Object Measurement methodology to calculate cybersecurity scores.
- Functional area assessment scores are evaluated alongside the risk mitigations and security operations to determine, in part, the enterprise’s overall cybersecurity posture.
- Step 3c: Assessing Security Operations
- Step 3c assesses the 17 security operational processes and the 14 supporting information systems in terms of utilization and effectiveness.
- Information Systems
- Administrator Audit Trail
- Accounts and Permissions
- Password and Key Vault
- Vulnerability Database
- Disaster Recovery Plans
- Incident Records
- Configuration Management Database
- Asset Database
- Security Policies
- Policy Exceptions
- Authority To Operate Records
- Enterprise Risks
- Security Controls
- Security Deficiencies
- Object Measurement methodology can be used to score the processes and/or systems.
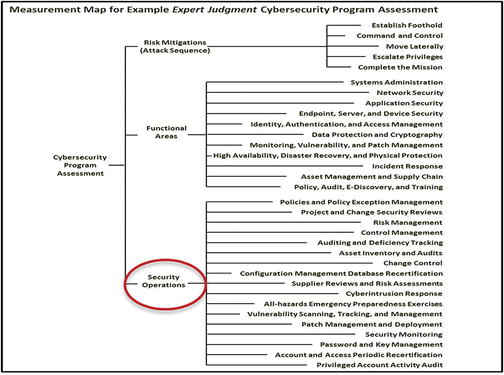
Cybersecurity Program Step 4: Identify Target Security Levels
- Step 4 identifies the target secu rity level for a cybersecurity scope, based on the risk assessment process that considers
- assets, threats, risks to scope, and potential attack sequences; and
- balance between restrictive cybersecurity needs vs. flexible business agility needs to determine security controls.
- The graphic shows the analytical progression from assets to vulnerabilities to threats to treatments, and finally, to controls to mitigate risks (see Chapter 2).
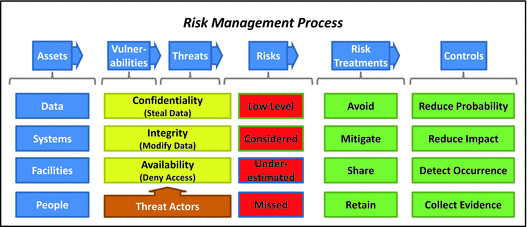
- One output can be a cybersecurity program assessment score that represents the assessed target security level for the security scope.
- Using Object Measurement, the assessed target security level can be represented as a single number (for example, 55%) for the entire scope.
- The graphic depicts one way to visualize this step’s output.
- Risk mitigations (aggregated score)
- 11 functional areas (individual scores)
- Security operations (aggregated score)
- Dotted line represents the target cybersecurity program score at the 80% target security level
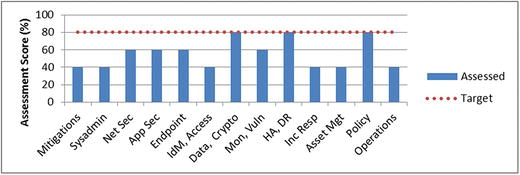
- The graphic also shows which cybersecurity areas are the strongest and weakest.
Cybersecurity Program Step 5: Identify Deficient Areas
- Step 5: Once the scoring is c ompleted and the results plotted or otherwise displayed, the cybersecurity areas that are most deficient should be apparent.
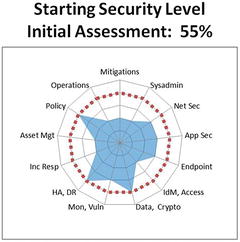
- The graphic shows the following cybersecurity areas standing out as being deficient relative to the overall average cybersecurity level of 55%:
- Risk Mitigations—40%
- Systems Administration—40%
- Identity, Authentication, and Access Management—40%
- Incident Response—40%
- Asset Management—40%
- Security Operations—40%
- The above cybersecurity areas are most likely to be related to security failures leading to successful cyb erattacks.
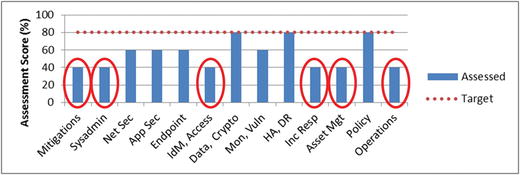
- The fact that risk mitigations and security operations are two of the weaker areas indicates:
- the cyberattack sequences are most likely not disrupted as effectively as they should be; and
- the enterprise’s overall cybersecurity program is likely not being operated with adequate rigor to protect against deliberate or targeted attacks.
Cybersecurity Program Step 6: Prioritize Remediation and Improvements
- Step 6 prioritizes the reme diation and improvement efforts across all scopes.
- The cybersecurity improvements can be performed in two phases.
- First, deficient cybersecurity areas are addressed and brought up to the same cybersecurity level as the other areas.
- Second, all the cybersecurity areas are brought up to the target level together.
- Improve risk mitigations by addressing projected attack sequences
- Improve functional areas by adding security capabilities or improving their utilization
- Improve security operations by implementing operational processes
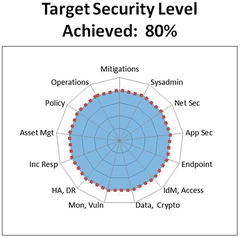
- The overall enterprise c ybersecurity program assessment score would change from 55% to 65%, and then to 80%.
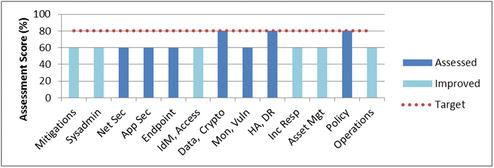
- In the above example, the first phase of improvements brings the most deficient areas up to the same level as the others.
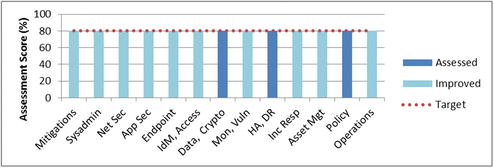
- In the above example, the second phase of improvements brings all cybersecurity areas up to the same target level.
Analyzing Enterprise Cybersecurity Improvements
Context
- Cybersecurity Program Assessment
- Assigns a quantitative measurement to cybersecurity
- Helps with making business decisions regarding the relative value of different types of security investments
- Helps in calculating which improvements will provide the biggest “bang for the buck”
- Provides insight into which cybersecurity improvements will generate the greatest security improvement for the lowest cost
- Projected program assessment score changes / Estimated improvement costs
- Challenges
- Cybersecurity program assessment focuses on the security scope as the basic platform for analyzing security and security capabilities.
- Most enterprises have multiple scopes.
- A single risk mitigation, capability, or operational process may be shared across multiple scopes.
- Consequently, the benefit of security improvements should be considered across multiple scopes as well.
- This section explains the following enterprise cybersecurity improvement topics in more detail, along with some helpful examples:
- Considering Types of Improvements
- Considering Threat Scenarios
- Examining Cybersecurity Assessment Scores across Multiple Scopes
- Considering Improvement Opportunities across Multiple Scopes
- Considering “Bang for the Buck”
Considering Types of Improvements
- In general, security improvements fall into three categories, depending upon the specific security area to be improved.
- Risk mitigations should be the top improvement category if it scores poorly compared to other categories.
- Focus on disrupting, detecting, delaying, and defeating known threats and their attack sequences
- Require certain levels of security capabilities and operational processes
- Security capabilities is the next category for improvement.
- Address unknown threats, unanticipated attacks, defender mistakes, and attackers who use new technologies or innovative approaches
- Security operations is the third c ategory for improvement.
- Required to make risk mitigations and security capabilities work in repelling attacks on an ongoing basis
- Cybersecurity improvements in the above categories improve the enterprise’s cybersecurity posture.
- Calculating which improvements will generate the greatest security improvement for the lowest investment and in the least amount of time helps the enterprise make informed business decisions.
Considering Threat Scenarios
- When thinking through a ttacker scenarios and corresponding risk mitigations, consider red-team exercises and penetration testing.
- These techniques analyze enterprise defenses from the attacker’s perspective to identify gaps in protection and vulnerabilities in defenses.
- Exercises can consider the following threat scenario elements:
- What asset would be endangered (for example, credit card numbers that could be stolen)
- Where the asset resides and when
- Who has access to the asset
- When and how an attacker might access the asset (for example, via the operating system, database, application, or user account levels)
- Attack sequences for attackers to obtain access
- Audit controls to log the access, if the access occurred
- Detective controls to alert the enterprise when such access occurred
- Preventive controls to block such access from occurring
- It is useful to bring in third parties to conduct a red-team review of enterprise scenarios, assumptions, and gaps to identify attack vectors the enterprise never considered.
- Another useful exercise is to have penetration testers actually exercise the scenarios.
- Use the tools and techniques attackers might be expected to use
- Use results to understand how preventive controls should block the attacks and how other controls should detect, log, and search for the attacks
Examining Cybersecurity Assessment Scores Across Multiple Scopes
- Most enterprises have multiple secur ity scores.
- Remember that cybersecurity program assessment scores are calculated within a single security scope.
- This reality adds complexity to the cybersecurity management effort.
- In an enterprise cybersecurity architecture, security scopes represent the following:
- Separately managing the security posture of each scope:
- assets, threats, and risks
- risk mitigations applied to defend against attacks
- cybersecurity capabilities and controls used to deliver risk mitigations
- operational processes used to operate capabilities
- Separately calculating cybersecurity assessment scores and target scores for each scope
- Frequently, there is significant sharing of cybersecurity capabilities across multiple scopes.
- Sharing is OK unless the cybersecurity capabilities allow attackers to exploit them to get from a lower-security scope to a higher-security scope.
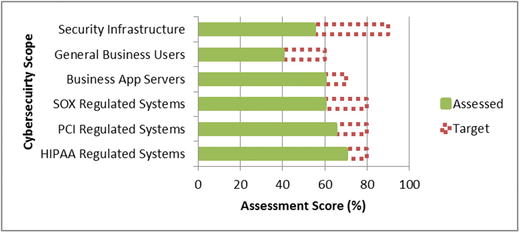
- The graphic depicts one way to visualize enterprise cybersecurity program assessment scores and target scores across multiple scopes.
- Considering the cybersecurity requirements associated with the hypothetical example, the enterprise might have the following six security scopes:
- Security infrastructure t hat protects the data in the other five scopes
- This infrastructure must be hardened to
- resist attack;
- detect breaches or failures of security;
- provide a forensic trail for all security-related activities; and
- be aggressively audited to ensure its ongoing integrity.
- General business users who primarily use e-mail, desktop productivity tools, and web -based business applications for conducting general business
- Business application servers that sup port the enterprise's business operations
- SOX regulated systems that support the business’s reporting of financial results to the publ ic stock markets and are subject to the Sarbanes-Oxley regulations regarding financial reporting integrity
- PCI regulated systems that support the business’ s processing of credit cards and other payment mechanisms and are subject to the regulations of the Payment Card Industry (PCI)
- HIPAA regulated systems that handle m edical and personally identifiable information for the business
Considering Improvement Opportunities Across Multiple Scopes
- When looking at cybersecurity sco res across multiple scopes it is worthwhile to model and visualize the cybersecurity value of potential improvements.
- To assess the value, the enterprise
- calculates its cybersecurity program assessment scores before and after the improvements; and
- determines the amount the assessment scores change between the two assessments.
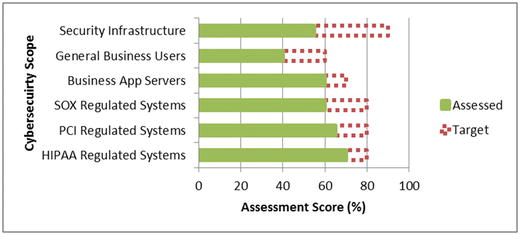
- The graphic provides an example of a before-and-after calculation.
- The proposed improvements impact five of the six security scopes.
- The total improvement value is calculated by adding up its impact across all scopes.
Considering “Bang for the Buck”
- It is important for leadership to make well-informed decisions regarding cybersecurity investments.
- Investments should consider the cost and time involved in deployment and operations compared to the impact the capability will have on the enterprise cybersecurity posture when deployed and operational.
- The challenge is spending thousands or millions of dollars and, at the end of the day, realizing that the huge investment only delivers a single or relatively few cybersecurity capabilities.
- Bottom line: There are no silver cybersecurity bullets and the deployment of one or relatively few capabilities seldom makes the difference between overall cybersecurity success and failure against targeted attackers.
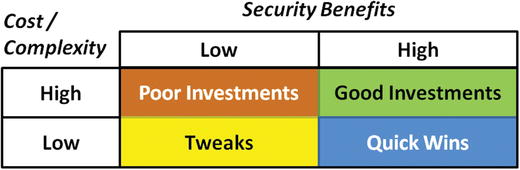
- The graphic depicts a matrix of possible results when considering cost/complexity vs. security benefits.
- This study guide’s enterprise cybersecurity architecture focuses on the value of having many capabilities all working together vs. a single or relatively few capabilities.
- Security strategy should consider the cost and benefit of desired improvements and prioritize quick wins and good investments.
- Lower-value tweaks should be delegated to technical staff and poor investments should be avoided altogether.
- The matrix shows potential improvements falling into four general categories.
- Tweaks have low security benefits, but also low costs. Tweaks can be a time suck for leadership as they distract leadership from the high-value activities and investments, and should be delegated to junior staff.
- Poor investments have high costs, but low security benefits. Unless these investment can be carefully managed to control the cost and ensure the potential benefits, these project should be avoided. In particular, poor investments can be a significant drain on leadership bandwidth, taking attention away from other opportunities with greater security value.
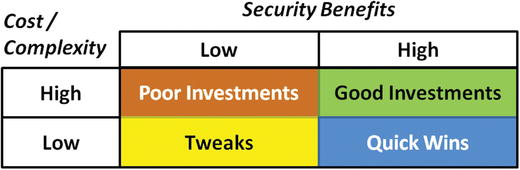
- Quick wins have high security benefits and low cost and complexity. Enterprise leadership should be on the lookout for these opportunities and should give them high priority for implementation.
- Good investments have high security benefits, but also have high cost and complexity. Leadership must carefully consider and manage these investments to ensure they are successful. Making multiple good investments in a single fiscal year may require significant resources.
Prioritizing Improvement Projects
- Cybersecurity improvement projects can be divided into four groups based on when they might take place.
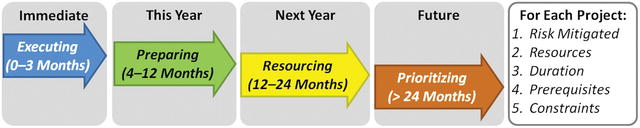
- It is seldom possible or practical for an enterprise to do all improvements at once.
- Improvements can be (1) prioritized based on value and cost, (2) sequenced based on dependencies, (3) resourced from limited available resources, and (4) influenced by internal and external constraints.
- Questions to consider when planning improvement projects:
- What is the risk to be mitigated by the project or its capabilities?
- What is the project going to do to improve the enterprise’s cybersecurity?
- Are the required resources within both the budget and personnel expertise?
- What is the duration of the project? A quarter? A year? Multiple years? Can the project be broken up into phases that are manageable and enable iterative success?
- What are the prerequisites for the project? Dependency on other projects?
- What are the constraints? Regulations? Audits?
- When combined, these four groups and their improvement projects constitute the enterprise’s long-term cybersecurity improvement program and strategy.
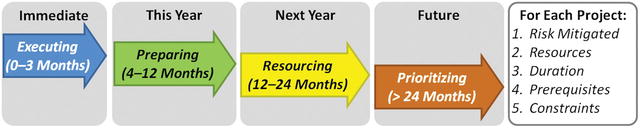
- Immediate: Executin g projects executing now. Generally quick wins at low cost.
- This Year: Preparing pro jects to be completed with the current fiscal year. Low cost, but may require investment. Moved to executing when ready to execute. Preparing includes technical prerequisites, vendor selections, or contract negotiations.
- Next Year: Resourci ng projects are not queued up within the current fiscal year. Focus is on refining plans. May need to execute sooner than originally planned.
- Future: Prioritizing projects do not make sense to execute within current fiscal year and where resources are not available to plan them until the following fiscal year. Competing for priority alongside other business concerns and strategic investments.
- Using cybersecurity assessments and calculated assessment scores, leadership can show quantitatively how the enterprise cybersecurity posture is going to change to help prioritize the projects.
- Over time, cybersecurity projects naturally migrate from one list to another.
- Executing projects are completed.
- Projects planned for this year move to execution.
- As fiscal years transition, what was planned for next year transitions into executing for the current year.
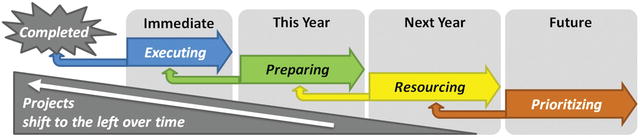
- The graphic above depicts this process of updating the enterprise’s priorities.
- Generally, projects shift to the left, although sometimes shifting business priorities and limited available resources can cause projects to be deferred to later times as well.
Tracking Cybersecurity Project Results
Visualizing Cybersecurity Program Assessment Scores
- Because a program assessment score is a quantitative measurement, it is well suited for managing cybersecurity status over time and visualizing that status graphically to inform leadership decision-making.
- The graphics can visualize the enterprise cybersecurity program via a Kiviat diagram or spider chart format.
- The shape of the filled-in areas reflects nicely the relationship among all the plotted assessment scores.
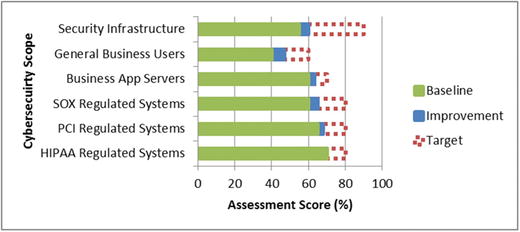
- Initial Assessment = 55%
- Updated Assessment = 65%
- Target Security Level Achieved = 80%


Measuring Cybersecurity Program Assessment Scores Over Time
- Using assessment scores, the security posture for a cybersecurity scope can be reduced to a single number that can be tracked over multiple time periods to show quantitatively the impact of security investments.
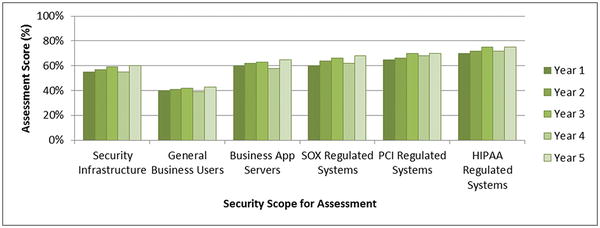
- The above figure depicts the assessment scores for six security scopes over a five-year period and shows trends of the enterprise’s cybersecurity posture over time.
- Security Infrastructure
- General Business Users
- Business Application Servers
- SOX Regulated Systems
- PCI Regulated Systems
- HIPAA Regulated Systems
- Quantitative as sessment methods, security scopes, and visualization techniques provide the enterprise with some of the tools it needs to delegate and manage its enterprise cybersecurity program.
