Overview
- This chapter examines how the cloud is transforming the way businesses everywhere approach building IT solutions.
- Rather than hiring technical staff to build data centers and configure servers, businesses are outsourcing these functions “to the cloud.”
- Businesses are procuring applications, platforms, and computing capacity.
- Cloud enables new levels of business agility.
- Small startups have access to computing and application capabilities that were once considered “supercomputing.”
- Transition to the cloud has its own set of challenges.
- Cybersecurity practitioners still struggle to effectively secure on-premise computers and servers.
- Cybersecurity protection has transformed from one of building high walls into something requiring more nuance and a new type of understanding.
- This chapter describes how an enterprise manages and operates cybersecurity when its computing and applications are in the cloud.
Topics
- Introducing the Cloud
- Cloud Protection Challenges
- Developer Operations (DevOps)
- Developer Security Operations (DevSecOps)
- Scopes and Account Management
- Authentication
- Data Protection and Key Management
- Logging, Monitoring, and Investigations
- Reliability and Disaster Recovery
- Scale and Reliability
- Contracts and Agreements
- Planning Enterprise Cybersecurity for the Cloud
Introducing the Cloud
Context
- NIST provides an industry-recognized definition of “the cloud” in their special publication 800-145.
- NIST also provides a discussion of challenges with cloud environments in their special publication 800-146.
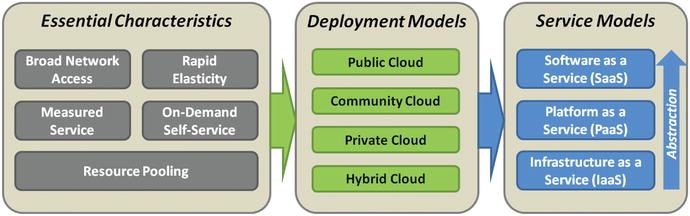
- The graphic depicts a version of the NIST reference model.1
Introducing the Cloud
Five Essential Characteristics
- Broad Network Access
- Means services are delivered via a network—most often the Internet
- Is accessible from a wide range of network-connected devices, such as via a web browser
- Rapid Elasticity
- Means resources and capabilities can be increased or decreased quickly in response to changing demands
- Presents what appears to be almost unlimited capacity to the end user
- Measured Service
- Refers to all aspects of service delivery— including storage, bandwidth, computing capacity, and application activity
- Is measured for reporting and potential charge-back to both the provider and the customer
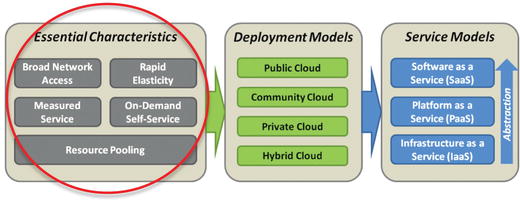
- On-Demand Self-Service
- Means the customer of the cloud service can unilaterally provision capabilities and capacity without requiring significant human interaction or coordination
- Resource Pooling
- Means all of these capabilities are delivered from a shared resource pool that supports multiple customers in a multitenant arrangement
- Ensures capabilities are isolated among customers so individual customers only have visibility of resources allocated to them
Deployment Models
- Public Cloud
- Is a cloud solution provided by a service provider for the general public
- Has no restrictions on who may procure and use its services
- Community Cloud
- Is a cloud solution provided for a restricted community of organizations, usually as a shared service or jointly contracted arrangement
- May be provided by a public cloud provider on its public infrastructure, but with certain restrictions on its configuration and authorized users
- Private Cloud
- Is a cloud solution built and operated by a single organization for its exclusive use
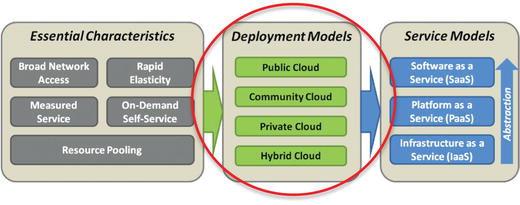
- May locate cloud infrastructure on the organization’s premises, or it may be provided by a third party via some sort of contractual arrangement
- Hybrid Cloud
- Is a combination of two or more of the previous arrangements, bound together using technology or standards so they function as an integrated system
Service Models
- Software as a Service (SaaS)
- SaaS is the highest level of abstraction, where the entire software application—such as sales management, financial system, or database—is delivered “on demand” to the customer over the network from the provider.
- Customers simply accesses the application using a web browser or other network client application.
- Platform as a Service (PaaS)
- PaaS is a lower level of abstraction, where the service provider delivers the underlying computing platform, such as operating systems.
- Customers have full control to install their own applications and data onto the platform.
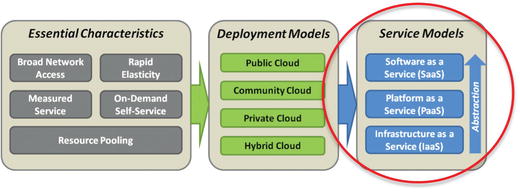
- Infrastructure as a Service (IaaS)
- IaaS is the lowest level of abstraction, where the cloud provider delivers the computing infrastructure—including storage, hardware, and network connectivity.
- Customers have full freedom to install and configure whatever operating systems, application software, and data onto that infrastructure that they please.
Cloud Protection Challenges
Context
- Moving enterprise IT to the cloud may or may not improve cybersecurity compared to operating it in a private network and datacenter.
- Improving cybersecurity with cloud computing depends, in part, on enterprise size and security maturity vs. the cloud provider’s size and security maturity.
- Cloud providers have the same challenges securing their systems that enterprises have.
- Shifting schedules and priorities
- Resource constraints
- Finding and retaining talented security professionals
- Cloud providers have several advantages.
- A consolidated, standardized infrastructure
- Ability to “design once and replicate many” for security solutions
- Simplicity due to standardized offerings and centralized management
High-Level Cybersecurity Considerations
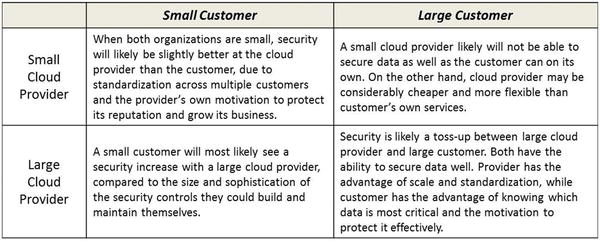
- Small cloud providers have many of the same strengths and challenges as a small business.
- Likewise, large cloud providers have many of the same strengths and challenges as a large business.
- However, large customer enterprises doing business with small cloud providers should be cautious because the business cybersecurity may be better than the cloud provider’s cybersecurity.
- Moving to the cloud presents a number of challenges
- Developer operations (DevOps) and developer security operations (DevSecOps)
- Scopes and account management
- Authentication
- Data protection and key management
- Logging, monitoring, and investigations
- Reliability and disaster recovery
- Scale
- Contracts and agreements
Developer Operations (DevOps) and Developer Security Operations (DevSecOps)
- DevOps and DevSecOps
- DevOps and DevSecOps provide an agile, cloud-based environment for software developers.
- Software developers are responsible for the life cycle of their products.
- Software development ➤ Path to production ➤ Operations
- New IT paradigms dramatically increase the speed and tempo of service updates and fixes to problems.
- DevOps
- DevOps makes server operating systems and system configuration “part of the code” and manages them in the same manner and with the same tools and procedures as the other software DevOps is maintaining.
- Security becomes one more part of the software codebase, and changes to security configurations are coded into the scripts used to build the computing environment and configure the servers.
- DevSecOps
- Cybersecurity becomes more about code and is integrated into systems in a cloud environment.
- Scripts used to build servers
- Scripts used to configure servers
- Scripts used to install applications
- Actual software code running on the applications
- Cybersecurity team members may have to update their skill sets to build scripts.
- This paradigm shift also means cybersecurity team members may have to change their methods of incentivizing developers to comply with security policies.
- Since anyone with a cloud account can stand up a server, install an application, and start running code on the platform, cybersecurity may not be able to use traditional “gates” to review cybersecurity and enforce cybersecurity policies.
- Instead, the cybersecurity team may have to switch to a more passive method:
- Review cybersecurity after the fact and then provide feedback to developers and management on significant cybersecurity deficiencies
- Rather than being a “gatekeeper,” cybersecurity may need to be more of a “scorekeeper,” giving cloud development teams feedback via “security scores” and “penalty flags” so business leaders can identify and consider cybersecurity concerns.
Scopes and Account Management
- Challenge
- In a cloud environment, developers can access the cloud and create hundreds of servers, platforms, or applications quickly.
- If the developer’s credentials are compromised, the same servers, platforms, or application instances can all be compromised or destroyed as equally quickly.
- In a complex environment, questions of scope can become complicated quickly.
- Response
- Use concept of “Blast Radius” to limit the potential compromise caused by a single developer account.
- “Network of Trust” organizes cloud accounts and services so a single compromise cannot bring down the entire enterprise (in other words, “watertight compartments”).
- Compartmentalization may include the following:
- Isolation by a business unit or development team
- Separation of sandbox, development, and production environments
- Separation of primary and alternate sites
- Isolation of high-availability nodes
- By ensuring different people and teams manage different scopes, the enterprise can guard against a single breach or failure being disastrous.
Authentication
- Cloud service is often delivered over an open network, and users and administrators must access the system and services through the network.
- Authentication credentials are the only things protecting their access.
- Enterprise may be only one username and password from the entire service being compromised.
- To protect against this possibility, the enterprise needs the strongest possible protection for administrative accounts, including network-based protections and multistep or multifactor authentication, if such protections are available.
- Another authentication challenge is account life cycle and access management.
- Some cloud providers allow federated authentication to enable users to use their enterprise credentials to access the cloud service.
- Federated authentication can allow the enterprise to manage permissions and access controls from within its enterprise directory.
- Federated authentication can increase cybersecurity risk if enterprise credentials are compromised.
- Balanced solutions may involve using federation in conjunction with strong authentication.
Data Protection and Key Management
- When using a cloud service, data is residing on someone else’s computer in someone else’s facility.
- Protection of data is at the mercy of someone else’s enterprise operational procedures and supply chain.
- Data stored in a cloud provider’s environment needs to be protected.
- Data encryption is possible, but must be carefully designed and deployed.
- Data needs to be encrypted to protect against an attacker, but it needs to be accessible by legitimate users.
- Encryption keys need to be positioned so they are accessible only for legitimate users.
- When customers rely on cloud provider’s encryption, customers need to ask about provider’s key rotation plan and processes for key escrow and recovery.
- When analyzing cloud key management, customers should ask the following questions:
- What cryptographic algorithms and key strengths does the provider support?
- Does the cloud provider have the ability to generate and store cryptographic keys for its customers?
- Does the cloud provider have the ability to use keys provided by the customer?
- What capabilities does the cloud provider have to rotate keys on an automatic or semiautomatic basis?
- What support does the cloud provider have for an enterprise re-key scenario?
- Enterprises must balance their design of key management strategies carefully.
- If keys to the encrypted data are lost, the data is as good as lost.
- Data needs to be protected without being endangered.
Logging, Monitoring, and Investigations
- Logging, monitoring, and investigations have to do with the enterprise’s ability to record, detect, and investigate cybersecurity incidents within its cloud provider services.
- Cloud customers need the ability to investigate cybersecurity incidents within their cloud services.
- Cloud providers need to provide logging, monitoring, and investigation capabilities.
- Potential lack of availability of logs sharply limits the customer’s ability to create detective controls on its cloud services.
- Incident detection and response start with logging of activity in the cloud environment so incidents can be detected.
- Cloud customers should understand what cloud provider logs are available and how those logs record activity.
- Customers should ask questions about key attributes:
- Do logs record all activity in the cloud environment from the cloud provider’s perspective?
- Are activities performed through application programming interfaces logged so customers can match up calls made from their software with activities performed by the cloud provider?
- Do the logs differentiate activities that are performed programmatically through application interfaces from activities that are performed manually through consoles or web interfaces?
- Do the logs differentiate between activities performed on behalf of a server or application and activities performed on behalf of a person?
- Good logging may be an afterthought for cloud providers and is a potential risk customers should consider.
Reliability and Disaster Recovery
- Cloud providers are highly motivated to provide the best possible service.
- Service outages can have dire consequences to provider reputation and business.
- Providers have complex, interconnected systems undergoing constant changes and upgrades and a relatively small number of people manage environment changes.
- Providers are subject to the same challenges of human frailty and fallibility as any organization.
- Providers will make mistakes.
- Cloud providers have the IT challenges of a normal enterprise (people changing roles, hardware failing, software patching and upgrading, and constant pressure to reduce costs and increase revenue).
- Providers manage challenges on their schedule and not their customer’s schedule (quarterly financial closing) and timing can be an issue (North America vs. Europe).
- Provider changes could be problematic for certain customers.
- Providers will not be aware of customer activities, such as quarterly financial closings.
- When the provider has an outage, customers may have little recourse and there may be few provider penalties.
- Cloud contracts may provide little protection or remuneration in the event of service outages.
- Customers need to think about extended outages and provider failures.
- Customers should have solid contingency plans.
Scale and Reliability
- Scale
- Scale is a fundamental factor for cloud services.
- Service consolidation into a cloud provider can be more efficient.
- Bus more efficient than a car.
- Train more efficient than a bus.
- Large-scale systems are less agile than smaller-scale systems.
- Car starts up faster than bus.
- Bus starts up faster than train.
- Scale of provider’s customer base can take cloud provider longer to troubleshoot and repair simple problem because provider is simultaneously solving problem for tens, hundreds, or thousands of customers.
- Reliability
- In general, the provider is more reliable and stable than on-premise enterprise systems.
- When providers fail, they can fail spectacularly.
- Unplanned outages that would result in only an hour of downtime for an enterprise on its own—hardly a business disaster—can result in ten times more downtime for a provider.
- Without considerable contingency capabilities, an enterprise may be down until provider recovers.
- Enterprise cloud architecture should be designed to be resilient.
- Multiple providers at multiple locations
- Unexpected failures handled without losing transactions
Contracts and Agreements
- By using a cloud provider, an enterprise takes technical problems—storage management, network configuration, maintenance—and makes them contractual in nature.
- Providers write contracts to provide desired services while protecting themselves from liability to the greatest extent possible allowed by market and regulations.
- Enterprise needs to ensure contract provides desired features and protections.
- Enterprise needs to have some contingency plans without dependencies on cloud providers.
- Enterprise needs to perform risk assessments and consider contingency, insurance, and disaster recovery options to fill in gaps between enterprise needs and provider services.
- Questions to consider:
- What happens if the cloud provider simply disappeared from the face of the earth?
- Will the cloud provider have all of the enterprise’s customer, financial, or billing information?
- Will the enterprise be able to restore this data from backups to an operational system or to another cloud service provider?
Planning Enterprise Cybersecurity for the Cloud
Systems Administration
How is an enterprise’s cybersecurity program affected by its use of cloud services?
- Systems administrators frequently do their work using regular usernames and passwords, just like ordinary users.
- Secure systems administration may be severely impaired when using cloud services.
- To compensate for this potential situation, there are some actions an enterprise can do to protect its cloud systems administration:
- If available, employ two-factor authentication for privileged accounts.
- If not available, change passwords frequently and review reports of failed logon attempts.
- Use network protection where privileged accounts can only be used from certain IP addresses or address ranges, or via a virtual private network connection.
- Regularly audit privileged account activity logs for unusual patterns or malicious activity.
Network Security
How is an enterprise’s cybersecurity program affected by its use of cloud services?
- Cloud providers often provide basic firewalling or load balancing for systems, but few additional networks security services are offered.
- Provider has own network security infrastructure for protection and detection; it is unusual for customers to get visibility into provider’s network security operations, events, alerts, or logs.
- Limitations may hamper customer’s ability to do investigations requiring analysis of network traffic.
- Customer considerations include
- network isolation for specific enterprise systems;
- the fact that PaaS and IaaS may provide greater security options than SaaS;
- host-based firewalls, intrusion detection/prevention, packet capture, and signature detection; and
- network-based access controls and access to clients in certain countries.
Application Security
How is an enterprise’s cybersecurity program affected by its use of cloud services?
- With SaaS, application-level security configuration is up to the cloud provider.
- With PaaS and IaaS, the customer has the ability to put in place application-level security, which can include extensive detection capabilities.
- Provider will have access to customer’s platform and storage. Customer should maintain tight control over the “path to production” to detect any unauthorized software changes.
- Every aspect of system configuration can become a script managed by the developers (see DevOps).
- Such scripts include network configuration, endpoint security, identify and authentication configuration, and so on.
- Enterprise needs to consider how to manage code, code configuration controls, and software path to production.
Endpoint, Server, and Device Security
How is an enterprise’s cybersecurity program affected by its use of cloud services?
2
- With SaaS, customers do not have control over how cloud provider configures and protects its servers, but customers can ask about protection.
- With PaaS, customers have more ability to configure server security, but options may be limited and lead to certain risks.
- With IaaS, customer security options are almost unlimited regarding hosts and operating systems.
- Major constraint is the fact that the servers reside on the Internet and may be accessible from the customer’s internal network and security services.
- Enterprise can compensate for this situation by connecting cloud systems to the enterprise network via a point-to-point, always-on, virtual private network.
- Such connectivity gives systems access to the enterprise’s internal services (that is, security). Be careful connectivity does not become a backdoor.
Identity, Authentication, and Access Management
How is an enterprise’s cybersecurity program affected by its use of cloud services?
- Public cloud services are connected to the Internet; user accounts are used to connect to these services.
- Protection of the services is primarily through identity, authentication, and access management of the user accounts.
- Multistep or multifactor authentication provides a dramatic increase in security over username and password authentication.
- Federated authentication simplifies authentication and the account management process, but it can add risk if accounts are compromised.
- Another security concern involves identity life cycle and de-provisioning.
- When people leave the organization, who removes their accounts and permissions on cloud services?
- In the absence of an automated process, periodic manual audits should be performed to clean up orphan accounts and excessive permissions.
Data Protection and Cryptography
How is an enterprise’s cybersecurity program affected by its use of cloud services?
- Data protection is critical for cloud services; it is difficult to “get it right.”
- Enterprises need to carefully review the cloud provider.
- Cryptography standards, algorithms, and key strengths to help ensure encryption is not obsolete or inadequate—annual audits required
- Key management: understand where encryption keys are stored, how they are protected, how they are accessed, and how they are rotated
- Hardware Security Module (HSM) services protecting cryptographic keys can be extremely effective at ensuring physical protection of keys, but they require significant expertise to deploy and maintain properly.
- Cryptographic keys need to be backed up to avoid a disaster recovery situation where the enterprise cannot decrypt its data.
- Digital signatures can be used for data integrity (detecting unauthorized changes to logs, transactions, and so on), but not for data confidentiality (stealing data).
Monitoring, Vulnerability, and Patch Management
How is an enterprise’s cybersecurity program affected by its use of cloud services?
- Functional area is largely depends on whether the cloud service is SaaS, PaaS, or IaaS.
- With SaaS, monitoring, vulnerability, and patch management are entirely up to the cloud provider and should be transparent to the customers; customers have few options.
- With PaaS, customers have control over the applications running on the platform; have the ability and responsibility to monitor, scan, and patch the applications to maintain their security.
- With IaaS, customers have full control over system at the operating systems level and above, and they have the ability to monitor, scan, and patch the systems.
- Customers need thorough logs of all activities against the cloud environment (user account, originating system, request interface).
- For monitoring, provider may be able to feed some logs into customer systems for the sake of monitoring and incident response.
- Providers may make application interfaces so customers can connect to cloud service logs programmatically.
High Availability, Disaster Recovery, and Physical Protection
How is an enterprise’s cybersecurity program affected by its use of cloud services?
- Cloud provider determines the physical location and protection of cloud resources.
- Customers may have option to select cloud provider facilities.
- Customers can protect themselves.
- Customers must have a solid disaster recovery plan for worst-case scenario, in which provider disappears and takes their infrastructure, software, applications and data.
- Worst-case scenario plan must include
- recovery point objectives (RPO) (how recently data is backed up); and
- recovery time objectives (RTO) (how long it would take to stand up contingency operations).
- Customers may choose to implement high-availability solutions that span multiple cloud providers.
- Resiliency should be a central tenet to a customer’s cloud solution design.
Incident Response
How is an enterprise’s cybersecurity program affected by its use of cloud services?
- Even with cloud services, there is still a need for an incident response capability.
- Monitoring and investigating cloud services for security incidents can be considerably more difficult than with a traditional network perimeter.
- Detection capabilities should cover the most expected attack scenarios against the cloud service, particularly, stolen credentials and compromised servers; logs should record cloud service activity.
- Enterprise’s Security Operations Center (SOC) should
- have access to cloud service logs; and
- practice common incident scenarios.
- Enterprises should meet periodically with cloud provider to discuss threat scenarios, incidents the provider is seeing, and joint protections.
Asset Management and Supply Chain
How is an enterprise’s cybersecurity program affected by its use of cloud services?
- Cloud services transform a technology challenge—standing up and deploying storage, computing, operating systems, and applications—into a supply chain challenge.
- Challenge involves establishing a contract with a supplier to deliver a service and manage assets associated with service in the context of cybersecurity that mitigates the enterprise’s major risks.
- Enterprise should treat cloud service provider contract as a risk management exercise where cybersecurity risks are considered in terms of the cybersecurity functional areas.
- What protections are provided?
- How do the protections fit into the enterprise’s overall cybersecurity plan? Is there a worst-case disaster recovery plan?
- Enterprise needs to perform cost-benefit analysis on security trade-offs and other related costs associated with breaches.
Policy, Audit, E-Discovery, and Training
How is an enterprise’s cybersecurity program affected by its use of cloud services?
- When using cloud services subject to regulation or external standards, the enterprise should consider the services in the context of those regulations or standards.
- Some services may be better suited for one standard (export control) than another standard (health care).
- An enterprise may need to use more than one provider to satisfy regulatory requirements.
- Cloud services may run afoul of other internal cybersecurity policies such as requirements for strong authentication, network protection, or encryption.
- Careful risk analyses should be performed.
- Analyses may result in policy exceptions or deployment of compensating preventive, detective, forensic, or audit controls.
- Just because a service is being provided by a cloud provider does not remove the service from enterprise’s policies, procedures, or security capabilities.
- Procedures for audits, re-certification, penetration tests, and so forth, apply to cloud services just as they do for internally hosted IT capabilities.
- Enterprise cybersecurity leadership must ensure policies and activities include cloud services.
- Business leaders need to understand how to apply these polices to cloud services.
