© Scott E. Donaldson, Stanley G. Siegel, Chris K. Williams, Abdul Aslam 2018
Scott E. Donaldson, Stanley G. Siegel, Chris K. Williams and Abdul AslamEnterprise Cybersecurity Study Guidehttps://doi.org/10.1007/978-1-4842-3258-3_20Cybersecurity Capability Value Scales
Scott E. Donaldson1 , Stanley G. Siegel2, Chris K. Williams3 and Abdul Aslam3
(1)Falls Church, Virginia, USA
(2)Potomac, Maryland, USA
(3)San Diego, California, USA
Overview
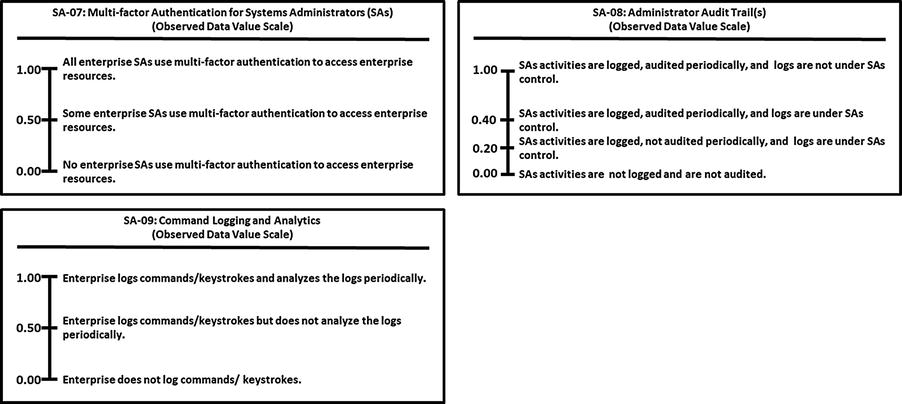
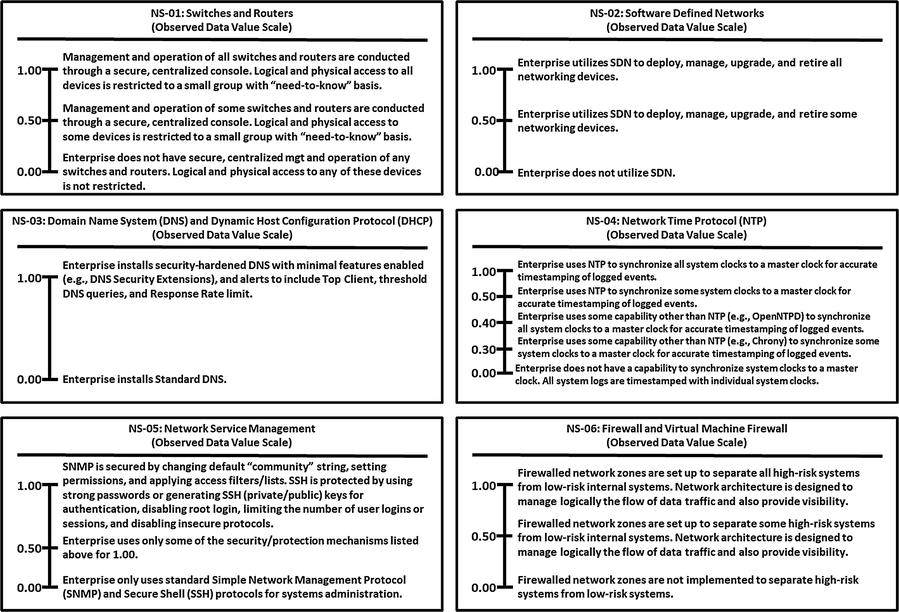
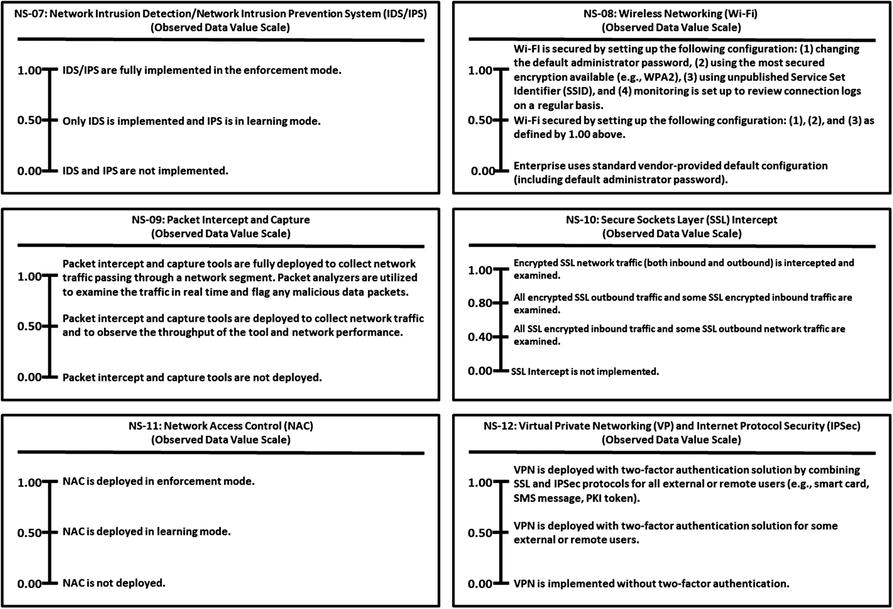
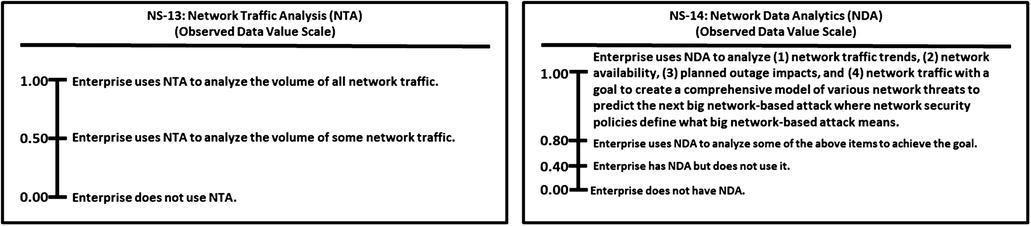
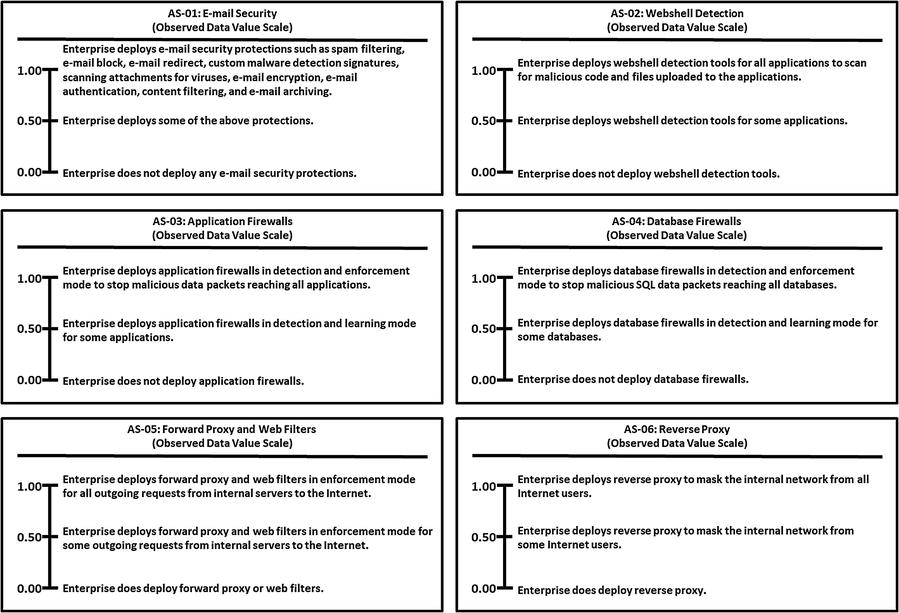
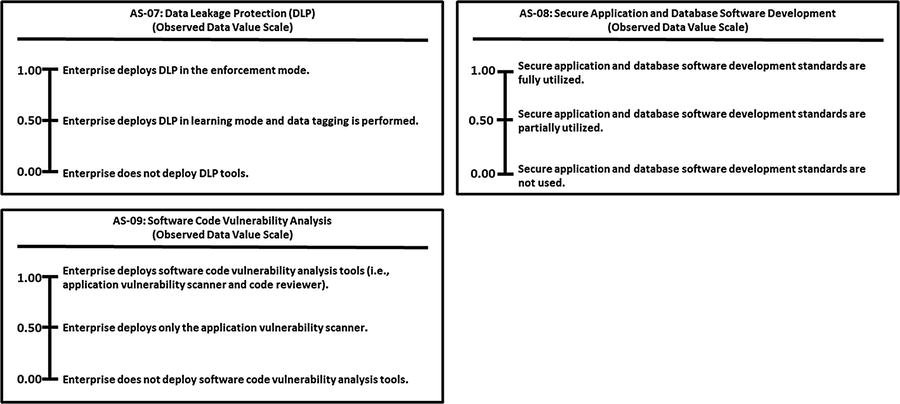
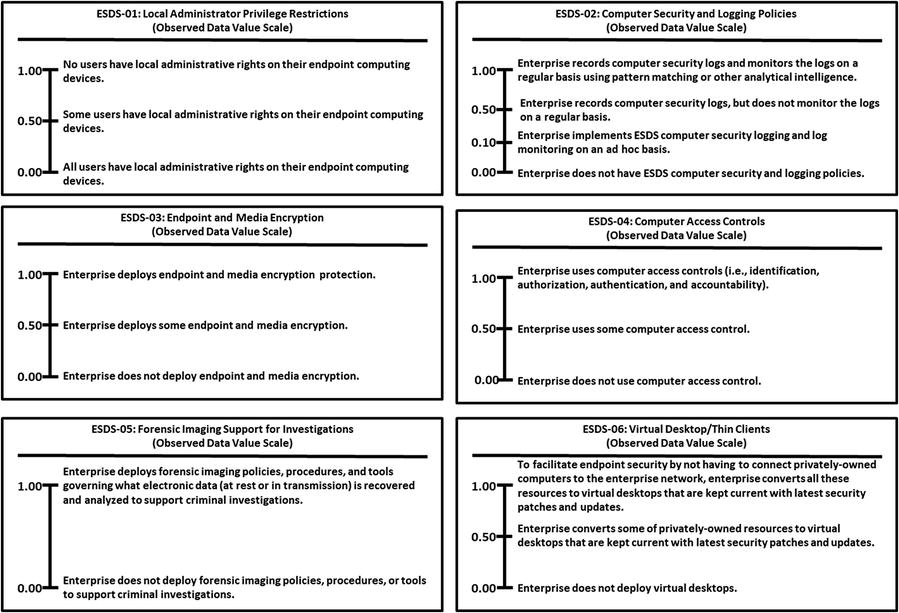
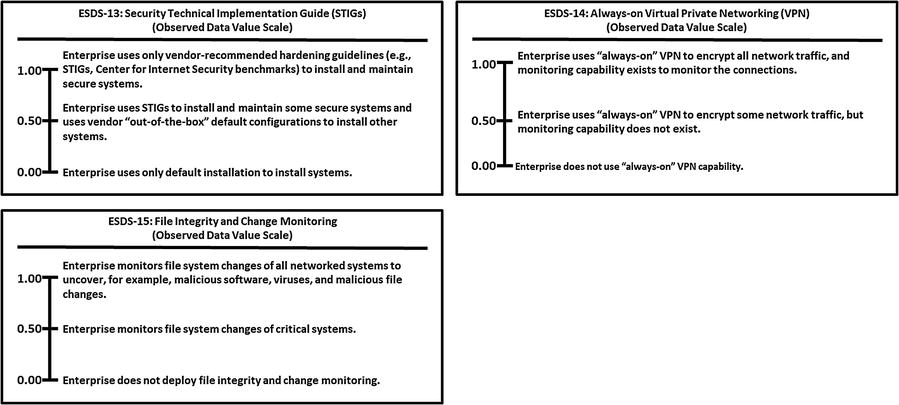
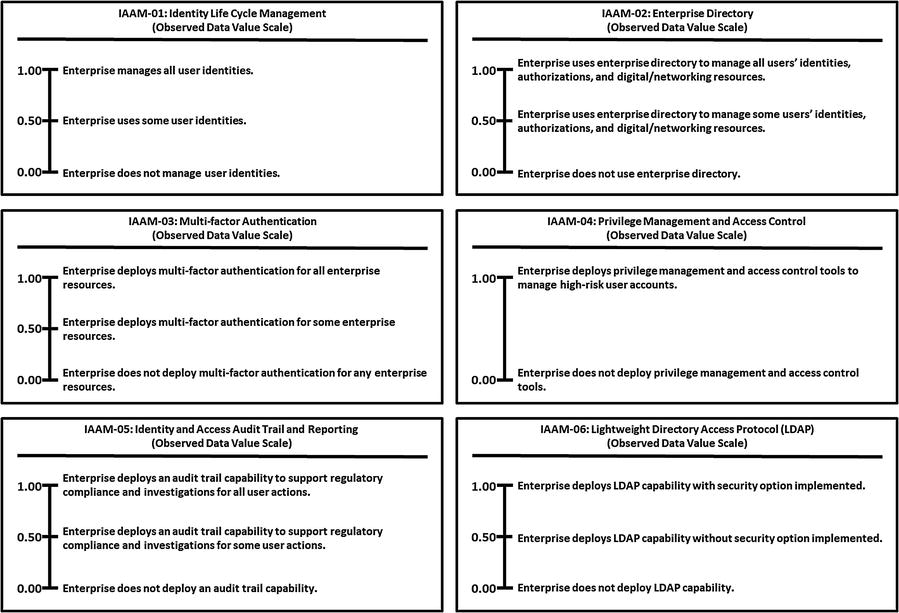
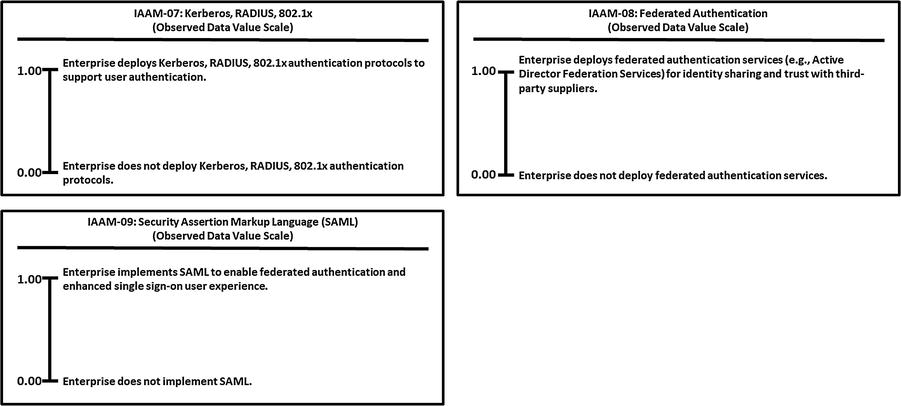
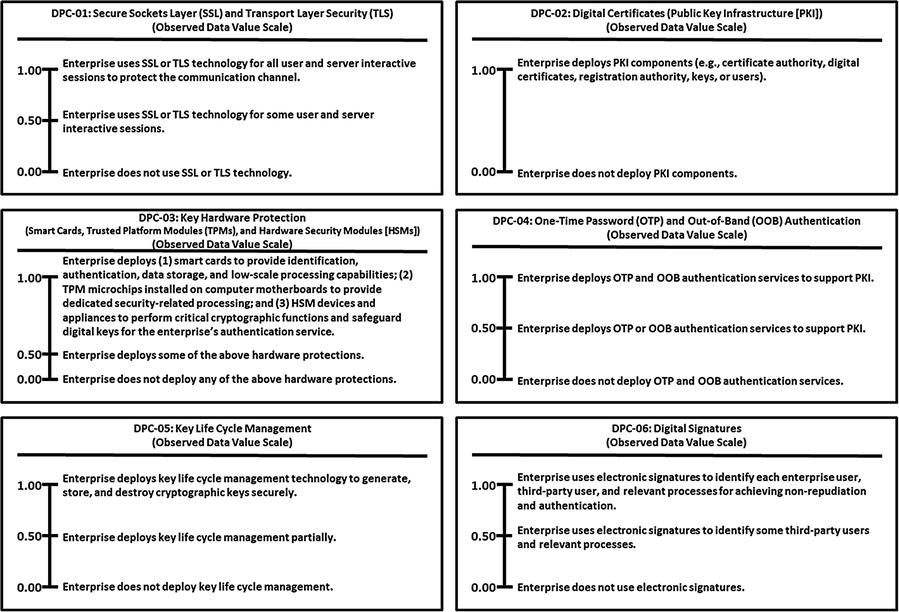
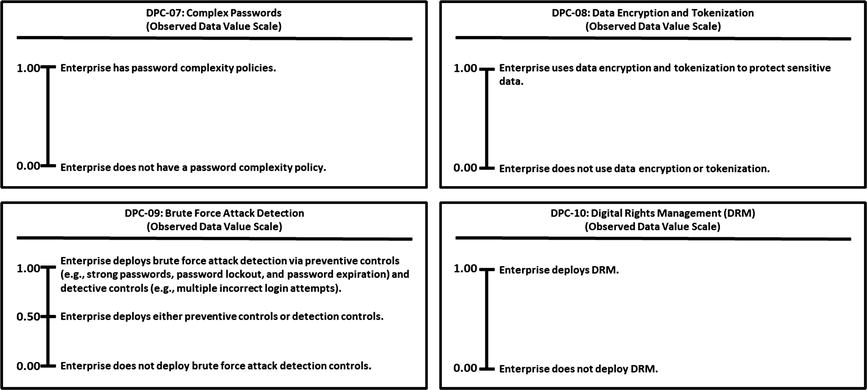
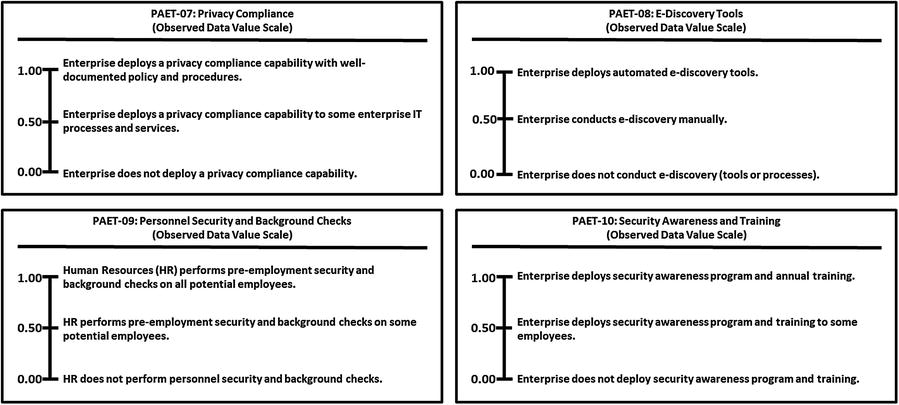
This appendix provides example Object Measurement (OM)
observed data value scale definitions for 113 cybersecurity capabilities.
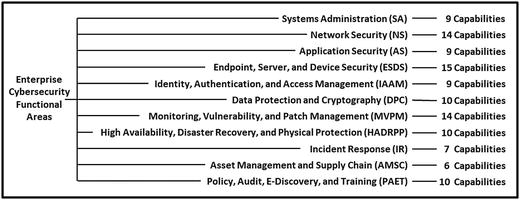
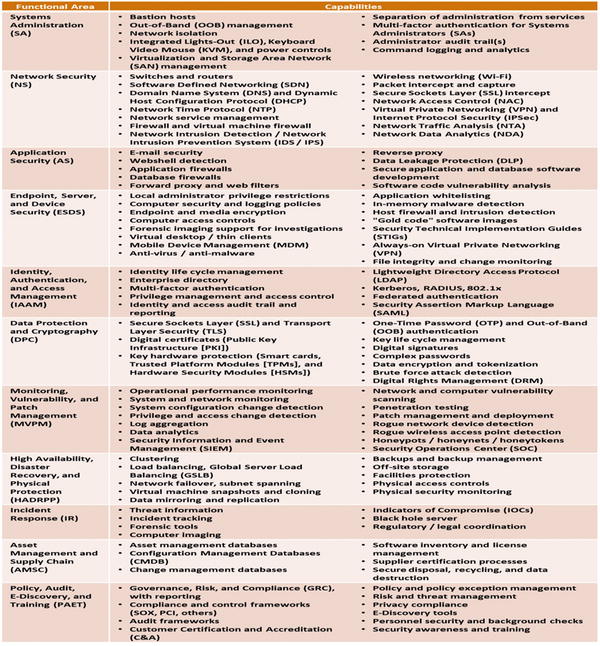
Grouped by 11 functional areas
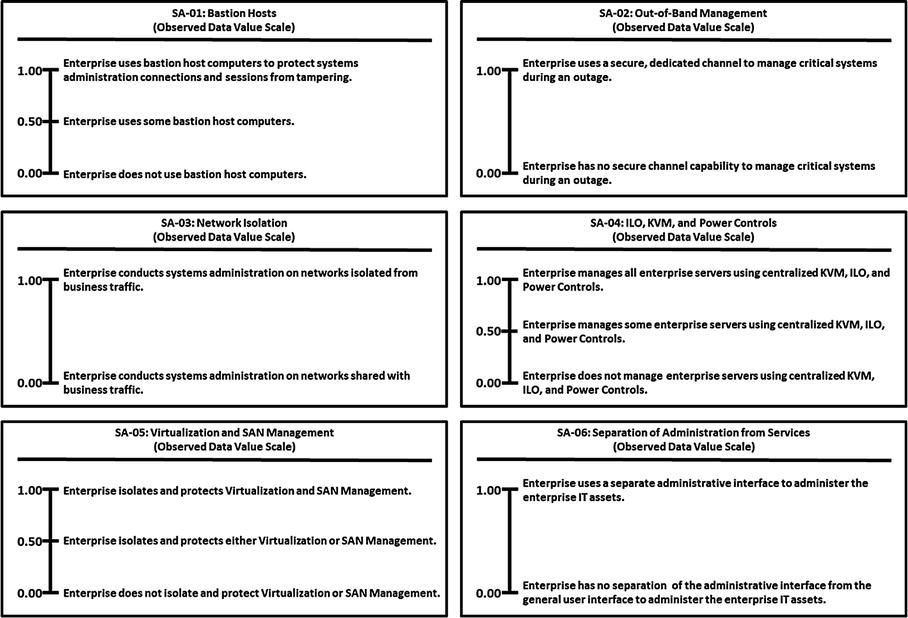
Minimum and maximum numeric values from 0.00 to 1.00, but scales can accommodate any numeric range
Tick marks with plain language descriptions to help associate an enterprise’s vocabulary with measurement activities
No one set of terms (that is, numeric value and tick-mark labels) that defines value scales
In the end, an enterprise needs meaningful measurements.
Meaningful here means “the enterprise uses the measurements, in part, to determine whether and where cybersecurity needs to be improved.”
Topics
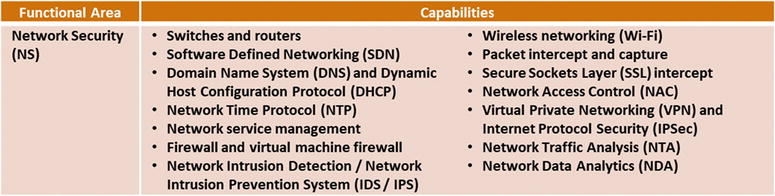
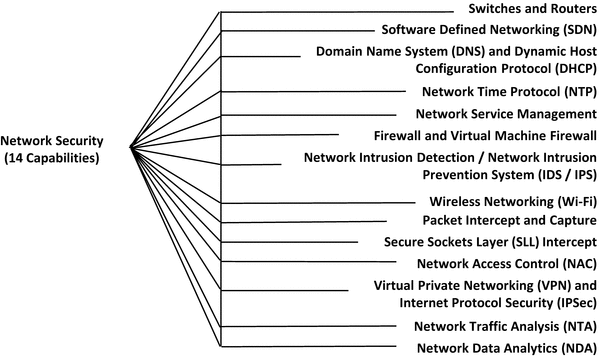
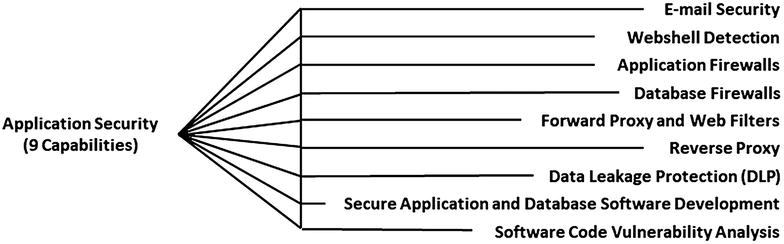
This appendix contains value scales for each of 113 cybersecurity capabilities, grouped into 11 functional areas:
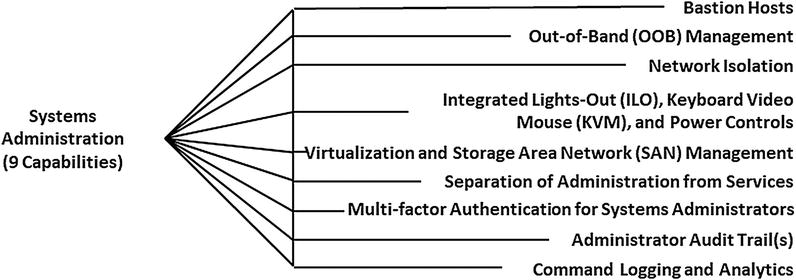
Systems Administration
Network Security
Applications Security
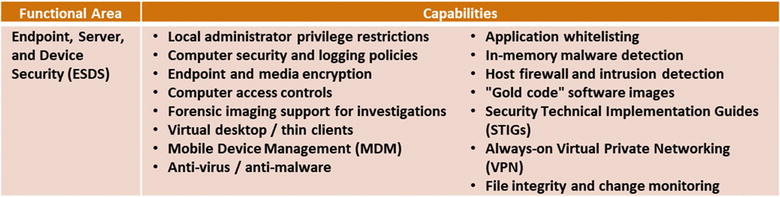
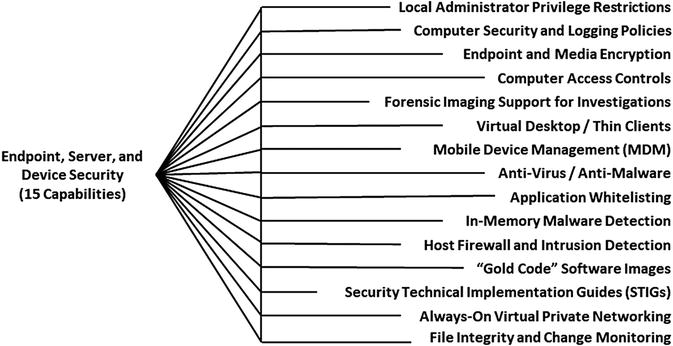
Endpoint, Server, and Device Security
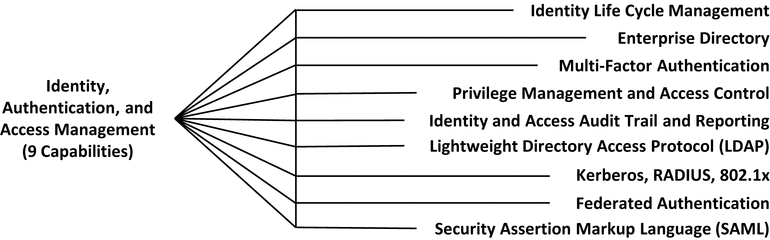
Identity, Authentication, and Access Management
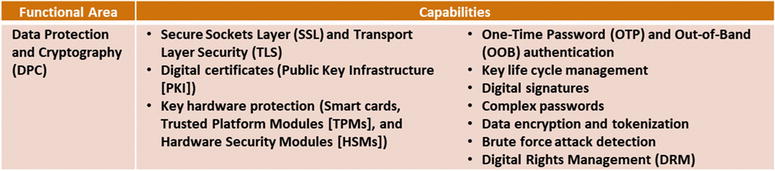
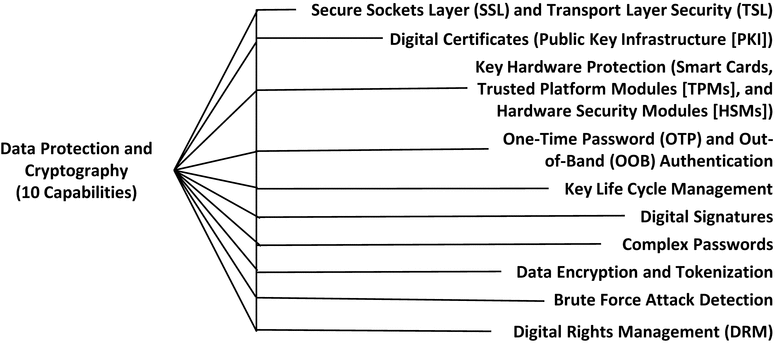
Data Protection and Cryptography
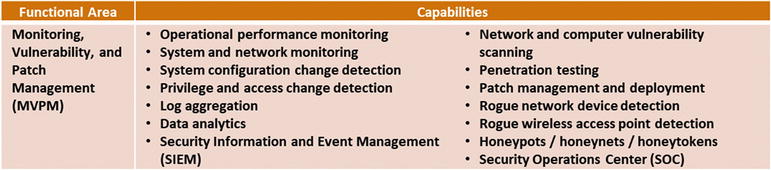
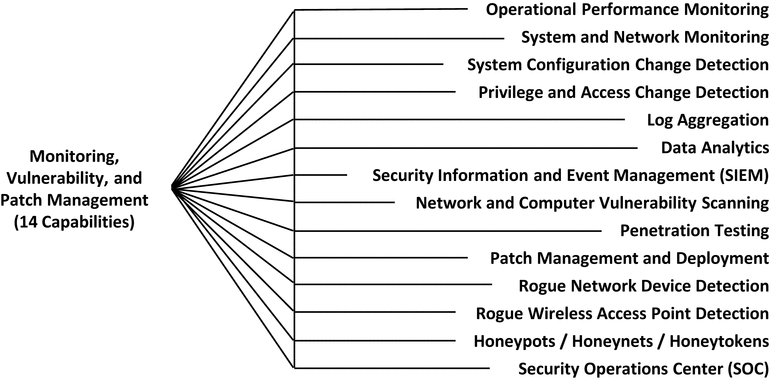
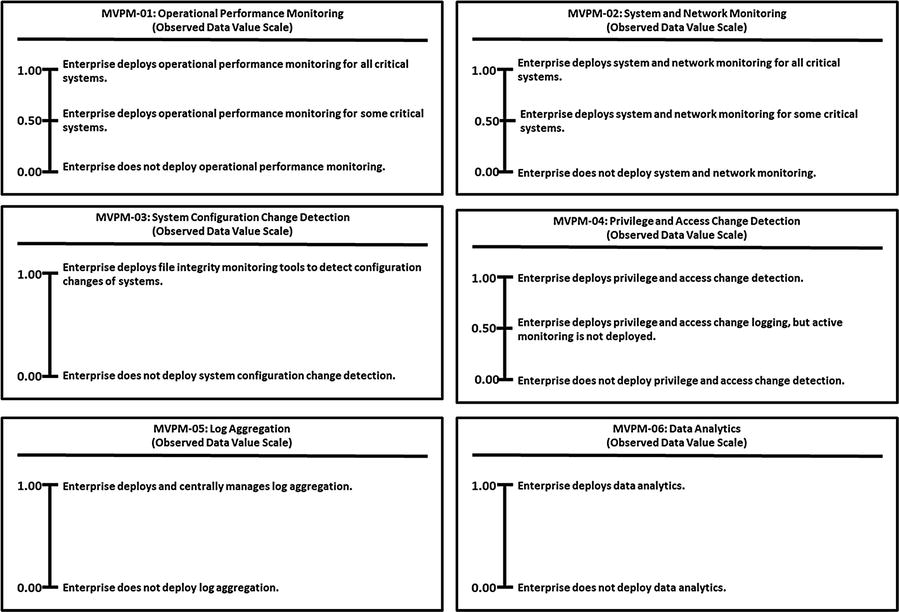
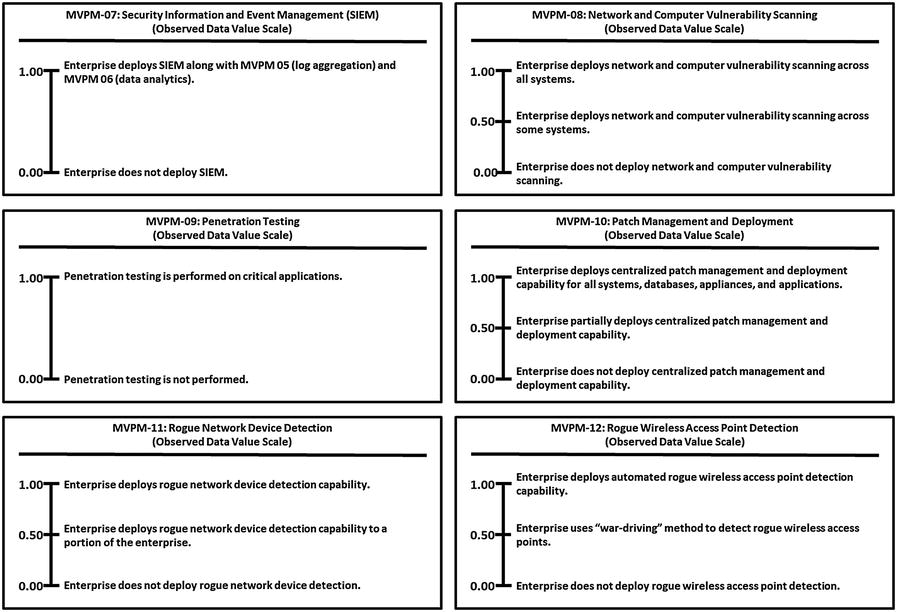
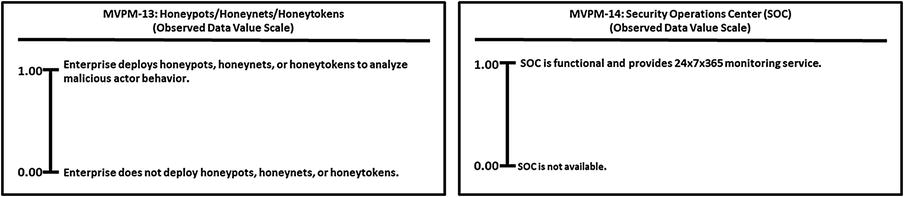
Monitoring, Vulnerability, and Patch Management
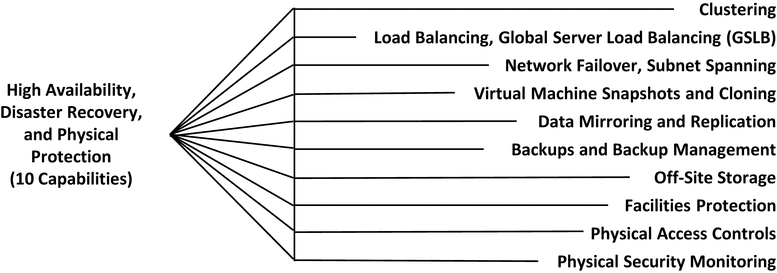
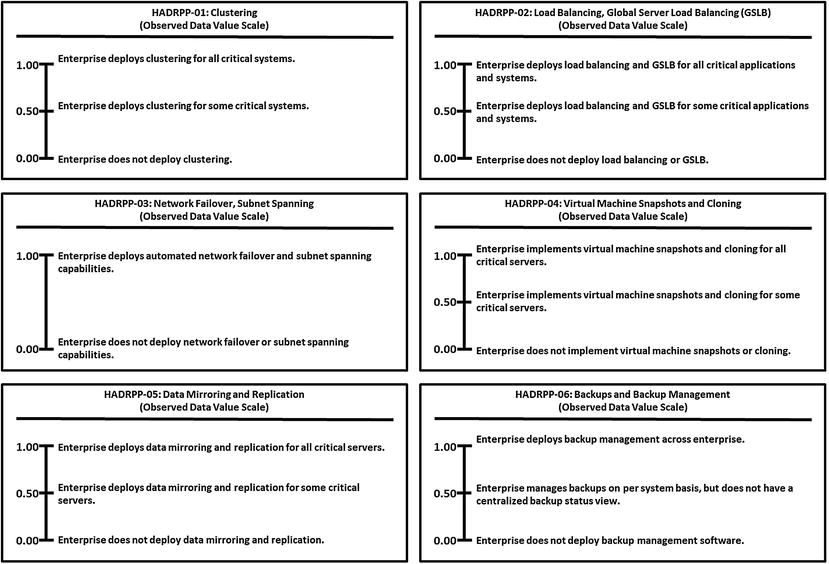
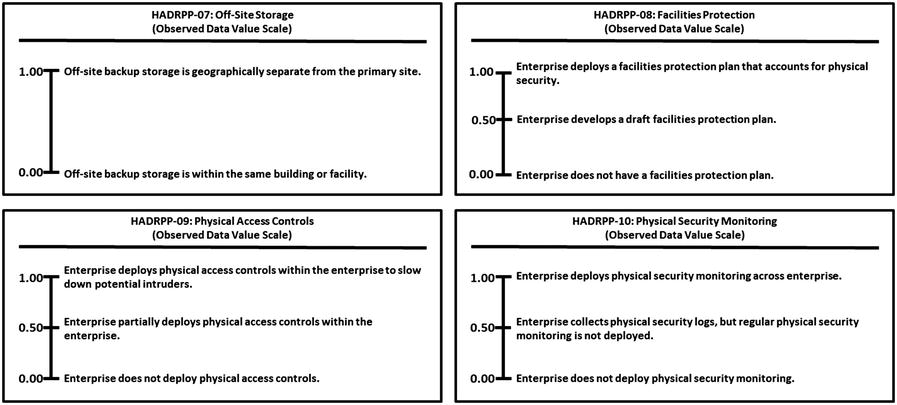
High Availability, Disaster Recovery, and Physical Protection
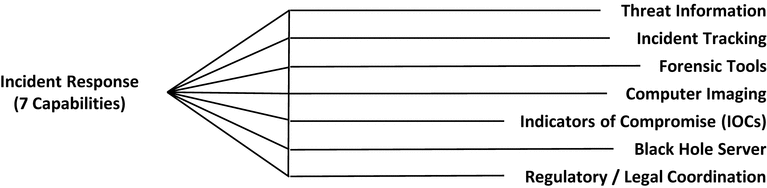
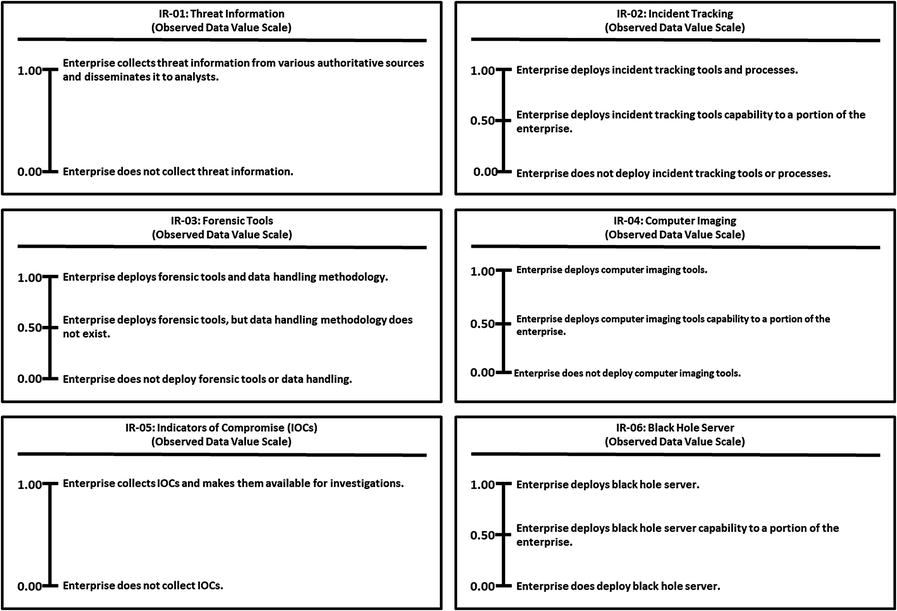
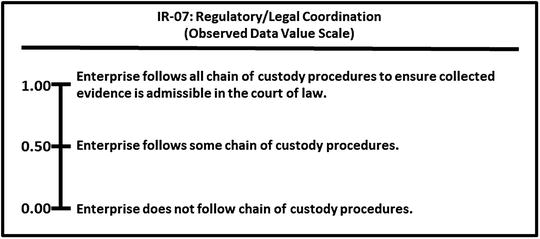
Incident Response
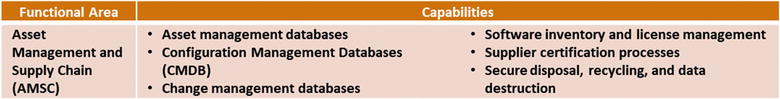
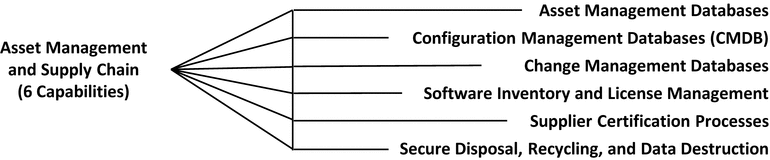
Asset Management and Supply Chain
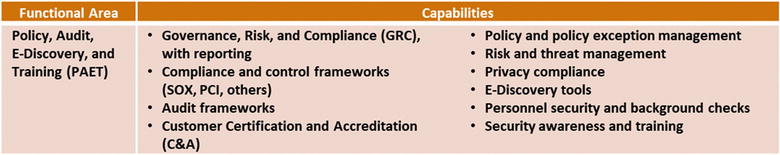
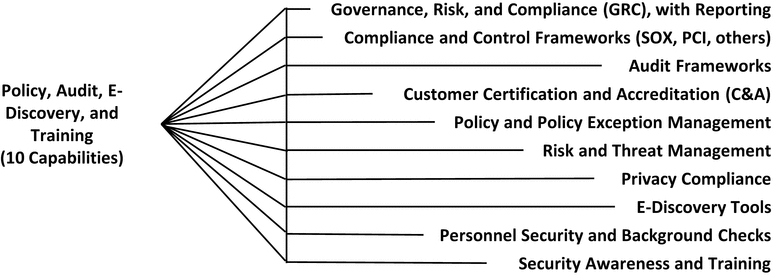
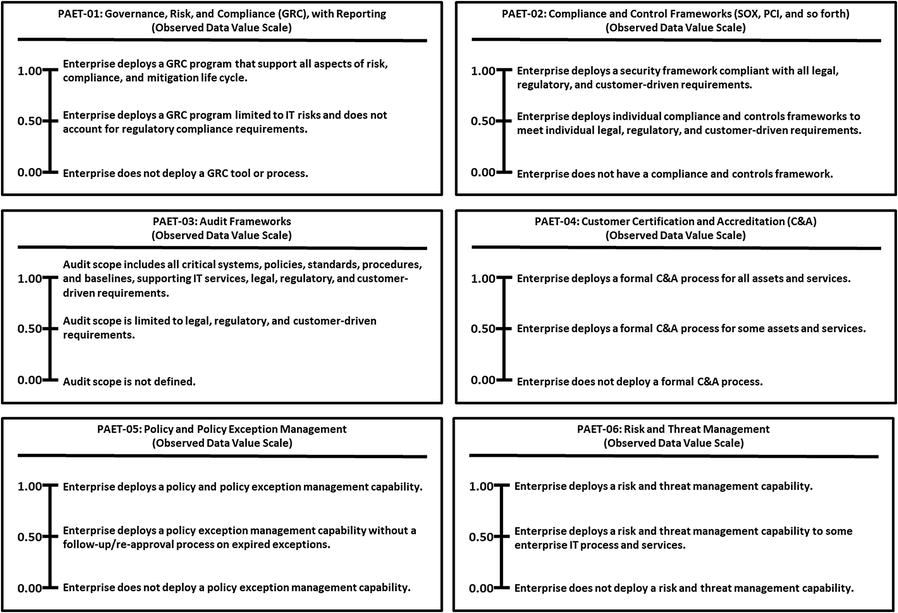
Policy, Audit, E-Discovery, and Training
Endpoint, Server, and Device Security
Identity, Authentication, and Access Management
Data Protection and Cryptography
Monitoring, Vulnerability, and Patch Management
High Availability, Disaster Recovery, and Physical Protection
Asset Management and Supply Chain
Policy, Audit, E-Discovery, and Training (PAET)
..................Content has been hidden....................
You can't read the all page of ebook, please click
here login for view all page.