Context
- Security policies identify the assets to be protected and the protection afforded those assets.
- What is protected
- Who is responsible for the protection
- How well the protection is to be performed
- What the consequences are for protection failure
- Policies should be unambiguous, well organized, well maintained, and balanced between security and business needs.
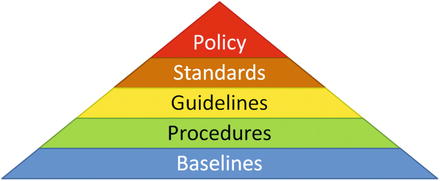
- The graphic depicts the security documentation pyramid.
- Policy is a high-level statement of principle or course of action governing enterprise information security.
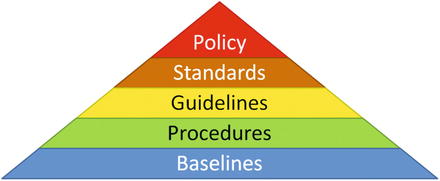
- Standards are documents specifying standards for behavior, processes, configurations, or technologies to be used for enterprise cybersecurity.
- Guidelines are documents providing non-authoritative guidance on policy and standards for use by subordinate organizations.
- Procedures are a set of documents describing step-by-step or detailed instructions for implementing or maintaining security controls.
- Baselines are sp ecific configurations for technologies and systems designed to provide easy compliance with the established policy, standards, guidelines, and procedures.
- This appendix provides an example cybersecurity policy.
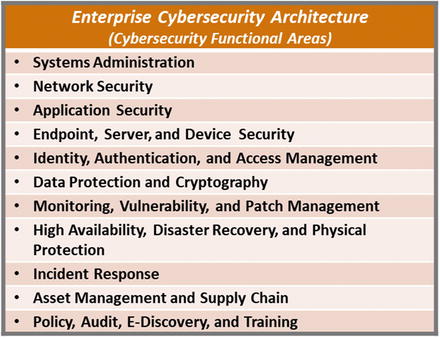
- Can be used as starting point for organizing an enterprise’s policies using enterprise cybersecurity functional areas
- Can be well coordinated with enterprise’s personnel, budgets, technologies, IT life cycle, and cybersecurity assessments
- Do not consider this example policy as the only way to do things or the best way to do things.
- Standards and requirements change over time.
- What makes sense today will change as technologies, standards, and best practices continue to evolve.
- Each enterprise is different and will need to develop and evolve a cybersecurity program that makes sense for the enterprise.
Topics
- The Policy
- Purpose
- Scope and Applicability
- Policy Statement
- Compliance
- Responsibilities
- Chief Information Officer (CIO)
- Chief Information Security Officer (CISO)
- Managers
- Employees
- Contracted third parties, suppliers, temporary employees, and consultants
- Policy Guidance by Functional Area
The Policy
- Purpose
- Delineates security requirements, roles, and responsibilities necessary to protect enterprise data and information from:
- Unauthorized access
- Inappropriate disclosures
- Compromise
- Reviewed and approved by enterprise senior management
- Disseminated to employees and relevant external partners
- The following parties provided input and reviewed content to ensure governing laws, regulations, and enterprise policies are appropriately incorporated
- Chief Information Officer (CIO)
- Chief Information Security Officer (CISO)
- Chief Human Resources Officer (CHRO)
- Defined in the context of the ownership of the enterprise (public vs. private) and legal regulatory requirements while taking into account industry security best practices
- Scope and Applicability
- Applicable to a ll employees, temporary employees, contractors, and enterprise subsidiaries
- Must be used to assess third-party suppliers who sign a contract to provide business services to the enterprise
- Must be used to assess the risk of conducting business
- Reviewed and adjusted as needed on a periodic basis
- Policy Statement
- Compil es with all legal, regulatory, and contractual obligations regarding protection of enterprise data
- Provides the authority to design, implement, and maintain security controls meeting enterprise standards
- Ensures enterprise employees comply with the policy and undergo periodic training
- Informs employees that the enterprise monitors employee usage of information systems
- Requires enterprise data be stored and manipulated on enterprise-provided information systems or contracted systems that comply with this policy
- Implements a security incident reporting mechanism
- Compliance
- Lapses or failu res may result in disciplinary action, such as removal or limiting access to systems, termination of employment, an so on.
- Lack of compliance could have legal or regulatory ramifications with regard to federal, state, local, or international law.
- Compliance is enforced through executing periodic assessments by enterprise security, internal / external audits, or self-assessments.
- Responsibilities
- Chief Information Officer (CIO)
- Provides governance for enterprise IT systems and information with respect to security compliance with this policy
- Publishes a common operating environment (COE) that defines infrastructure standards incorporating security policies
- Reviews and approves any low-risk COE deviations or exceptions
- Provides guidelines for on-and-off-network information systems with respect to maintaining an information security plan
- Chief Information Security Officer (CISO)
- Acts as primary custodian of the information security risk assessment process
- Reports identified risk to the enterprise risk committee and other key stakeholders
- Keeps the enterprise security policy and procedures current for both digital and physical assets
- Ensures identified system vulnerabilities are mitigated in a timely manner
- Publishes up-to-date security standards
- Acts as the incident lead during an active incident
- Is responsible for submitting an incident root-cause report to management
- Enforces compliance with enterprise security policies by conducting periodic security checks and audits
- Oversees internal and external reporting requirements (SOX, SEC, incidents, HIPAA)
- Interfac es with the legal department to support e-discovery
- Implements security awareness and training campaigns
- Supports due diligence process for vetting security quality of suppliers, products, and subsidiaries during mergers and acquisitions
- Managers
- Ensure compliance with enterprise’s security policies by incorporating security into the IT lifecycle process.
- Ensure employee security training is completed
- Follow established incident reporting and escalation procedures
- Periodically update standard operating procedures (SOPs) to ensure compliance with enterprise policy and procedures
- Employees
- Comply with enterprise security policy and procedures
- Complete required security training
- Follow established incident reporting and escalation procedures
- Take reasonable care to protect their enterprise-provided equipment and access credentials
- Contracted third parties, suppliers, temporary employees, and consultants
- Must demonstrate they can meet and perform per enterprise policy and procedures
- Provide the enterprise with required third-party audit reports as part of due care
Policy Guidance by Functional Area
Systems Administration
- Provides management and administration of enterprise IT and cybersecurity systems.
- If malicious actors compromise systems administration, they have access to enterprise data and information systems.
- Activities must include the following:
- All systems administration activities at the application, data, and operating system levels shall require authentication, and all logons to these systems shall be logged for audit.
- Systems administration protocols that are insecure or vulnerable to attack, including critical infrastructure of storage, computing, and data center management, shall only be used on isolated networks.
- Systems Administrator
- Accounts shall require multi-factor authentication before administrative access is granted.
- Activities shall be monitored for signs of inappropriate activity.
- Logons shall be recorded and audited periodically (for example, weekly).
- Access control lists shall be verified periodically (for example, quarterly) to ensure least privilege and separation of duties.
- Changes to access control lists shall be recorded and audited periodically (for example, weekly).
- Security configurations shall be reviewed on a periodic basis (for example, annually), including re-validation of all policy exceptions.
- Systems administration’s preventive, detective, audit, and forensic controls shall be verified and tested for proper operation periodically (for example, at least annually).
Network Security
- Network security pro tects enterprise data and information from internal and external malicious actors.
- Activities must include the following:
- Network and network security infrastructure, including routers, switches, and firewalls, shall be centrally managed; logons shall be logged for audit.
- Network infrastructure administration activities shall be isolated from general business network traffic.
- All administrative logons shall require credentials and multi-factor authentication.
- Networks
- Publicly accessed or not physically protected, networks, such as wireless networks, shall use access control to ensure only authorized users are permitted access.
- Networks shall have measures in place to detect and block network traffic known to be malicious via protocols, payloads, sources, or destinations.
- Access to
- enterprise networks from the Internet shall require multi-factor authentication; and
- privileged internal networks directly from the Internet shall not be permitted.
- Network traffic
- known to be malicious, either through automated or manual means, shall be blocked within a defined period, such as one business day of detection;
- thought to be questionable and may be indicative of attacks shall be recorded and retained for a defined period of time (for example, 90 days) to permit analysis and investigation; and
- known to be secure shall not be excluded from analysis to identify and block malicious activity.
- Network
- Infrastructure shall provide for basic services, such as host configuration, that shall be hardened to protect them from attack or compromise.
- Configuration changes shall require approval and shall be logged for audit and investigation, as required.
- Security configurations shall be reviewed on a periodic basis (for example, annually).
- All network policy configurations and exceptions shall be re-validated periodically (for example, annually).
- Network security’s preventive, detective, audit, and forensic controls shall be verified and tested for proper operation periodically (for example, annually).
Application Security
- Application security pro tects enterprise application systems from external and internal attacks and vulnerabilities.
- Activities must include the following:
- Internet-facing application servers shall be protected from unauthorized configuration changes.
- Configuration changes shall be logged and audited to catch the introduction of unauthorized “backdoors” into application systems.
- Critical enterprise applications such as e-mail, voicemail, and web services must be configured to prevent and detect attacks and exploits of vulnerabilities.
- For attacks and exploits that are not prevented or detected, adequate forensic logs much be maintained to permit audit and investigation after the fact.
- Communication between application components shall require authentication and shall be performed using secure protocols when performed over networks.
- Applications sens itive to
- confidentiality concerns—processing data sensitive to breach—shall employ protection and detection to protect against data leakage;
- integrity concerns—potential data changes with financial or other repercussions—shall employ data integrity protections such as digital signature and data modification audit trails; and
- availability concerns shall employ high availability and rapid disaster recovery to protect them from internal or external denial of service attacks.
- Applications
- using custom source code shall be analyzed using static code analysis periodically (for example, at least quarterly), and all medium and higher vulnerabilities shall be addressed and remediated;
- that are generally available on the Internet or internal networks shall be scanned for vulnerabilities periodically (for example, at least monthly), and all medium and higher vulnerabilities shall be addressed and remediated (for ex ample, 90 days); and
- found to be in violation of policy may be temporarily or permanently disconnected from Internet or enterprise network until remediated.
Endpoint, Server, and Device Security
- This functional area hard ens and secures endpoints such as desktops, laptops, mobile devices, and servers using standard vendor-recommended security guides and builds.
- Activities must include the following:
- Local administrator account passwords or keys shall be unique to each endpoint.
- Enterprise endpoints shall be configured from master images that are configuration-controlled and protected from tampering, changes, or the introduction of authorized or malicious code.
- Network-connected endpoint systems shall be configured to forward security logs—including administrator logon and security component configurations—to a central infrastructure for logging and correlation.
- All portable and removeable endpoints shall have their built-in and removable media encrypted.
- Personal computes and mobile devices, when used for enterprise work, must include the ability to remotely delete enterprise data from the system in the event of compromise.
- Security infrastruct ure endpoints shall include the ability to detect and alert on changes to security configuration files within a set time (for example, 1 hour).
- Endpoint systems
- shall be configured for investigation of cyberincidents by installing forensic tools and configuration security logs to meet incident investigators’ requirements;
- shall be configured according to vendor-approved security guidelines for secure operating system installation and operation;
- shall include endpoint protection to block and detect malicious software and network connectivity as appropriate for system security; and
- that are involved in operating or managing cybersecurity functions for the enterprise shall have application whitelisting installed and configured for maximum restrictiveness.
- Servers directly connected to the Internet shall be scanned for operating system vulnerabilities using a credentialed vulnerability scanner periodically (for example, monthly) and remediated according to policy (for example, 30 days).
- Endpoints found to be in violation of policy may be temporarily or permanently dis connected from the enterprise network until the violation is remediated.
- Endpoint server and device security configurations shall be reviewed on periodic basis (for example, annually).
- …
Identity, Authentication, and Access Management
- Access to enterprise sy stems shall require unique network identities and authentication to systems shall use approved means.
- Such access shall provide for unique identification of the users and non-repudiation of their activities.
- Accesses to data and systems shall be configured on an as-required basis according to need-to-know.
- Accesses and online identities that are no longer required shall be removed on a timely basis.
- Activities must include the following:
- All production enterprise systems shall use centralized identity provisioning and de-provisioning, and centralized access management where possible.
- Cloud-based systems and Software-as-a-Service (SaaS) solutions used by the enterprise are subject to this policy as well as on-premise systems.
- Identity systems
- shall be protected at the same or greater level as the sensitivity of the enterprise application that they serve;
- shall alert on suspected attacker activities, including using privileged account s on non-privileged systems and patterns of excessive logons or logon attempts that may be malicious;
- shall provide protective, detective, audit, and forensic controls governing all administrative changes to the identity system and identity life cycle actions—including account provisioning, de-provisioning, and changes—and permission provisioning, de-provisioning, and changes; and
- shall support the protocols required for authentication and access control on enterprise on-premise and cloud-based systems, such as Kerberos, RADIUS, LDAP, X.509 certificates, and SAML.
- Electronic identities and permissions
- held by non-employees shall be sponsored by at least one employee and re-certified periodically (for example, 90 days).
- Electronic identities and permissions used by computer systems (servic e accounts) shall be sponsored by at least one employee and re-certified on a periodic basis, such as 90 days, or be de-provisioned.
- Electronic identities no longer needed shall be de-provisioned with a set time period (for example, 180 days).
- Access permissions no longer needed shall be removed with a set time period (for example, 90 days).
- Multi-factor authentication shall be supported for access to enterprise systems and applications from untrusted networks such as the Internet, and for all uses of privileged systems administrator accounts on all networks.
- Authentication failures shall not reveal information about user names, passwords, permissions, or authentication methods.
- Identity, authentication, and access management security configurations shall be reviewed on a periodic basis (for example, annually).
- Failed logons shall include a delay so no more than five failed logons can be performed within one hour.
- More than ten failed logon attempts on a single account shall generate an alert requiring investigation before the account may be used.
- Security configurations and policy exceptions shall be reviewed periodically (for example, annually).
- Passwords, when they are used for authentication, shall be subject to the following policy requirements:
- Passwords
- should be at least 12 characters long;
- must contain uppercase, lowercase, and a number or a special character;
- should not contain internal repetitions to allow them to meet length requirements (PasswordPassword 1); and
- should not be displayed in clear text during the login process.
- Active user passwords
- must be changed periodically (for example, 90 days) and the past ten passwords must be unique; and
- shall n ot be written down on paper or stored in unencrypted computer files.
- Passwords internal to systems and not used interactively by users must be changed periodically (for example, annually) and the past ten passwords must be unique.
- System account passwords shall be physically protected in a locked safe.
- If stored electronically on network-accessible systems, such storage shall be encrypted and access-controlled.
- If a single electronic system contains more than 100 system passwords, user access to it shall require multi-factor authentication.
- When passwords must be generated and transmitted, such transmission shall be by encrypted means, or given verbally over the telephone.
- Only one-time passwords may be transmitted over insecure channels.
- Password security configuration shall be reviewed on a periodic basis (for example, annually), including re-validation of all policy exceptions.
- Password management preventive, detective, audit, and forensic controls shall be verified and tested for proper operation periodically (for example, annually).
Data Protection and Cryptography
- Data protection and cryptography are essential to achieving
- strong authentication, non-repudiation, and the protection of confidentiality and integrity of data at rest and in transit; and
- protection of enterprise data and identities adequate to resist current and projected attacks.
- Activities must include the following:
- Sensitive data transmission shall be protected—using Secured Sockets Layer (SSL), Transport Layer Security (TLS), Internet Protocol Security (IPSec), or equivalent secure protocols—on internal protected networks and insecure networks such as the Internet.
- Encryption modules, algorithms, and protocols shall meet US National Institute of Standards and Technology (NIST) requirements as documented in approved Federal Information Processing Standards (FIPS) documents.
- Cryptography used for more sensitive operations may need to resist an attacker with $100,000 worth of computing power.
- Password policy shall be set using cryptographic principles based upon the amount of entropy required and the ability of brute-force attacks to be detected or delayed.
- Design password complexity and rotation policy so attackers have less than 1% chance of successfully guessing a password within its usable lifetime.
- Passwords with longer lifetimes shall require commensurately greater complexity to resist brute-force attacks.
- Published cryptographic vulnerabilities (such as Heartbleed) shall be remediated within a set period (for example, 30 days) of publication, or comp ensating preventive or detective controls shall be put place so attempted exploits are blocked or at least detected.
- Encryption keys shall be centrally escrowed and retained for a period of time (for example, seven years) after the date of last use.
- All non-public enterprise data at rest shall be either physically protected in a locked facility or container, or encrypted using cryptographic keys that are separate from the data, such as a strong password or encryption token.
- Data encryption shall include adequate logging separate from the media itself to permit investigators to validate that lost media was, in fact, encrypted at the time of loss.
- Strong and multi-factor authentication shall use cryptographic methods to make authentication resistant to keylogging, replay, session hijacking, and brute-force attacks.
- Methods include digital certificates, one-time passwords, and secure cryptographic modules for storing persistent keys.
- Persistent keys used for strong authentication or persistent encryption shall be protected using Hardware Security Modules (HSMs), Trusted Platform Modules (TPMs), secure elements, or smart cards that resist physical and logical attacks to extract the keys.
- Session encryption (such as that used by SSL, TLS, or IPSec) does not require hardwa re protection, except where session compromise would pose an enterprise risk.
- Data protection and cryptography modules, algorithms, protocols, and security configurations shall be reviewed on a periodic basis (for example, annually), including re-validation of all policy exceptions.
- Data protection and cryptography preventive, detective, audit, and forensic controls shall be verified and tested for proper operation on a periodic basis (for example, at least annually).
Monitoring, Vulnerability, and Patch Management
- Monitoring of account a ctivity and security incidents relies on robust logging of activities and alerting that catches potentially malicious activities.
- Such monitoring shall be able to detect violations of security policies, procedures, and active attacks when they occur.
- Timely detection of malicious activities aids in preventing or containing malicious actions before damage can be performed.
- Vulnerability and patch management reduce exposure to attacks by tracking and remediating vulnerabilities in a timely fashion, and by patching systems to reduce their exposure to attack.
- Activities must include the following:
- Enterprise systems and cloud services
- shall be monitored for performance and availability if delivering business-critical functions so that failures can be detected within a set period of time (for example, 30 minutes) of their occurrence; and
- shall forward their logs to a central system for correlation and analysis, or shall provide for in-place analysis and alerting that ties in with enterprise incident detection and investigation services.
- Log entries shall be synchronized to Coordinated Universal Time (UTC) or a clearly deline ated global time zone so the times when events occur are clearly presented to investigators.
- Security audit logs
- must clearly tie user activity in the information system to named user or service accounts;
- must be protected from tampering;
- shall be made available to support investigations for a set period of time (for example, one year) after the event is logged; and
- that are related to public company financial activities shall be retained for a set period of time (for example, seven years) after the event is logged.
- Networks shall be monitored to detect rogue or malicious devices connecting to them.
- Wireless networks shall be configured to detect attacks and rogue wireless access points.
- Cybersecurit y may use detective technologies such as honeypots, honeynets, and honeytokens to detect attacker exploits of vulnerabilities and identify attacker tools, techniques, and procedures (TTPs).
- System security monitoring shall feed into a central system for correlation that is monitored 24/7 to detect security incidents.
- Security logs shall be monitored for activities known or suspected to be malicious.
- Security alerts shall be generated within a set period of time (for example, 30 minutes) of such activity occurring.
- New applications and servers shall be vulnerability-scanned, and all medium or high vulnerabilities shall be addressed prior to their becoming operational.
- Enterprise applications that are generally available on the Internet or enterprise internal networks shall be scanned for vulnerabilities using a credentialed vulnerability scanner on a periodic basis (for example, m onthly).
- All medium or higher operating system vulnerabilities shall be addressed or remediated within a set period of time, such as 30 days, upon discovery.
- For sensitive systems with significant business impact, this remediation window may be shorter—as little as one day.
- Servers directly connected to the Internet
- Servers shall be scanned for operating system vulnerabilities using a credentialed vulnerability scanner on a periodic basis (for example, monthly).
- All medium or higher operating system vulnerabilities shall be addressed or remediated with a set period of time (for example, 30 days) upon discovery.
- For sensitive systems with significant business impact, this remediation window may be shorter—as little as six hours.
- Cybersecurity shall ensure that applications and systems in violation of vulnerability remediation policy are disconnected from the Internet and enterprise networks until remediation is performed and validated.
- Vendor-provided patches shall be evaluated and installed as recommen ded by vendors.
- Vulnerabilities relating to missing patches shall be handled as per vulnerability policy.
- When security patches cannot be installed for operational reasons, mitigating preventive and detective controls shall be employed to keep the overall risk acceptable.
- The system owner is responsible for patching.
- Automated systems may be used to simplify patch deployment.
- Limitations to such automated systems must be compensated for using manual techniques to ensure that security vulnerabilities are addressed in a timely manner.
- Detective controls shall be configured to detect attacker exploits of known vulnerabilities when this configuration is technically possible.
- Internet-facing and user networks shall be penetration-tested on a periodic basis, such as annually, to identify vulnerabilities related to real-world attacker techniques.
- Monitoring, vulnerability, and patch management are essential.
- Security configurations shall be reviewed on a periodic basis, such as annually, including re-validation of all policy exceptions.
- Preventive, detective, audit, and forensic controls shall be verified and tested for proper operation on a periodic basis, such as at least annually.
High Availability, Disaster Recovery, and Physical Protection
- Enterprise IT service s, systems, servers, and data shall be
- protected from losses of availability related to system failure, physical destruction, and accidental or malicious incidents; and
- configured with adequate redundancy and protection to meet business needs and cost-effective service delivery in the event of accidental or deliberate incidents targeting their availability.
- Activities must include the following:
- Availability
- Revenue-generating systems must have at least 99.99% availability.
- Other business IT systems must have at least 99.9% availability.
- Supporting infrastructure may be subject to high-availability requirements as needed by the business.
- Recovery Point Objectives (RPO) in the event of natural or man-made disaster
- Revenue-generating and business financial systems must be able to recover all committed transactions with customers or vendors that have financial consequences.
- Other business IT systems must be able to recover data up into the day previous to the incident (daily backup).
- Recovery Time Objectives (RTO) in the event of natural or man-made disaster
- Revenue-generating business functions must be able to recover and achieve initial operating capability within a specific time (for example, seven days).
- Business financial sys tems must be able to recover to initial operating capability within a specific time (for example, 45 days).
- Other business IT systems must be able to recover to initial operating capability within a specific time (for example, 90 days).
- Recovery Time Objectives (RTO) in the event of natural or man-made disaster
- Planning shall consider the time required for rebuilding affected servers, in addition to the time required for restoring affected data.
- Major system upgrades and configuration changes must include adequate backups to “roll back” the changes within the availability, recovery point, and recovery time requirements.
- Backup data
- shall be sufficiently protected physically and logically so that natural or man-made disasters will not result in the destruction of both the primary copy and the backup;
- that is taken offsite shall be encrypted, and the keys to that data shall be sufficiently protected from loss or compromise so that data can be recovered even in the event of catastrophic loss.
- Theft or loss of any enterprise-furnished equipment must be reported to the incident response team as soon as possible.
- Enterprise-sensitiv e data printed on paper or other material must be physically protected in a locked room or cabinet.
- Enterprise facilities and data centers
- These centers shall include physical protection, monitoring, and detective controls to protect personnel and equipment from harm and accidents.
- Sensitive data and systems handling personnel and equipment in an unencrypted fashion shall be protected using double-barrier protection and need-to-know access controls.
- Third-party access to the data center must be approved by the data center operations supervisor and guests must be escorted during the visit.
- When automated physical access controls are used at facilities, the access logs shall be
- maintained for a specific time (for example, one year) to support investigations by audit, security, legal, and law enforcement personnel; and
- monitored 24/7 to detect intrusions and intrusion attempts.
- Backup media, replication processes, and snapshot procedures must be tested periodically ( for example, at least annually) to verify their proper operation.
- Disaster recovery and service continuity plans must be tested using a drill, rehearsal, or tabletop practical exercise periodically (for example, every two years) to ensure their effectiveness.
- Physical security risk assessments must be conducted for all data centers, server rooms, and server closets on a periodic basis (for example, annually).
- High availability, disaster recovery, and physical protection
- Configurations shall be reviewed on a periodic basis (for example, annually), including re-validation of all policy exceptions.
- Preventive, detective, audit, and forensic controls shall be verified and tested for proper operation on a periodic basis (for example, annually ).
Incident Response
- A security incident is any malicious event (perceived or real) performed against the enterprise’s data or information systems.
- Such incidents can originate inside the enterprise (insider threat), in external entities, or in the surrounding environment.
- When a cybersecurity-related incident is reported, the incident response team takes charge of the incident and matrixes with the appropriate resources to investigate and remediate the situation.
- Activities must include the following:
- Incident response team shall
- track cybersecurity threats against the enterprise;
- inform cybersecurity and IT leadership of threats that pose new or previously unknown risk to the enterprise; and
- propose potential mitigations.
- All information systems supporting enterprise business systems must have a documented incident response process.
- Incident response processes must have clearly defined roles and responsibilities, and may leverage shared services that are centrally operated by cyber security.
- For major incidents, a single leader must be designated for the duration of the incident.
- Coordinates containment of the incident
- Reduces the impact
- Ensures remediation
- Keeps all stakeholders informed of the status
- Suspected incidents shall be investigated according to a set schedule (example timeframes):
- Critical alerts shall be investigated within one hour of their detection.
- High alerts shall be investigated within 12 hours of their detection.
- Medium alerts shall be investigated within 24 hours of their occurrence.
- Low or routine alerts shall be investigated within two business days of their occurrence.
- All incidents shall be documented to capture the originating alert or event, results of investigation, and remediation and conclusion.
- Confirmed incidents shall have their root cause investigated, identified, and documented.
- Incident documentation shall be retained for a specific period (for example, seven years after conclusion).
- Incident investigation teams shall
- have the tools and permissions they need to investigate accounts, computers, and networks involved in malicious activity; and
- have the ability to directly or by request disable and remediate accounts, computers, and networks as necessary to contain and resolve the incident.
- The cybersecurity de partment shall
- oversee contractual, regulatory, or legal obligations related to incidents;
- identify incidents with contractual, regulatory, or legal implications; and
- bring to bear the appropriate resources to ensure that contractual, regulatory, and legal obligations related to those incidents are met.
- The enterprise shall have anonymous methods for employees to report security policy violations or suspected security incidents without fear of reprisal.
- Incident response configurations shall be reviewed on a periodic basis (for example, annually), including re-validation of all policy exceptions.
- Incident response preventive, detective, audit, and forensic controls shall be verified and tested for proper operation on a periodic basis (for example, at least annually).
Asset Management and Supply Chain
- Asset management is the accoun ting of all enterprise assets (hardware and software).
- It is critical this information be kept up-to-date to support IT operation and handling of cybersecurity incidents.
- A supply chain management program covers both products and services to include the following:
- Security assessment
- Periodic re-assessments
- Inclusion of supplier information in the asset management database
- Activities must include the following:
- All software and hardware assets shall be assigned to an enterprise system with a primary and alternative employee point of contact.
- A centralized asset management system shall be utilized to track all enterprise hardware and software assets from their acquisition through to their disposal.
- A centralized c onfiguration and change management system shall be utilized to
- track configurations of enterprise hardware and software systems;
- track the approval of changes to those configurations; and
- detect unauthorized changes when they occur.
- Software licenses and software utilization in the enterprise shall be tracked so that
- software licenses can be matched to utilization;
- software license compliance can be ensured; and
- unauthorized software in the enterprise can be identified and remediated.
- As part of the system acquisition, cybersecurity shall review and approve vendors and suppliers, with associated risks identified and accepted or mitigated.
- Hardware and s oftware assets retired from service shall be properly disposed by
- removal of assets from asset and configuration databases;
- release of software licenses and termination of software and hardware support contracts; and
- sanitization or destruction of hardware persistent storage (flash and hard drive storage) to protect enterprise data.
- Persistent storage media, including flash drives, portable media, hard drives, and device-embedded storage (such as copiers and voicemail appliances with data storage features), shall be sanitized of enterprise data using the following:
- Physical destruction
- Data cleaning
- Data scrubbing
- Data encryption methods so that data may not be recovered after disposal
- Data disposal methods shall be validated periodically (for example, annually) to ensure their effectiveness.
- Data encryption methods shall be validated to ensure the encryption strength is adequate to protect data for a set period (for example, ten years) following disposal.
- Loss or unintended disposal of equipment or disclosure of data shall be reported as a cybersecurity incident.
- Hardware and software assets shall be inventoried periodically (for example, annually), with all associated points of contact validated and updated as necessary.
- Hardware, software, and service provider risk evaluations shall be reviewed and updated periodically (for example, annually) or when changes occur that materially affect the security posture.
- Cyberincidents or breaches
- Mergers
- Divestitures
- Bankruptcies
- Foreign acquisitions
- Asset management and supply chain configurations shall be reviewed periodically (for example, annually), including re-validation of all policy exceptions.
- Asset management and supply chain preventive, detective, audit, and forensic controls shall be verified and tested for proper operation perio dically (for example, at least annually).
Policy, Audit, E-Discovery, and Training
- Security governance is p aramount for the smooth functioning of the enterprise cybersecurity program.
- Maintenance of enterprise cybersecurity policies
- Periodic audits of controls and protections
- Support for legal e-discovery activities
- Training of cybersecurity personnel, employees and contractors in proper cybersecurity practices and techniques
- Activities must include the following:
- Enterprise cybersecurity policy shall be approved by business leadership with inp uts from key stakeholders.
- Business leadership
- Legal
- Contractual
- IT
- Cybersecurity departments
- A formal security forum shall be established to enable key stakeholders to discuss security matters on a regular basis and document policy changes or enhancement recommendations.
- Enterprise shall
- track cybersecurity risks and their potential consequences;
- report on cybersecurity risks and their mitigation on a periodic basis (for example, quarterly);
- employ tools to provide the following:
- overall cybersecurity governance
- risk management
- compliance reporting so all contractual, regulator, statutory and legal requirements can be met;
- comply with all contractual, regulatory, statutory, and legal requirement as th ey are stipulated:
- Sarbanes-Oxley (SOX), Payment Card Industry (PCI), and Health Insurance Portability and Accountability Act (HIPAA)
- regulations relating to privacy of employee and customer data; and
- comply with all requests for e-discovery originating from the legal department.
- Requests shall be documented.
- Documentation shall be retained for a set period (for example, seven years).
- Exceptions to cybersecurity policies shall be documented, tracked, and re-certified on a periodic basis (for example, annually).
- Policy exceptions that are not re-certified shall be removed and the policy enforced.
- The enterprise shall comply with customer and internal requirements for information system Certification and Accreditation (C&A), as specified in customer contracts and internal Memorandum of Understanding (MOUs).
- The enterprise shall ensure all employees receive annual training on cybersecurity concern s and obligations.
- Employees in positions of trust, including executives and systems administrators, shall receive additional training.
- Suitable to their roles
- Risks associated with those roles
- Their obligation to provide additional protection of enterprise and customer data
- The enterprise shall audit all cybersecurity preventive, detective, audit, and forensic controls on a periodic basis (for example, annually) to ensure their proper design and operation.
- Policy, audit, e-discovery, and training programs shall be reviewed on a periodic basis (for example, annually), including re-validation of all policy exceptions.
- Policy, audit, e-discovery, and training preventive, detective, audit, and forensic controls shall be verified and tested for proper operation on a periodic bas is (for example, at least annually).
