Overview
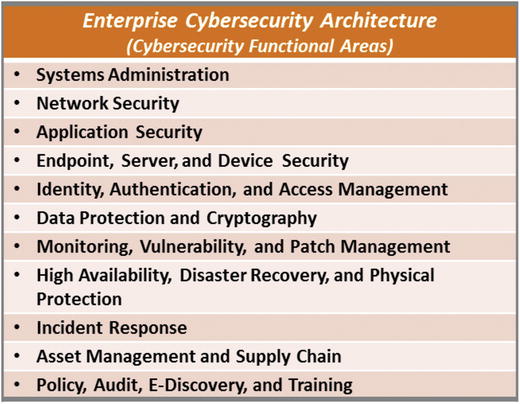
- This chapter describes an architecture consisting of cybersecurity functional areas used to organize and manage enterprise cybersecurity.
- Each functional area is described using the following characteristics :
- Definition
- Goal / Objectives
- Threat Vectors
- Capabilities
- As the cyberthreat evolves, so will specific functional areas and corresponding capabilities.
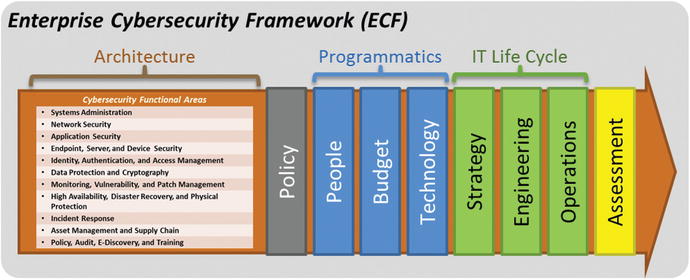
Organizing a cybersecurity program around the cybersecurity functional areas delineated in this presentation provides an enterprise with an underlying architecture for an extensible cybersecurity framework to protect against evolving cyberthreats.
Topics
- Systems Administration
- Network Security
- Application Security
- Endpoint, Server, and Device Security
- Identity, Authentication, and Access Management
- Data Protection and Cryptography
- Monitoring, Vulnerability, and Patch Management
- High Availability, Disaster Recovery, and Physical Protection
- Incident Response
- Asset Management and Supply Chain
- Policy, Audit, E-Discovery, and Training
Systems Administration
- Definition
- Provides secure administration of enterprise and security infrastructures by protecting systems administration (SA) channels from compromise
- Probably most important functional area because if it is compromised, an attacker can easily disable and bypass rest of enterprise security
- Goal / ObjectivesProtect the enterprise’s administrative channels from being used by an adversary
- Preventive objective is to (1) make it harder for attackers to get SA control, (2) slow down attackers so they are easier to catch, and (3) make it easier to catch attacks when they occur.
- Detective objective focuses on detecting attacks against SA channels and attempts at malicious SA activity.
- Forensic objective focuses on creating detailed audit logs of all privileged SA activities.
- Audit objective focuses on generating artifacts and evidence that SA is not malicious in the enterprise.
- Threat Vectors
- SA credentials and computers
- Computing infrastructure (virtualization, storage, and so on)
- SA infrastructure (enterprise computer management, patch management, other systems, and so forth)
- Monitoring systems that have administrative access to the enterprise
- Local computer administrative accounts to move from one computer to another
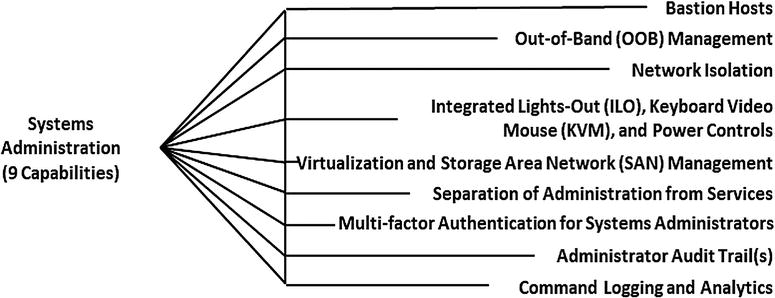
- Capabilities
- Make it harder for attackers to get administrative access
- Make attackers easier to detect and stop if they get control
- Isolate command and control networks and protocols
- Provide cryptographic protection for system administrators
- Allow for auditing of SA activities to detect attacks
- Representative Capabilities
- Bastion Hosts
- Out-of-Band (OOB) management
- Network Isolation
- Integrated Lights-Out (ILO), Keyboard Video Mouse (KVM), and Power Controls
- Virtualization and Storage Area Network (SAN) Management
- Separation of Administration from Services
- Multifactor Authentication for Systems Administrators
- Administrator Audit Trail(s)
- Command Logging and Analytics
Network Security
- Definition
- Protects enterprise network from unauthorized access
- Examines data traversing the network to detect intrusions against the network and connected computers
- Is used to channel user and attacker activity, routing it toward sensors and defensive mechanisms and away from weaknesses and vulnerabilities
- Involves filtering and monitoring the network traffic to block malicious network traffic and detect attacker network traffic
- Goal / ObjectivesProtect the enterprise’s network from use or attack by an adversary
- Preventive objective is to block or channel malicious traffic.
- Detective objective is to monitor and analyze network traffic.
- Forensic objective is to log information about network traffic.
- Audit objective is to analyze network traffic to identify malicious activity or generate artifacts indicating lack of malicious activity.
- Threat Vectors
- Outbound network connections from servers or clients on the internal network
- Network connections of Internet-facing servers
- Internal networks where attackers move laterally between computers inside the enterprise
- Network infrastructure components to gain entry to the enterprise or to bypass other security measures
- Capabilities
- Preventive, detective, forensic, and audit functions
- Not “silver bullets” that satisfy all cybersecurity requirements
- Can block, detect, and intercept many potential attacks
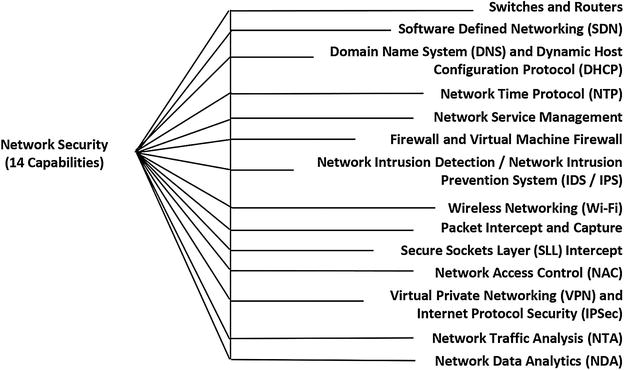
- Representative Capabilities
- Switches and Routers
- Software Defined Networks (SDN)
- Domain Name System (DNS) and Dynamic Host Configuration Protocol (DHCP)
- Network Time Protocol (NTP)
- Network Service Management
- Firewall and Virtual Machine Firewall
- Network Intrusion Detection/Network Intrusion Prevention System (IDS/IPS)
- Wireless Networking (Wi-Fi)
- Packet Intercept and Capture
- Secure Sockets Layer (SSL) Intercept
- Network Access Control (NAC)
- Virtual Private Networking (VPN) and Internet Protocol Security (IPSec)
- Network Traffic Analysis (NTA)
- Network Data Analytics (NDA)
Application Security
- Definition
- Involves security measures that are specific to certain applications or protocols running within the enterprise
- Protects applications accessible from the Internet with security
- Operates alongside network security
- Includes e-mail security, application-aware firewall features, database gateways, and forward web proxies
- Helps prevent attacks that exploit application vulnerabilities or application communication protocols
- Goal / ObjectivesProtect the enterprise’s applications from use or attack by an adversary
- Preventive objective is to block exploitation of applications and application communications protocols from malicious use.
- Detective objective is to detect compromises of applications and attempts to exploit them for malicious purposes.
- Forensic objective is to log data about application activities that can be used for audits and investigation of incidents.
- Audit objective is for auditors to be able to collect evidence and artifacts that suggest the applications are safe and not being used or manipulated by attackers.
- Threat Vectors
- E-mail messages that may contain attachments that attempt to exploit vulnerabilities
- Web browsers and web plug-ins
- Enterprise server applications (web application servers)
- Flaws in in-house enterprise applications
- Capabilities
- Additional protections to many enterprise applications that are tailored to them specifically
- Commercially-available solutions include e-mail filtering, web proxies, web application firewalls, and database firewalls
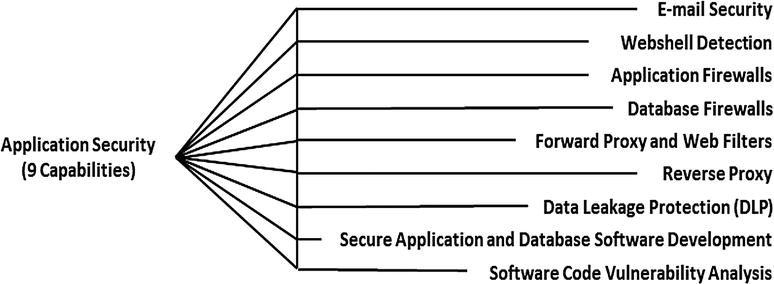
- Representative Capabilities
- E-Mail Security
- Webshell Detection
- Application Firewalls
- Database Firewalls
- Forward Proxy and Web Filters
- Reverse Proxy
- Data Leakage Protection (DLP)
- Secure Application and Database Software Development
- Software Code Vulnerability Analysis (including source code verification and bug tracking)
Endpoint, Server, and Device Security
- Definition
- Involves protecting endpoint computing devices (personal computers, servers, and mobile devices) from attack and detecting when those endpoint defenses have been breached
- Reduces the probability that the enterprise’s endpoints will be compromised
- Deploys protection tailored to specific needs of each computing platform. “One sizes does not fit all.”
- Goal / ObjectivesPrevent attackers from taking administrative control of computing devices
- The overall goal is to detect attempts to maliciously use these devices.
- The objectives include facilitating investigation of incidents when compromises of systems or data are suspected.
- Preventive objective is to make endpoints, servers, and devices hard to compromise. Endpoint security centers on hardening operating systems so they are difficult to breach and exploit.
- Detective objective is to alert the enterprise about malicious software and attempts to exploit the operating system so defenders can identify systems that are either compromised or under attack.
- Forensic objective is to log device activities securely so there is an audit trail for investigations. Forensics may include complete imaging of systems for detailed forensic analysis.
- Audit objective involves analyzing logs to identify malicious activity or to create artifacts indicating the absence of malicious activity on audited systems.
- Threat Vectors
- Unlimited ways to take control of an endpoint
- Operating system vulnerabilities
- Unpatched vulnerabilities–zero-day attacks
- Enterprise software products
- Administrative credentials
- Malicious software on app stores
- Capabilities
- Endpoint security, server security, and device security may need to be considered separately due to the differences in how they are used; there may be some common security capabilities.
- Capabilities include hardened computer images, computer policies, endpoint security suites (anti-virus, anti-malware, host firewall and intrusion detection) and polices for access controls, privilege management, auditing, and forensics.
- Mobile devices generally require their own sets of tools and technologies.
- BYOD may not have features needed for enterprise protection.
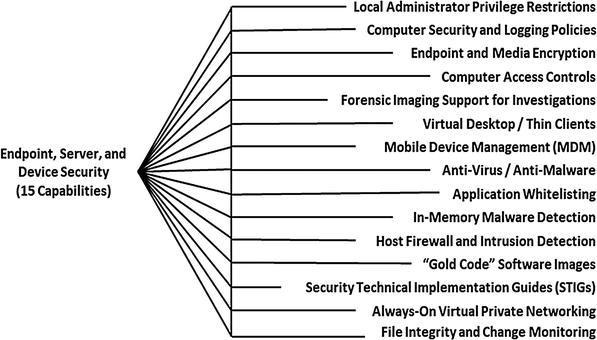
- Representative Capabilities
- Local Administrator Privilege Restrictions
- Computer Security and Logging Policies
- Endpoint and Media Encryption
- Computer Access Controls
- Forensic Imaging Support for Investigations
- Virtual Desktop/Thin Clients
- Mobile Device Management (MDM)
- Anti-Virus/Anti-Malware
- Application whitelisting
- In-Memory Malware Detection
- Host Firewall and Intrusion Detection
- “Gold Code” Software Images
- Security Technical Implementation Guides (STIGs)
- Always-On Virtual Private Networking (VPN)
- File Integrity and Change Monitoring
Identity, Authentication, and Access Management
- Definition
- Supports all other security functional areas by providing answers to the following questions:
- Who is accessing enterprise IT systems?
- How are they identified?
- What can they access once they are authenticated?
- Identity management helps to ensure accounts and accesses are provisioned, de-provisioned, and periodically re-certified according to enterprise policies.
- Authentication helps to ensure appropriate technologies are used to positively identify users who are accessing enterprise systems.
- Access management helps to ensure that privileges are provisioned and de-provisioned according to least privilege and that users do not have privileges exceeding their roles.
- Goal / ObjectivesEnsure only authorized people can access enterprise resources while people, resources, and permissions change over time
- Preventive objective is to make it harder for attackers to gain access to enterprise resources by impersonating legitimate users.
- Detective objective is to alert the enterprise on credential or permission abuse and identify when accounts are being attacked or have been compromised.
- Forensic objective is to log account activity that can be data-mined and correlated with other enterprise events to identify attack patterns.
- Audit objective involves analyzing logs to create artifacts and gather evidence if accounts and permissions are being abused.
- Threat Vectors
- Credential abuse
- Accounts that are no longer used or maintained, but have not been removed from enterprise
- Credentials to legitimate accounts used, in part, to escalate attacker privileges
- Weak authentication methods or protocols allow impersonation of legitimate users
- Weaknesses in privilege management allow regular user accounts to obtain administrative or other super-user privileges
- Capabilities
- Center around managing the full identity and access life cycle that can be complex and cost millions of dollars
- Require a careful balance between automation and manual procedures
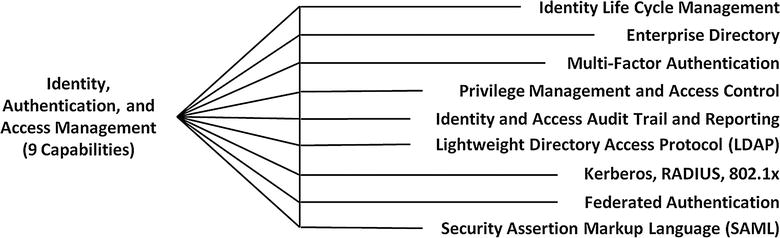
- Representative Capabilities
- Identity Life Cycle Management
- Enterprise Directory
- Multifactor Authentication
- Privilege Management and Access Control
- Identity and Access Audit Trail and Reporting
- Lightweight Directory Access Protocol (LDAP)
- Kerberos, RADIUS, 802.1x
- Federated Authentication
- Security Assertion Markup Language (SAML)
Data Protection and Cryptography
- Definition
- Protects data at rest and in transit
- Provides for strong authentication and non-repudiation for messages and data
- Supports message identity and authenticity
- Goal / ObjectivesProtect the confidentiality and integrity of data using such techniques such as encryption and digital signatures
- Preventive objective involves protecting the confidentiality and integrity of enterprise data by using cryptographic technologies.
- Detective objective involves monitoring enterprise cryptographic use to detect weak cryptography or cryptographic breaches when they occur.
- Forensic objective involves tracking the cryptography used in the enterprise and logging what algorithms and keys are used to support later investigations.
- Audit objective involves collecting information on the cryptography and keys that are used and their strengths, and ensuring they meet enterprise requirements for strength and protection.
- Threat Vectors
- Encrypted web sessions either into or out of an enterprise
- Attacker-encrypted enterprise data used to demand a ransom for the keys to decrypt the data
- Weak cryptography
- Passwords
- Keys to strong cryptography
- “Code signing” certifications
- Unencrypted stolen data (at rest or in transit)
- Capabilities
- Require three things to be accomplished correctly:
- Cryptography algorithms must be chosen that are secure and stay secure for the life of the protected data.
- Cryptographic keys must be chosen and protected from compromise.
- Application of cryptography must be carefully coordinated with the overall life cycle of the data to be protected.
- Decrypt data and protect decrypted data by other means so it can be used when needed
- Representative Capabilities
- Secure Sockets Layer (SSL) and Transport Layer Security (TLS)
- Digital Certificates (Public Key Infrastructure [PKI])
- Key Hardware Protection (Smart Cards, Trusted Platform Modules [TPMs], and Hardware Security Modules [HSMs])
- One-Time Password (OTP) and Out-of-Band (OOB) Authentication
- Key Life Cycle management (including key rotation)
- Digital Signatures
- Complex Passwords
- Data Encryption and Tokenization
- Brute Force Attack Detection
- Digital Rights Management (DRM)
Monitoring, Vulnerability, and Patch Management
- Definition
- Monitors the status of the enterprise’s security
- Maintains security over time by identifying and patching vulnerabilities as they become known
- Supports operational processes by identifying and patching vulnerabilities
- Monitors security systems so security alerts can be detected and acted upon
- Goal / ObjectivesUnderstand how security changes over time
- Preventive objective is to ensure vulnerabilities are compensated for and patched before they can be exploited by attackers.
- Detective objective involves monitoring all enterprise security automation systems to detect incidents.
- Forensic objective involves logging event and incident information to be correlated, cross-checked, and investigated.
- Audit objective involves centrally collecting forensic data to be analyzed by auditors and investigators.
- Threat Vectors
- Attack methods that are not detected, or detected by unmonitored systems and are invisible to defenders
- Exploit of software vulnerabilities during the time window when they become known and before they can be patched enterprisewide
- Exploit of vulnerabilities in software components that are not centrally managed or patched
- Zero-day exploits
- Compromise of security or logging infrastructure to block or delete records of attacker activities
- Lack of cross-correlation of attacker activities
- Capabilities
- Focus on maintaining the enterprise’s security on an ongoing basis and actively detecting incidents against enterprise security systems
- Collect and analyze logging data
- Process data to identify events of interest
- Identify specific incidents that require investigation and remediation
- Scan the enterprise infrastructure and computers to identify vulnerabilities in software or configuration so identified vulnerabilities can be remediated
- Help ensure the ongoing patching of commercial products to keep them current with the latest security fixes and enhancements
- Representative Capabilities
- Operational Performance Monitoring
- System and Network Monitoring
- System Configuration Change Detection
- Privilege and Access Change Detection
- Log Aggregation
- Data Analytics
- Security Information and Event Management (SIEM)
- Network and Computer Vulnerability Scanning
- Penetration Testing
- Patch Management and Deployment
- Rogue Network Device Detection
- Rogue Wireless Access Point Detection
- Honeypots/Honeynets/Honeytokens
- Security Operations Center (SOC)
High Availability, Disaster Recovery, and Physical Protection
- Definition
- Provides the enterprise’s primary protection against threats to availability
- Leverages HADRPP capabilities for protection against all types of hazards to availability, not just cyberattacks
- Provides cost-effective business continuity capabilities measured in terms of recovery point objectives (RPO) and recovery time objectives (RTO)
- Goal / ObjectivesSatisfy business requirements for continuity of operations in the face of adversity
- Rather than discuss this functional area in terms of preventive, detective, forensic, or audit objectives, it makes more sense to discuss it in terms of the enterprise’s reaction capabilities.
- Overall objective is to ensure enterprise has ability to respond to wide range of potential adverse situations.
- Perhaps most importantly, an enterprise needs to consider how these reaction capabilities might serve the enterprise in the event of a cyberattack.
- Threat Vectors
- Adversities, whether they come from regular mechanical wear and tear, natural circumstances that are outside of anyone’s control, or human-led activities that are either negligent or malicious
- Scheduled maintenance when systems are taken offline
- Regular wear and tear or hard-to-predict circumstances that result in enterprise systems failing
- Cyberattack impacts to the integrity of IT systems such as backup systems or disaster recovery systems
- Loss of a primary data center
- A deliberate attack (act of war or a sophisticated criminal act) resulting in the physical destruction or impairment of facilities required for operations
- Capabilities
- Center on making IT systems more robust and having the same data in multiple locations
- Protect the physical devices and storage containing enterprise data and systems
- Primarily about availability, but also consider data confidentiality and integrity
- Representative Capabilities
- Clustering
- Load Balancing, Global Server Load Balancing (GSLB)
- Network Failover, Subnet Spanning
- Virtual Machine Snapshots and Cloning
- Data Mirroring and Replication
- Backups and Backup Management
- Off-Site Storage
- Facilities Protection
- Physical Access Controls
- Physical Security Monitoring
Incident Response
- Definition
- Capability to respond to cybersecurity incidents
- Occurs when monitoring reveals that something of interest has actually occurred
- Consists of further alert analysis and investigation to understand what is occurring and its significance
- Is primarily procedural with some supporting technology
- Does not protect enterprise from attack
- Gives the enterprise the ability to respond to attacks
- Is a multistep process consisting of investigating, reporting, containing, and ultimately remediating the incident
- Includes operational disruptions, security incidents, deliberate attacks, natural and man-made disasters, and mistakes/accidents
- Goal / ObjectivesProvide for timely response when security incidents are identified
- Overall objective is to reduce the enterprise’s vulnerability while simultaneously repelling the attack.
- Overall objective includes clearly defining formal communication channels and lines of authority.
- Overall objective includes defines processes for assessing the situation so the enterprise understands when a situation is “snowballing” and overwhelming the enterprise’s initial response.
- Overall objective includes knowing the limits of the enterprise’s crisis response capabilities and the potential losses of service due to exceptional severe circumstances.
- When the enterprise is operating in a degraded state, it is critical to have a security reserve to protect the enterprise.
- Threat Vectors
- No enterprise incident-response process coordinated ahead of time
- Poor coordination between operational and security personnel
- Failure to feed indicators of compromise (IOCs) back to the monitoring and detection process
- Incident remediation process fails to adequately strengthen defenses that were breached
- Deliberate attackers leveraging the incident response (for example, attackers force the enterprise into an incident response mode and then manipulate and disable security features)
- Failure to account for regulatory or legal requirements on reporting and disclosure that can result in financial, legal, or public relations penalties
- Capabilities
- Enable the enterprise to respond to incidents effectively and efficiently
- May include technologies that greatly assist with the forensic investigations needed to track down and catch stealthy attackers
- May be fundamentally procedural in nature
- Representative Capabilities
- Threat Information
- Incident Tracking
- Forensic Tools
- Computer Imaging
- Indicators of Compromise (IOC)
- Black Hole Server
- Regulatory/Legal Coordination

Asset Management and Supply Chain
- Definition
- Involves tracking enterprise assets and the origin of the assets
- Accounts for the IT enterprise assets throughout their life cycle
- Has appropriate level of confidence assets are doing what they are supposed to be doing
- Prerequisite for endpoint and server security controls
- Helps ensure assets are accounted for during their life cycle and made compliant with enterprise policies when they are put into service
- Helps ensure assets are properly disposed of or protected when assets are finally disposed at the end of their life cycle
- Goal / ObjectivesEnsure the enterprise knows what IT assets it has and manage supply chain risks from acquisition through operation through disposal
- Overall objective is to ensure operational staff follow proper procedures that are supported by various technical capabilities.
- Threat Vectors
- Attacker’s ability to place components in the enterprise without those components being noticed
- Unauthorized changes or reconfiguration of systems
- Compromised products provided by suppliers
- Supplier ecosystem that is not protected as well as the enterprise
- Disposed electronics that were not properly sanitized, revealing enterprise information
- Capabilities
- Ensure enterprise assets are accounted for over their life cycle, are made compliant with enterprise policies, and are properly disposed at end of life
- Ensure assets are obtained from trustworthy suppliers
- Representative Capabilities
- Asset Management Database
- Configuration Management Databases (CMDB)
- Change Management Databases
- Software Inventory and License management
- Supplier Certification Processes
- Secure Disposal, Recycling, and Data Destruction

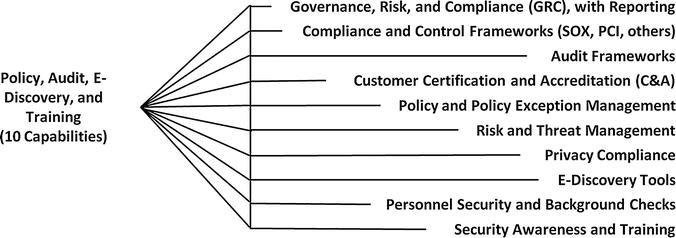
Policy, Audit, E-Discovery, and Training
- Definition
- Deals with governance and security oversight functions
- Includes mapping security controls to meet compliance requirements, along with some secondary functions regarding personnel security and privacy concerns
- Sets the organizational strategy for all other functional areas (policy)
- Periodically reviews other functional areas for compliance (audit)
- Oversees
- External reporting requirements
- Audit program of preventive, detective, and monitoring controls
- Interfaces with the legal department to support e-discovery
- Training for employees, IT, and security personnel
- Home of the Chief Information Security Officer (CISO)
- Goal / ObjectivesAddress the people, policy, regulatory, and compliance aspects of enterprise cybersecurity
- Control of enterprise processes and capabilities
- Management of programmatic and personnel issues associated with process and capability deployment
- Threat Vectors
- Consist of gaps that result in processes or capabilities being neglected, causing security risks
- Security management
- Compliance management
- Personnel security
- Training and accountability
- Capabilities
- Provide oversight of controls and audit of their effectiveness, support for legal e-discovery activities, and training of staff in proper security policies and practices
- Account for compliance requirements and mapping security controls to meet those requirements
- Oversee the security control audit program that periodically reviews preventive, detective, and monitoring controls to verify their operation and effectiveness
- Representative Capabilities
- Governance, Risk, and Compliance (GRC) with Reporting
- Compliance and Control Frameworks (SOX, PCI, others)
- Audit Frameworks
- Customer Certification and Accreditation (C&A)
- Policy and Policy Exception Management
- Risk and Threat Management
- Privacy Compliance
- E-Discovery Tools
- Personnel Security and Background Checks
- Security Awareness and Training