A formal change management process is not only a requirement for many regulatory and standards bodies, but in general a good practice of due diligence. In the typical implementation of change management there is a process followed to ensure all affected parties are aware of a planned change. This allows the various business units and IT to fully understand impact and properly set the risk level for the change. What happens many times though is the security team is not made aware of the changes in the environment. Sometimes this lack of review is due to reducing the workload for the team and not overburdening them with reviewing countless changes. This can be a serious misstep because teams may not be aware that a change has security implications.
Another issue is intentional bypassing of security because security is seen as a road block. Information security should be involved in changes that affect the security posture of the enterprise, introduce risk, involve a modification to an existing implementation, or a net new implementation. There are approaches to IT service management such as ITIL that provides an excellent road map for proper change management implementation and process flow. The following process flow diagram is from Cisco's High Availability Change Management: Best Practices site http://www.cisco.com/en/US/technologies/collateral/tk869/tk769/white_paper_c11-458050.html, and is also available via download in PDF form from http://www.cisco.com/en/US/technologies/collateral/tk869/tk769/white_paper_c11-458050.pdf:
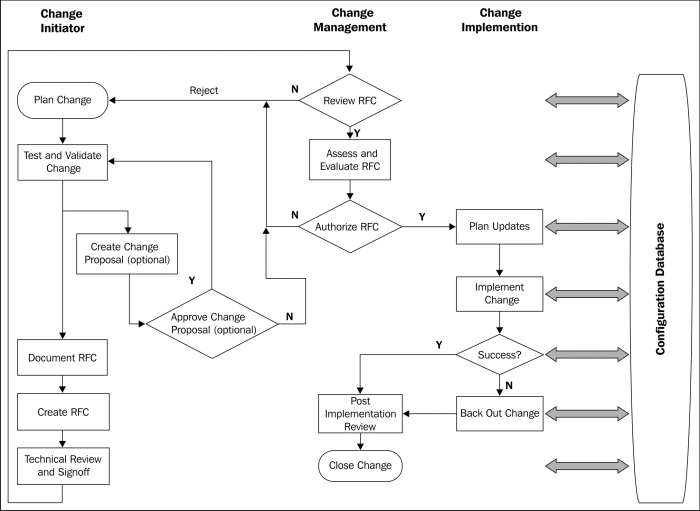
Ideally, the security team would be involved in technical review and post-implementation review phases of the change management process. This will allow the security team to halt a change if it is assessed as too risky, or provide another solution to meet the business needs without increasing risk. The security team should thoroughly document their review of the change for audit purposes and for historical documentation.
The perimeter, whatever and wherever it is, is the area where the first line of defense is positioned to protect assets within the perimeter. Types of security mechanisms deployed at the perimeter include, but are not limited to firewalls, intrusion detection and prevention, data loss prevention, Internet proxy, and advanced malware mitigation. Therefore changes to this infrastructure can have a significant impact on the security provided at the perimeter. Changes in this area of the network should by default always include the information security team to assess the security implications of the change and assign a risk value to the proposed change. Though the perimeter is typically not the scope of attack if there is a weakness introduced, it can be detected and exploited. A recent large-scale breach was the result of the data loss prevention technology being configured only to detect not prevent, as it is capable of doing. The implementation may have always been in this manner, but changes like this can happen with a lack of due diligence and oversight by the information security team.
The following are a few questions to determine if IT security should review a change:
- Does the change involve a perimeter network or security solution?
- Does the change provide more access than previously permitted?
- Does the change affect traffic flow at the perimeter?
- What type of access is being provisioned?
- What systems and data are being accessed?
If this process is implemented, it is critical that there is absolutely no change implemented without the explicit documented approval of the information security team. The other side of this equation is that the information security team must involve themselves in the process and when presented with a change, understand it, analyze it, and if it is not a sound security change, provide an alternative solution to the requester. This last step not happening is what usually gets the security team bypassed. Other times the security operations team who run the security infrastructure such as firewalls are simply aggressively entering firewall policy changes in order to reduce a ticket queue with no regard to the security implications of the request.
All data within the enterprise ideally is classified, and the handling of all data types is communicated and understood by all those who will handle enterprise data. The challenge that is typically the undoing of data classification is enforcing the policy. What happens over time is data is put where it is not supposed to be and not protected properly; it either sits there unnoticed or it falls into the wrong hands. What we attempt to do is protect at the system level, but in reality this method is no less than useless.
Implementation of the trust models applied to enterprise data should get us to the protection mechanisms required to enforce the trust level we have for who and what is accessing the data. Once we have implemented these mechanisms, we need to closely monitor any and all changes to the protection mechanisms. Changes will most likely be location of the data or modification to access permissions.
With data protection the primary concern of auditing bodies, permissions for all locations of data whether a file, file share, database, or ETL, will be heavily scrutinized to ensure that only those individuals, processes, and applications that need access to the data are permitted it. The access level will be audited as well. Ideally, data access changes are few and far between and when it does occur, the process is well documented. The documentation should include all the information necessary for both internal and external resources to make a proper risk decision and be able to attest to the business reason for the access creation or access modification. Including data access modifications and additions in the formal change management process will ensure the previously mentioned documentation and approvals occur. If the enterprise loses sight of the value their data represents, then the IT security team has some work to do!
The following are a few questions to ensure review of data access changes:
- Is the data business critical?
- Are there internal and/or external regulatory requirements for protection?
- Is the access method secure?
- What trust model does this access fall within?
Great! A new network segment was created. The new zone was undoubtedly in reaction to a business unit request. Should information security have been made aware of the request before implementation? Absolutely! The network itself is the infrastructure that provides connectivity to business partners, third parties, the Internet, and enterprise assets so it is important when it undergoes a modification that IT security is able to analyze any risk and make suggestions or provide solutions to reduce the impact to the enterprise.
Communicating network changes to other IT teams will help identify when security mechanisms implemented may not be in place where the change is occurring to provide the correct security protection. The security team usually thinks more from a data position and network teams about how to get traffic from point A to point B. Both are correct, but they need to work together to ensure the long-term protection and availability of the enterprise data.
As networks become more complex to support emerging technologies and updated protocols, the relationship between network and security becomes less of a non-functional requirement but an intertwined and joint venture. IPv6 is an example where there are many security implications when assessing the implementation of the upgraded protocol. Various enterprise implementations seem to be eluding the traditional wisdom of network and security architecture and are putting a strain on current solutions. Therefore, network teams are sometimes forced to make bad decisions to meet a business request. Reaching out to the ally security team may be the best option to save the enterprise from itself.
A benefit of engagement across both network and security teams is an evaluation of current network and security technologies implemented at each phase of change. Significant cost can be attributed to increasing security hardware required to protect each perimeter connection. This is leading to a shift in integrated solutions where a firewall, IPS, and proxy server is one physical device providing the protection of the traditional three separate solutions. Security spend can be more intelligent by simple cooperation and collaboration with other teams. Business benefits can be realized with a simple step in the change management process to include IT security.
