Firewalls have been an interesting evolution. They not only provide the most basic protection, but are also able to understand the traffic inspected and look for the applications being used. This may seem insignificant at first glance, but to have a device that can tell if the traffic traversing the firewall is legitimate or not, and be able to mitigate malicious traffic masquerading as legitimate, can be the difference between a breach and a non-event. An example may be the DNS traffic as inspected by a standard firewall, which looks like legitimate DNS traffic, but in reality has DNS packets that are padded with data that is being exfiltrated from the network.
A next generation firewall (NGFW) would be able to detect the anomaly behavior in such network transactions, alerting security staff of a potential network breach. The standard firewall would simply check for the policy allowing the source IP, destination IP, and TCP/UDP port, without a further deep packet analysis to ensure that the traffic is in fact DNS related. This is the primary distinction between an NGFW and a stateful firewall. The following image is taken from the Palo Alto networks website (http://media.paloaltonetworks.com/documents/Content_ID_tech.pdf). It shows how an NGFW inspects traffic for data, threats, and web traffic:
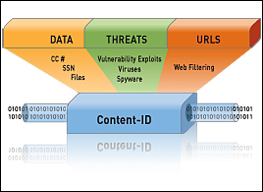
Over the years, there have been many names given to firewalls with the ability to identify application traffic. Most recently, it is called the NGFW. Each vendor has developed a trademarked name along with unique offerings. There are leaders in this space, such as Palo Alto Networks. Where the firewall industry is headed is still unclear, as the path of software development blazes with more features and the firewall role is becoming gray. This is partly because the value of a one-trick pony technology doesn't uniquely distinguish the vendors enough, nor does it drive better mitigation technologies for the buyer.
With next generation firewalls, new technologies become a part of the firewall tier, including intrusion prevention, user authorization, application awareness, and advanced malware mitigation, further expanding the role of the next generation firewall in a network.
This shift in firewall capabilities may add confusion to the role the appliance plays in the overall network protection in comparison to web application and database firewalls. While the next generation firewall provides some coverage across these areas today, the available platforms do not have the advanced capabilities of purposefully designed web application firewalls or database firewalls. An NGFW is capable of basic detection and mitigation of common web application attacks, but lacks the more in-depth coverage provided by web application firewalls with database counterparts. It is important to note that implementing a NGFW in addition to web application and database firewalls provides the most comprehensive coverage for a network. A more detailed coverage of web application firewalls with database protection capabilities will be covered later in this chapter.
The most significant benefit of the NGFW is awareness . I know, this sounds like a sci-fi artificial intelligence concept. In a way, it is. The NGFW no longer makes packet permit and deny decisions using only the simple network portions of the communication, such as source and destination IP and port pairings; it can look into the traffic flow and decode the exact application that makes up the communication flow. This is rather special from a security perspective. The technology is aware of what the traffic is, and not just how the traffic is communicating. For years, malware has been able to invade and evade by simply masquerading as well-known legitimate traffic.
The NGFW makes evasion much more difficult, requiring malware writers to leverage encryption and complicated encoding methods to evade the firewall. While this constitutes an evasion method, there are methods to mitigate unwanted traffic with obfuscated malicious payloads within the NGFW and other perimeter security mechanisms. Two more significant features of the NGFW include intrusion prevention technology and user awareness.
The firewall can now detect and mitigate attacks typically analyzed by an intrusion prevention system while reducing the complexity of a DMZ implementation. In the common DMZ design there may be a firewall in addition to an intrusion prevention system in order to enforce permitted traffic and mitigate threats over acceptable ports and protocols. This separation in systems, while effective at segregation of duties, further complicates the network implementation and presents another point of failure. Having IPS functionality within the firewall makes sense, as the appliance is already in-line and inspecting network traffic. Potential downsides may be the maturity of the feature in a, NGFW, effective segregation of duties, and performance loss with feature enablement.
User role-based access facilitates separation of duties for policy administration, reporting, and troubleshooting. With the ability to authorize a user as a part of a rule, access is no longer based solely on a valid IP address and port pair, but also on who is attempting the access. User awareness also makes the firewall an excellent choice within the network to secure various segments, by authorizing access based on user and network information.
These features add significant layers of security to the traditional firewall. We will look at each feature in depth to help realize the benefits of the next generation firewall.
This feature alone provides the most value in an NGFW platform. Application awareness has for years been implemented poorly and to the point where the feature was typically turned off, reducing the firewall to the most basic mitigation through access control list logic.
The shortcoming in the area of application awareness has allowed undetected unauthorized access at staggering levels. This is evident as longtime breaches take one to three years to finally detect, because the data exfiltration was happening over accepted ports and protocols with no application awareness. The firewall manufacturers were right when they moved in the direction of application detection. This provides intelligent decision factoring, based on more than network level information that can be easily spoofed, allowing evasion.
Traditional firewalls only look at the source and destination IP addresses and the TCP or UDP port to make a decision to block or permit a packet. Here is a simplified version of a TCP packet with an IP header to only show the fields that a basic non-NGFW will inspect for the permit or deny decision. These fields are indicated by the dotted line:
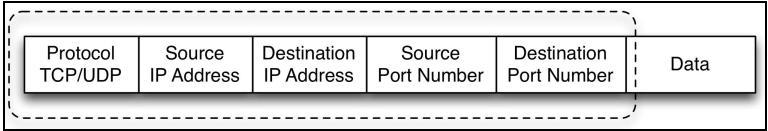
Simplified TCP packet with IP header with header inspection only
Having the application awareness capability, NGFW is able to perform deep packet inspection to also decode and inspect the application data in network communication.
The thought leaders in this technology area have made application awareness a must have. We have seen this feature mature rapidly. Some firewall manufacturers, such as Palo Alto Networks, are able to identify over 3000 unique applications as traffic traverses the firewall. An example benefit of this capability is detecting and mitigating protocol misuse. This method of attack would typically be passed ignorantly through a basic firewall. Additional examples are applications such as torrent clients, anonymous proxy services, and tunneled connections back to a home, office, or other unapproved destinations. The ability to identify and take action on network traffic that violates security policy or in other ways introduces risk to the enterprise reduces the enterprise threat surface significantly.
It is highly recommended to do your research when assessing what technology to purchase. There are well-known testing services, such as NSS Labs (https://www.nsslabs.com/), that can provide objective effectiveness testing results. Understanding the purpose of the device in the network is critical to product selection. Leveraging a trusted third-party integrator may also be a method to test the validity of vendor claims and observe the solution in the environment prior to a purchase.
The following questions may influence a purchase decision:
- What is the perceived need for the technology?
- What protection capabilities are required?
- How does the product integrate with existing infrastructure and technologies?
- Will the technology be used to augment other solutions?
- What is the level of expertise required to operate the solution?
Another benefit of the NGFW is the inclusion of intrusion prevention technology. This is significant, because one challenge the security team must face is providing intrusion prevention coverage for every connection to the enterprise network. With the average cost of an IPS being over $40,000, this adds up quickly in addition to the support and maintenance costs. The balance of available budget and protection requirements increases the acceptance of relatively similar protection from a software feature of the firewall that is already inline. It is not a bad gamble as firewall manufacturers have taken this new responsibility seriously and are providing undeniable intrusion prevention protection according to industry-accepted lab tests results.
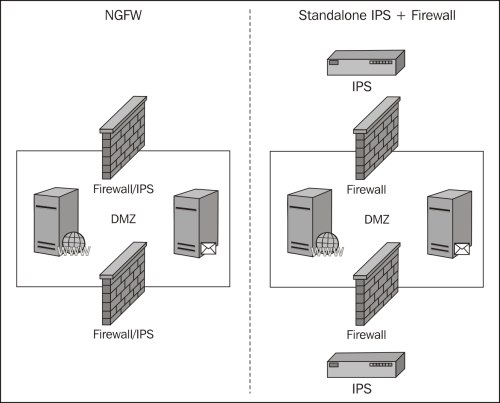
Simplifying the security implementation at the perimeter provides several gains that must be taken into consideration when replacing the traditional standalone intrusion prevention system. First, removing a device and the related management components simplifies management of IT security and the skillsets required to operationally support the solution. Second, one less appliance in the DMZ or inline inspecting traffic increases the performance and removes one layer of failure probability.
Here is a diagram depicting an example of the benefit of simplification using a next generation firewall IPS feature-set. There are fewer devices in the network perimeter, reduced management requirements, and less points of failure.
The newest addition to the features that NGFWs are offering is advanced malware protection in the form of botnet identification along with malware analysis in the cloud. Botnets, such as Zeus, have been a painful reminder that end point protection and security awareness training alone will not thwart the more persistent malware writers. A few products have come to market to address advanced malware detection and mitigation, but with significant cost to purchase and the additional skillset needed to properly use the tools. With a solution built into the firewall, where the malware is examined in the cloud, protection developed and mitigation implemented by the manufacturer, all without any work by the customer or additional operational costs, make this an attractive option.
There are standalone solutions for Advanced Persistent Threat (APT) detection and mitigation at the network perimeter, but there is a learning curve and additional analysis required. This may not be an issue for an organization that can get the skillset needed, but it is not attainable for smaller IT organizations. Another consideration for standalone solutions is the high price tags of the top products in this space.
Note
When evaluating a solution, look for opportunities to simplify implementation and operationalizing. Where there are expertise gaps, there may be features built into the solution that provide the benefits of advanced analysis and mitigation that would take additional time and money to equal the value.
An example is malware analysis, detection, and mitigation. This is a highly specialized skillset. If this can be done in an automated fashion, value can be realized quickly.
Malware mitigation at the perimeter is not the ideal implementation, however, it does provide an additional layer of protection needed before the malware can make a successful connection back to the initiator. It is assumed that if the detection and mitigation happens at the network perimeter, internal hosts get infected and current endpoint protection becomes insufficient. If the firewall can provide this last layer of malware communication disruption, it is a worthwhile investment. While the next generation firewall implementation is less mature than the standalone solutions, leveraging the cloud and the vendor's entire customer base to provide samples will increase the effectiveness and value of the feature at an accelerated rate.
