Chapter 16
Databases and Storage Systems
IN THIS CHAPTER
![]() Testing and exploiting database flaws
Testing and exploiting database flaws
![]() Finding storage weaknesses
Finding storage weaknesses
![]() Ferreting out sensitive information
Ferreting out sensitive information
![]() Countering database and storage abuse
Countering database and storage abuse
Attacks against databases and storage systems can be very serious, because that’s where “the goods” are located, and those with ill intent are well aware of that fact. These attacks can occur across the Internet or on the internal network when external attackers and malicious insiders exploit any number of vulnerabilities. These attacks can also occur via the web application through SQL injection. This chapter covers some common vulnerabilities that, when exploited, can be very impactful to the business.
Diving Into Databases
Database systems — such as Microsoft SQL Server, MySQL, and Oracle — have lurked behind the scenes, but their value and vulnerabilities have finally come to the forefront. Yes, even the mighty Oracle, which was once claimed to be unhackable, is as susceptible to exploits as its competition. With the slew of regulatory requirements governing database security, hardly any business can hide from the risks that lie within because practically every business (large and small) uses some sort of database, either in-house or hosted in the cloud.
Choosing tools
As with wireless networks, operating systems, and so on, you need good tools if you’re going to find the database security issues that count. The following are my favorite tools for testing database security:
-
Advanced SQL Password Recovery (
https://www.elcomsoft.com/asqlpr.html) for cracking Microsoft SQL Server passwords. -
Cain & Abel (
www.oxid.it/cain.html) for cracking database password hashes. -
Nexpose (
https://www.rapid7.com/products/nexpose) for performing in-depth vulnerability scans. -
SQLPing3 (
www.sqlsecurity.com/downloads) for locating Microsoft SQL Servers on the network, checking for blank passwords for the sa account (the default SQL Server system administrator), and performing dictionary password-cracking attacks.
You can also use network vulnerability scanners, such as Nexpose, along with exploit tools, such as Metasploit, for your database testing.
Finding databases on the network
The first step in discovering database vulnerabilities is figuring out where they’re located on your network. It sounds funny, but many network admins I’ve met aren’t even aware of various databases running in their environments. This situation is especially true of the free SQL Server Express database software editions that users can download and run on your network.
The best tool I’ve found to discover Microsoft SQL Server systems is SQLPing3 (see Figure 16-1).

FIGURE 16-1: SQLPing3 can find SQL Server systems and check for missing sa account passwords.
SQLPing3 can even discover instances of SQL Server hidden behind personal firewalls, such as Windows Firewall. This feature is nice, as Windows Firewall is enabled by default in Windows 7 and later.
Cracking database passwords
SQLPing3 also serves as a nice dictionary-based SQL Server password-cracking program. As Figure 16-1 shows, it checks for blank sa passwords by default. Another free tool for cracking SQL Server, MySQL, and Oracle password hashes is Cain & Abel, shown in Figure 16-2.

FIGURE 16-2: Using Cain & Abel to crack Oracle password hashes.
You simply load Cain & Abel, click the Cracker tab at the top, select Oracle Hashes in the bottom-left corner, and click the blue plus symbol at the top to load a user name and password hash to start the cracking. You can also select Oracle TNS Hashes at bottom left and attempt to capture Transport Network Substrate hashes off the wire when capturing packets with Cain. You can do the same for MySQL password hashes.
The commercial product ElcomSoft Distributed Password Recovery (https://www.elcomsoft.com/edpr.html) can also crack Oracle password hashes. If you have access to SQL Server master.mdf files (which are often readily available on the network due to weak share and file permissions, as I outline later in this chapter), you can use ElcomSoft's Advanced SQL Password Recovery to recover database passwords immediately.
As you can imagine, these password-cracking tools are great ways to demonstrate the most basic of weaknesses in your database security. They’re also nice ways to underscore the problems with critical files scattered across the network in an unprotected fashion.
Another good way to demonstrate SQL Server weaknesses is to use SQL Server Management Studio (https://docs.microsoft.com/en-us/sql/ssms/download-sql-server-management-studio-ssms) to connect to the database systems you now have the passwords for and to set up backdoor accounts or browse around to see (and show) what’s available. Practically every unprotected SQL Server system I come across has sensitive personal financial or healthcare information available for the taking. It simply takes a query such as the following to access the records in any given table:
select * from tablename
Scanning databases for vulnerabilities
As with operating systems and web applications, some database-specific vulnerabilities can be rooted out only by using the right tools. I use Nexpose to find such issues as the following:
- Buffer overflows.
- Privilege escalations.
- Password hashes accessible through default/unprotected accounts.
- Weak authentication methods enabled.
Many vulnerabilities can be tested from both an unauthenticated outsider’s perspective as well as a trusted insider’s perspective. The important thing is to review the security of your databases from as many angles as reasonably possible. As I’ve said before, if a database is out there and accessible, people are going to play with it.
Following Best Practices for Minimizing Database Security Risks
Keeping your databases secure is fairly simple if you do the following things:
- Run your databases on dedicated servers (or workstations where necessary).
- Check the underlying operating systems for security vulnerabilities. (I cover operating system (OS) exploits for Windows and Linux in chapters 12 and 13, respectively.)
- Ensure that your databases fall within the scope of vulnerability scanning, patching, and system hardening.
- Seek out and replace (or otherwise segment off) end-of-life database systems. They’re just too risky to leave around.
- Require strong passwords on every database system. Most enterprise-ready databases, such as Oracle and SQL Server, allow you to use domain authentication (such as Active Directory or LDAP) so that you can tie in your existing domain policy and user accounts without having to worry about managing a separate set.
- Use appropriate file and share permissions to keep prying eyes away.
- Deidentify any sensitive production data before it’s used in nonproduction environments such as development or quality assurance.
- Check your web applications for SQL injection and related input validation vulnerabilities. (I cover web application security in Chapter 15.)
- Use a network firewall, such as the type available from Fortinet (
https://www.fortinet.com) or Cisco (https://www.cisco.com) and database-specific controls, such as those available from Imperva (https://www.imperva.com) and IDERA (https://www.idera.com). - Perform related database hardening and management by using a tool such as Microsoft Security Compliance Manager (
https://technet.microsoft.com/en-us/library/cc677002.aspx). - Run the latest version of database server software. The new security features in Oracle, SQL Server 2016 and SQL Server 2017 are great advancements toward better database security for on-premise databases as well as those in the cloud.
Opening Up About Storage Systems
Attackers are carrying out a growing number of storage-related hacks and using various attack vectors and tools to break into the storage environment. (Surely you know what I’m going to say next.) Therefore, you need to get to know the techniques and tools yourself and use them to test your own storage environment.
As with databases, practically every business has some sort of network storage housing sensitive information that it can’t afford to lose. For that reason, it’s important to include both network storage (SAN and NAS systems) and traditional file shares in the scope of your security testing.
Choosing tools
These are my favorite tools for testing storage security:
-
nmap (
http://nmap.org) for port scanning to find live storage hosts. -
SoftPerfect Network Scanner (
https://www.softperfect.com/products/networkscanner) for finding open and unprotected shares. -
FileLocator Pro (
https://www.mythicsoft.com) for finding specific files and information. - Nexpose for performing in-depth vulnerability scans.
Finding storage systems on the network
To seek out storage-related vulnerabilities, you first have to figure out what’s where. The best way to get rolling is to use a port scanner and, ideally, an all-in-one vulnerability scanner such as Nexpose or LanGuard. Also, given the fact that many storage servers have built-in web servers, you can use such tools as Acunetix Web Vulnerability Scanner and Netsparker to uncover web-based flaws. You can use these vulnerability scanners to gain good insight into areas that need further inspection, such as weak authentication, unpatched operating systems, and cross-site scripting.
You can also perform basic file permission and share scans (as outlined in Chapter 12) in conjunction with a text search tool to uncover sensitive information that no one on the network should have access to. Digging down further, a quick means for finding open network shares is to use SoftPerfect Network Scanner’s share scanning capabilities, as shown in Figure 16-3.

FIGURE 16-3: Using SoftPerfect Network Scanner to search for network shares.
As you can see in Figure 16-3, Network Scanner enables you to perform a security and security permission scan for all devices or simply folders. I recommend selecting Specific Account in the Authentication section and then clicking Manage so that you can enter a domain account for the network that has general user permissions. This technique provides a good level of access to determine which shares are accessible.
When Network Scanner completes its scan, the shares showing Everyone in the Shared Folder Security column are the shares that need attention. I rarely complete a security assessment without coming across such shares open to the Windows Everyone group. Just as common is seeing the directories and files within these shares that are accessible to any logged-in Windows user to open, modify, delete, and do whatever else they please. How’s that for accountability?
Rooting out sensitive text in network files
When you find open network shares, scan for sensitive information stored in files such as .pdf, .docx, and .xlsx files. The process is as simple as using a text search utility such as FileLocator Pro. Alternatively, you can use Windows Explorer or the find command in Linux to scan for sensitive information, but that process is too slow and cumbersome for my liking.
You'll be amazed by what you come across stored insecurely on users’ desktops, server shares, and more, such as the following:
- Employee health records
- Customer credit card numbers
- Corporate financial reports
- Source code
- Master database files
The sky’s the limit. Such sensitive information should be protected by good business practices, and it’s also governed by state, federal, and international regulations, so make sure that you find it and secure it.
- DOB (for dates of birth)
- SSN (for Social Security numbers)
- License (for driver’s-license information)
- Credit or CCV (for credit-card numbers)
The possibilities for information exposure are endless. Start with the basics, and peek only into common files that you know may have some juicy info in them. Limiting your search to these files will save you a ton of time:
-
.txt -
.docand.docx -
.rtf -
.xlsand.xlsx -
.pdf
Figure 16-4 shows a basic text search with FileLocator Pro. Notice the files located on different parts of the server.
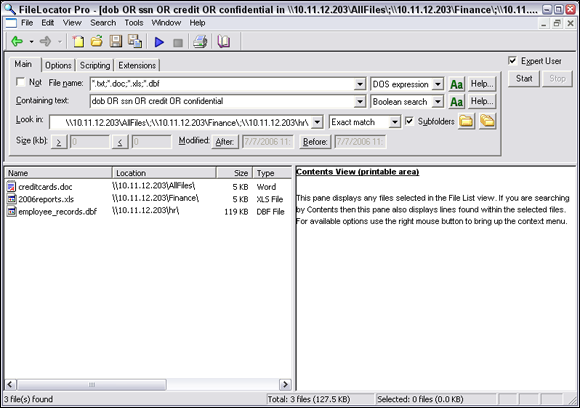
FIGURE 16-4: Using FileLocator Pro to search for sensitive text on unprotected shares.
FileLocator Pro can also search for content inside .pdf files to uncover sensitive data.
To speed the process, use Spirion's Sensitive Data Manager (https://www.spirion.com). This product, formerly known as IdentityFinder and since rolled into the company’s enterprise data discovery platform, is a neat tool designed for scanning storage devices for sensitive, personally identifiable information. It can also search inside binary files such as PDFs.
For a second round of testing, you could perform your searches while logged in as an administrator. You’re likely to find a lot of sensitive information scattered about. It might seem worthless at first, but it can highlight sensitive information stored in places where it shouldn’t be or that network administrators shouldn’t be able to access.
Following Best Practices for Minimizing Storage Security Risks
Like database security, storage security isn’t brain surgery. Keeping your storage systems secure is simple, too, if you do the following things:
- Check the underlying operating systems for security vulnerabilities. I cover operating system exploits for Windows and Linux in chapters 12 and 13.
- Ensure that your network storage (SAN and NAS systems) falls within the scope of patching and system hardening.
- Require strong passwords on every storage management interface.
- Use appropriate file and share permissions to keep prying eyes away.
- Educate your users on where to store sensitive information and the risks of mishandling it.
- Deidentify any sensitive production data before it’s used in development or quality assurance, using tools made for this purpose.
- Use a network access control lists or a firewall, such as those available from Fortinet (
https://www.fortinet.com) or WatchGuard Technologies (https://www.watchguard.com) to ensure that only the people and systems with a business need to access your storage environment can do so — and do nothing more.

 I can’t tell you how often I find sensitive production data, such as credit card and Social Security numbers, being used in test databases that are wide open to abuse by curious insiders or even external attackers who have made their way into the network. Using sensitive production data in the uncontrolled areas of the network such as sales, software development, and quality assurance is a data breach waiting to happen.
I can’t tell you how often I find sensitive production data, such as credit card and Social Security numbers, being used in test databases that are wide open to abuse by curious insiders or even external attackers who have made their way into the network. Using sensitive production data in the uncontrolled areas of the network such as sales, software development, and quality assurance is a data breach waiting to happen. If you have Oracle in your environment, Pete Finnigan has a great list of Oracle-centric security tools at
If you have Oracle in your environment, Pete Finnigan has a great list of Oracle-centric security tools at  Don’t forget about your mobile devices when seeking sensitive, unprotected information. Everything from laptops to USB drives to external hard drives is fair game to the bad guys. A misplaced or stolen system can create a costly data breach. The same can be said for cloud-based file sharing services such as OneDrive and Sharefile.
Don’t forget about your mobile devices when seeking sensitive, unprotected information. Everything from laptops to USB drives to external hard drives is fair game to the bad guys. A misplaced or stolen system can create a costly data breach. The same can be said for cloud-based file sharing services such as OneDrive and Sharefile.