

Setting up an IBM Cloud Object Storage Object Store
IBM Cloud Object Storage is a highly scalable cloud storage service that is designed for high durability, resiliency, and security. The TS7700 can be enabled to use IBM Cloud Object Storage as a Cloud Storage Tier.
This chapter explains how to set up your IBM Cloud Object Storage so that it can be used by the IBM TS7700C and includes the following topics:
7.1 TS7700 interaction with IBM Cloud Object Storage
A TS7700 that is enabled to use Cloud Storage Tier must connect to a previously installed cloud object store. For the IBM Cloud Object Storage case, the user must obtain the following elements to complete the TS7700 configuration process:
•The URL of the IBM Cloud Object Storage system in the form of a web address, which includes the indication of the access web protocol (http or https) and the numeric static IP address that is associated to the service (for example, https://192.168.100.210).
•The name of the vault to be used to store TS7700 virtual volumes. The vault is referred to by the TS7700 as a cloud container.
•Authentication credentials. An account should be created in the IBM Cloud Object Storage system that owns storage resources to be used by the TS7700. To access such resources, the TS7700 uses the Access Management (IAM) method, which requires the following credentials to be supplied instead of the traditional user name plus password:
– Access key ID
– Secret access key
IBM Cloud Object Storage is presented in on-premises or off-premises (public) offering types. For the TS7700 at R4.2 code level, only on-premise IBM Cloud Object Storage is supported.
This chapter describes the following basic management procedures for the IBM Cloud Object Storage system, which are related to TS7700 requirements:
•Creating a IBM Cloud Object Storage vault (as a custom vault or originating from a template) and configuring its corresponding properties.
•Generating IAM authentication credentials to access the vault.
IBM Cloud Object Storage is a dispersed storage mechanism that use a cluster of storages nodes to store pieces of the data across the available nodes. IBM Cloud Object Storage uses an Information Dispersal Algorithm (IDA) to divide files into unrecognizable slices that are then distributed to the storage nodes. No single node contains all of the data, which makes it safe and less susceptible to data breaches while also needing only a subset of the storage nodes to be available to fully retrieve stored data. This ability to reassemble all the data from a subset of the chunks dramatically increases the tolerance to node and disk failures (IBM, 2017).
The IBM Cloud Object Storage architecture is composed of the following three functional components:
•IBM Cloud Object Storage Manager: This component provides an out-of-band management interface that is used for administrative tasks, such as system configuration, storage provisioning, and monitoring the health and performance of the system.
•IBM Cloud Object Storage Accesser: This component imports and reads data, encrypts and encodes data on import, and decrypts and decodes data on read. It is a stateless component that presents the storage interfaces to the client applications and transforms data by using an IDA.
•IBM Cloud Object Storage Slicestor®: This node is primarily responsible for storage of the data slices. It receives data from the Accesser on import and returns data to the Accesser as required by reads.
Consider the following key concepts for IBM Cloud Object Storage:
•Device sets
IBM Cloud Object Storage uses the concept of device sets to group Slicestor devices. Each device set consists of the “width” number of Slicestor devices. Device sets can be spread across one or multiple data centers and regions.
•Storage pool
A set of one or more device sets. Storage pools can be spread across one or multiple data centers and regions as they consist of one or many device sets
•Vaults
Logical storage containers for data objects that are contained in a storage pool.
•Width
The width of a vault or storage pool is the number of Slicestor devices that the data is striped across for a vault or storage pool. For example, a storage pool that has 30 storage devices is a 30-wide storage pool. As the storage pool grows, device sets of 30 more devices are added; however, the width of the storage pool remains at 30. The maximum vault width can be set to a value up to the size of the storage pool in which is it contained.
•Vault Threshold
The threshold of an IBM Cloud Object Storage system is the number of devices that must be available for the data to be transparently readable to the user. For example, a 30-wide vault system with a threshold of 18 means that any 18 of the devices must be up for the data to be readable. Conversely, 12 of the 30 devices can be down or unavailable without affecting data accessibility.
The TS7700 interacts with IBM Cloud Object Storage through the credential records in IBM Cloud Object Storage to grant access to VAULTs. It is out of the scope of this document to describe the procedure to install and configure the IBM Cloud Object Storage offering. For the topics that are covered here, it is assumed that the IBM Cloud Object Storage is fully available and storage pools were prepared in advance to allocate vaults for usage of TS770 storage of virtual volumes.
A storage pool is defined by a logical grouping of Slicestor devices that are used to store vault data. A vault is initially created on a storage pool and can be expanded by using an existing storage pool or by creating a storage pool.
|
Note: A Slicestor device can be assigned to one storage pool only. Likewise, a storage pool can be created from unassigned devices only. After it is created, a storage pool cannot be expanded; however, more pools can be created and merged to expand a vault.
|
7.2 Creating an IBM Cloud Object Storage vault
A vault is created inside of a storage pool. Consider the following rules:
•Storage pools must be defined before vault creation. If pools are not defined, vault creation is redirected to the Create Storage Pool page.
•Multiple vaults can be created on a storage pool.
•Each pool can only be used by a single vault type.
The following types of vaults can be created:
•Management vaults retain statistics data that is generated within the system.
•Standard vaults are used to store user data. This type of vault must be paired to a TS7700 cloud container.
•Container vaults are used when the system is in container mode. Containers are created in container vaults. User data is stored within containers.
•Service vaults are needed when the system is operating in container mode. The service vault is used internally by the system to store container metadata, storage accounts, and access keys.
A system can contain a limited number of vaults. Standard and container vaults count against this limit, but management and service vaults do not. The maximum number of vaults is limited to 1000 by default. When the limit is reached, standard vault creation requests are rejected.
Standard vaults can be created after the system is set up and a storage pool is available. To use Standard vaults, the system must be operating in vault mode.
|
Note: As part of the planning phase, a determination must be made about the vault width and threshold (for more information about these settings, see “Creating a custom vault” on page 41). These decisions affect the availability, resiliency, performance, and storage capacity of the vault. These settings should be used to adjust the characteristics of each vault as wanted for the specific application.
|
Vaults can be created by using the following methods:
•Customizing a configuration
•Using a vault template
7.3 Creating a custom vault
The TS7700 requires a vault to be used as a container. Complete the following steps:
1. Open the Cloud Object Storage Manager web site of the corresponding on-premises IBM Cloud Object Storage. Select the Configure tab, click Create Vault in the Summary section, or right-click any item in the navigation tree (see Figure 7-1).

Figure 7-1 Create Vault option in the Configure panel
2. If storage pools were created in advance, the Create New Standard Vault page opens (storage vaults are inside storage pools). Select Custom Vault From Storage pool (see Figure 7-2) for the target pool and then, click Continue.

Figure 7-2 Selecting a method to create a new standard vault
3. In the General section (see Figure 7-3 on page 42), the following settings are available:
– Name: Each vault must be uniquely named. The IBM Cloud Object Storage Manager use this name for all references to this vault. Consider the following rules:
• Container names must be 3 - 63 characters long.
• Container names must not contain uppercase characters, underscores, or periods (“.”).
– Description: Optional free-form description of the vault.
– Tags: Optional labels can be created and or assigned to a vault before the vault is created.

Figure 7-3 Creating standard vault
– The following options can be available in this panel, depending on the configuration of the IBM Cloud Object Storage or the IBM Cloud Object Storage storage pool where the vault is stored:
• Provisioning code: During the container creation process, specify a unique provisioning code to indicate in which container vault the container should be created. The default value is the vault name, after it is entered. The value often is the locationConstraint or region. If the provisioning code is not set, containers can be created in this new container vault if it is configured as the default container vault for an access pool.
• Region (Optional): A region can be provided to indicate where the contents of this vault is stored. The locationConstraint parameter, which is shown for containers that are associated with this vault in the S3 GET Service Extended and S3 GET Bucket Location APIs, are populated with the value set for region.
• Storage class: This setting is optional setting, is used for the IBM Cloud Object Storage, and differs from the construct policy type that is used for the TS7700. It is provided to assign a classification to all objects that are stored within this vault. The header x-amz-storage-class is shown in the S3 GET/HEAD Object and the StorageClass in the response body of the S3 GET Bucket are populated with the value set for storage class.
4. Several options are displayed in the Configuration section. When the width of the pool for this vault is greater than 6, complete the following fields:
– Width: The width of the vault corresponds to the number of slices into which all data in the vault is split. Vault width must be a factor of the storage pool width. The Manager Web Interface allows any vault width that is greater than or equal to 6 and less than or equal to 60.
– Threshold: The minimum number of slices that must be available to perform a read:
• Pre-defined, supported thresholds are presented when the drop-down list is clicked. The vault threshold (which is always less than the width) determines the reliability of the vault. If the set of available Slicestor devices is such that the number of slices falls below this threshold, the vault content cannot be read, and the vault appears as red in the Monitor application.
• The Manager Web Interface allows any value between 1 and Vault Width, inclusive.
• If the vault is on a storage pool that spans multiple sites, the Manager Web Interface warns the user if the selected threshold is high enough such that a single site outage affects read and write availability.
– Write threshold: The Manager Web Interface allows any value if the following conditions are met:
• Write Threshold > Threshold (Write Threshold = Threshold is allowed if Threshold = Vault Width or if Vault Width < 6).
• Write Threshold <= Vault Width.
• Write Threshold + Threshold) > Vault Width.
• Write Threshold defaults to Threshold + 2, if that is within the allowed range. Otherwise, the selected Write Threshold is the halfway point between the minimum allowed Write Threshold and Vault Width, rounded up. This value is selected by default in the Write Threshold drop-down when Threshold is selected. This value is also used as the Write Threshold when a vault is created through the Manager REST API and a Write Threshold is not specified.
• If the vault is on a storage pool that spans multiple sites, the Manager Web Interface warns the user if the selected write threshold is high enough such that a single site outage affects write availability.
– Alert level: Optional setting. If the set of available Slicestor devices is such that the number of slices is between the write threshold and the alert level exclusive, the vault icon is yellow in the Monitor application. In this case, the vault is still fully functional (see Figure 7-4).

Figure 7-4 Create new standard vault (Configuration section)
– When the width of the pool for the vault is 7, you also should be able to select a vault optimization to create a Concentrated Dispersal vault. This option is available only if the parent storage pool also was configured for Concentrated Dispersal. In this mode, each Slicestor device can be responsible for multiple slices of a object that is stored in the system instead of only one (when you choose a vault optimization, it cannot be changed later). Consider the following settings:
• Storage efficiency: Width value of 7. This setting provides more usable capacity with reasonable performance.
• Performance: Width value of 3 - 6 (better performance with less usable capacity).
5. Select a protection setting for the vault to be created (if applicable), as shown in Figure 7-5.

Figure 7-5 Enabling vault protection for the IBM Cloud Object Storage system
When a vault is created, the Protection section (see Figure 7-6) displays only if the Vault Protection Configuration options was enabled from the Configure tab. It allows objects that are stored in vaults to include associated deletion protection, where protected objects cannot be deleted until the associated data retention duration expires, and all legal holds associated with the object are removed. Consider the following settings:
– Disabled: The vault to be created does not include a protection levelRetention set; therefore, the remaining fields are not shown.
|
Note: This option is selected for TS7700 that is running R4.2.
|
– Retention: This option is not supported for TS7700 machines at R4.2 code level (see Figure 7-6). This option means that data is retained for a default duration of time unless you specify a custom duration. After you create the vault, you can modify the retention time settings, but you cannot change the protection level. In the Data Retention Durations section, specify the following values or accept the default values:
• Default Duration: The default retention period (in days) for an object in this vault. The minimum supported value is 0 days, and the maximum is 36159 days. The default value is 730 days.
• Minimum Duration: The minimum retention period (in days) for an object in this vault. The minimum supported value is 0 days, and the maximum is 36159 days. The default value is 365 days.
• Maximum Duration: The maximum retention period (in days) for an object in this vault. The minimum supported value is 0 days, and the maximum is 36159 days. The default value is 7305 days.
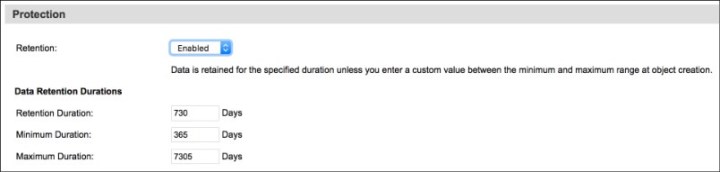
Figure 7-6 Create new standard vault (“Protection” section)
6. In the Options section (see Figure 7-7 on page 45), complete the following fields:
– Enable SecureSlice Technology: This optional setting provides extra encryption benefits that are combined with dispersal. This option is selected by default for new vaults. The feature can be deactivated, although it is not recommended. If it is cleared, a warning message appears, and a confirmation is needed before proceeding. After the vault is created, the SecureSlice option cannot be modified.
– Enable Versioning: Do not check this option for TS7700 vaults. It enables versioning on the vault and the TS7700 does not support a method to expire previously deleted objects. Therefore, to prevent the vault from expanding in capacity indefinitely, do not enable versioning.
– Delete Restricted: Because TS7700 needs full access to stores objects do not use this feature, which allows Security Officers to restrict vault access permissions such that users with write access to the vault are not able to delete objects from the vault.
Also, object versioning is enabled in parallel to this feature, which is not fully supported by the TS7700.
– Enable Server-Side Encryption with Customer-Provided Keys (SSE-C): Do not select this option when vaults are created that are intended for TS7700 (support pending to be implemented). In IBM Cloud Object Storage, all stored objects are encrypted by default by using randomly generated keys and an all-or-nothing-transform.
The default encryption model provides at-rest security, and this feature allows some workloads to possess the encryption keys that are used. Requests to read or write objects or their metadata send the required encryption information (customer-managed keys) as headers in HTTP requests.
– Restrictive Access Control: This setting restricts reads, metadata writes, and access control to only the owner of the object on protected vaults (this setting cannot be modified after the vault is created).

Figure 7-7 Creating standard vault
7. In the Quotas section (see Figure 7-8), complete the following optional fields, if needed:
– Soft Quota: A notification is sent to the Event Console if the soft quota setting is exceeded. It does not cause restrictions to usage. Setting the quota higher than the total space available in one or more storage pools that are associated with this vault has no effect.
– Hard Quota: The Accesser device (or application) does not permit the user to exceed the hard quota value for this vault. A notification is also sent to the Event Console if the hard quota setting is exceeded. Setting the quota higher than the total space available in one or more storage pools that are associated with this vault has no effect.

Figure 7-8 Create new standard vault (“Quotas” section)
8. In the Advanced Index Settings section (see Figure 7-9), the Name Index Enabled is selected by default for Standard vaults and you can enable Recovery Listing. Consider the following options:
– Name Index Enabled: This option is enabled by default to allow a user to list the contents of a vault in lexicographical order based on the object’s name or key. The Name Index is updated whenever objects are added or removed from a vault. The Name Index must be enabled to provide prefix-based listing and sorted listing results for named object vaults. To accommodate TS7700 future cloud salvage recovery procedures, it is highly recommended that this option is enabled.
– Recovery Listing Enabled: This option enables limited listing capability, even when the contents of a vault are not indexed. When enabled, Recovery Listing lists the SourceNames of the metadata headers. Recovery Listing is slower than the Name Index listing and the results are not sorted. Recovery Listing can be used to list the contents of a vault for which Name Index is corrupted or not enabled. If Name Index Enabled is not used, this option is required at a minimum for TS7700 use.

Figure 7-9 Creating standard vault
9. Click Save.
The new vault is shown in the Vault Summary page, as shown in Figure 7-10.

Figure 7-10 Showing Vault Summary
10. Click the vault and adjust the following properties as needed (see Figure 7-11):
– Deployment: A vault must be deployed to be visible by an Accesser pool. Available Access Pools are shown, and their view can be expanded to show their assigned devices. Click Change to open the Deployment menu. The Accesser registry update (and Vault availability) can take up to 5 minutes.
– Access control: For added data security, the Vault access can be restricted to specific IP addresses.
– Authorized users: Access permissions must be granted for each object vault. Extend proper authorization for TS7700 cloud accounts that must access created vaults.

Figure 7-11 Adjusting other vault properties
7.4 Using vault templates
An alternative approach to vault creation is based on the use of vault templates. These templates allow a user to create multiple vaults with the same parameters quickly and enable common vault configurations to be used across multiple users.
Your IBM Cloud Object Storage administrator might create a vault template on your behalf, which makes the process of creating TS7700-based vaults much easier. A vault template is created on a storage pool and can then be used when a vault is created. All parameters that are set in the vault template apply to the vault.
7.4.1 Creating vault templates
Complete the following steps to create a vault template:
1. Open the Cloud Object Storage Manager web site of the corresponding on-premises IBM Cloud Object Storage. Click the Configure tab (see Figure 7-12) and then, click the storage pool for which you want to create a vault template.

Figure 7-12 Selecting a storage pool to create a vault template

Figure 7-13 Creating a vault template from a storage pool
3. Configure the template according to the target use case (see Figure 7-14). The allowed values of fields to fill for vault templates are the same as those fields that are described in the Cloud Object Storage creation of a custom vault procedure.

Figure 7-14 Configuring settings for a new vault template
4. When complete, click Save.
7.4.2 Creating a vault by using a template
Complete the following steps to create a vault by using a template:
1. Open the Cloud Object Storage Manager web site of the corresponding on-premises IBM Cloud Object Storage. Click the Configure tab and then, click the storage pool for which you want to create a vault. Available options are listed under the Vault Templates section of that page (see Figure 7-15 on page 50).

Figure 7-15 Locating vault templates available to a storage pool
2. Click Create Vault next to the template to be used. At this point, the new vault needs a unique name assigned to it. The newly created vault inherits the SecureSlice state (enabled or disabled) from the Vault Template. It cannot be changed for the vault after it is created (see Figure 7-16).

Figure 7-16 Creating a vault by using a template

Figure 7-17 Displaying available vaults
7.5 Granting access key authentication
Access Key Authentication enables the generation of AWS-style credentials for user accounts. These credentials can be used to perform AWS authentication for S3 requests. As of release 4.2, this method must be used to be compatible with the TS7700.
Complete the following steps:
1. Open the Cloud Object Storage Manager web site of the corresponding on-premises IBM Cloud Object Storage. Click Security → Enable/Disable Authentication Mechanisms (see Figure 7-18).

Figure 7-18 Checking configuration of authentication mechanisms
2. Enable Access Key by clicking Configure (see Figure 7-19). The target user account must exist or be created in advance. Accounts that are created while Access Key Authentication is enabled (which is the required authentication method for TS7700 access) no longer require a username and password to be set (but remains as a valid option). Be careful if the Hide secret access keys option is selected because keys are shown during creation time only (they cannot be recovered later); therefore, so copy them to a safe location.

Figure 7-19 Enabling or disabling authentication mechanisms
3. Complete the following steps to set up Access Key Authentication:

Figure 7-20 Displaying IBM Cloud Object Storage user accounts
b. Create access keys for the target account. Select Change Keys to create access keys, as shown in Figure 7-21.

Figure 7-21 Changing access keys for selected user
c. Click Generate New Access Key to create corresponding credentials. A maximum of 10 different access keys can be created (see Figure 7-22).

Figure 7-22 Generating new access keys
Generated Access Key ID and Secret Access Key are required when Cloud Account access is configured in the TS7700 (see Figure 7-23).

Figure 7-23 Displaying access keys
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
