3.2. Mobile NAC
The purpose of Mobile NAC is to protect mobile devices as they are mobile. In doing so, Mobile NAC indirectly helps protect the corporate LAN. If mobile devices aren't allowed to get into a noncompliant state while mobile, or if they are restricted when noncompliant to where they can't get themselves into more trouble, then they'll be in good shape when they finally do try to come back to the LAN.
Why do enterprises care so much about protecting their corporate LAN? That's where the data is, and that's where people work. Systems need to remain up and running, data needs to be secure, and systems and people need to be productive. If these elements became jeopardized, it could affect the bottom line and the business would suffer.
LAN-based NAC is designed to protect the corporate LAN so that everything can remain secure and productive. In fact, LAN-based NAC is only one technology that is designed to do so. As mentioned, firewalls and intrusion-detection equipment are also in place. It is not uncommon for millions of dollars to be spent protecting the corporate LAN for all of the aforementioned reasons.
Here's an interesting fact: 60 percent of all corporate data assets reside unprotected on PCs (according to Search Security Newsletter). Also, workers are now routinely working from many different places outside the four walls of the physical corporate office space. It is imperative that these workers' devices be operational, or the bottom line and the business could suffer. So, are companies also spending millions of dollars to protect their mobile devices, and are they implementing Mobile NAC?
The answer is that the smart ones are. Mobility adds a tremendous risk to the enterprise, and it is something that cannot be ignored. LAN-based NAC serves a good purpose, and companies should consider it a useful technology. They also need to use LAN-based NAC to protect their LAN from mobile users as they remotely access the network. The key is that Mobile NAC also needs to be used to cover the mobile devices as they are mobile.
3.2.1. Dangers of Mobility
Chapters 4 and 5 cover specific attacks and defines specific reasons on why each NAC-type is needed, including Mobile NAC.
3.2.2. Sedentary Desktop
So, walking through the cubical farms with all the desktop computers, would they benefit from Mobile NAC? The first response might be "no," that Mobile NAC is for mobile devices. While it is true that mobile devices reap the most outwardly understandable benefits of Mobile NAC, I actually know of a few companies that are using a Mobile NAC solution inside of their corporate LAN. Keep in mind, NAC solutions provide a number of different functions, including assessment, restriction, remediation, and so on.
One company in particular is using a Mobile NAC solution to provide the remediation capabilities. The remediation component being utilized provides a mechanism to push Microsoft patches to systems wherever they may be located when they need the patch. It just so happens that a good number of these machines are located on the corporate LAN and are sedentary desktops!
3.2.3. Laptops Used on and off the LAN
These types of devices are where Mobile NAC shines. With all that data being on those laptops, and those laptops needing to be in top working order, Mobile NAC is a strong fit for many organizations. Not to mention, these devices will come back to the corporate LAN and connect physically. They cannot afford to be in a noncompliant state while they are mobile.
Let's look at a few graphical representations of how Mobile NAC helps with these devices, as compared to LAN-based NAC. Figures 3-1 and 3-2 show this comparison.
Figure 3-1. LAN-based NAC topology

Figure 3-2. Agent-based mobile NAC topology
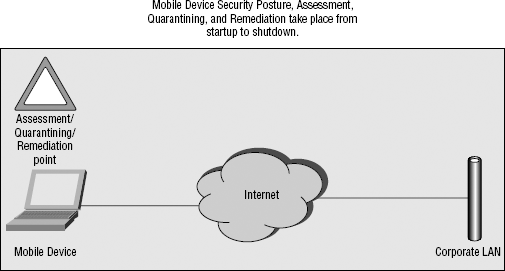
The key differences here are the point where the assessment, quarantining, and remediation take place. With LAN-based NAC, these functions take place when the mobile device returns physically to the corporate LAN, or attempts to remotely access the corporate LAN via VPN. With Mobile NAC, these functions take place any time the device is powered-on. Clearly, that extends the protection to mobile device.
So, what types of restrictions and actions can take place on these mobile devices if they become noncompliant? A complete list will be shown in Chapter 8, but here's a quick overview:
Layer 7 restriction of applications, such as Internet Explorer, the IPSec or SSL VPN client, e-mail programs, and so on.
Layer 3 restriction, where the device can only access specific subnets, preferably only subnets that contain servers to fix any security deficiency.
Automatically restart security applications, such as the personal firewall and antivirus application, if they become disabled.
Clearly, performing these types of functions on these devices provides much more security than doing nothing for them. A device that is noncompliant should be restricted and fixed, too.
3.2.4. Mobile-Only Laptops
Here's another great area where Mobile NAC is useful. These devices never reach a point where a LAN-based solution would be able to perform any NAC function on them. Consequently, they are allowed to perform whatever functions they want, their security posture could be completely noncompliant, and they are never under any restriction — the ultimate Mobile Blindspot!
Let's take a particular focus on patching. To me, patching includes the typical Microsoft Patch Tuesday (the first Tuesday of every month) items (OS patches, Internet Explorer Patches, MS Office patches), as well as antivirus and antispyware updates. Every computer needs these types of updates, especially ones that don't receive the inherent protection from the security equipment on the corporate LAN.
Every company I talk to has a means to push patches to their LAN-based systems. Some common technologies would be the following:
Even with these patch technologies in place, I've spoken with enterprises that still don't have a great feeling that their LAN-based systems are completely up to date. Part of that has to do with reporting deficiencies (where they can't prove exactly who is patched), and some of it has to do with the fact that patching is just not that easy to do. Many enterprises I've spoken with actually have a hard time determining how many computer systems they actually have. Throw in the extra challenge of mobile systems, and it becomes a mess.
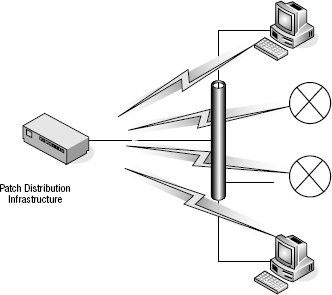
Figure 3-3 shows how typical LAN-based patching solutions operate. It's pretty simple: You decide to push a patch, press a few buttons, and the systems get the patch.
This is all good and fine, but what happens when a mobile system doesn't happen to be on the LAN? They don't get the push, as shown in Figure 3-4.
This seems simple, and it really is, although a lot of companies don't have another way to push patches to the mobile systems when they are mobile. Some ignore the problem and pretend it doesn't open them up to vulnerabilities. Chapters 4 and 5 will disprove that line of thinking! For companies truly looking for a solution, Mobile NAC is a viable option.
Figure 3-3. Operation of typical LAN-based patching solutions

Figure 3-4. Mobile system not on a LAN
3.2.5. Employee-Owned Home Computers
Frequently, I get asked if Mobile NAC is a good option for employee-owned home computers that are used to give gain access to the corporate LAN. The answer is "yes," as Mobile NAC can help, but there are pros and cons.
3.2.5.1. Pros
The following are the pros to this solution:
The employee-owned machine can be thoroughly assessed prior to allowing VPN access.
The machine can be brought up to snuff, to allow the access.
Enterprises can accurately report on all systems accessing their LAN.
3.2.5.2. Cons
Following are the cons to this solution:
Any time the enterprise installs software on a home system, it is responsible for supporting that software and the home system.
There can be additional license fees for the home systems.
Ultimately, the decision is up to the enterprise based upon these points. If it does go with Mobile NAC, then it would no longer just give VPN clients to every home user, it would also need to give the Mobile NAC client.
NOTE
Don't forget about using SSL VPN for employee-owned systems.
3.2.6. Unknown Devices
In regard to Mobile NAC, contractor, vendor, and other unknown devices are similar to the employee-owned home systems. You could potentially put Mobile NAC software onto them, but it may not be the best solution. Here's an interesting Catch 22:
If the plan is to put Mobile NAC software onto unknown devices and require that it be installed to allow access to the LAN, then you would want to have a technical means to enforce that it was installed. If that technical means could check to see if that software was installed, it would have a good chance of checking for other security items, thus negating the need to have a second solution, Mobile NAC, installed in the first place.
Again, the decision is ultimately up to each enterprise.
3.2.7. PDAs and Other Devices
This one is pretty easy. I am not aware of any Mobile NAC solutions that support PDAs and those types of solutions, so it's not really an option to load onto them. However, it doesn't just end there....
Figure 3-5. Devices that can carry data out of an organization

As stated earlier, the biggest threat to enterprises has to do with protecting and controlling its data. A big vulnerability in doing so has to do with PDAs and other devices connecting to laptops. Whether data is synched or intentionally and manually copied over, these devices are a conduit out for corporate data. Figure 3-5 gives a visual representation of devices that can carry data out of an organization.
Mobile NAC can help by doing a couple of things. First, it can restrict these types of devices from ever connecting to a mobile laptop. It can also prohibit data from being copied over to these types of devices. That's rather powerful technology to protect the biggest vulnerability that enterprises have.
