4.4. Intentional LAN-Based Threats
So far, you've seen how unintentional threats can cause problems on a LAN. Although these users are utilizing their systems with the most honorable of intentions, they can still cause problems from the simple act of them connecting to the LAN. The next set of threats operate under a completely different set of assumptions.
Intentional LAN-based threats involve malicious actions knowingly and consciously taking place on the LAN. These threats are not accidental; they are purposeful. The method of attack relies upon establishing LAN connectivity to establish the attack. This connectivity can be established a number of different ways:
A contractor, business partner, or the like is given authorization and instructions to connect to the LAN, although they use that access to perform unauthorized and malicious acts.
An outsider is allowed physical access inside the office, although they are not authorized to connect to the LAN (such as a sales guy — physical security important), and use someone else's system by walking up to it.
An outsider isn't authorized to physically enter the space or gain access to the LAN.
An outsider takes advantage of non-Ethernet connectivity to gain access (Wi-Fi, remote dial war dial).
All of these means to establish connectivity are important because they share a common trait. They all bypass the firewalls and other technologies put in place to protect the LAN from outsiders on the Internet. Bypassing these systems leaves them free to perform their attacks from the inside. Figure 4-12 shows a graphical representation of this threat.
Once connected to the LAN from the inside, they can perform a slew of malicious attacks. These attacks would go unnoticed from the traditional lines of defense and include such acts as the following:
Sniffing application and file data being transferred across the LAN
Sniffing usernames and passwords on the LAN
Figure 4-12. Bypassing the technologies designed to protect the LAN

Attacking servers and workstations to affect the confidentiality and integrity of data
Attacking the infrastructure and affecting the availability of systems
There are certainly ways in which LAN-based NAC (and other systems, for that matter) can help protect against these types of threats. In order to know how to protect against these scenarios, it is critical to understand how the LAN can be exploited.
4.4.1. Exploitation by Authorized Access and Malicious Use
This first scenario uses the case of a contractor. This contractor has been hired by a company to come in and perform some programming tasks. To perform these tasks, he has been given authorization to connect to the LAN for Internet connectivity. This company informs the contractor that it is very stringent about its security policies, and it takes great pride in its security efforts. The contractor is even given a document that outlines the actions he can and cannot perform while working at the company. For example, he is not allowed to try to access pornographic and gambling web sites.
When the contractor arrives the first day, he is given access and shown to his work area. The contractor gets to work and all appears to be well. What the company doesn't realize is that the contractor is going to take advantage of this access in an attempt to exploit the company.
Since the contractor doesn't want any of his actions to be traced back to him, he is going to be rather passive about his attacks. He is going to perform the passive acts of sniffing data and usernames and passwords on the LAN. While this can yield him some very useful information, the likelihood of him getting caught is extremely low, barring someone sneaking up on him and viewing what is on his screen.
Sniffing is the act of literally viewing data as it is flowing across a network. The data is sent in packets, and often, this data is sent in the clear. By analyzing the packets, the data can be viewed. As you can imagine, companies have tons of sensitive information floating across their LANs. Figure 4-13 shows how sniffing takes place.
The sniffing that takes place is done passively. This means the data is not modified in transit; it is simply just looked at as it goes by. Think of it as a semi on a highway. The semi may pass you on the highway, and you may read an advertisement or other information on the side of the trailer. This information isn't hidden, and by looking at it, you aren't affecting it passing by you.
Sniffing is done using special applications. These applications serve a multitude of purposes, many of them very legitimate. They can analyze network behavior, applications, and so on and are truly invaluable tools. Personally, I use sniffers all the time. I do use them for legitimately looking at network traffic and for analyzing applications, although I also use them to show people how their data can be illegitimately sniffed. Let's take a look at this.
Figure 4-13. Sniffing

In the case of the contractor, he used the very well-known sniffer Wireshark. Wireshark used to be called Ethereal, for those of you who may have been familiar with that tool in the past. In short, Wireshark rocks! When I am asked to name my number one favorite hacking tool, I say it is Wireshark. This sometime surprises people, because they expect it to be some fancy exploit tool, but there is just so much information that can be gathered by watching traffic as it goes by.
So, the contractor was on the LAN, and he started Wireshark to sniff the traffic. Figure 4-14 shows Wireshark actively sniffing packets.
The contractor allowed Wireshark to run for quite some time. This was easy to do. He simply let the application run on his machine while he performed his legitimate programming duties. All the time, the sniffer was gathering traffic information. In fact, the contractor didn't even bother to look at what he had gathered until he went home for the night. Once he was home, he decided to analyze the packets he had received. The first thing he did was run a search against the packets to see if he could find anything interesting. In this case, he searched for the word "mail," as shown in Figure 4-15.
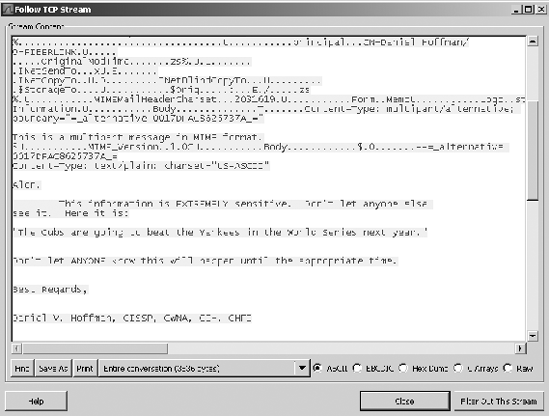
In looking at Figure 4-15, you should notice a few things. First, the word "mail" was found in the 15th packet that was sniffed. The bottom portion of the application shows what that packet actually contains. If you look along the right column of data, you can actually see information such as to whom the e-mail is being sent and the subject line. This is an easy way to find data, but it isn't the easiest way to read it. With Wireshark, the contractor could simply right-click on packet 15, choose "Follow TCP Stream," and the data would be presented in a much easier-to-read format. Figure 4-16 shows the available options when a user right-clicks on a packet, while Figure 4-17 shows the e-mail in the easier-to-read format.
Figure 4-14. Wireshark actively sniffing packets

Just that easily, the contractor can view an e-mail message that was sent on the network. Of course, he isn't limited to only e-mail messages. He can view IM applications, files being transferred, and so on. There are a number of tools available that will sniff LANs for specific types of information. Some of these applications include the following:
Figure 4-15. Search taking place

NOTE
Some of you may be thinking about switched networks and the use of SSL. Switched networks can still be sniffed using Address Resolution Protocol (ARP) poisoning, and SSL can be exploited by performing SSL Man-in-the Middle attacks. Showing these procedures in this book would be a bit out of scope, though they are shown in detail in my book Blackjacking: Security Threats to Blackberry Devices, PDAs, and Cell Phones in the Enterprise (Wiley, 2007).
In addition to sniffing messages and other types of application data, the contractor could try sniffing domain usernames and passwords. This information could prove to be the most valuable. If he could get his hands on an actual user's credentials, he could use those to log in to systems on the LAN, access e-mail, access the LAN remotely, and so on.
Figure 4-16. Available options when a user right-clicks on a packet

Another great tool of which to be aware is called CAIN. CAIN is an extraordinarily useful tool that can be considered like a hacking Swiss Army knife. It performs a ton of different functions in one handy little tool. The ARP poisoning mentioned previously can actually be done with this tool. From a sniffing perspective, it can sniff out a bunch of different types of credentials, including the following:
Figure 4-17. E-mail in the easier-to-read format
The MS Kerberos credential sniffing is what would be most useful for the contractor. MS Kerberos is what is used by Windows domains. This is what would enable the contractor to sniff actual domain authentications.
Figure 4-18 shows a screenshot of CAIN.
All of this is possible because the contractor is physically located on the LAN. While he was authorized to access the LAN as a contractor, clearly the company who hired him wouldn't want him to perform these types of functions.
NOTE
The administrative step of running a background check on the contractor could have also helped to prevent this from happening. If a company is willing to spend hundreds of thousands of dollars on LAN-based NAC equipment, it would be worth it to spend the minuscule amount to have this step taken. If the contractor is from an agency, the agency can be asked to pay for that expense.
4.4.2. Exploitation by Authorized Physical Access and Unauthorized LAN Access
As a guest of the company, the aforementioned contractor was authorized to physically come into the office space and to connect to the LAN. That doesn't mean that everyone who is granted permission to enter the office space would be allowed access to the LAN. Many people pass through an office and don't have a valid reason to access the LAN, including the following:
Figure 4-18. CAIN

Friends of employees
Relatives of employees
Cleaning and maintenance personnel
Sales people
Business partners
Just because they shouldn't connect to the LAN, doesn't necessarily mean that they couldn't. In practically every office I've ever entered, direct LAN connectivity is only an Ethernet cable away. The only thing stopping this connectivity is an employee who visually notices an unauthorized person connecting. In some companies, that unauthorized person could be caught pretty quickly. In others, the person could literally show up for work every day, and no one would ask any questions.
An important item to remember with these types of users is that they have been given permission to be in the space. Often, other workers will see these people walking and talking with company employees, and seeing that relationship instills a level of trust. They see a stranger talking to a fellow employee, so they believe the person is OK. Another employee may not think twice about them connecting to the LAN.
Needless to say, guests given physical access can connect to the LAN without permission. In doing so, they can sniff data just like the contractor in the previous example. The can also do a heck of a lot more — as could the contractor. Let's take a look at more of these exploits.
4.4.3. Exploitation with Unauthorized Physical Access and Unauthorized LAN Access
I really like the malicious USB drive story I told earlier in this chapter. I like it because it's true and the use of USB drives is common. So is the type of scenario where someone who has no right to even be in the office space is able to gain access. That person could even connect directly to the LAN.
This next story also comes from a well-known expert penetration tester. The tester and his crew were hired to try to find ways in which they could exploit the company that hired them. The crew was able to exploit the company in a matter of minutes. Here's the complex procedure they followed. (Follow each step closely — it gets tricky and quite technical!)
The penetration tester wakes in the morning and drives to the client's office location.
He decided to wear a suit, so that he looks nice, and wearing a suit instills a level of trust.
He probably stops and gets a cup of coffee.
As he approaches the building, he puts his cell phone up to his ear and talks, appearing as though he is having a conversation.
He times his arrival at the locked entrance to coincide with that of authorized employees entering the door.
As the authorized employees use their keycards to enter the door, he motions for them to hold the door open for him.
They do.
He walks into the secured space, still acting as though he is on the phone. That way, no one will bother him.
He walks up to a cubicle that is empty.
The cubicle has a computer that is powered on and has a user logged in.
He now has access to the network with the same rights and privileges as the person who logged in.
He can also use a number of hacking tools that he carries with him on his USB hard drive. These tools can allow him to attack servers, place key-loggers and malware onto the system, and so on.
NOTE
The penetration tester could have disabled the antivirus program and installed a keylogger in less than 1 minute. That keylogger would have captured every key that the user typed, including the username and password. That keystroke information could then be automatically sent to him every day.
Once on the LAN, the penetration tester could have performed the exact actions that the contractor did. The key difference is that that the penetration tester wouldn't necessarily care if his actions were traced or found out about in the future, nor would a hacker who snuck in just for the day. Remember, the contractor only wanted to be passive. Because this was his new job, he would show up every day. There are logs and other mechanisms that could trace malicious acts back to him, so he had to be careful. The penetration tester and the hacker were going to perform their malicious acts and disappear. They could afford to be aggressive in their acts.
Something that would be useful for the penetration tester or hacker to know is what systems on the LAN were vulnerable to exploitation. It's the first logical step in launching an attack:
Find a victim or target.
Enumerate the victim (which means find out as much information as possible about their system).
Run an exploit against the victim to gain access.
Once access is achieved, malicious acts can be executed.
It may be desirable to place a backdoor on the victim system, so that it can be accessed remotely in the future.
Remove any evidence of the attack.
There are many, many tools that could help in these attacks. Hackers and penetration testers will have their favorites. I'll cover two tools now. One will find vulnerable systems, and one will be used to exploit the vulnerable systems.
To find vulnerable systems, let's consider the tool Nessus. Nessus is a very well-known vulnerability scanner. It has very legitimate uses by system administrators and network managers, because it can help them identify vulnerabilities on their networks. As with just about any tool, it can also be used for malicious intent. The penetration tester and hacker would want to run the tool to find an easy target to exploit.
Nessus works by choosing targets and deciding what vulnerabilities to identify on those targets. Figure 4-19 shows Nessus being configured to search all systems on the Class C 192.168.150.0 network.
With the targets identified, the hacker or penetration tester would need to determine which vulnerabilities to seek. Nessus works under the concept of using plugins. Each plugin looks for a specific vulnerability. As new vulnerabilities are found, new plugins can be created and easily imported into Nessus. Figure 4-20 shows the Plugins selection screen.
Figure 4-19. Nessus configuration

In Figure 4-20, you can see that the Windows: Microsoft Bulletins plu-gins are highlighted. These plugins will determine if the targeted systems are vulnerable to exploitation because they are missing Microsoft Windows patches.
You may also note the buttons regarding dangerous plugins. Dangerous plugins have the potential to cause harm just by seeing if the system is potentially vulnerable to exploitation. Because the hacker and penetration tester don't really care if they cause harm, they will run the scan with the dangerous plugins. The contractor from the previous example, as well as system administrators and network managers, would seriously consider not using the dangerous plugins. The contractor wouldn't want to bring attention to himself if something bad happened to a system during the scan, and the system administrator and network manager may not want to chance causing harm to systems on their network.
Figure 4-20. Plugins selection screen

Figure 4-21 shows a scan in progress.
Once the scan is done, vulnerabilities and security deficiencies on the target systems can be identified. The hacker or penetration tester would then use this information to determine which exploits they would want to run to take advantage of those vulnerabilities. Figure 4-22 shows security deficiencies found on a target system.
Figure 4-21. Scan in progress

At this point in the scenario, the hacker or penetration tester was able to sneak into the office, connect to the LAN, and get information about all the vulnerabilities on the LAN. Now, they can mount their attack!
One of my favorite security tools is Metasploit. It works in a similar manner as Nessus, in that new components can be added as they become available. While Nessus is used to find vulnerabilities, Metasploit is used to exploit systems that have vulnerabilities. As new exploits become available, they can be plugged into Metasploit by using its internal update process. Anyone who is tasked with protecting systems needs to be aware of Metasploit and how powerful it is. To help you understand its power, the following is a list of the exploits through which Metasploit can take advantage of your LAN because a malicious person was able to gain access. These are only the Windows-related exploits; there are other exploits included in the program.
Figure 4-22. Security deficiencies found on a target system

Execution windows/antivirus/Symantec_rtvscan Symantec Remote Management Buffer Overflow windows/arkeia/type77 Arkeia Backup Client Type 77 Overflow (Win32) windows/backupexec/name_service Veritas Backup Exec Name Service Overflow
windows/backupexec/remote_agent Veritas Backup Exec Windows Remote Agent Overflow windows/brightstor/discovery_tcp CA BrightStor Discovery Service TCP Overflow windows/brightstor/discovery_udp CA BrightStor Discovery Service Overflow windows/brightstor/lgserver CA BrightStor ARCserve for Laptops & Desktops LGServer Buffer Overflow windows/brightstor/message_engine CA BrightStor ARCserve Message Engine Buffer Overflow windows/brightstor/message_engine_heap CA BrightStor ARCserve Message Engine Heap Overflow windows/brightstor/sql_agent CA BrightStor Agent for Microsoft SQL Overflow windows/brightstor/tape_engine CA BrightStor ARCserve Tape Engine Buffer Overflow windows/brightstor/universal_agent CA BrightStor Universal Agent Overflow windows/browser/aim_goaway AOL Instant Messenger goaway Overflow windows/browser/apple_itunes_playlist Apple ITunes 4.7 Playlist Buffer Overflow
windows/browser/apple_quicktime_rtsp Apple QuickTime 7.1.3 RTSP URI Buffer Overflow windows/browser/ie_createobject Internet Explorer COM CreateObject Code Execution windows/browser/ie_iscomponentinstalled Internet Explorer isComponentInstalled Overflow windows/browser/mcafee_mcsubmgr_vsprintf McAfee Subscription Manager Stack Overflow windows/browser/mirc_irc_url mIRC IRC URL Buffer Overflow windows/browser/ms03_020_ie_objecttype MS03-020 Internet Explorer Object Type windows/browser/ms06_001_wmf_setabortproc Windows XP/2003/Vista Metafile Escape() SetAbortProc Code Execution windows/browser/ms06_013_createtextrange Internet Explorer createTextRange() Code Execution windows/browser/ms06_055_vml method Internet Explorer VML Fill Method Code Execution windows/browser/ms06_057_webview_setslice Internet Explorer WebViewFolderIcon setSlice() Overflow windows/browser/realplayer_smil RealNetworks RealPlayer SMIL Buffer Overflow windows/browser/winamp_playlist_unc Winamp Playlist UNC Path Computer Name Overflow windows/browser/xmplay_asx XMPlay 3.3.0.4 (ASX Filename) Buffer Overflow windows/dcerpc/ms03_026_dcom Microsoft RPC DCOM Interface Overflow windows/dcerpc/ms05_017_msmq Microsoft Message Queueing Service Path Overflow windows/driver/broadcom_wifi_ssid Broadcom Wireless Driver Probe Response SSID Overflow windows/driver/dlink_wifi_rates D-Link DWL- G132 Wireless Driver Beacon Rates Overflow windows/driver/netgear_wg111_beacon NetGear WG111v2 Wireless Driver Long Beacon Overflow windows/firewall/blackice_pam_icq ISS PAM.dll ICQ Parser Buffer Overflow windows/firewall/kerio_auth Kerio Firewall 2.1.4 Authentication Packet Overflow windows/ftp/3cdaemon_ftp_user 3Com 3CDaemon 2.0 FTP Username Overflow windows/ftp/cesarftp_mkd Cesar FTP 0.99g MKD Command Buffer Overflow windows/ftp/freeftpd_key_exchange FreeFTPd 1.0.10 Key Exchange Algorithm String Buffer Overflow windows/ftp/freeftpd_user freeFTPd 1.0 Username Overflow windows/ftp/globalscapeftp_input GlobalSCAPE Secure FTP Server Input Overflow
windows/ftp/netterm_netftpd_user NetTerm NetFTPD USER Buffer Overflow windows/ftp/oracle9i_xdb_ftp_pass Oracle 9i XDB FTP PASS Overflow (win32) windows/ftp/oracle9i_xdb_ftp_unlock Oracle 9i XDB FTP UNLOCK Overflow (win32) windows/ftp/servu_mdtm Serv-U FTPD MDTM Overflow windows/ftp/slimftpd_list_concat SlimFTPd LIST Concatenation Overflow windows/ftp/warftpd_165_pass War-FTPD 1.65 Password Overflow windows/ftp/warftpd_165_user War-FTPD 1.65 Username Overflow windows/ftp/wsftp_server_503_mkd WS-FTP Server 5.03 MKD Overflow windows/ftp/wsftp_server_505_xmd5 Ipswitch WS_FTP Server 5.0.5 XMD5 Overflow windows/games/ut2004_secure Unreal Tournament 2004 "secure" Overflow (Win32) windows/http/altn_webadmin Alt-N WebAdmin USER Buffer Overflow windows/http/apache_chunked Apache Win32 Chunked Encoding windows/http/badblue_ext_Overflow BadBlue 2.5 EXT.dll Buffer Overflow windows/http/edirectory_host Novell eDirectory NDS Server Host Header Overflow windows/http/edirectory_imonitor eDirectory 8.7.3 iMonitor Remote Stack Overflow windows/http/ia_webmail IA WebMail 3.x Buffer Overflow windows/http/icecast_header Icecast (<= 2.0.1) Header Overwrite (win32) windows/http/ipswitch_wug_maincfgret Ipswitch WhatsUp Gold 8.03 Buffer Overflow windows/http/mailenable_auth_header MailEnable Authorization Header Buffer Overflow windows/http/maxdb_webdbm_database MaxDB WebDBM Database Parameter Overflow windows/http/maxdb_webdbm_get_Overflow MaxDB WebDBM GET Buffer Overflow windows/http/minishare_get_Overflow Minishare 1.4.1 Buffer Overflow windows/http/navicopa_get_Overflow NaviCOPA 2.0.1 URL Handling Buffer Overflow windows/http/novell_messenger_acceptlang Novell Messenger Server 2.0 Accept-Language Overflow windows/http/oracle9i_xdb_pass Oracle 9i XDB HTTP PASS Overflow (win32)
windows/http/peercast_url PeerCast <= 0.1216 URL Handling Buffer Overflow (win32) windows/http/privatewire_gateway Private Wire Gateway Buffer Overflow windows/http/shoutcast_format SHOUTcast DNAS/win32 1.9.4 File Request Format String Overflow windows/http/shttpd_post SHTTPD <= 1.34 URI-Encoded POST Request Overflow (win32) windows/http/Sybase_easerver Sybase EAServer 5.2 Remote Stack Overflow windows/http/trackercam_phparg_Overflow TrackerCam PHP Argument Buffer Overflow windows/iis/ms01_023_printer Microsoft IIS 5.0 Printer Host Header Overflow windows/iis/ms01_033_idq Microsoft IIS 5.0 IDQ Path Overflow windows/iis/ms02_018_htr Microsoft IIS 4.0 .HTR Path Overflow windows/iis/ms03_007_ntdll_webdav Microsoft IIS 5.0 WebDAV ntdll.dll Path Overflow windows/imap/Eudora_list Qualcomm WorldMail 3.0 IMAPD LIST Buffer Overflow windows/imap/imail_delete IMail IMAP4D Delete Overflow windows/imap/mailenable_login MailEnable IMAPD (2.35) Login Request Buffer Overflow windows/imap/mailenable_status MailEnable IMAPD (1.54) STATUS Request Buffer Overflow windows/imap/mailenable_w3c_select MailEnable IMAPD W3C Logging Buffer Overflow windows/imap/mdaemon_cram_md5 Mdaemon 8.0.3 IMAPD CRAM-MD5 Authentication Overflow windows/imap/mercur_imap_select_Overflow Mercur v5.0 IMAP SP3 SELECT Buffer Overflow windows/imap/mercur_login Mercur Messaging 2005 IMAP Login Buffer Overflow windows/imap/mercury_rename Mercury/32 v4.01a IMAP RENAME Buffer Overflow windows/imap/novell_netmail_append Novell NetMail <= 3.52d IMAP APPEND Buffer Overflow windows/imap/novell_netmail_auth Novell NetMail <=3.52d IMAP AUTHENTICATE Buffer Overflow windows/imap/novell_netmail_status Novell NetMail <= 3.52d IMAP STATUS Buffer Overflow windows/imap/novell_netmail_subscribe Novell NetMail <= 3.52d IMAP SUBSCRIBE Buffer Overflow windows/isapi/fp30reg_chunked Microsoft IIS ISAPI FrontPage fp30reg.dll Chunked Overflow windows/isapi/nsiislog_post Microsoft IIS ISAPI nsiislog.dll ISAPI POST Overflow
windows/isapi/rsa_webagent_redirect Microsoft IIS ISAPI RSA WebAgent Redirect Overflow windows/isapi/w3who_query Microsoft IIS ISAPI w3who.dll Query String Overflow windows/ldap/imail_thc IMail LDAP Service Buffer Overflow windows/license/sentinel_lm7_udp SentinelLM UDP Buffer Overflow windows/lpd/hummingbird_exceed Hummingbird Connectivity 10 SP5 LPD Buffer Overflow windows/lpd/niprint NIPrint LPD Request Overflow windows/misc/backbone_netvault_heap BakBone NetVault Remote Heap Overflow windows/misc/bomberclone_Overflow Bomberclone 0.11.6 Buffer Overflow windows/misc/eiqnetworks_esa eIQNetworks ESA License Manager LICMGR_ADDLICENSE Overflow windows/misc/eiqnetworks_esa_topology eIQNetworks ESA Topology DELETEDEVICE Overflow windows/misc/goodtech_telnet GoodTech Telnet Server <= 5.0.6 Buffer Overflow windows/misc/mercury_phonebook Mercury/32 <= v4.01b PH Server Module Buffer Overflow windows/misc/shixxnote_font ShixxNOTE 6.net Font Field Overflow windows/mssql/ms02_039_slammer Microsoft SQL Server Resolution Overflow windows/mssql/ms02_056_hello Microsoft SQL Server Hello Overflow windows/nntp/ms05_030_nntp Microsoft Outlook Express NNTP Response Parsing Buffer Overflow windows/novell/nmap_stor Novell NetMail <= 3.52d NMAP STOR Buffer Overflow windows/novell/zenworks_desktop_agent Novell ZENworks 6.5 Desktop/Server Management Overflow windows/pop3/seattlelab_pass Seattle Lab Mail 5.5 POP3 Buffer Overflow windows/proxy/bluecoat_winproxy_host Blue Coat WinProxy Host Header Overflow windows/proxy/proxypro_http_get Proxy-Pro Professional GateKeeper 4.7 GET Request Overflow windows/sip/aim_triton_cseq AIM Triton 1.0.4 CSeq Buffer Overflow windows/sip/sipxezphone_cseq SIPfoundry sipXezPhone 0.35a CSeq Field Overflow windows/sip/sipxphone_cseq SIPfoundry sipXphone 2.6.0.27 CSeq Buffer Overflow windows/smb/ms03_049_netapi Microsoft Workstation Service NetAddAlternateComputerName Overflow
windows/smb/ms04_007_killbill Microsoft
ASN.1 Library Bitstring Heap Overflow
windows/smb/ms04_011_lsass Microsoft
LSASS Service DsRolerUpgradeDownlevelServer Overflow
windows/smb/ms04_031_netdde Microsoft
NetDDE Service Overflow
windows/smb/ms05_039_pnp Microsoft
Plug and Play Service Overflow
windows/smb/ms06_025_rasmans_reg Microsoft
RRAS Service RASMAN Registry Overflow
windows/smb/ms06_025_rras Microsoft
RRAS Service Overflow
windows/smb/ms06_040_netapi Microsoft
Server Service NetpwPathCanonicalize Overflow
windows/smtp/ms06_019_exchange MS06-019
Exchange MODPROP Heap Overflow
windows/smtp/wmailserver SoftiaCom
WMailserver 1.0 Buffer Overflow
windows/smtp/ypops_overflow1 YPOPS 0.6
Buffer Overflow
windows/ssh/freesshd_key_exchange FreeSSHd
1.0.9 Key Exchange Algorithm String Buffer Overflow
windows/ssh/putty_msg_debug PuTTy.exe <=
v0.53 Buffer Overflow
windows/ssh/securecrt_ssh1 SecureCRT <=
4.0 Beta 2 SSH1 Buffer Overflow
windows/ssl/ms04_011_pct Microsoft
Private Communications Transport Overflow
windows/tftp/futuresoft_transfermode FutureSoft
TFTP Server 2000 Transfer-Mode Overflow
windows/tftp/tftpd32_long_filename TFTPD32 <=
2.21 Long Filename Buffer Overflow
windows/tftp/threectftpsvc_long_mode 3CTftpSvc
TFTP Long Mode Buffer Overflow
windows/unicenter/cam_log_security CA CAM
log security() Stack Overflow (Win32)
windows/vnc/realvnc_client RealVNC 3.3.7
Client Buffer Overflow
windows/vnc/ultravnc_client UltraVNC
1.0.1 Client Buffer Overflow
windows/wins/ms04_045_wins Microsoft
WINS Service MemoryArmed with Metasploit, an attacker can launch an attack against your systems that have any of the these vulnerabilities. To do so, the following logical steps are performed in Metasploit:
The exploit is chosen.
A payload is chosen. (The payload is what will happen when the exploit takes place.)
Payload options are configured.
The exploit command is launched.
Chapter 5 will show you, step by step, how Metasploit is used to exploit a system. For now, realize that the payload is the bad thing that will happen on the exploited system. For example, if Metasploit were run against a server, then any of the following actions could take place on that server:
win32_adduser Windows Execute net user /ADD win32_bind Windows Bind Shell win32_bind dllinject Windows Bind DLL Inject win32_bind meterpreter Windows Bind Meterpreter DLL Inject win32_bind_stg Windows Staged Bind Shell win32_bind_stg_upexec Windows Staged Bind Upload/Execute win32_bind_vncinject Windows Bind VNC Server DLL Inject win32_downloadexec Windows Executable Download and Execute win32_exec Windows Execute Command win32_passivex Windows PassiveX ActiveX Injection Payload win32_passivex_meterpreter Windows PassiveX ActiveX Inject Meterpreter Payload win32_passivex_stg Windows Staged PassiveX Shell win32_passivex_vncinject Windows PassiveX ActiveX Inject VNC Server Payload win32_reverse Windows Reverse Shell win32_reverse_dllinject Windows Reverse DLL Inject win32_reverse_meterpreter Windows Reverse Meterpreter DLL Inject win32_reverse_stg Windows Staged Reverse Shell win32_reverse_stg_upexec Windows Staged Reverse Upload/Execute win32_reverse_vncinject Windows Reverse VNC Server Inject
These would all be devastating events on any company's systems. Adding a user, downloading and executing any file the attacker would want, establishing a remote control session to that system even if remote control software wasn't installed — imagine these actions happening to a domain controller or other vital piece of equipment. These are the types of things companies are up against and why they look to LAN-based NAC solutions.
The key to this scenario is that no amount of technology can completely replace the human factor. This company spent the money on a keycard system to help with physical security, and that was completely bypassed by the employees holding the door open. Once inside, the penetration tester simply had to find an unoccupied cubicle and start his work. Even if he didn't find the unoccupied computer, he could have plugged in his laptop and done everything he needed to do. Again, this is a true story, so don't think that it can't happen.
4.4.4. Exploitation from Unauthorized Wireless and Remote Access Connectivity to the LAN
The previous examples showed an attacker physically coming into the office to perform his attacks. For most companies, that isn't even necessary. Attackers can attempt to exploit the LAN in the following ways:
Via the company's mobile laptops
By breaking into their wireless LAN from a nearby location
By gaining access via the remote VPN solution
By using war dialing to find legacy dial access to the LAN
Chapter 5 addresses the extreme vulnerability that mobile laptops bring to the table. In fact, you'll see how the need for Mobile NAC often surpasses the need for LAN-based NAC. Chapter 5 also shows how wireless LANs can expose the LAN and how NAC can help. Until that time, keep in mind that the vulnerabilities of the LAN often involve technologies that are used to extend the LAN.
4.4.5. Does LAN-Based NAC Protect against Intentional Threats?
Just as with the "Unintentional LAN-Based Threats" section, the answer is, "It depends." Following is a list of ways LAN-based NAC would help, given the previous scenarios:
NAC solutions that require authentication would prevent unauthorized access to the LAN from non-corporate-owned systems.
Limiting contractors and other outsiders to their own LAN segments would help protect internal systems.
Ensure that corporate assets are always up to snuff or disconnect them from the LAN. When the penetration tester or attacker disabled antivirus software on the unoccupied system, NAC could have disconnected the system from the LAN.
For the contractor running the sniffer, Post-Admission NAC could have routinely checked to see if disallowed applications (such as known sniffer applications) were running on his machine. This action could have been stopped and reported.
This chapter has shown you the actual threats to the LAN. In seeing exactly how these exploits take place, companies can better assess their own vulnerabilities and decide upon the best NAC/NAP solution to meet their needs. These examples can also be used as ammunition to help change policies and help get the needed security solutions into place.
