9.2. Microsoft 802.1x
When it comes to 802.1x, many people immediately think of Wireless LAN security. In reality, 802.1x is port-based authentication that can apply to both wired and wireless networks. With authentication being a requirement for port access, this technology can be used to keep unwanted users off of the LAN. In doing so, this is performing an NAC/NAP function.
802.1x consists of two primary components:
Supplicant — Requests access to a network.
Authenticator — Authenticates supplicants and decides whether or not to grant them access. This can be a wireless access point (WAP) or a Remote Authentication Dial-in User Service (RADIUS) Server
To completely understand 802.1x, you must understand controlled and uncontrolled ports. A controlled port controls to what network addresses communication can take place. Uncontrolled ports allow unrestricted access. Figure 9-1 illustrates controlled and uncontrolled ports.
Figure 9-1. Controlled and uncontrolled ports
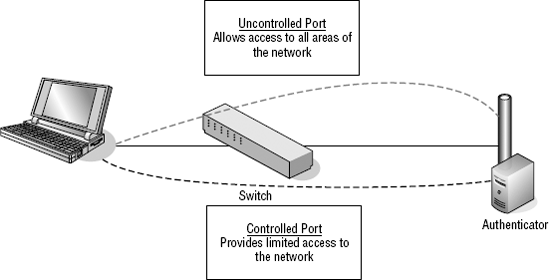
By having all devices that are connecting to the LAN placed onto a controlled port, their access is limited to just the Authenticator. This protects the network from having just anyone plug in and gain access. Once authenticated by the Authenticator, the device is placed onto an uncontrolled port and access to the network is unrestricted.
Clearly, the 802.1x functionality can prohibit just any device from gaining full access to the LAN. Therefore, simply using 802.1x on the LAN performs NAC functionality. It's really a very easy-to-understand concept that can have significant security advantages. Microsoft offers a Wired 802.1x solution for Windows 2000, Windows Server 2003, and Windows XP. For Wireless 802.1x, there are many well-known technologies and vendors that have solutions.
Detailed information on Microsoft's Wired 802.1x capabilities can be found at http://download.microsoft.com/download/b/0/e/b0e2a363-0044-4327-8f17-020818f57234/Wireddepl.doc.
9.2.1. NAP
Microsoft's Network Access Protection is marketed as Microsoft's future and robust play into the NAP and NAC market. The NAP platform requires servers running Windows Server 2008 and clients running Windows Vista or Windows XP Service Pack 3. Microsoft is still defining the compatibility details for NT 4.0 and Windows 2000 and will post more information when it becomes available.
NOTE
As with Windows Server 2008, Windows XP Service Pack 3 is not yet available as of this writing.
Microsoft NAP can be utilized to control access across the following access vectors:
IPsec NAP EC for IPsec-protected communications
EAPHost NAP EC for 802.1X-authenticated connections
Following are the core components of Microsoft NAP:
NAP Agent — This maintains health state based on input from the System Health Agent's communications with Enforcement Client components. This agent creates Statements of Health (SoH) based upon this information.
System Health Agent (SHA) — This is the component for each type of health requirement. For example, there could be an SHA for antivirus and another for operating system updates. (These are similar to Cisco NAC Framework Posture Plugins.)
SHA Application Programming Interface (API) — This allows vendors to create and install custom SHAs.
Enforcement Client components (EC) — These request a type of access to a network, pass the computer's health status to a NAP enforcement point that is providing the network access, and indicate the limited or unlimited network access status of the NAP client to other components of the NAP client architecture.
NAP EC API — This allows vendors to create and install additional NAP ECs.
The following are the server components:
NAP Enforcement Server (ES) — This allows a level of network access or communication. It passes client health status to a health policy server and, based upon that feedback, can control network access. It is the enforcement point for the NAP solution.
NAP Administration Server — This obtains the SoH from the NAP ES through the NPS service. It distributes the SoHs in the System Statement of Health (SSoH) to the appropriate System Health Validators. It collects the Statement of Health Responses (SoHRs) from the System Health Validators and passes them to the NPS service for evaluation.
Network Policy Servers (NPS) — The implementation of a RADIUS server and proxy in Windows Server 2008. This provides centralized health policy configuration and evaluation of the NAP client health state.
System Health Validator (SHV) — This receives an SoH from the NAP Administration Server and compares the system health status information in the SoH with the required system health state.
Microsoft NAP will work with existing Windows-based infrastructure such as the Active Directory domain service, Group Policy, Microsoft Systems Management Server (SMS), Windows Update Services, and Microsoft Internet Security and Acceleration (ISA) Server. In addition, some components can be provided by third-party vendors. Microsoft does offer two APIs for vendors to provide integration with their products.
