4.2. Unintentional LAN-Based Threats
You have now seen briefly how unintentional threats can cause problems on a LAN. Although these users are utilizing their systems with the most honorable of intentions, they can still cause problems by the simple act of them connecting to the LAN.
NOTE
I spoke with a company that actually caused one of their customer's LANs to become infected. One of their laptops contained malware, and it spread throughout the customer's LAN. That is certainly not a good position to be in and was why that company was seeking a Mobile NAC solution!
Unintentional threats are not limited to outsiders. Employees can cause unintentional infections as well. The following are the two types of devices of which to be aware of in regard to unintentional threats:
Corporate-owned devices that are authorized to connect to the LAN
Guest (or unknown) devices that may or may not be authorized to connect to the LAN
When utilizing a LAN-based NAC/NAP solution to address unintentional threats, the enterprise has a few decisions to make on how it wants to address this threat from a topological standpoint. How this is done defines the types of threats to which the LAN is vulnerable. The topology considerations include the following:
Having all guest/unknown device access be limited to guest networks, which are separate from the corporate LAN
Assessing the devices and providing access based upon their security posture
4.2.1. The Pros and Cons of a Guest Network
Guest networks have become somewhat popular in companies. These organizations recognize the need to provide a level of connectivity to outsiders, although the organizations don't want them connecting directly to their LANs. Providing a separate network, and allowing outsiders to connect to it, helps to address both of these needs. In essence, the guest network performs NAC-like functionality by segmenting guest systems from the corporate LAN.
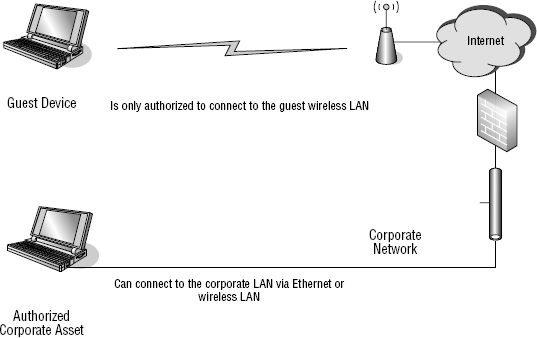
In my travels, I typically see guest networks being provided via Wi-Fi. As a security guy, I will never connect my laptop to an Ethernet port or a Wi-Fi connection at a prospect or customer location without first receiving permission (unlike some sales guys I know). If I am unable to receive an EvDO or CDMA connection from my location within their facility and outside connectivity is desired, I may ask if a guest network is available. More and more often, the answer is "yes," and I am given the SSID of the network to which I can connect. Generally speaking, I don't see widespread use of guest Ethernet connections, although they are certainly possible. Sometimes, I'll be in a server room or network operations center (NOC) and ask for outside connectivity, and I can usually get an Ethernet connection directly to the Internet. That is because of the fact that I am in the server room or NOC, and that option is generally not available in conference rooms and other locations where outsiders would generally connect. Figure 4-2 gives an example of a guest wireless LAN topology.
The biggest "pro" to utilizing this method of restriction is that the guest device is on a completely separate LAN. It does not have network connectivity to the corporate network and, consequently, doesn't pose any bigger threat to the LAN than anyone else connected to the Internet. This is a good method of stopping the threat from unintentional infection.
There is, however, a pretty big "con" to relying on guest networks. That "con" is that utilizing this method alone doesn't provide any means of enforcement. An outsider can be told to connect to the wireless LAN, although a live Ethernet connection directly into the corporate LAN could be sitting right next to him or her. There wouldn't be any technical means to stop that person from using the connection.
Figure 4-2. Guest network topology
For example, consider the following scenario:
A contractor arrives at the customer's office and wants to begin working. He is led to a conference room and told that he can connect to the guest wireless LAN. He connects and begins working. The wireless LAN signal isn't very strong and there is considerable interference in the area, so his wireless connection keeps getting dropped. He sees an Ethernet cable connected to the wall and plugs it into his laptop. He connects to the LAN and receives his Internet connectivity. With this connectivity, he can be productive and finish the task at hand.
In this scenario, the contractor wasn't being malicious. He may not have even realized that he did something wrong. The problem is that he was allowed to connect to the corporate LAN simply by plugging in the Ethernet cable. While the guest network provided a means for segmenting guest users from the corporate LAN, there wasn't a mechanism to restrict the guest from accessing other network connections.
So, in short, there are two sides to using guest networks:
4.2.1.1. Pro
Following is the "pro" to using guest networks:
Allows for complete segmentation of guests from the corporate LAN
4.2.1.2. Con
Following is the "con" to using guest networks:
Doesn't provide a means to restrict the use of other available networks
4.2.2. The Pros and Cons of Assessing Each Device
Another approach to use with guest systems is to assess every device that connects to the corporate LAN. That would protect the corporate LAN against the previous example and provide the most robust security. As with guest networks, there are "pros" and "cons" to using this methodology. Also, let's not forget that unintentional threats can also come from corporate-owned assets that are fully authorized to access the LAN.
NOTE
Assessing every device that connects to a corporate LAN can be used in conjunction with a guest network.
The big "pro" with assessing every device that attempts to gain access to the corporate LAN is that it provides robust security. If a device is simply connected to an Ethernet cable that happens to be available, it doesn't mean that access to the corporate LAN will be provided. An assessment will take place, and if the predefined criteria are met, corporate LAN access can be provided. With this methodology, some logical rules would be the following:
Provide unrestricted access to devices that meet all predefined criteria
Provide restricted access to devices that only partially meet the predefined criteria
Disallow connectivity for unknown and guest systems
Provide restricted access for unknown and guest systems
The type of NAC solution being used will also come into play when making decisions on how to enforce policies. For example, if a client-based NAC solution is being used, then every authorized device will need to have the NAC client installed to gain appropriate levels of access. This isn't necessarily a bad thing, but it does have the potential of locking out devices. The use of a scanning NAC solution wouldn't require that a client be installed, although the granularity of the assessment could be limited.
In short, there are two sides to assessing each device.
4.2.2.1. Pro
Following is the "pro" to assessing each network device:
No corporate LAN access is granted without the device being assessed and meeting predefined criteria.
4.2.2.2. Con
Following is the "con" to assessing each network device:
A NAC solution actually has to be put into place, and often, a client will need to be installed on all authorized devices.
