

Security
Many components in SAN security relate to SAN design, and the decision to use these components depends on installation requirements rather than network functioning or performance. One clear exception is the zoning feature that is used to control device communication. The proper use of zoning is key to fabric functioning, performance, and stability, especially in larger networks. For more information, see 10.5, “Zoning” on page 260. Other security-related features are largely mechanisms for limiting access and preventing attacks on the network (and are mandated by regulatory requirements). They are not required for normal fabric operation.
This chapter includes the following sections:
11.1 Role-Based access controls
One way to provide limited accessibility to the fabric is through user roles. FOS has predefined user roles, each of which has access to a subset of the CLI commands. These roles are known as role-based access controls (RBACs), and they are associated with the user login credentials. When you log in to a switch, your user account is associated with a predefined role or a user-defined role. The role that your account is associated with determines the level of access you have on that switch and in the fabric. For more information about RBAC, see the “Managing User Accounts” chapter in the Fabric OS Administrator’s Guide, which you can find at the following website:
11.2 Default accounts
FOS offers four predefined accounts: Admin, factory, root, and user. Although the root and factory accounts are reserved for development and manufacturing, the password for all default accounts should be changed and secured during the initial installation and configuration of each switch. Recovering passwords might require significant effort and fabric downtime.
11.3 User accounts
In addition to the default permissions assigned to the roles of root, factory, admin, and user, Fabric OS supports up to 252 additional user accounts on the chassis. These accounts expand the ability to track account access and audit administrative activities.
Each user account is associated with the following things:
•Admin Domain list: Specifies the Administrative Domains to which a user account is allowed to log in.
•Home Admin Domain: Specifies the Admin Domain that the user is logged in to by default. The home Admin Domain must be a member of the user’s Admin Domain list.
•Permissions: Associate roles with each user account to determine the functional access levels within the bounds of the user’s current Admin Domain.
•Virtual Fabric list: Specifies the Virtual Fabric that a user account is allowed to log in to.
•Home Virtual Fabric: Specifies the Virtual Fabric that the user is logged in to, if available. The home Virtual Fabric must be a member of the user’s Virtual Fabric list. If the fabric ID is not available, the next-lower valid fabric ID is used.
•LF Permission List: Determines functional access levels within the bounds of the user’s Virtual Fabrics.
•Chassis role. Similar to switch-level roles, but applies to a different subset of commands.
11.4 Security protocols
Security protocols provide endpoint authentication and communications privacy by using cryptography. Typically, the user is authenticated to the switch while the switch remains unauthenticated. This authentication means that you can be sure that you know with whom you are communicating. The next level of security, in which both ends of the conversation are sure with whom they are communicating, is known as two-factor authentication. Two-factor authentication requires public key infrastructure (PKI) deployment to clients.
Table 11-1 shows the security protocols that are supported by Fabric OS.
Table 11-1 Security protocols that are supported by Fabric OS
|
Protocol
|
Description
|
|
CHAP
|
Challenge Handshake Authentication Protocol (CHAP) uses shared secrets to authenticate switches.
|
|
HTTPS
|
HTTPS is a Uniform Resource Identifier scheme that is used to indicate a secure HTTP connection. Web Tools supports the use of Hypertext Transfer Protocol over SSL (HTTPS).
|
|
IPSec
|
Internet Protocol Security (IPSec) is a framework of open standards for providing confidentiality, authentication, and integrity for IP data transmitted over untrusted links or networks.
|
|
LDAP
|
Lightweight Directory Access Protocol (LDAP) with Transport Layer Security (TLS) uses a certificate authority (CA). By default, LDAP traffic is transmitted unsecured. With the import of signed certificates, you can make LDAP traffic confidential and secure by using Secure Sockets Layer (SSL) / TLS technology with LDAP.
|
|
SCP
|
Secure Copy Protocol (SCP) is a means of securely transferring computer files between a local and a remote host or between two remote hosts that use the Secure Shell (SSH) protocol. Configuration upload and download support the use of SCP.
|
|
Secure Syslog
|
Secure syslog requires importing syslog CA certificates by using the secCerUtil command.
|
|
SFTP
|
Secure File Transfer Protocol (SFTP) is a network protocol for securely transferring files on a network. Configuration upload and download support the use of SFTP.
|
|
SNMP
|
Simple Network Management Protocol (SNMP) is used in network management systems to monitor network-attached devices for conditions that warrant administrative attention. Supports SNMPv1 and v3.
|
|
SSH
|
SSH is a network protocol that allows data to be exchanged over a secure channel between two computers. Encryption provides confidentiality and integrity of data. SSH uses public-key cryptography to authenticate the remote computer and allow the remote computer to authenticate the user, if necessary.
|
|
SSL
|
Fabric OS uses SSL to support HTTPS. A certificate must be generated and installed on each switch to enable SSL. This configuration supports SSLv3, 128-bit encryption by default. It also supports TLSv1.0, TLSv1.1, and TLSv1.2.
|
|
Note: Some of the security protocols that are listed in Table 11-1 require additional software or certificates that you must obtain to deploy secure protocols. For more information and configuration instructions, see the Fabric OS Administrator’s Guide at the following website:
|
11.5 Access control lists
Access control lists (ACLs) are used to provide network security through policy sets. FOS provides several ACL policies, including a Switch Connection Control (SCC) policy, a Device Connection Control (DCC) policy, a Fabric Configuration Server (FCS) policy, an IP Filter, and others. The following sections briefly describe each policy and provide basic guidelines. A more in-depth description of ACLs can be found in the Fabric OS Administrator’s Guide, which you can find at the following website:
11.5.1 SCC policy
The SCC policy restricts the fabric elements (FC switches) that can join the fabric. Only switches that are specified in the policy are allowed to join the fabric. All other switches fail authentication if they attempt to connect to the fabric, resulting in the respective E_Ports being segmented because of the security violation.
Use the SCC policy in environments where you need strict control of fabric members. Because the SCC policy can prevent switches from participating in a fabric, it is important to regularly review and properly maintain the SCC ACL.
11.5.2 DCC policy
The DCC policy restricts the devices that can attach to a single Fibre Channel (FC) port. The policy specifies the FC port and one or more worldwide names (WWNs) that are allowed to connect to the port. The DCC policy set comprises all of the DCC policies that are defined for individual FC ports. Not every FC port must have a DCC policy, and only ports with a DCC policy in the active policy set enforce access controls. A port that is present in the active DCC policy set allows only WWNs in its respective DCC policy to connect and join the fabric. All other devices fail authentication when they attempt to connect to the fabric, resulting in the respective F_Ports being disabled because of the security violation.
Use the DCC policy in environments where you need strict control of fabric members. Because the DCC policy can prevent devices from participating in a fabric, it is important to regularly review and properly maintain the DCC policy set.
11.5.3 FCS policy
Use the FCS policy to restrict the source of fabric-wide settings to one FC switch. The policy contains the WWN of one or more switches, and the first WWN (that is online) in the list is the primary FCS. If the FCS policy is active, then only the primary FCS is allowed to make or propagate fabric-wide parameters. These parameters include zoning, security (ACL) policies databases, and other settings.
Use the FCS policy in environments where you need strict control of fabric settings. As with other ACL policies, it is important to regularly review and properly maintain the FCS policy.
11.5.4 IP Filter
The IP Filter policy is a set of rules that are applied to the IP management interfaces as a packet filtering firewall. The firewall permits or denies the traffic to go through the IP management interfaces according to the policy rules.
As a preferred practice, non-secure IP protocols that are used for switch management such as Telnet and HTTP should be blocked. SSH is enabled on the default IP Filter policy and SSL should be configured to use HTTPS for web access.
The IP Filter policy should be used in environments where you need strict control of fabric access. As with other ACL policies, it is important to regularly review and properly maintain the IP Filter policy.
11.5.5 Authentication protocols
Fabric Operating System (FOS) supports both Fibre Channel Authentication Protocols (FCAPs) and Diffie-Hellman CHAPs (DH-CHAPs) on E_Ports and F_Ports. Authentication protocols provide extra security during link initialization by ensuring that only the wanted device/device type is connecting to a given port.
11.6 Policy Database Distribution
Security Policy Database Distribution provides a mechanism for controlling the distribution of each policy on a per-switch basis. Switches can individually configure policies to either accept or reject a policy distribution from another switch in the fabric. In addition, a fabric-wide distribution policy can be defined for the SCC and DCC policies with support for strict, tolerant, and absent modes. This setting can be used to enforce whether the SCC or DCC policy must be consistent throughout the fabric.
The Policy Database Distribution has three modes:
•Strict mode: All updated and new policies of the type specified (SCC, DCC, or both) must be distributed to all switches in the fabric, and all switches must accept the policy distribution.
•Tolerant mode: All updated and new policies of the type specified (SCC, DCC, or both) are distributed to all switches (FOS V6.2.0 or later) in the fabric. However, the policy does not need to be accepted.
•Absent mode: Updated and new policies of the type specified (SCC, DCC, or both) are not automatically distributed to other switches in the fabric. Policies can still be manually distributed.
Together, the policy distribution and fabric-wide consistency settings provide a range of control on the security policies from little or no control to strict control.
11.7 In-flight encryption and compression: b-type (16 Gbps) platforms only
IBM b-type Fibre Channel (16 Gbps) platforms support both in-flight compression and encryption at a port level for both local and long-distance inter-switch links (ISLs). In-flight data compression is a useful tool for saving money when either bandwidth caps or bandwidth usage charges are in place for transferring data between fabrics. Similarly, in-flight encryption enables a further layer of security with no key management impact when transferring data between local and long-distance data centers besides the initial setup.
Enabling in-flight ISL data compression or encryption increases the latency as the ASIC processes the frame compression or encryption. The approximate latency at each stage (encryption and compression) is 6.2 microseconds. For example (see Figure 11-1), compressing and then encrypting a 2 KB frame incurs approximately 6.2 microseconds of latency on the sending Condor3-based switch, and approximately 6.2 microseconds of latency at the receiving Condor3-based switch to decrypt and decompress the frame. This combination results in a total latency time of 12.4 microseconds, again not counting the link transit time.
Figure 11-1 shows the total accumulated latency when encryption and compression are in use.
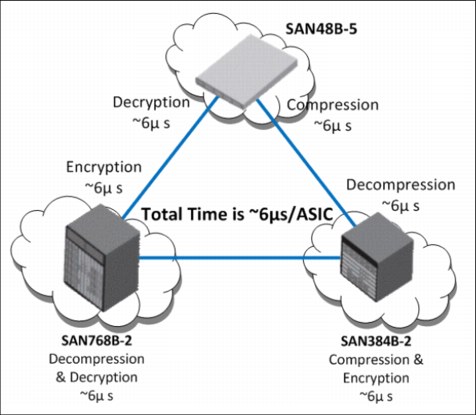
Figure 11-1 Latency for encryption and compression
|
Virtual Fabric considerations (encryption and compression): The E_Ports in the user-created Logical Switch, Base Switch, or default switch can support encryption and compression. Both encryption and compression are supported on XISL ports, but not on LISL ports. If encryption or compression is enabled and ports are being moved from one LS to another, it must be disabled before the ports are moved.
|
11.8 In-flight encryption and compression guidelines
Consider these in-flight encryption and compression guidelines:
•Encryption and compression are supported on E_Ports and EX_Ports.
•ISL ports must be set to Long-Distance (LD) mode when compression is used.
•Twice the number of buffers should be allocated if compression is enabled for long distance because frame sizes might be half the size.
•If both compression and encryption are used, enable compression first.
When you implement ISL encryption, using multiple ISLs between the same switch pair requires that all ISLs be configured for encryption, or none at all.
No more than two ports on one ASIC can be configured with encryption, compression, or both when running at 16 Gbps speed. With FOS V7.1, additional ports can be used for data encryption, data compression, or both if the system is running at lower than 16 Gbps speeds.
Encryption is not compliant with Federal Information Processing Standards (FIPS).
|
Note: For more information about securing a SAN network and associated management and IP WAN connectivity, see the Fabric OS Administration Guide that is available at the following website:
|
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
