Chapter 10: Investigating Data Exfiltration Techniques
Once ransomware affiliates have obtained access to privileged credentials and enabled lateral movement capability, they usually start working on their real goal. One such goal is data exfiltration.
Of course, not every group performs such activities, and even threat actors with their own DLS don't do it during every attack. Still, as double-extortion is a very common technique, incident responders should be well aware of approaches used by ransomware affiliates for the exfiltration of sensitive data from compromised networks.
In this chapter, we'll look at forensic artifacts, which allow us to understand ransomware affiliates' activities related to data exfiltration. Approaches may vary significantly and depend wholly on the threat actor. Some prefer a straightforward approach and exfiltrate data via a web browser or a cloud service client, while others prefer to use a custom application provided as part of a ransomware-as-a-service program.
We'll look at the following topics:
- Investigating web browser abuse for data exfiltration
- Investigating cloud service client application abuse for data exfiltration
- Investigating third-party cloud synchronization tool abuse for data exfiltration
- Investigating the use of custom data exfiltration tools
Investigating web browser abuse for data exfiltration
As you already know from the previous chapters, ransomware affiliates abuse Remote Desktop Protocol (RDP) connections both for initial access and lateral movement quite often, so they can easily use built-in legitimate tools to solve various tasks, including data exfiltration.
One such tool is a web browser. Threat actors may use it to upload sensitive data collected by them to various file-sharing services, for example, DropMeFiles.
Web browsers have great logging capabilities, so digital forensic analysts and incident responders can always check the browsing history for any traces of data exfiltration.
Let's look at a classic version of a built-in web browser – Microsoft Edge. History data is stored in a WebCacheV01.dat file that is an Extensible Storage Engine (ESE) database. Of course, there are quite a few tools that can be used to browse and analyze its contents. A good example is ESEDatabaseView from NirSoft.
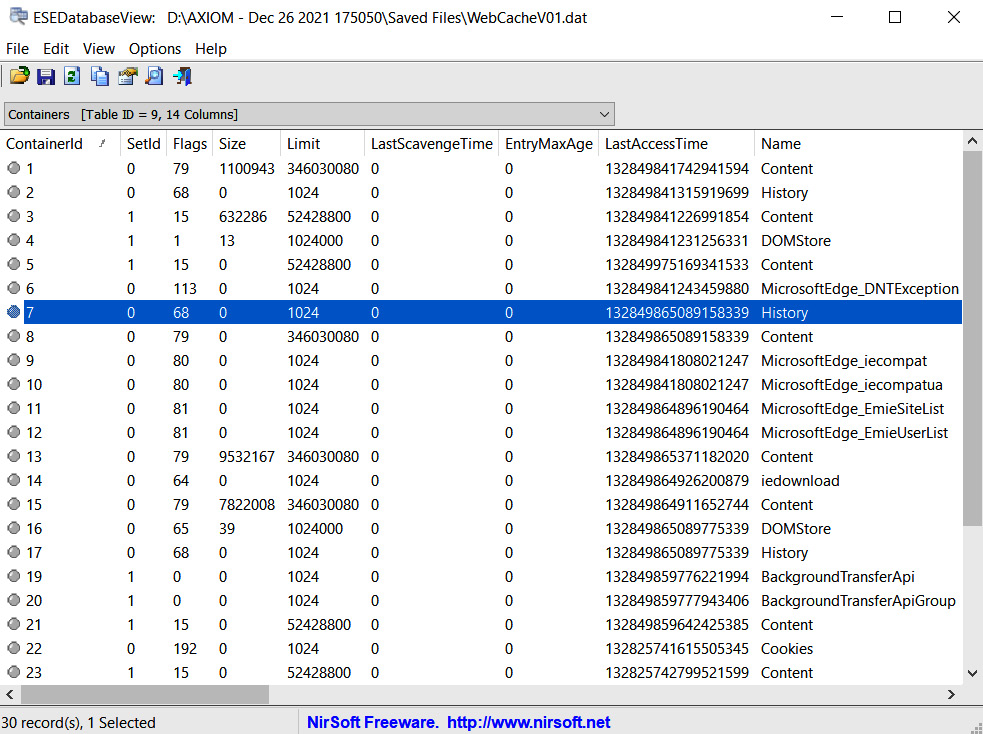
Figure 10.1 – The WebCacheV01.dat file opened in ESEDatabaseView
In the preceding screenshot, you can see the table named Containers. This table can help us determine which tables contain information of interest. As we are interested in web browsing history, we should check tables marked as History, for example, the table named Container_7 (you can find the ID on the left). Let's look at the Url column.
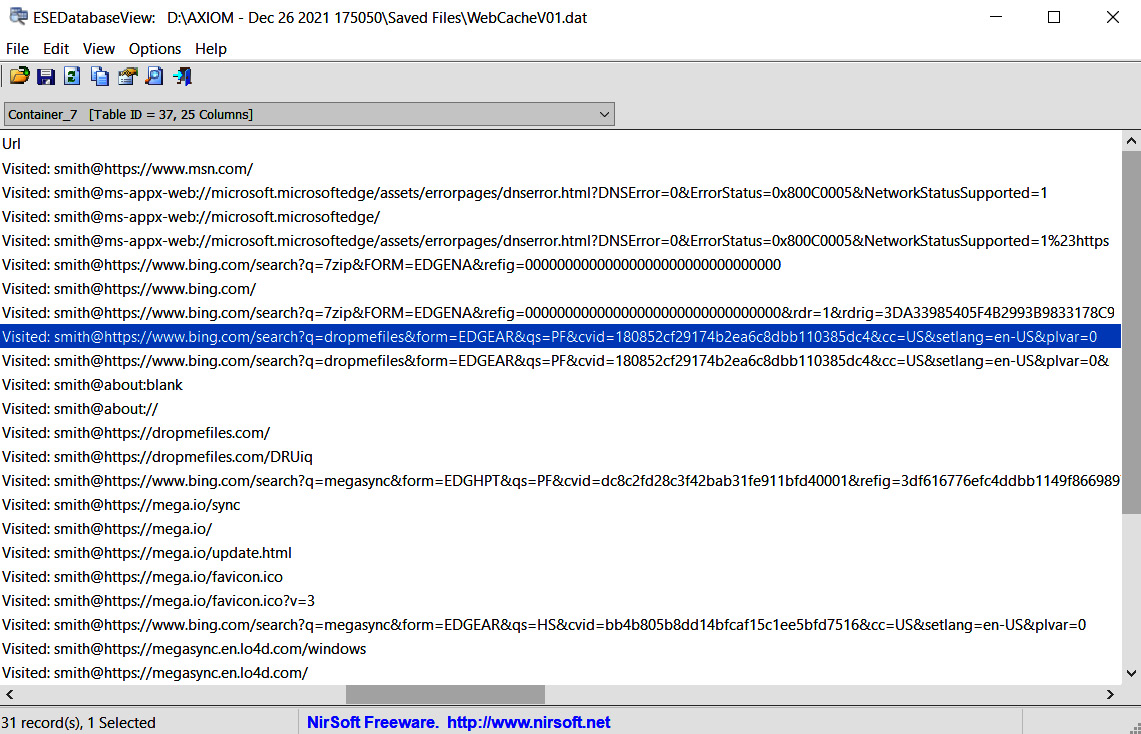
Figure 10.2 – The Container_7 table
Here we can see quite a few interesting records. First of all, we can see that ransomware affiliates used the Bing search engine to get a popular archiving tool – 7-Zip:
Visited: smith@https://www.bing.com/search?q=7zip&FORM=EDGENA&refig=00000000000000000000000000000000&rdr=1&rdrig=3DA33985405F4B2993B9833178C9DA02
It's not the only notable artifact – another one is the user's name. In some cases, it may even lead the investigator to the initially compromised host, also known as patient zero.
We can also get the access timestamp from this table. In our case, it's 132849977563921851. Doesn't look like a timestamp? This is just because it's stored in Webkit format. It can be easily converted to a human-readable format, and we'll get the following: Sunday, 26 December 2021, 13:09:16.
So, why do the threat actors require such utilities? Most likely, to archive data prior to exfiltration! We already have our first pivot point, so let's check for any other interesting artifacts parsing $MFT.
We can see that ransomware affiliates dropped 7-Zip to the Temp folder:
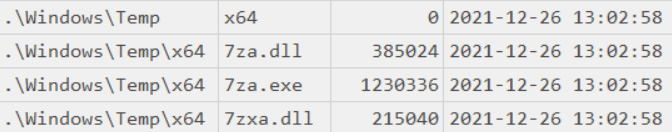
Figure 10.3 – 7-Zip related file in the Temp folder
If we scroll through our MFT-based timeline, soon we can find another interesting artifact:
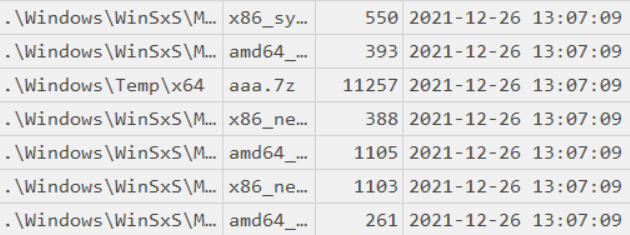
Figure 10.4 – A 7z archive in the suspicious folder
Now we can see that the threat actors most likely leveraged 7-Zip to archive some data, most likely to prepare it for exfiltration. Archiving collected data before exfiltration is a very common technique observed as being used by many ransomware affiliates.
Now let's look inside the prefetch file related to 7za.exe:
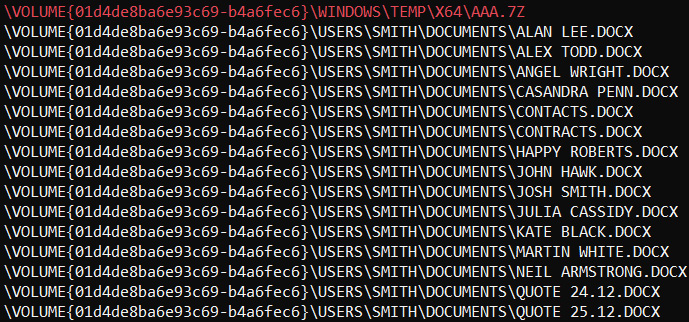
Figure 10.5 – Archived data as seen in the referenced files list
As prefetch files contain both referenced files and referenced directories lists, we can use it to understand what exactly was archived even if the archive is already deleted by the threat actors.
Let's get back to the uncovered web browsing history in Figure 10.2. The next thing that should attract your attention is another Bing search:
Visited: smith@https://www.bing.com/search?q=dropmefiles&form=EDGEAR&qs=PF&cvid=180852cf29174b2ea6c8dbb110385dc4&cc=US&setlang=en-US&plvar=0
This time, the threat actors searched for a popular file-sharing website – DropMeFiles. This and other similar websites are common means used by ransomware affiliates for data exfiltration. Ransomware affiliates may use various services, even those typical of the compromised infrastructure, so that they can hide in plain sight.
Also, we can see a very interesting URL – https://dropmefiles.com/DRUiq, which stores the following content:

Figure 10.6 – Exfiltrated archive
If we download the data from this link, we can see that the archive we found previously was uploaded to DropMeFiles.
Of course, this isn't the only technique used by threat actors to exfiltrate data. In the next section, we'll look at how they abuse cloud service client applications.
Investigating cloud service client application abuse for data exfiltration
Ransomware affiliates may use built-in tools, such as web browsers, for data exfiltration, but also can install and execute third-party tools to solve this task.
So, it's always a good idea to check for freshly installed programs, which may be related to activities performed by the threat actors. Such information can be collected from the SOFTWARE registry file, which is located under C:WindowsSystem32config.
Information about installed programs can be located under SOFTWARE | MicrosoftWindowsCurrentVersionUninstall:
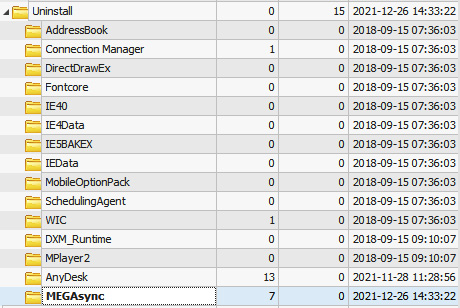
Figure 10.7 – Information on installed programs
We can get even more information on the installed application by checking the values of the MEGAsync subkey:
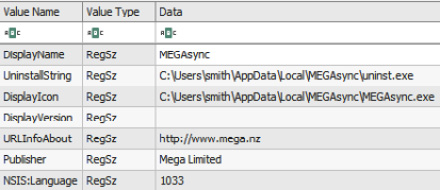
Figure 10.8 – MEGAsync installation details
MEGA provides the threat actors with great exfiltration capabilities, which is why many ransomware affiliates prefer to use it to achieve this goal.
Client applications often store various logs on the host, so it's always worth checking the C:Users\%USERNAME%AppData subfolders for any good sources of evidence. One such interesting file related to MEGAsync is MEGAsync.log. In our case, it's located under C:UserssmithAppDataLocalMega LimitedMEGAsynclogs.
If we look through this file, we can easily get information about exfiltrated files, including the exact folder on the compromised host:
12/26-14:35:26.853651 7940 INFO Adding file to upload queue: C:UserssmithDocumentsKate Black.docx [:-1]
12/26-14:35:26.853731 7940 INFO Adding file to upload queue: C:UserssmithDocumentsMartin White.docx [:-1]
12/26-14:35:26.853802 7940 INFO Adding file to upload queue: C:UserssmithDocumentsNeil Armstrong.docx [:-1]
12/26-14:35:26.853889 7940 INFO Adding file to upload queue: C:UserssmithDocumentsQuote 24.12.docx [:-1]
12/26-14:35:26.853957 7940 INFO Adding file to upload queue: C:UserssmithDocumentsQuote 25.12.docx [:-1]
12/26-14:35:26.854021 7940 INFO Adding file to upload queue: C:UserssmithDocumentsAlan Lee.docx [:-1]
12/26-14:35:26.854085 7940 INFO Adding file to upload queue: C:UserssmithDocumentsAlex Todd.docx [:-1]
12/26-14:35:26.854149 7940 INFO Adding file to upload queue: C:UserssmithDocumentsAngel Wright.docx [:-1]
12/26-14:35:26.854212 7940 INFO Adding file to upload queue: C:UserssmithDocumentsCasandra Penn.docx [:-1]
12/26-14:35:26.854274 7940 INFO Adding file to upload queue: C:UserssmithDocumentsContacts.docx [:-1]
12/26-14:35:26.854336 7940 INFO Adding file to upload queue: C:UserssmithDocumentsContracts.docx [:-1]
12/26-14:35:26.854400 7940 INFO Adding file to upload queue: C:UserssmithDocumentsHappy Roberts.docx [:-1]
12/26-14:35:26.854462 7940 INFO Adding file to upload queue: C:UserssmithDocumentsJohn Hawk.docx [:-1]
12/26-14:35:26.854524 7940 INFO Adding file to upload queue: C:UserssmithDocumentsJosh Smith.docx [:-1]
12/26-14:35:26.854586 7940 INFO Adding file to upload queue: C:UserssmithDocumentsJulia Cassidy.docx [:-1]
What's more, this log file provides us with information about the account used for data exfiltration:
12/26-14:34:51.962318 8004 DBG cs Sending 158: [{"a":"us","user":"[email protected]","uh":"_qjNUa1_sKTh0Kvk-KS6nA","sek":"F_3tILmzDLfT8880lIJGBg","si":"9eXU674TFeBa5PpTUm80WQuUJ8LkL82tgGH1xG-7cf8"}] [net.cpp:1440]
OK, now we know which data was exfiltrated to MEGA, as well as the account name used to conduct this activity, but still don't know how this application got to the compromised host.
Let's analyze the web browsing history again, focusing on another browser – Mozilla Firefox. This web browser stores history information in a SQLite database called places.sqlite. We can use, for example, DB Browser for SQLite to analyze its contents.
Figure 10.9 – Database structure
The most interesting pieces of information from the investigation perspective are located in the moz_places table. Here we can find the list of visited URLs:
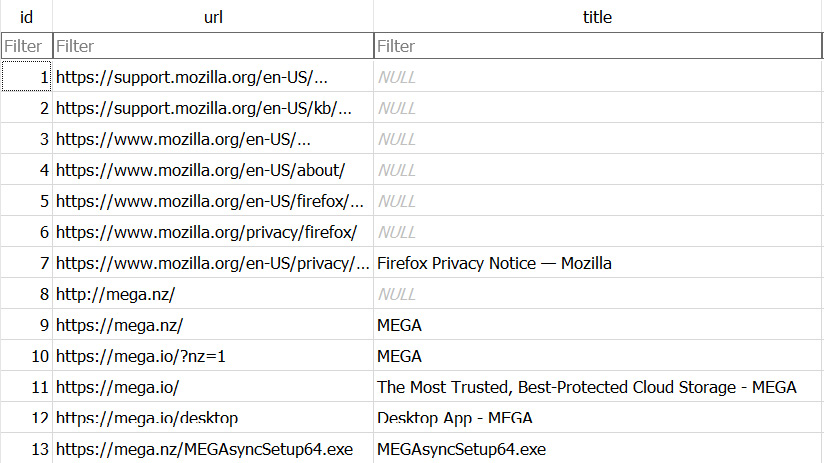
Figure 10.10 – The contents of the moz_places table
Now we can clearly see that ransomware affiliates downloaded and executed the MEGAsync installer from the official website and then used it to exfiltrate sensitive data. But was Mozilla Firefox present on the host before it was compromised?
You already know where to check for evidence of program installation, so we can use the same registry key to get the Firefox installation date.
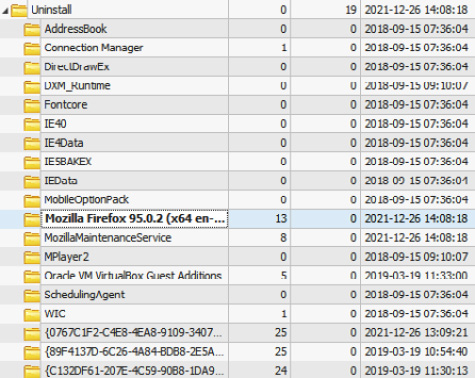
Figure 10.11 – Mozilla Firefox installation date
As you can see, Mozilla Firefox was installed on the same date as MEGAsync, and then was used by the threat actors to download and install the MEGAsync client application.
Tools for data exfiltration can be downloaded to the target system not only via web browser abuse. For example, ransomware affiliates may use external or internal RDP-connection, the bot's command and control server, or Cobalt Strike Beacon.
Let's move forward and look at other popular tools used by the threat actors involved in ransomware attacks.
Investigating third-party cloud synchronization tool abuse for data exfiltration
Threat actors use a wide variety of tools, including absolutely legitimate ones, to solve various tasks at different stages of the attack life cycle. Of course, the data exfiltration stage isn't an exception. We have already looked at web browsers and cloud service client application abuse for solving this task, but let's look at one more example.
Ransomware affiliates may want to be even stealthier to avoid detection and may leverage various masquerading techniques.
For example, they can rename tools to look like legitimate processes. As you already know, Shimcache is one of the most common sources of evidence of execution, so we can extract this data from the SYSTEM registry file (located under C:WindowsSystem32config), for example, via RegRipper, and check for any traces of leveraging masquerading.
Very soon, we notice the following record:
C:Windowssvchost.exe 2021-12-26 13:56:30
At first glance, it's an absolutely legit Windows executable that allows services to share a single process. But there's one important thing – a legitimate svchost.exe file should be located under C:WindowsSystem32!
The timestamp stored in Shimcache reflects the last modification date of the file, so let's review MFT to understand when it was created:
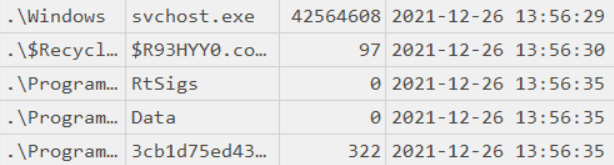
Figure 10.12 – A suspicious svchost.exe file
The creation date almost matches the modification date. Let's scroll down the MFT-based timeline to uncover more suspicious files.
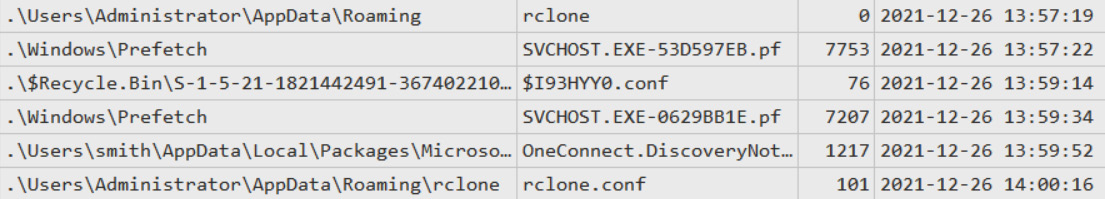
Figure 10.13 – A suspicious configuration file
In the preceding screenshot, you can see that the first rclone folder was created, followed by the rclone.conf file. It looks like it's a configuration file. Let's look inside:
[mega]
type = mega
user = [email protected]
pass = zLnoSesMMMauZfT6[redacted]
Here we have a configuration file for the MEGA account we uncovered in the previous section. Very interesting! So, apart from MEGAsync, the threat actors also used another tool to exfiltrate data: Rclone.
To make sure our initial finding matches newly uncovered evidence, let's check the properties of svchost.exe:
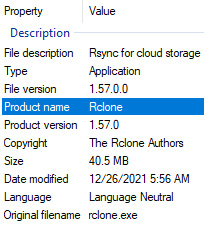
Figure 10.14 – svchost.exe properties
Now we can definitely say that the suspicious svchost.exe file is Rclone, a command-line tool for transferring content to the cloud and other high latency storage.
As you can see, very often, ransomware affiliates use various legitimate tools and web services for data exfiltration, so it's also a good idea to check for related network connections in proxy or firewall logs.
It's important to note that in some cases, the threat actor may use custom tools for data exfiltration. Let's look at one such example.
Investigating the use of custom data exfiltration tools
In 2021, some representatives of popular ransomware-as-a-service programs introduced custom data exfiltration tools as an addition to the ransomware itself. One notable example is StealBit, an information stealer distributed as part of LockBit 2.0 RaaS. Other examples include Sidoh, which was used by Ryuk ransomware affiliates, and ExMatter, which was used by BlackMatter ransomware affiliates.
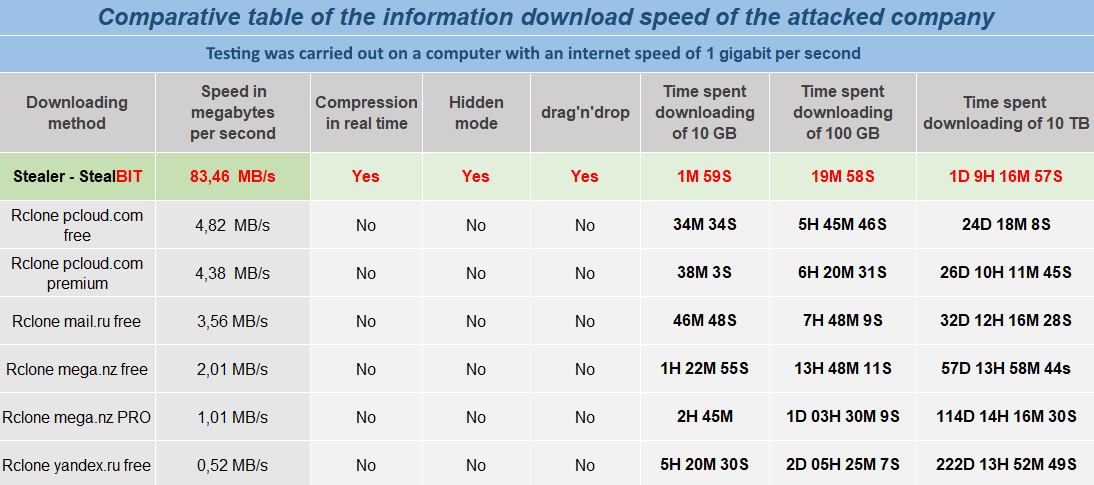
Figure 10.15 – StealBit information from LockBit 2.0 DLS
In some cases, it's really easy to spot during incident investigations – ransomware affiliates may use an executable named StealBit.exe. So, you can extract information from various sources of evidence of execution you are already well aware of, and search for files with similar names. If the threat actors prefer to use masquerading techniques, just focus on staging folders used by the attackers, or use timelines to find pivot points.
Let's discuss StealBit in more detail. First of all, just like LockBit ransomware itself, it doesn't work on computers that use the following languages: Azerbaijani, Armenian, Belarusian, Georgian, Kazakh, Kyrgyz, Moldovan, Russian, Tajik, Turkmen, Uzbek, and Ukrainian. At the same time, some newer versions don't have these checks implemented, so they can be executed on any system.
Again, just like LockBit, it uses I/O completion ports, this time not for file encryption, but for uploading files of interest to hardcoded command and control servers.
LockBit affiliates can either drag and drop files of interest to the StealBit window or specify a file or folder path as a command-line argument. The malware uses the HTTP PUT method to transfer the data of interest to the command and control server.
Also, if the -delete/-d command-line parameter is specified, StealBit deletes itself once the exfiltration process is finished. To do this, the malware executes the following commands, where <file size> is the size of the executable file and <file path> is the path to the StealBit:
ping 127.0.0.7 -n 7 > Nul
fsutil file setZeroData offset=0 length=<file size> <file path>
del /f /q <file path>
As you can see, ransomware affiliates may be very creative in their attempts to exfiltrate sensitive data, and they can use a wide variety of tools to solve this task, so it's very important for incident responders to be armed with up-to-date cyber threat intelligence.
Summary
Double-extortion has become an extremely popular tactic among ransomware gangs. Sensitive data exfiltrated from hundreds of organizations is posted online every year. So, incident responders need to be well aware of the techniques and tools commonly used by ransomware affiliates to solve this task, as well as forensic artifacts, enabling the ability to uncover such activities. We really need to understand threat actors and how they carry out their business.
In this chapter, we have looked at common approaches leveraged by threat actors to collect and exfiltrate data from a compromised network and learned which forensic artifacts can be used to uncover related traces.
In the next chapter, we'll dive into how ransomware affiliates achieve their final goal – deploying ransomware.
