Chapter 2: The Life Cycle of a Human-Operated Ransomware Attack
Human-operated ransomware attacks may be very complex, especially if we are talking about Big Game Hunting – attacks on huge enterprises. So, before diving into the technical details, it's very important to understand the life cycle of a typical attack. Understanding the attack life cycle helps security professionals to both perform proper reconstruction of an incident and make adequate decisions at various stages of the incident response life cycle.
As you already know from Chapter 1, The History of Human-Operated Ransomware Attacks, a ransomware strain can be operated by a group or multiple threat actors, if we are talking about ransomware-as-a-service programs. What does this mean? Tactics, techniques, and procedures may be quite different, but for most cases the attack life cycle will still be quite similar, as threat actors usually have two main goals – to exfiltrate sensitive information out of the target network and to deploy a piece of ransomware enterprise-wide.
In this chapter, we'll briefly discuss the various stages of human-operated ransomware attacks, so you have a solid understanding of these attacks' life cycle and be ready to dive into the technical details.
In this chapter, we'll look at the following topics:
- Initial attack vectors
- Post-exploitation
- Data exfiltration
- Ransomware deployment
Initial attack vectors
Any attack starts from an initial access. It can be an access to the internal network via a VPN, a trojan delivered via spear phishing, a web shell deployed via exploitation of public-facing application, or even a supply-chain attack.
At the same time, the three most common initial attack vectors are RDP compromise, spear phishing, and exploitation of software vulnerabilities.
For example, here are some statistics on the most common ransomware attack vectors in Q2 2021 collected by Coveware (source: https://www.coveware.com/blog/2021/7/23/q2-ransom-payment-amounts-decline-as-ransomware-becomes-a-national-security-priority):
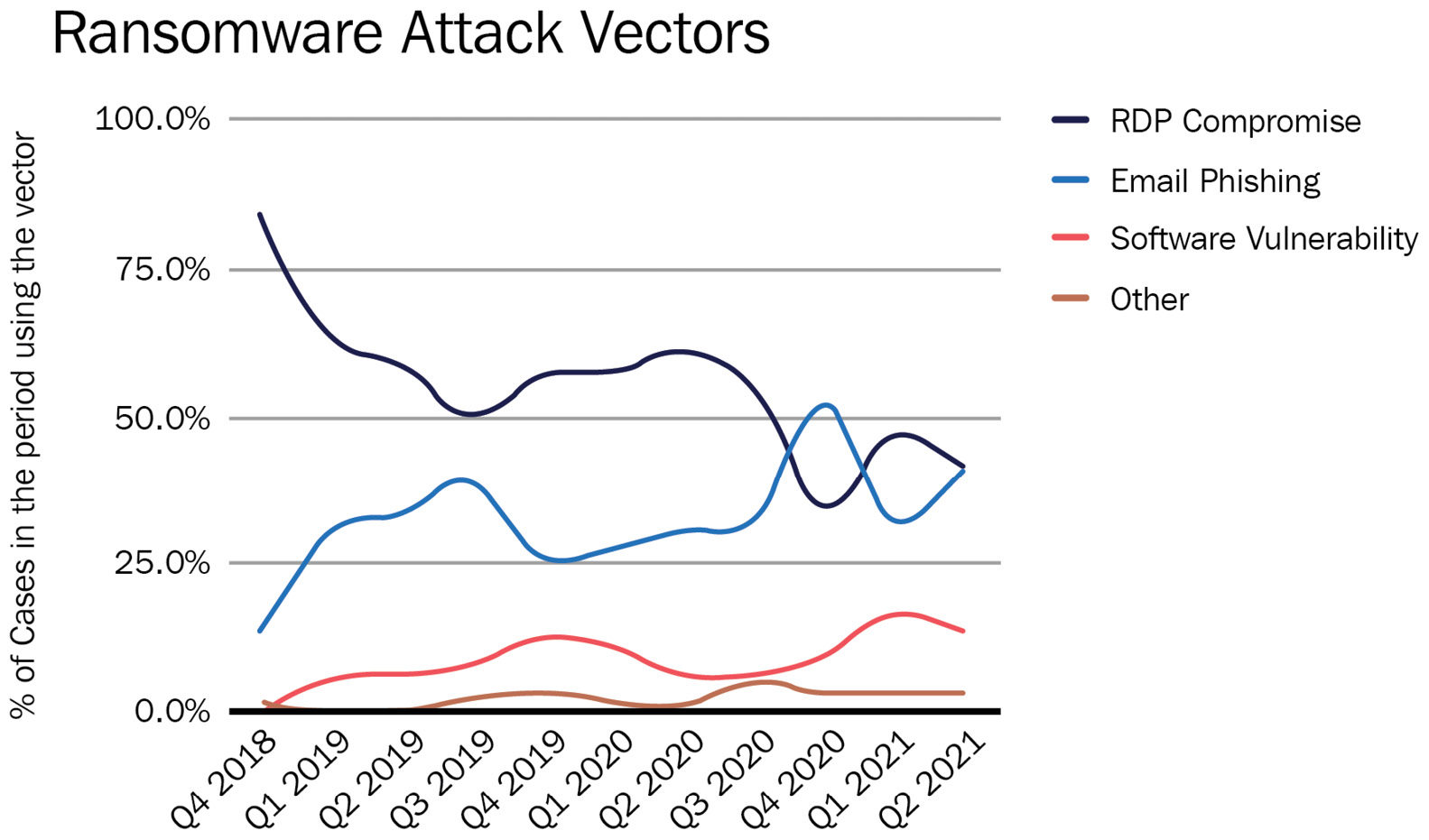
Figure 2.1 – The most common ransomware attack vectors according to Coveware
Let's look at each of them in greater detail, with examples, of course.
RDP compromise
For many years, RDP has remained the most common way for threat actors to access the target network. From Chapter 1, The History of Human-Operated Ransomware Attacks, you already know that it was the preferred way of initial access for the human-operated ransomware attacks pioneers – the SamSam operators. Of course, SamSam isn't the only example. Currently, you can see a wide range of threat actors leveraging this vector, from the more opportunistic, such as the Dharma ransomware, to the more targeted, such as REvil.
The pandemic made it even worse, as many companies had to think about providing their employees with the capability for remote working, so even more servers were exposed to the internet and, of course, became targets for threat actors of different kinds, including ransomware operators.
For example, if we use Shodan to search for publicly exposed servers with port 3389 open (the default port for RDP), we immediately see millions of devices:
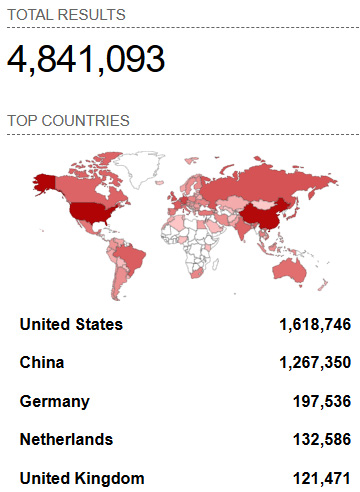
Figure 2.2 – The number of devices with port 3389 exposed to the internet
As you can see, even such a simple query gives us millions of results – this is one of the reasons this initial attack vector is so popular among ransomware operators.
In fact, threat actors do not always attempt to attack such servers themselves. They can simply buy such access, especially if we are talking about ransomware-as-a-service program affiliates. Such threat actors may not only rent ransomware, but also buy access to corporate networks from other actors, who are commonly referred to as initial access brokers. Usually, they don't focus a lot on post-exploitation activities, but rather sell initial access or even give it away for a percentage, usually up to 10%, of the potential ransom payment.
Sometimes, ransomware operators even start topics on underground forums to attract attention from the initial access brokers. For example, here's a post collected by Group-IB's Threat Intelligence and Attribution Platform, showing Crylock ransomware operators are interested in buying various types of access to corporate networks:
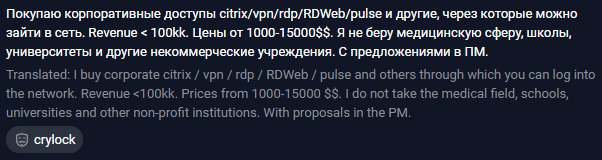
Figure 2.3 – A post on an underground forum
Let's move on and look at another extremely popular initial attack vector – spear phishing.
Spear phishing
Spear phishing, that is, using social engineering to trick targeted users into opening malicious attachments or clicking links, may be used by threat actors both to harvest credentials, which potentially could be used to gain VPN access to the target network due to password reuse, or, as you already know from Chapter 1, The History of Human-Operated Ransomware Attacks, to infect a device with a trojan.
It's true that many threat actors who used such malware mostly for banking fraud back in the day, now also use it for gaining initial access to enterprise networks.
The most common examples of such trojans include the following:
- BazarLoader
- Hancitor
- IcedID
- Qakbot
- Trickbot
Of course, this isn't a full list but, again, these are just the most common examples often observed in-the-wild as ransomware precursors.
Usually, the operators of such trojans use massive spam campaigns, targeting mainly enterprise users. The most common technique used is thread hijacking – the threat actors use compromised email addresses to send a malicious document as the reply to a previously sent legitimate email:
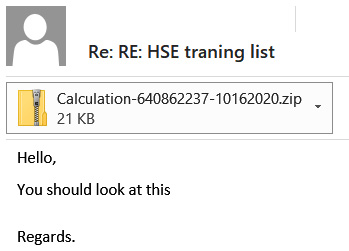
Figure 2.4 – An example of thread hijacking leveraged by Qakbot operators
In some cases, the threat actors use even more sophisticated techniques: from Chapter 1, The History of Human-Operated Ransomware Attacks, you learned that BazarLoader operators also leveraged vishing (voice phishing) in their delivery schemes.
Here's an example of such an email:
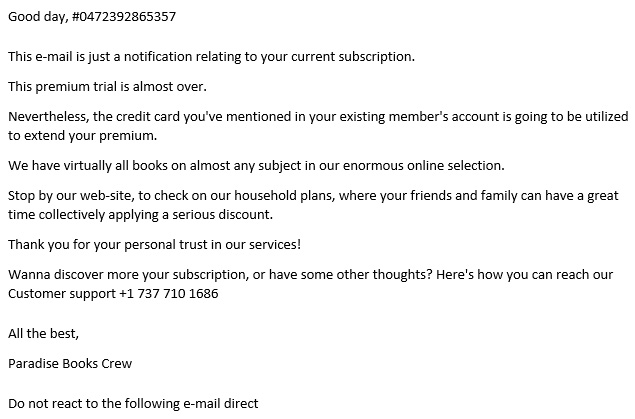
Figure 2.5 – An example of a phishing email aiming to distribute BazarLoader
As you can see, there are no malicious attachments in this case. Instead, the threat actors tells the victim not to reply to this email and to use the customer support phone number to contact the fake company and cancel the subscription.
If the victim calls, threat actors from the fake call center will guide him or her to a website where a malicious document is located, and even guide the victim to open it and enable the macros, so BazarLoader is downloaded and executed.
More technical details on the execution and persistence techniques of such trojans will be covered in the follow-up chapters; for now, just remember that they can be used by threat actors to download additional tools to the initially compromised host, so they can perform post-exploitation activities, resulting in obtaining the capability to use privileged accounts and move laterally through the network.
OK, let's finish our initial attack vectors overview by looking at various software vulnerabilities enabling ransomware operators to gain access to the target network.
Software vulnerabilities
Software vulnerabilities have allowed many initial access brokers to earn hundreds of thousands of dollars, but ransomware-as-a-service programs' affiliates have earned even more – millions.
Of course, not every vulnerability allows a threat actor to gain initial access to the network. Most commonly, these are vulnerabilities that enable remote code execution or expose files with credentials.
A good example of a vulnerability is Pulse Secure VPN appliances. For example, CVE-2019-11510 allowed threat actors to obtain usernames and plaintext passwords from vulnerable appliances to be used for accessing the network.
Another similar vulnerability actively leveraged by ransomware operators is CVE-2018-13379 in FortiGate VPN servers. It also allows an attacker to read files with plaintext credentials.
CVE-2019-19781 exploitation in Citrix ADC and Gateway instances was also a common technique for many ransomware gangs – it allowed the threat actors to download and execute malicious code remotely and perform other post-exploitation activities.
One more example is the multiple vulnerabilities in Accellion Legacy File Transfer Appliance exploited by the Cl0p ransomware gang, which included CVE-2021-27101, CVE-2021-27102, CVE-2021-27103, and CVE-2021-27104.
Finally, in some cases, threat actors manage to use even zero-day vulnerabilities – vulnerabilities in systems or devices that have been disclosed but not patched yet. In July 2021, some of the REvil affiliates successfully exploited multiple vulnerabilities in Kaseya's VSA remote management service and launched a malicious update package resulting in ransomware deployment. It affected lots of Kaseya's customers, including managed service providers, so the attackers asked for a really outstanding ransom – $70 million:
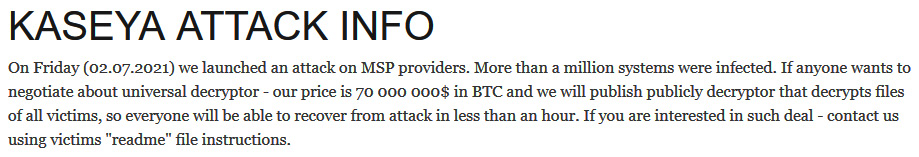
Figure 2.6 – Information about the attack on REvil's DLS
Of course, obtaining the initial access to the network isn't all – in most cases, the attackers have to elevate privileges, dump credentials, and perform network reconnaissance and other post-exploitation activities.
Post-exploitation
It can be noted and observed that gaining network access isn't the entire end game. In many cases, the threat actors still don't know much about the network, and may have access to accounts with limited privileges, so they can't disable security controls and move laterally to start achieving their goals, such as data exfiltration and ransomware deployment.
Of course, post-exploitation steps depend on the type of access. If the threat actors have VPN access, for example, they may want to scan the network for vulnerabilities, which may enable lateral movement for them.
You may be really surprised, but the notorious EternalBlue (CVE-2017-0144) is still extremely common for many enterprise networks, even if we are talking about really big enterprises.
Another very common vulnerability exploited by various ransomware operators is Zerologon (CVE-2020-1472). It allows the attackers to obtain access to the domain controller with a few clicks!
Those who rely on various trojans usually start by abusing built-in Windows tools for network and Active Directory reconnaissance, such as net.exe, nltest, and others, then continue with third-party tools downloaded to the initially compromised host. The most common examples are the following:
- AdFind
- Bloodhound (Sharphound)
- ADRecon
These tools allow the threat actors to collect information about users and groups, computers, subnets, domain trusts, and even to identify relationships within Active Directory!
If the attackers have obtained access to an initially compromised host via RDP, they usually use a wide range of tools – from network scanners to password dumpers. Some of most common tools are the following:
- SoftPerfect Network Scanner
- Advanced IP Scanner
- Mimikatz
- LaZagne
- Process Hacker
- ProcDump
- NLBrute
In some cases, especially if the attackers got the initial access to a server, they may obtain elevated credentials almost immediately, using parts of the downloaded toolset to, for example, dump a Local Security Authority Subsystem Service (LSASS) process.
Another typical characteristic of modern human-operated ransomware attacks is heavy usage of various post-exploitation frameworks. I'm almost certain you've heard about Cobalt Strike! It's the most common framework used not only by cybercriminals, but even by state-sponsored threat actors.
Of course, it's only one example. If you are responding to human-operated ransomware attacks, you may also spot the following:
- Metasploit
- PowerShell Empire
- CrackMapExec
- Koadic
- PoshC2
These toolsets allow ransomware operators to solve various tasks: scan the network, elevate privileges, dump credentials, download and execute third-party tools and scripts, move laterally using various techniques, and more.
Another important step for threat actors is to maintain redundant access. For example, they may distribute the trojans they used for initial access, run post-exploitation framework payloads on remote hosts and just install legitimate remote access software, such as TeamViewer, on some servers with internet access.
Once they learn enough about the network they have broken into and obtained elevated credentials, it's time to start achieving the main goals – exfiltrating data and deploying ransomware.
Data exfiltration
Data exfiltration is sometimes referred to as data extrusion, data exportation, or data theft, and it's extremely popular among ransomware affiliates. Almost any threat actor involved in human-operated ransomware attacks has its own Dedicated Leak Site (DLS). They use such websites to publish information about successful attacks and even exfiltrated data if a company refuses to pay the ransom.
The amount of exfiltrated data may be very different. In some cases, it's just a few gigabytes, while in others it may be terabytes. Exfiltrated data may include credit card information, Social Security numbers (SSNs), Personal Identifiable Information (PII), Protected Health Information (PHI), and National Provider Identifiers (NPIs), but are not limited to company private information and proprietary information.
Here's an example of a DLS that belongs to the Conti ransomware:
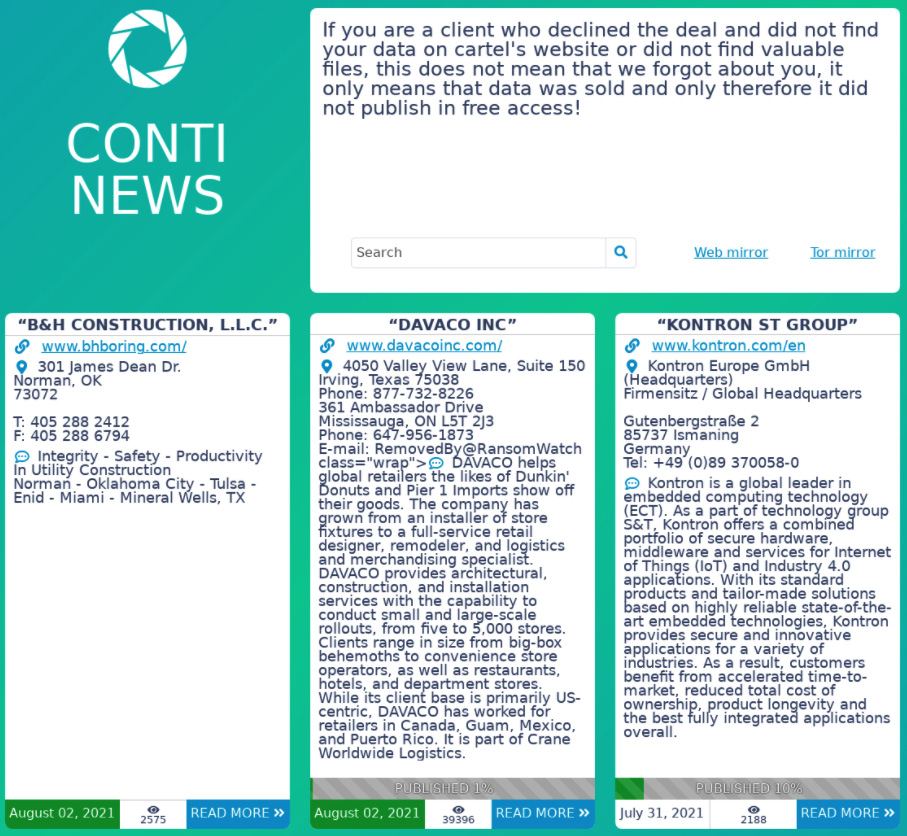
Figure 2.7 – Conti ransomware DLS
Most such websites are located on the dark web and can be accessed, for example, via Tor Browser. If you want to track changes on such websites using a regular web browser, it may be a good idea to use the Ransomwatch project (https://www.ransomwatch.org/). This website automatically captures and publishes screenshots of active DLSes belonging to various ransomware operators.
Threat actors may spend quite a lot of time exfiltrating data from the compromised network – it may continue even for a few months. Also, during this time, they may find more and more sensitive data, as well as plant additional backdoors to regain access to the compromised network environment, for example, if the initial access technique is detected and access is blocked.
Typically, there are two approaches to data exfiltration. First, the threat actors may set up a server for such purposes, or even use the same servers they use to perform the actual attack, for example, using post-exploitation frameworks.
In such cases, the attackers commonly use legitimate tools for data exfiltration, for example, WinSCP or FileZilla. Such legitimate tools may be extremely hard to detect, especially if an organization doesn't have a dedicated monitoring team as part of its security team that uses a threat-hunting approach during their day-to-day activities.
Of course, they usually collect data first, but in some cases, it can be exfiltrated directly from a file server even without archiving.
Another approach is to use public cloud storage, such as MEGA, DropMeFiles, and others. The same storage can be used by the threat actors to publish data on their DLS.
For example, here's data exfiltrated by Everest ransomware affiliates from one of their victims, which was uploaded to DropMeFiles:
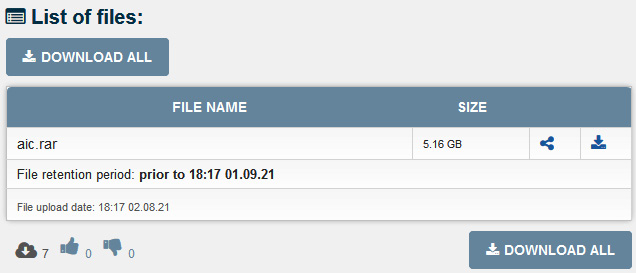
Figure 2.8 – Exfiltrated data published by Everest ransomware affiliates
To exfiltrate data this way, the threat actors may use a regular web browser or, in some cases, corresponding client applications. For example, Nefilim ransomware affiliates just installed MEGAsync on the target host and used it to exfiltrate data.
Another notable example is the Mount Locker affiliates. These threat actors used AWS S3 buckets to steal collected data. AWS and other cloud solutions are big pivot points in big targets for data exfiltration. Without the proper governance and oversight, AWS and other cloud solutions are a rich hunting ground for threat actors.
Once all sensitive data (at least from the attackers' point of view) is exfiltrated, the victim network is ready to be prepared for ransomware deployment.
Ransomware deployment
In your opinion, what's a ransomware operator's worst enemy? Yes, you're right, backups – secure and not tampered with backups. But they have a very bad weakness – they can be deleted by threat actors.
Unfortunately, system administrators often don't think about either the 3-2-1 rule (3 backup copies on 2 different media with 1 located offsite) or separate accounts and multi-factor authentication for the backup servers. What's more, nowadays, having proper secure backups isn't only important for ransomware mitigation, but also to ensure an organization meets industry regulatory requirements.
What does this mean? If the attackers obtain domain administrator credentials, they can easily access the backup servers and wipe all available backups. That's it, so the victim company has no other choice than to pay the ransom.
Also, talking about backups, some ransomware samples have built-in capabilities for wiping files with extension typical backup solutions. For example, here's a list of extensions for backup files wiped by TinyCryptor:
- .vbm
- .vib
- .vbk
- .bkf
- .vlb
- .vlm
- .iso
You may be surprised, but the Windows operating system has a built-in backup mechanism called the Volume Shadow Copy Service. It creates backup copies of files or even volumes, so the user can restore them to the previous state.
Of course, ransomware operators have taken note of this Windows feature – most ransomware samples disable this service and remove available copies.
Backups aren't the only enemy of the ransomware operator. Another enemy is security solutions, as they may easily block ransomware execution – if they are operating properly, of course.
For example, threat actors can add a ransomware sample to exclusions, or just disable available security software. At this stage, the attackers commonly have domain administrator credentials, so they can deploy batch scripts abusing Group Policy to achieve this goal. Of course, it's not the only way. Another example is to use the security software's console to disable it.
Ransomware deployment can be achieved via various techniques, including Group Policy modification, using PsExec, or even manual dropping and execution – it depends on the threat actor.
Another important point – the system should be available, so the victim can get the email or portal link to communicate with the threat actors. That's why many ransomware samples have a list of system folders in the exclusion list. For example, here's an exclusion list from a Darkside ransomware sample:
- $recycle.bin
- config.msi
- $windows.~bt
- $windows.~ws
- windows
- appdata
- application data
- boot
- mozilla
- program files
- program files (x86)
- programdata
- system volume information
- tor browser
- windows.old
- intel
- msocache
- perflogs
- x64dbg
- public
- all users
- default
It is interesting that the list contains the tor browser folder. The thing is, Darkside had a portal for victims on the dark web, which is only accessible via Tor Browser.
Once ransomware has been deployed, the threat actors are ready to negotiate with the victim regarding the ransom amount. In some cases, there are separate ransom demands for decryption and removing exfiltrated data.
In rare cases, the attack may continue. For example, REvil ransomware affiliates are known to run DDoS attacks against victims who refuse to pay.
Summary
Now you have a solid understanding of a typical human-operated ransomware attack. Of course, from a tactics, techniques, and procedures perspective, such attacks may be very different, but the main goals are almost always the same – to take full control of the domain, exfiltrate the most sensitive data, and deploy ransomware.
In the next chapter, we will look at the incident response process, and look at each of six stages from the angle of modern human-operated ransomware attacks.
