Chapter 12: The Unified Ransomware Kill Chain
Throughout this book, you have learned a lot about how exactly threat actors operate during various stages of a human-operated ransomware attack life cycle.
We have learned how to collect and produce cyber threat intelligence, as well as how to collect data from various sources and perform digital forensic analysis in order to reconstruct various stages of ransomware attacks during incident response engagements.
In this chapter, we will summarize everything we have learned by looking at various kill chains through the lens of human-operated ransomware attacks and introduce the Unified Ransomware Kill Chain.
In this chapter, we will cover the following topics:
- Cyber Kill Chain®
- MITRE ATT&CK®
- The Unified Kill Chain
- The Unified Ransomware Kill Chain
Cyber Kill Chain®
The Cyber Kill Chain® was introduced by Lockheed Martin as part of the Intelligence Driven Defense® model. This model was described in the white paper entitled Intelligence-Driven Computer Network Defense Informed by Analysis of Adversary Campaigns and Intrusion Kill Chains (https://www.lockheedmartin.com/content/dam/lockheed-martin/rms/documents/cyber/LM-White-Paper-Intel-Driven-Defense.pdf).
According to this white paper, the Cyber Kill Chain® consists of the following seven phases:
- Reconnaissance
- Weaponization
- Delivery
- Exploitation
- Installation
- Command and Control (C2)
- Actions on Objectives
Let's look at each phase in more detail.
Reconnaissance
During this phase, threat actors collect information about their target. This may include crawling-related websites and an examination of social media, as well as an examination of the target's infrastructure, especially its public-facing part.
From a ransomware perspective, this phase may include threat actors' communications with the initial access brokers, as well as collecting information on the target's revenue – it's commonly used by ransomware affiliates to form the ransom amount.
The reconnaissance phase is widely underestimated. Many times, a threat actor will recon a subject for weeks, months, and sometimes even many years. This is to ensure that they have a thorough understanding of not only what is externally facing, but also to understand the other fundamental elements of the business of the subject.
Weaponization
The original white paper describes the process of preparing a malicious document so that it can be delivered via spear phishing. At the same time, this process can be much broader. Ransomware affiliates may need to find proper exploits to gain initial access, privilege escalation, or, for example, lateral movement, setting up and configuring servers, for example, Cobalt Strike, and choose a proper toolset for the attack they are planning.
Delivery
This phase describes the method used to deliver the malicious payload. In fact, this phase could be split into two. Ransomware affiliates may need to deliver a bot, remote access tool/trojan (RAT), or, for example, a web shell to gain initial access, but they also need to deploy ransomware once post-exploitation and data exfiltration is complete.
What's more, in some cases, a separate team of threat actors may be involved at this stage, especially if access was obtained from an initial access broker.
Delivering the payload is part of the kill chain as well. However, establishing a secondary backdoor prior to deployment is usually a method that we have seen carried out by the majority of recent threat actors to ensure they do not have any loss of connection or get blocked out.
Exploitation
Commonly, this phase is associated with the exploitation of vulnerabilities in order to execute the payload. I'm sure you have already thought of a few examples – Microsoft Office-related vulnerabilities or Microsoft Exchange, depending on which technique threat actors rely on.
But there's another thing. Threat actors may exploit any vulnerability in the software, but human vulnerabilities, as you already know, involve many techniques based on phishing.
Also, especially if we are talking about ransomware deployment, threat actors may exploit various built-in features and use so-called "living-off-the-land" techniques.
"Living-off-the-land" techniques allow the threat actor to use already installed features of compromised systems to bypass defenses and perform below the radar.
Installation
During this phase, threat actors should make the payload persistent in the compromised system so that they can have redundant access to it.
If we are talking about human-operated ransomware attacks, this phase may be expanded significantly. Ransomware affiliates may use an extensive toolset, so it's not about using just one implant. They may access public-facing servers with legitimate credentials, have VPN access to the compromised network, install legitimate remote access software, and so on.
Something to note during this phase is that there may be multiple installations and staging points. Also, at certain points, there may even be decoy staging points so that the investigator is distracted from the actual installation and utilization of other tools.
Command and Control (C2)
Once the payload is installed successfully, threat actors need to be able to communicate with the compromised host from the outside.
As you already know, ransomware affiliates may use various tools and techniques: bots, RATs, web shells, and even legitimate remote access software, so communication channels largely depend on this or that threat actor's toolkit.
Actions on Objectives
This phase describes all the actions performed by threat actors in order to achieve their original objectives. This phase covers the whole post-exploitation process and may include privilege escalation, credential access, lateral movement, as well as data exfiltration and ransomware deployment.
Due to the fact that the Cyber Kill Chain® was developed quite some time ago, it now seems a bit outdated as it focuses more on the initial access stage of the attack. Let's now look at a more contemporary example – MITRE ATT&CK®.
MITRE ATT&CK®
ATT&CK is a globally accessible knowledge base of adversary strategies and procedures based on real-world observations, developed and maintained by the MITRE Corporation with the help of the global cybersecurity community.
We have already used this framework throughout this book, but I still recommend reading the following white paper, MITRE ATT&CK®: Design and Philosophy (https://attack.mitre.org/docs/ATTACK_Design_and_Philosophy_March_2020.pdf).
There are 14 adversary tactics described in MITRE ATT&CK®:
- Reconnaissance
- Resource development
- Initial access
- Execution
- Persistence
- Privilege escalation
- Defense evasion
- Credential access
- Discovery
- Lateral movement
- Collection
- Command and control
- Exfiltration
- Impact
Let's look at each tactic separately.
Reconnaissance
The adversary collects information about the target. As discussed previously, threat actors may use both passive and active methods for profiling the target and getting the information they need to initiate the attack.
There are many ways to conduct the reconnaissance phase of the attack. Some actors prefer to use dual-use tools, while others employ a manual process. There is no right or wrong answer; it's a matter of what will work and what won't.
Resource development
ATT&CK has a separate tactic for describing the stage of an attack where threat actors prepare the infrastructure – set up servers, register domains, prepare phishing emails, obtain ransomware or other types of malware and tools from third-party providers, and so on.
Initial access
Threat actors, including ransomware affiliates, may use various techniques to gain initial access to the target network. As you already know, they may exploit public-facing applications, use spear phishing, and abuse remote access services or trusted relationships to jump from one compromised network to another.
Execution
Threat actors need to execute various commands and binaries during the attack life cycle. It may be a payload that is downloaded and executed via malicious macros embedded into a Microsoft Office document, various reconnaissance commands executed via a web shell, or a ransomware binary triggered on a remote host via PsExec.
Persistence
Ransomware affiliates need to maintain their foothold, so they may use, for example, legitimate remote access software for redundant access to the compromised network, or use more traditional techniques to survive reboots, such as registry modifications or creating scheduled tasks.
Privilege escalation
In many cases, threat actors don't have proper privileges to start post-exploitation activities effectively, so they need to escalate them. Ransomware affiliates may leverage various misconfigurations and vulnerabilities to achieve it. Also, some persistence techniques enable privilege escalation.
Defense evasion
Ransomware deployment is almost impossible without disabling security products implemented in the target environment. What is more, threat actors need to avoid detection throughout the attack life cycle, so they obfuscate/encrypt their toolset and remove artifacts and logs in order to make the investigation and response process more difficult.
Credential access
Usually, ransomware affiliates need to access various servers during the attack life cycle, for example, for data exfiltration or backup removal. So, they require proper credentials to solve this task. You already know that they may dump them from memory, extract them from various password stores, or, for example, run a kerberoasting attack.
Discovery
To exfiltrate the most sensitive data and deploy ransomware on as many hosts as possible, threat actors need to perform proper reconnaissance. This may include collecting information about installed software, accounts, network shares, and remote hosts.
Lateral movement
Ransomware affiliates mostly target corporate networks, so they need to jump from one compromised system to another. In most cases, they use legitimate credentials and protocols, such as RDP and SMB.
Collection
Ransomware affiliates need to collect sensitive data before exfiltration and placement on the DLS. Threat actors may collect data from local systems, network shared drives, emails, and other sources of sensitive data.
Command and control
Threat actors need to communicate with compromised systems. To avoid detection, ransomware affiliates may mimic normal traffic, obfuscate or encrypt transferred data, or, for example, use a connection proxy.
Exfiltration
Ransomware affiliates may exfiltrate collected data using the main C2 channel, as well as using various web services. Before exfiltration, data can be archived and/or encrypted.
Impact
The main goal of most ransomware affiliates is to encrypt data on target systems. At the same time, they always attempt to inhibit system recovery, destroying both built-in and third-party backups.
Of course, both models have their advantages and disadvantages, so some researchers combine them to create something new. A good example is the Unified Kill Chain.
The Unified Kill Chain
The Unified Kill Chain merges and extends the Cyber Kill Chain® and MITRE ATT&CK®. It was developed by Paul Pols in his master's thesis, Modeling Fancy Bear Attacks: Unifying the Cyber Kill Chain.
The white paper is available here: https://www.unifiedkillchain.com/assets/The-Unified-Kill-Chain.pdf.
The Unified Kill Chain splits the attack life cycle into three main stages: Initial Foothold, Network Propagation, and Action on Objectives. Let's look at each stage separately.
Initial Foothold
The first stage describes the steps performed by threat actors to gain access to the target system or network.
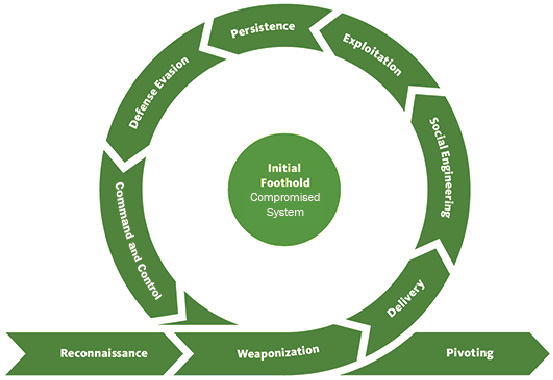
Figure 12.1 – The steps of the Initial Foothold stage
The life cycle starts with researching the target (Reconnaissance). Then, ransomware affiliates need to prepare the infrastructure: malware (including ransomware) and other weaponized objects, as well as C2 infrastructure, and so on (Weaponization). If weaponized objects are used, for example, malicious documents, they should be delivered to the target (Delivery). Threat actors should either trick the victim into downloading and opening a malicious file (Social Engineering) or exploit a vulnerability to execute it (Exploitation). Once the malicious or weaponized object is executed, threat actors may need to acquire persistent access to the compromised system (Persistence). To start pivoting, threat actors should bypass defenses (Defense Evasion), as well as being able to communicate with the initially compromised system (Command and Control).
Network Propagation
Once ransomware affiliates have gained an initial foothold in the target network, they are ready to pivot to the next stage – Network Propagation.
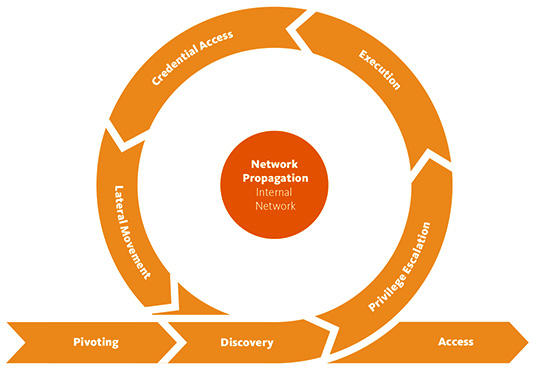
Figure 12.2 – The steps of the Network Propagation stage
Threat actors need to collect information about the compromised system in order to understand current privileges and accesses (Discovery). If current privileges are not enough, threat actors may escalate them, for example, via exploiting a vulnerability (Privilege Escalation). With elevated privileges, ransomware affiliates can execute arbitrary code on the compromised system (Execution). The ability to execute arbitrary code enables threat actors to obtain credential material (Credential Access). With the proper credentials, ransomware affiliates may discover remote systems (Discovery) and start moving laterally (Lateral Movement), so they can start performing actions on the objectives of the attack.
Actions on Objectives
With proper credentials and the ability to move laterally, ransomware affiliates can move to the final stage – Actions on Objectives.
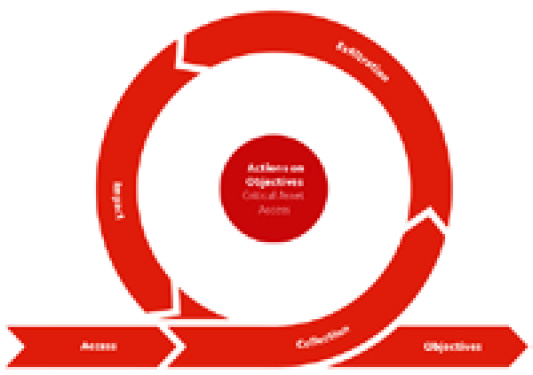
Figure 12.3 – The steps of the Actions on Objectives stage
As you already well know, in many human-operated ransomware attacks, one of the main goals of threat actors is to access sensitive data. Once such data is discovered, it's collected (Collection) and then exfiltrated (Exfiltration). After achieving this goal, threat actors are usually ready to move to the final stage – ransomware deployment (Impact).
OK. We have looked at various kill chains, and now it's time to build our own – the Unified Ransomware Kill Chain.
The Unified Ransomware Kill Chain
Throughout this book we have consumed quite a lot of cyber threat intelligence related to ransomware attacks, as well as looked at the most common techniques used by threat actors from a forensic perspective, so we have a good understanding of human-operated ransomware attacks and are ready to build a unique kill chain.
Gain Access to the Network
Ransomware affiliates may gain access to the target network themselves or purchase such access from the initial access brokers. Access may be granted to a certain host in the network, or to the network itself, for example, via compromised VPN credentials.
Ransomware affiliates may employ a wide range of techniques to gain access, from quite common techniques, such as brute-force attacks and phishing emails, to more advanced techniques, such as supply chain attacks.
Establish Foothold
This stage may include various activities. Ransomware affiliates may need to collect information about the compromised host, find ways to elevate privileges and access credentials, as well as disabling or bypassing defenses to initiate network discovery and propagation.
Also, ransomware affiliates may need to gain persistent access to the compromised system and organize redundant access to it.
Network Discovery
Before starting network propagation, ransomware affiliates need to collect information about remote systems so that they can understand where they should pivot first.
Key Assets Discovery
Of course, not every host is equally valuable for threat actors. Mostly, they are interested in assets where they can acquire additional privileged credentials, sensitive information for collection and exfiltration, and, of course, backups!
Network Propagation
To gain access to the most valuable assets, ransomware affiliates need to move laterally through the network. As you already know, they commonly use legitimate tools and techniques to enable this capability.
Data Exfiltration
In some cases, ransomware affiliates may exfiltrate data just from one host, for example, a file server. At the same time, threat actors may collect and exfiltrate data from multiple sources. In some cases, such activity may last a month or even longer.
Despite the fact that data exfiltration is a trend for modern human-operated ransomware attacks, sometimes, threat actors skip this stage.
Deployment Preparation
Many compromised environments have at least some security products implemented and backups available, so threat actors need to disable and remove them prior to ransomware deployment.
Ransomware Deployment
At this stage, threat actors attempt to achieve their main goal – deploy ransomware. It's important to note that in some cases, they may not even use malicious code and could encrypt data with legitimate tools such as BitLocker and DiskCryptor.
Most ransomware is very noisy and easily detected, so threat actors try to find new ways to bypass defenses and achieve their goals.
Extortion
Encrypting the whole network and waiting for a response from the victim may not be very effective, so ransomware affiliates are finding new ways to facilitate extortion. They may put samples of exfiltrated data on the DLS, call the victims' employees, and even perform DDoS attacks against already compromised infrastructure.
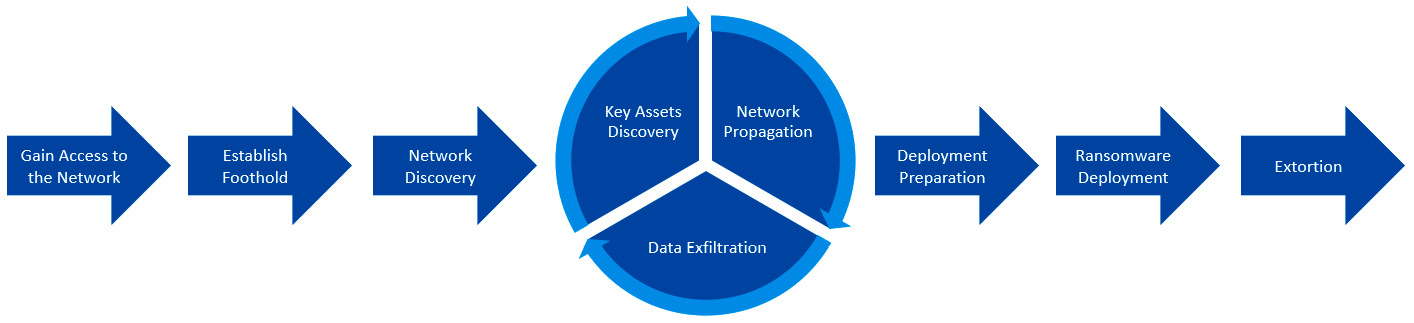
Figure 12.4 – The Unified Ransomware Kill Chain
As you can see, three stages are looped as ransomware affiliates may perform the same activities on multiple hosts.
The Unified Ransomware Kill Chain can easily be used by incident responders to reconstruct a ransomware attack during the engagement and structure the final report, so each stage of the attack is easy to understand and you have enough artifacts to describe it.
Summary
Throughout this book, you've learned a lot about modern human-operated ransomware attacks. Now you can find and monitor various cyber threat intelligence sources.
You clearly understand the ransomware attack life cycle and can use various kill chains, including the Unified Ransomware Kill Chain, to reconstruct such attacks, and you know the most common forensic artifacts, which may help you to solve this task.
I hope this book will help you in your current or future incident response engagements, as well as helping you better understand the current threat landscape related to human-operated ransomware attacks.
One other important note; you shouldn't just focus on default forensic artifacts described in this book as some environments may have quite useful third-party sources, such as SIEMs and EDEs. Use as much data as possible – this will allow you to reconstruct the attack in as much detail as possible and build proper protection to save your (or your client's) network from such threats.
