To develop an information governance (IG) policy, you must inform and frame the policy with internal and external frameworks, models, best practices, and standards—those that apply to your organization and the scope of its planned IG program. In this chapter, we first present and discuss major IG frameworks and models and then identify key standards for consideration.
A Brief Review of Generally Accepted Recordkeeping Principles®
In Chapter 3 we introduced and discussed ARMA International's eight Generally Accepted Recordkeeping Principles®, known as The Principles1 (or sometimes GAR Principles). These Principles and associated metrics provide an IG framework that can support continuous improvement.
To review, the eight Principles are:
- Accountability
- Transparency
- Integrity
- Protection
- Compliance
- Availability
- Retention
- Disposition2
The Principles establish benchmarks for how organizations of all types and sizes can build and sustain compliant, legally defensible records management (RM) programs. Using the maturity model (also presented in Chapter 3), organizations can assess where they are in terms of IG, identify gaps, and take steps to improve across the eight areas The Principles cover.
IG Reference Model
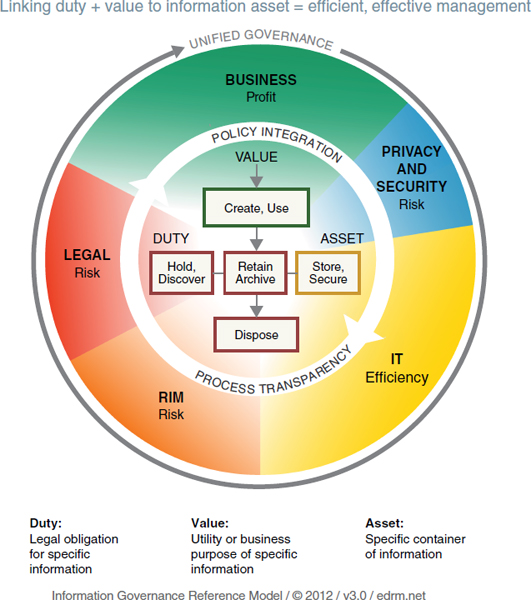
In late 2012, with the support and collaboration of ARMA International and the Compliance, Governance and Oversight Council (CGOC), the Electronic Discovery Reference Model (EDRM) Project released version 3.0 of its Information Governance Reference Model (IGRM), which added information privacy and security “as primary functions and stakeholders in the effective governance of information.”3 The model is depicted in Figure 6.1.
The IGRM is aimed at fostering IG adoption by facilitating communication and collaboration between disparate (but overlapping) IG stakeholder functions, including information technology (IT), legal, RM, risk management, and business unit stakeholders.4 It also aims to provide a common, practical framework for IG that will foster adoption of IG in the face of new Big Data challenges and increased legal and regulatory demands. It is a clear snapshot of where IG touches and shows critical interrelationships and unified governance.5 It can help organizations forge policy in an orchestrated way and embed critical elements of IG policy across functional groups. Ultimately, implementation of IG helps organizations leverage information value, reduce risk, and address legal demands.
Figure 6.1 Information Governance Reference Model
Source: EDRM.net
You must inform and frame IG policy with internal and external frameworks, models, best practices, and standards.
The growing CGOC community (2,000+ members and rising) has widely adopted the IGRM and developed a process maturity model that accompanies and leverages IGRM v3.0.6
Interpreting the IGRM Diagram*
Outer Ring
Starting from the outside of the diagram, successful information management is about conceiving a complex set of interoperable processes and implementing the procedures and structural elements to put them into practice. It requires:
- An understanding of the business imperatives of the enterprise,
- Knowledge of the appropriate tools and infrastructure for managing information, and
- Sensitivity to the legal and regulatory obligations with which the enterprise must comply.
For any piece of information you hope to manage, the primary stakeholder is the business user of that information [emphasis added]. We use the term “business” broadly; the same ideas apply to end users of information in organizations whose ultimate goal might not be to generate a profit.
Once the business value is established, you must also understand the legal duty attached to a piece of information. The term “legal” should also be read broadly to refer to a wide range of legal and regulatory constraints and obligations, from e-discovery and government regulation to contractual obligations such as payment card industry requirements.
Finally, IT organizations must manage the information accordingly, ensuring privacy and security as well as appropriate retention as dictated by both business and legal or regulatory requirements.
Center
In the center of the diagram is a work-flow or life-cycle diagram. We include this component in the diagram to illustrate the fact that information management is important at all stages of the information life cycle—from its creation through its ultimate disposition. This part of the diagram, once further developed, along with other secondary-level diagrams, will outline concrete, actionable steps that organizations can take in implementing information management programs.
Even the most primitive business creates information in the course of daily operations, and IT departments spring up to manage the logistics; indeed, one of the biggest challenges in modern organizations is trying to stop individuals from excess storing and securing of information. Legal stakeholders can usually mandate the preservation of what is most critical, though often at great cost. However, it takes the coordinated effort of all three groups to defensibly dispose of a piece of information that has outlived its usefulness and retain what is useful in a way that enables accessibility and usability for the business user.
How the IGRM Complements the Generally Accepted Recordkeeping Principles*
AU: We have inserted astric on h2 for footnote, please suggest.
The IGRM supports ARMA International's “Principles” by identifying the cross-functional groups of key information governance stakeholders and by depicting their intersecting objectives for the organization. This illustration of the relationship among duty, value, and the information asset demonstrates cooperation among stakeholder groups to achieve the desired level of maturity of effective information governance.
Effective IG requires a continuous and comprehensive focus. The IGRM will be used by proactive organizations as an introspective lens to facilitate visualization and discussion about how best to apply The Principles. The IGRM puts into sharp focus The Principles and provides essential context for the maturity model.
Information management is important at all stages of the life cycle.
Legal stakeholders can usually mandate the preservation of what is most critical, though often at great cost.
The IGRM was developed by the EDRM Project to foster communication among stakeholders and adoption of IG. It complements ARMA's Generally Accepted Recordkeeping Principles.
Best Practices Considerations
IG best practices should also be considered in policy formulation. Best practices in IG are evolving and expanding, and those that apply to organizational scenarios may vary. A best practices review should be conducted, customized for each particular organization.
In Chapter 5, we provided a list of 25 IG best practices, with some detail. The IG world is maturing, and more best practices will evolve. The 25 best practices, summarized next, are fairly generic and widely applicable.
- IG is a key underpinning for a successful ERM program.
- IG is not a project but rather an ongoing program.
- Using an IG framework or maturity model is helpful in assessing and guiding IG programs.
- Defensible deletion of data debris and information that no longer has value is critical in the era of Big Data.
- IG policies must be developed before enabling technologies are added to assist in enforcement.
- To provide comprehensive e-document security throughout a document's life cycle, documents must be secured upon creation using highly sophisticated technologies, such as information rights management (IRM) technology.
- A records retention schedule and legal hold notification process (LHN) are the two primary elements of a fundamental IG program.
- A cross-functional team is required to implement IG.
- The first step in information risk planning is to consider the applicable laws and regulations that apply to your organization in the jurisdictions in which it conducts business.
- A risk profile is a basic building block in enterprise risk management, assisting executives in understanding the risks associated with stated business objectives and in allocating resources within a structured evaluation approach or framework.
- An information risk mitigation plan is a critical part of the IG planning process. An information risk mitigation plan involves developing risk mitigation options and tasks to reduce the specified risks and improve the odds of achieving business objectives.7
- Proper metrics are required to measure the conformance and performance of your IG program.
- IG programs must be audited for effectiveness.
- An enterprise-wide retention schedule is preferable because it eliminates the possibility that different business units will have different records retention periods.
- Senior management must set the tone and lead sponsorship for vital records program governance and compliance.
- Business processes must be redesigned to improve the management of electronic records or implement an electronic records management (ERM) system.
- E-mail messages, both inbound and outbound, should be archived automatically and (preferably) in real time.
- Personal archiving of e-mail messages should be disallowed.
- Destructive retention of e-mail helps to reduce storage costs and legal risk while improving “findability” of critical records.
- Take a practical approach and limit cloud use to documents that do not have long retention periods and carry a low litigation risk.
- Manage social media content by IG policies and monitor it with controls that ensure protection of critical information assets and preservation of business records.
- International and national standards provide effective guidance for implementing IG.
- Creating standardized metadata terms should be part of an IG effort that enables faster, more complete, and more accurate searches and retrieval of records.8
- Some digital information assets must be preserved permanently as part of an organization's documentary heritage.
- Executive sponsorship is crucial.
Standards Considerations
Standards must also be considered in policy development. There are two general types of standards: de jure and de facto. De jure (“the law”) standards are those published by recognized standards-setting bodies, such as the International Organization for Standardization (ISO), American National Standards Institute (ANSI), National Institute of Standards and Technology (NIST—this is how most people refer to it, as they do not know what the acronym stands for), British Standards Institute (BSI), Standards Council of Canada, and Standards Australia. Standards promulgated by authorities such as these have the formal status of standards.
De facto (“the fact”) standards are not formal standards but are regarded by many as if they were. They may arise though popular use (e.g., Windows at the business desktop in the 2001–2010 decade) or may be published by other bodies, such as the U.S. National Archives and Records Administration (NARA) or Department of Defense (DoD) for the U.S. military sector. They may also be published by formal standards-setting bodies without having the formal status of a “standard” (such as some technical reports published by ISO).9
Benefits and Risks of Standards
Some benefits of developing and promoting standards are:
- Quality assurance support. If a product meets a standard, you can be confident of a certain level of quality.
- Interoperability support. Some standards are detailed and mature enough to allow for system interoperability between different vendor platforms.
- Implementation frameworks and certification checklists. These help to provide guides for projects and programs to ensure all necessary steps are taken.
- Cost reduction, due to supporting uniformity of systems. Users have lower maintenance requirements and training and support costs when systems are more uniform.
- International consensus. Standards can represent “best practice” recommendations based on global experiences.10
Some downside considerations are:
- Possible decreased flexibility in development or implementation. Standards can, at times, act as a constraint when they are tied to older technologies or methods, which can reduce innovation.
- “Standards confusion” from competing and overlapping standards. For instance, an ISO standard may be theory-based and use different terminology, whereas regional or national standards are more specific, applicable, and understandable than broad international ones.
- Real-world shortcomings due to theoretical basis. Standards often are guides based on theory rather than practice.
- Changing and updating requires cost and maintenance. There are costs to developing, maintaining, and publishing standards.11
Key Standards Relevant to IG Efforts
Below we introduce and discuss some established standards that should be researched and considered as a foundation for developing IG policy.
Risk Management
ISO 31000:2009 is a broad, industry-agnostic (not specific to vertical markets) risk management standard. It states “principles and generic guidelines” of risk management that can be applied to not only IG but also to a wide range of organizational activities and processes throughout the life of an organization.12 It provides a structured framework within which to develop and implement risk management strategies and programs.
ISO 31000 defines a risk management framework as a set of two basic components that “support and sustain risk management throughout an organization.”13 The stated components are: foundations, which are high level and include risk management policy, objectives, and executive edicts; and organizational arrangements, which are more specific and actionable, including strategic plans, roles and responsibilities, allocated budget, and business processes that are directed toward managing an organization's risk.
Additional risk management standards may be relevant to your organization's IG policy development efforts, depending on your focus, scope, corporate culture, and demands of your IG program executive sponsor.
Information Security and Governance
ISO/IEC 27001:2005 is an information security management system (ISMS) standard that provides guidance in the development of security controls to safeguard information assets. Like ISO 31000, the standard is applicable to all types of organizations, irrespective of vertical industry.14 It “specifies the requirements for establishing, implementing, operating, monitoring, reviewing, maintaining and improving a documented information security management system within the context of the organization's overall business risks.”
ISO/IEC 27001 is flexible enough to be applied to a variety of activities and processes when evaluating and managing information security risks, requirements, and objectives, and compliance with applicable legal and regulatory requirements. This includes use of the standards guidance by internal and external auditors as well as internal and external stakeholders (including customers and potential customers).
ISO/IEC 27002:2005, “Information Technology—Security Techniques—Code of Practice for Information Security,”15
establishes guidelines and general principles for initiating, implementing, maintaining, and improving information security management in an organization and is identical to the previous published standard, ISO 17799. The objectives outlined provide general guidance on the commonly accepted goals of information security management. ISO/IEC 27002:2005 contains best practices of control objectives and controls in the following areas of information security management:
- security policy;
- organization of information security;
- asset management;
- human resources security;
- physical and environmental security;
- communications and operations management;
- access control;
- information systems acquisition, development, and maintenance;
- information security incident management;
- business continuity management; and
- compliance.
The control objectives and controls in ISO/IEC 27002:2005 are intended to be implemented to meet the requirements identified by a risk assessment. ISO/IEC 27002:2005 is intended as a common basis and practical guideline for developing organizational security standards and effective security management practices, and to help build confidence in inter-organizational activities.
ISO/IEC 27001 and ISO/IEC 27002 are information security management systems standards that provide guidance in the development of security controls.
ISO/IEC 38500:2008 is an international standard that provides high-level principles and guidance for senior executives and directors, and those advising them, for the effective and efficient use of IT.16 Based primarily on AS 8015, the Australian IT governance standard, it “applies to the governance of management processes” that are performed at the IT service level, but the guidance assists executives in monitoring IT and ethically discharging their duties with respect to legal and regulatory compliance of IT activities.
The ISO 38500 standard comprises three main sections:
- Scope, Application and Objectives
- Framework for Good Corporate Governance of IT
- Guidance for Corporate Governance of IT
It is largely derived from AS 8015, the guiding principles of which were:
- Establish responsibilities
- Plan to best support the organization
- Acquire validly
- Ensure performance when required
- Ensure conformance with rules
- Ensure respect for human factors
The standard also has relationships with other major ISO standards, and embraces the same methods and approaches. It is certain to have a major impact upon the IT governance landscape.17
Records and E-Records Management
ISO 15489–1:2001 is the international standard for RM. It identifies the elements of RM and provides a framework and high-level overview of RM core principles. RM is defined as the “field of management responsible for the efficient and systematic control of the creation, receipt, maintenance, use and disposition of records, including the processes for capturing and maintaining evidence of and information about business activities and transactions in the form of records.”18
ISO 38500 is an international standard that provides high-level principles and guidance for senior executives and directors responsible for IT governance.
The second part of the standard, ISO 15489–2:2001, contains the technical specifications and a methodology for implementing the standard, originally based on early standards work in Australia (Design and Implementation of Recordkeeping Systems—DIRKS). Note: Although still actively used in Australian states, the National Archives of Australia has not recommended use of DIRKS by Australian national agencies since 2007 and has removed DIRKS from its Web site.)19
The ISO 15489 standard makes little mention of electronic records, as it is written to address all kinds of records; nonetheless it was widely viewed as the definitive framework of what RM means.
In 2008, the International Council on Archives (ICA) formed a multinational team of experts to develop “Principles and Functional Requirements for Records in Electronic Office Environments,” commonly referred to as ICA-Req.20 The project was cosponsored by the Australasian Digital Recordkeeping Initiative (ADRI), which was undertaken by the Council of Australasian Archives and Records Authorities, which “comprises the heads of the government archives authorities of the Commonwealth of Australia, New Zealand, and each of the Australian States and Territories.”21 The National Archives of Australia presented a training and guidance manual to assist in implementing the principles at the 2012 International Congress on Archives Congress in Brisbane, Australia.
In Module 1 of ICA-Req, principles are presented in a high-level overview; Module 2 contains specifications for electronic document and records management systems (EDRMS) that are “globally harmonized”; and Module 3 contains a requirements set and “implementation advice for managing records in business systems.”22 Module 3 recognizes that digital recordkeeping does not have to be limited to the EDRMS paradigm—the insight that has now been picked up by “Modular Requirements for Records Systems” (MoReq2010, the European standard released in 2011).23
Parts 1 to 3 of ISO 16175 were fully adopted in 2010–2011 based on the ICA-Req standard. The standard may be purchased at www.ISO.org, and additional information on the Australian initiative may be found at www.adri.gov.au.
ISO 16175 is guidance, not a standard that can be tested and certified against. This is the criticism by advocates of testable, certifiable standards like U.S. DoD 5015.2 and the European standard, MoReq2010.
In November 2011, ISO issued new standards for ERM, the first two in the ISO 30300 series, which are based on a managerial point of view and targeted at a management-level audience rather than at records managers or technical staff:
- ISO 30300:2011, “Information and Documentation—Management Systems for Records—Fundamentals and Vocabulary”
- ISO 30301:2011, “Information and Documentation—Management Systems for Records—Requirements”
ISO 15489 is the international RM standard.
The ICA-Req standard was adopted as ISO 16175. It does not contain a testing regime for certification.
The standards apply to “management systems for records” (MSR), a term that, as of this printing, is not typically used to refer to ERM or RM application [RMA] software in the United States or Europe and is not commonly found in ERM research or literature.
The ISO 30300 series is a systematic approach to the creation and management of records that is “aligned with organizational objectives and strategies.” [italics added]24
“ISO 30300 MSR ‘Fundamentals and Vocabulary’ explains the rationale behind the creation of an MSR and the guiding principles for its successful implementation. and it provides the terminology that ensures that it is compatible with other management systems standards.
ISO 30301 MSR ‘Requirements’ specifies the requirements necessary to develop a records policy. It also sets objectives and targets for an organization to implement systemic improvements. This is achieved through designing records processes and systems; estimating the appropriate allocation of resources; and establishing benchmarks to monitor, measure, and evaluate outcomes. These steps help to ensure that corrective action can be taken and continuous improvements are built into the system in order to support an organization in achieving its mandate, mission, strategy, and goals.”25
Major National and Regional ERM Standards
For great detail on national and regional standards related to ERM, see the book Managing Electronic Records: Methods, Best Practices, and Technologies (Wiley 2013) by Robert F. Smallwood. Below is a short summary:
United States E-Records Standard
The U.S. Department of Defense 5015.2 Design Criteria Standard for Electronic Records Management Software Applications, standard was established in 1997 and is endorsed by the leading archival authority, the U.S. National Archives and Records Administration (NARA). There is a testing regime that certifies software vendors that is administered by JITC. JITC “builds test case procedures, writes detailed and summary final reports on 5015.2-certified products, and performs on-site inspection of software.”26 The DoD standard was built for the defense sector, and logically “reflects its government and archives roots.”
Since its endorsement by NARA, the standard has been the key requirement for ERM system vendors to meet, not only in U.S. public sector bids, but also in the commercial sector.
The 5015.2 standard has since been updated and expanded, in 2002 and 2007, to include requirements for metadata, e-signatures and Privacy and Freedom of Information Act requirements, and, as previously stated, was scheduled for update by 2013.
The U.S. DoD 5015.2-STD has been the most influential worldwide since it was first introduced in 1997. It best suits military applications.
The 5015.2 standard has been updated to include specifications such as those for e-signatures and FOI requirements.
Canadian Standards and Legal Considerations for Electronic Records Management*
The National Standards of Canada for electronic records management are: (1) Electronic Records as Documentary Evidence CAN/CGSB-72.34–2005 (“72.34”), published in December 2005; and, (2) Microfilm and Electronic Images as Documentary Evidence CAN/CGSB-72.11–93, first published in 1979 and updated to 2000 (“72.11”).27 72.34 incorporates all that 72.11 deals with and is therefore the more important of the two. Because of its age, 72.11 should not be relied upon for its “legal” content. However, 72.11 has remained the industry standard for “imaging” procedures—converting original paper records to electronic storage. The Canada Revenue Agency has adopted these standards as applicable to records concerning taxation.28
72.34 deals with these topics: (1) management authorization and accountability; (2) documentation of procedures used to manage records; (3) “reliability testing” of electronic records according to existing legal rules; (4) the procedures manual and the chief records officer; (5) readiness to produce (the “prime directive”); (6) records recorded and stored in accordance with “the usual and ordinary course of business” and “system integrity,” being key phrases from the Evidence Acts in Canada; (7) retention and disposal of electronic records; (8) backup and records system recovery; and, (9) security and protection. From these standards practitioners have derived many specific tests for auditing, establishing, and revising electronic records management systems.29
The “prime directive” of these standards states: “An organization shall always be prepared to produce its records as evidence.”30 The duty to establish the “prime directive” falls upon senior management:31
5.4.3 Senior management, the organization's own internal law-making authority, proclaims throughout the organization the integrity of the organization's records system (and, therefore, the integrity of its electronic records) by establishing and declaring:
- the system's role in the usual and ordinary course of business;
- the circumstances under which its records are made; and
- its prime directive for all RMS [records management system] purposes, i.e., an organization shall always be prepared to produce its records as evidence. This dominant principle applies to all of the organization's business records, including electronic, optical, original paper source records, microfilm, and other records of equivalent form and content.
Being the “dominant principle” of an organization's electronic records management system, the duty to maintain compliance with the “prime directive” should fall upon its senior management.
Legal Considerations
Because an electronic record is completely dependent upon its ERM system for everything, compliance with these National Standards and their “prime directive” should be part of the determination of the “admissibility” (acceptability) of evidence and of electronic discovery in court proceedings (litigation) and in regulatory tribunal proceedings.32
There are 14 legal jurisdictions in Canada: 10 provinces, 3 territories, and the federal jurisdiction of the Government of Canada. Each has an Evidence Act (the Civil Code in the province of Quebec33), which applies to legal proceedings within its legislative jurisdiction. For example, criminal law and patents and copyrights are within federal legislative jurisdiction, and most civil litigation comes within provincial legislative jurisdiction.34
The admissibility of records as evidence is determined under the “business record” provisions of the Evidence Acts.35 They require proof that a record was made “in the usual and ordinary course of business,” and of “the circumstances of the making of the record.” In addition, to obtain admissibility for electronic records, most of the Evidence Acts contain electronic record provisions, which state that an electronic record is admissible as evidence on proof of the “integrity of the electronic record system in which the data was recorded or stored.”36 This is the “system integrity” test for the admissibility of electronic records. The word “integrity” has yet to be defined by the courts.37
However, by way of sections such as the following, the electronic record provisions of the Evidence Acts make reference to the use of standards such as the National Standards of Canada:
For the purpose of determining under any rule of law whether an electronic record is admissible, evidence may be presented in respect of any standard, procedure, usage or practice on how electronic records are to be recorded or stored, having regard to the type of business or endeavor that used, recorded, or stored the electronic record and the nature and purpose of the electronic record.38
U.K. and European Standards
In the United Kingdom, The National Archives (TNA) (formerly the Public Record Office, or PRO) “has published two sets of functional requirements to promote the development of the electronic records management software market (1999 and 2002).” It ran a program to evaluate products against the 2002 requirements.39 Initially these requirements were established in collaboration with the central government, and they later were utilized by the public sector in general, and also in other nations. The National Archives 2002 requirements remain somewhat relevant, although no additional development has been underway for years. It is clear that the second version of Model Requirements for Management of Electronic Records, MoReq2, largely supplanted the UK standard, and subsequently the newer MoReq2010 may further supplant the UK standard.
MoReq2010 “unbundles” some of the core requirements in MoReq2, and sets out functional requirements in modules. The approach seeks to permit the later creation of e-records software standards in various vertical industries such as defense, health care, financial services, and legal services.
MoReq2010 is available free—all 525 pages of it (by comparison, the U.S. DoD 5015.2 standard is less than 120 pages long). For more information on MoReq2010, visit www.moreq2010.eu. The entire specification may be downloaded at: http://moreq2010.eu/pdf/moreq2010_vol1_v1_1_en.pdf.
MoReq2010
In November 2010, the DLM Forum, a European Commission–supported body, announced the availability of the final draft of the MoReq2010 specification for electronic records management systems (ERMS), following extensive public consultation. The final specification was published in mid-2011.40
The DLM Forum explains that “With the growing demand for [electronic] records management, across a broad spectrum of commercial, not-for-profit, and government organizations, MoReq2010 provides the first practical specification against which all organizations can take control of their corporate information. IT software and services vendors are also able to have their products tested and certified that they meet the MoReq2010 specification.”41
MoReq2010 supersedes its predecessor MoReq2 and has the continued support and backing of the European Commission.
Australian ERM and Records Management Standards
Australia has adopted all three parts of ISO 16175 as its e-records management standard.42 (For more detail on this standard go to ISO.org.)
Australia has long led the introduction of highly automated electronic document management systems and records management standards. Following the approval and release of the AS 4390 standard in 1996, the international records management community began work on the development of an International standard. This work used AS 4390–1996 Records Management as its starting point.
Development of Australian Records Standards
In 2002 Standards Australia published a new Australian Standard on records management, AS ISO 15489, based on the ISO 15489 international records management standard. It differs only in its preface verbiage.43 AS ISO 15489 carries through all these main components of AS 4390, but internationalizes the concepts and brings them up to date. The standards thereby codify Australian best practice but are also progressive in their recommendations.
Additional Relevant Australian Standards
The Australian Government Recordkeeping Metadata Standard Version 2.0 provides guidance on metadata elements and subelements for records management. It is a baseline tool that “describes information about records and the context in which they are captured and used in Australian Government agencies.” This standard is intended to help Australian agencies “meet business, accountability and archival requirements in a systematic and consistent way by maintaining reliable, meaningful and accessible records.” The standard is written in two parts, the first describing its purpose and features and the second outlining the specific metadata elements and subelements.44
The Australian Government Locator Service, AGLS, is published as AS 5044–2010, the metadata standard to help find and exchange information online. It updates the 2002 version, and includes changes made by the Dublin Core Metadata Initiative (DCMI).
Another standard, AS 5090:2003, “Work Process Analysis for Recordkeeping,” complements AS ISO 15489 and provides guidance on understanding business processes and workflow so that recordkeeping requirements may be determined.45
Long-Term Digital Preservation
Although many organizations shuffle dealing with digital preservation issues to the back burner, long-term digital preservation (LTDP) is a key area in which IG policy should be applied. LTDP methods, best practices, and standards should be applied to preserve an organization's historical and vital records (those without which it cannot operate or restart operations) and to maintain its corporate or organizational memory. The key standards that apply to LTDP are listed next.
The official standard format for preserving electronic documents is PDF/A-1, based on PDF 1.4 originally developed by Adobe. ISO 19005-1:2005, “Document Management—Electronic Document File Format for Long-Term Preservation—Part 1: Use of PDF 1.4 (PDF/A-1),” is the published specification for using PDF 1.4 for LTDP, which is applicable to e-documents that may contain not only text characters but also graphics (either raster or vector).46
ISO 14721:2012, “Space Data and Information Transfer Systems—Open Archival Information Systems—Reference Model (OAIS),” is applicable to LTDP.47 ISO 14271 “specifies a reference model for an open archival information system (OAIS). The purpose of ISO 14721 is to establish a system for archiving information, both digitalized and physical, with an organizational scheme composed of people who accept the responsibility to preserve information and make it available to a designated community.”48 The fragility of digital storage media combined with ongoing and sometimes rapid changes in computer software and hardware poses a fundamental challenge to ensuring access to trustworthy and reliable digital content over time. Eventually, every digital repository committed to long-term preservation of digital content must have a strategy to mitigate computer technology obsolescence. Toward this end, the Consultative Committee for Space Data Systems developed the OAIS reference model to support formal standards for the long-term preservation of space science data and information assets. OAIS was not designed as an implementation model.
The ISO 30300 series of e-records standards are written for a managerial audience and encourage ERM that is aligned to organizational objectives.
LTDP is a key area to which IG policy should be applied.
OAIS is the lingua franca of digital preservation, as the international digital preservation community has embraced it as the framework for viable and technologically sustainable digital preservation repositories. An LTDP strategy that is OAIS compliant offers the best means available today for preserving the digital heritage of all organizations, private and public. (See Chapter 17.)
ISO TR 18492 (2005), “Long-Term Preservation of Electronic Document Based Information,” provides practical methodological guidance for the long-term preservation and retrieval of authentic electronic document-based information, when the retention period exceeds the expected life of the technology (hardware and software) used to create and maintain the information assets. ISO 18492 takes note of the role of ISO 15489 but does not cover processes for the capture, classification, and disposition of authentic electronic document-based information.
ISO 16363:2012, “Space Data and Information Transfer Systems—Audit and Certification of Trustworthy Digital Repositories,” “defines a recommended practice for assessing the trustworthiness of digital repositories. It is applicable to the entire range of digital repositories.”49 It is an audit and certification standard organized into three broad categories: Organization Infrastructure, Digital Object Management, and Technical Infrastructure and Security Risk Management. ISO 16363 represents the gold standard of audit and certification for trustworthy digital repositories. (See Chapter 17.)
Business Continuity Management
ISO 22301:2012, “Societal Security—Business Continuity Management Systems—Requirements,” spells out the requirements for creating and implementing a standardized approach to business continuity management (BCM, also known as disaster recovery [DR]), in the event an organization is hit with a disaster or major business interruption.50 The guidelines can be applied to any organization regardless of vertical industry or size. The specification includes the “requirements to plan, establish, implement, operate, monitor, review, maintain and continually improve a documented management system to protect against, reduce the likelihood of occurrence, prepare for, respond to, and recover from disruptive incidents when they arise.”
An LTDP strategy that is OAIS compliant (based on ISO 14721) offers the best means available today for preserving the digital heritage of all organizations.
ISO 16363 represents the gold standard of audit and certification for trustworthy digital repositories.
ISO 22301 spells out requirements for creating and implementing a standardized approach to business continuity management.
The UK business continuity standard, BS25999-2, which heavily influenced the newer ISO standard, was withdrawn when ISO 22301 was released.51 The business rationale is that, with the increasing globalization of business, ISO 22301 will allow and support more consistency worldwide not only in business continuity planning and practices but also will promote common terms and help to embed various ISO management systems standards within organizations. U.S.-based ANSI, Standards Australia, Standards Singapore, and other standards bodies also contributed to the development of ISO 22301.
Benefits of ISO 22301
- Threat identification and assessment. Discover, name, and evaluate potential serious threats to the viability of the business.
- Threat and recovery planning. so the impact and resultant downtime and recovery from real threats that do become incidents is minimized
- Mission-critical process protection. Identifying key processes and taking steps to ensure they continue to operate even during a business interruption.
- Stakeholder confidence. Shows prudent management planning and business resilience to internal and external stakeholders, including employees, business units, customers, and suppliers.52
Making Your Best Practices and Standards Selections to Inform Your IG Framework
You must take into account your organization's corporate culture, management style, and organizational goals when determining which best practices and standards should receive priority in your IG framework. However, you must step through your business rationale in discussions with your cross-functional IG team and fully document the reasons for your approach. Then you must present this approach and your draft IG framework to your key stakeholders and be able to defend your determinations while allowing for input and adjustments. Perhaps you have overlooked some key factors that your larger stakeholder group uncovers, and their input should be folded into a final draft of your IG framework.
You must take into account your organization's corporate culture, management style, and organizational goals when determining which best practice and standards should be selected for your IG framework.
Next, you are ready to begin developing IG policies that apply to various aspects of information use and management, in specific terms. You must detail the policies you expect employees to follow when handling information on various information delivery platforms (e.g., e-mail, blogs, social media, mobile computing, cloud computing). It is helpful at this stage to collect and review all your current policies that apply and to gather some examples of published IG policies, particularly from peer organizations and competitors (where possible). Of note: You should not just adopt another organization's polices and believe that you are done with policy making. Rather, you must enter into a deliberative process, using your IG framework for guiding principles and considering the views and needs of your cross-functional IG team. Of paramount importance is to be sure to incorporate the alignment of your organizational goals and business objectives when crafting policy.
With each policy area, be sure that you have considered the input of your stakeholders, so that they will be more willing to buy into and comply with the new policies and so that the policies do not run counter to their business needs and required business processes. Otherwise, stakeholders will skirt, avoid, or halfheartedly follow the new IG policies, and the IG program risks failure.
Once you have finalized your policies, be sure to obtain necessary approvals from your executive sponsor and key senior managers.
Roles and Responsibilities
Policies will do nothing without people to advocate, support, and enforce them. So clear lines of authority and accountability must be drawn, and responsibilities must be assigned.
Overall IG program responsibility resides at the executive sponsor level, but beneath that, an IG program manager should drive team members toward milestones and business objectives and should shoulder the responsibility for day-to-day program activities, including implementing and monitoring key IG policy tasks. These tasks should be approved by executive stakeholders and assigned as appropriate to an employee's functional area of expertise. For instance, the IG team member from legal may be assigned the responsibility for researching and determining legal requirements for retention of business records, perhaps working in conjunction with the IG team member from RM, who can provide additional input based on interviews with representatives from business units and additional RM research into best practices.
Lines of authority, accountability, and responsibility must be clearly drawn for the IG program to succeed.
Program Communications and Training
Your IG program must contain a communications and training component, as a standard function. Your stakeholder audience must be made aware of the new policies and practices that are to be followed and how this new approach contributes toward the organization's goals and business objectives.
The first step in your communications plan is to identify and segment your stakeholder audiences and to customize or modify your message to the degree that is necessary to be effective. Communications to your IT team can have a more technical slant, and communications to your legal team can have some legal jargon and emphasize legal issues. The more forethought you put into crafting your communications strategy, the more effective it will be.
That is not to say that all messages must have several versions: Some core concepts and goals should be emphasized in communications to all employees.
How should you communicate? The more ways you can get your IG message to your core stakeholder audiences, the more effective and lasting the message will be. So posters, newsletters, e-mail, text messages, internal blog or intranet posts, and company meetings should all be a part of the communications mix. Remember, the IG program requires not only training but retraining, and the aim should be to create a compliance culture that is so prominent and expected that employees adopt the new practices and policies and integrate them into their daily activities. Ideally, employees will provide valuable input to help fine-tune and improve the IG program.
Training should take multiple avenues as well. Some can be classroom instruction, some online learning, and you may want to create a series of training videos. But the training effort must be consistent and ongoing to maintain high levels of IG effectiveness. Certainly, this means you will need to add to your new hire training program for employees joining or transferring to your organization.
Program Controls, Monitoring, Auditing, and Enforcement
How do you know how well you are doing? You will need to develop metrics to determine the level of employee compliance, its impact on key operational areas, and progress made toward established business objectives.
Testing and auditing the program provides an opportunity to give feedback to employees on how well they are doing and to recommend changes they may make. But having objective feedback on key metrics also will allow for your executive sponsor to see where progress has been made and where improvements need to focus.
Communications regarding your IG program should be consistent and clear and somewhat customized for various stakeholder groups.
Clear penalties for policy violations must be communicated to employees so they know the seriousness of the IG program and how important it is in helping the organization pursue its business goals and accomplish stated business objectives.
CHAPTER SUMMARY: KEY POINTS
- You must inform and frame IG policy with internal and external frameworks, models, best practices, and standards
- The business user is the primary stakeholder of managed information.
- Information management is important at all stages of the life cycle.
- Legal stakeholders usually can mandate the preservation of what is most critical, though often at great cost.
- The IGRM was developed by the EDRM Project to foster communication among stakeholders and adoption of IG. It complements ARMA's The Principles.
- ISO 31000 is a broad risk management standard that applies to all types of businesses.
- ISO/IEC 27001 and ISO/IEC 27002 are ISMS standards that provide guidance in the development of security controls.
- ISO 15489 is the international RM standard.
- The ICA-Req standard was adopted as ISO 16175. It does not contain a testing regime for certification.
- The ISO 30300 series of e-records standards are written for a managerial audience and encourage ERM that is aligned to organizational objectives.
- DoD 5015.2 is the U.S. ERM standard; the European ERM standard is MoReq2010. Australia has adopted all three parts of ISO 16175 as its e-records management standard.
- LTDP is a key area to which IG policy should be applied.
- An LTDP strategy that is OAIS compliant (based on ISO 14721) offers the best means available today for preserving the digital heritage of all organizations.
- ISO 16363 represents the gold standard of audit and certification for trustworthy digital repositories.
- ISO 38500 is an international standard that provides high-level principles and guidance for senior executives and directors responsible for IT governance.
- ISO 22301 spells out requirements for creating and implementing a standardized approach to business continuity management.
- You must take into account your organization's corporate culture, management style, and organizational goals when determining which best practices and standards should be selected for your IG framework.
- Lines of authority, accountability, and responsibility must be clearly drawn for the IG program to succeed.
- Communications regarding your IG program should be consistent and clear and somewhat customized for various stakeholder groups.
- IG program audits are an opportunity to improve training and compliance, not to punish employees.
Notes
1. ARMA International, “Generally Accepted Recordkeeping Principles,” www.arma.org/r2/generally-accepted-br-recordkeeping-principles/copyright (accessed November 25, 2013).
2. ARMA International, “Information Governance Maturity Model,” www.arma.org/r2/generally-accepted-br-recordkeeping-principles/metrics (accessed November 25, 2013).
3. Electronic Discovery, “IGRM v3.0 Update: Privacy & Security Officers As Stakeholders – Electronic Discovery,” http://electronicdiscovery.info/igrm-v3-0-update-privacy-security-officers-as-stakeholders-electronic-discovery/ (accessed April 24, 2013).
4. EDRM, “Information Governance Reference Model (IGRM),” www.edrm.net/projects/igrm (accessed October 9, 2013).
7. Project Management Institute, A Guide to the Project Management Body of Knowledge (PMBOK Guide), 4th ed. (Newtown Square, PA, Project Management Institute, 2008), ANSI/PMI 99-001-2008, pp. 273–312.
8. Kate Cumming, “Metadata Matters,” in Julie McLeod and Catherine Hare, eds., Managing Electronic Records, p. 34 (London: Facet, 2005).
9. Marc Fresko, e-mail to author, May 13, 2012.
10. Hofman, “The Use of Standards and Models,” in Julie McLeod and Catherine Hare, eds., Managing Electronic Records, p. 34 (London: Facet, 2005) pp. 20–21.
12. International Organization for Standardization, “ISO 31000:2009 Risk Management—Principles and Guidelines,” www.iso.org/iso/home/store/catalogue_tc/catalogue_detail.htm?csnumber=43170 (accessed April 22, 2013).
14. International Organization for Standardization, ISO/IEC 27001:2005, “Information Technology—Security Techniques—Information Security Management Systems—Requirements,” www.iso.org/iso/catalogue_detail?csnumber=42103 (accessed April 22, 2013).
15. International Organization for Standardization, ISO/IEC 27002:2005, “Information Technology—Security Techniques—Code of Practice for Information Security Management,” www.iso.org/iso/cata-logue_detail?csnumber=50297 (accessed July 23, 2012).
16. International Organization for Standardization, ISO/IEC 38500:2008, www.iso.org/iso/catalogue_detail?csnumber=51639 (accessed March 12, 2013).
17. ISO 38500 IT Governance Standard, www.38500.org/ (accessed March 12, 2013).
18. International Organization for Standardization, ISO 15489-1: 2001 Information and Documentation—Records Management. Part 1: General (Geneva: ISO, 2001), section 3.16.
19. National Archives of Australia, www.naa.gov.au/records-management/publications/DIRKS-manual.aspx (accessed October 15, 2012).
20. International Council on Archives, “ICA-Req: Principles and Functional Requirements for Records in Electronic Office Environments: Guidelines and Training Material,” November 29, 2011, www.ica.org/11696/activities-and-projects/icareq-principles-and-functional-requirements-for-records-in-electronic-office-environments-guidelines-and-training-material.html.
21. Council of Australasian Archives and Records Authorities, www.caara.org.au/ (accessed May 3, 2012).
22. Adrian Cunningham, blog post comment, May 11, 2011. http://thinkingrecords.co.uk/2011/05/06/how-moreq-2010-differs-from-previous-electronic-records-management-erm-system-specifications/.
24. “Relationship between the ISO 30300 Series of Standards and Other Products of ISO/TC 46/SC 11: Records Processes and Controls,” White Paper, ISO TC46/SC11-Archives/Records Management (March 2012), www.iso30300.es/wp-content/uploads/2012/03/ISOTC46SC11_White_paper_relationship_30300_technical_standards12032012v6.pdf
26. Julie Gable, Information Management Journal, November 1, 2002, www.thefreelibrary.com/Everything+you+wanted+to+know+about+DoD+5015.2:+the+standard+is+not+a...-a095630076.
27. These standards were developed by the CGSB (Canadian General Standards Board), which is a standards-writing agency within Public Works and Government Services Canada (a department of the federal government). It is accredited by the Standards Council of Canada as a standards development agency. The Council must certify that standards have been developed by the required procedures before it will designate them as being National Standards of Canada. 72.34 incorporates by reference as “normative references”: (1) many of the standards of the International Organization for Standardization (ISO) in Geneva, Switzerland. (“ISO,” derived from the Greek word isos (equal) so as to provide a common acronym for all languages); and (2) several of the standards of the Canadian Standards Association (CSA). The “Normative references” section of 72.34 (p. 2) states that these “referenced documents are indispensable for the application of this document.” 72.11 cites (p. 2, “Applicable Publications”) several standards of the American National Standards Institute/Association for Information and Image Management (ANSI/AIIM) as publications “applicable to this standard.” The process by which the National Standards of Canada are created and maintained is described within the standards themselves (reverse side of the front cover), and on the CGSB's Web site (see, “Standards Development”), from which Web site these standards may be obtained; http://www.ongc-cgsb.gc.ca.
28. The Canada Revenue Agency (CRA) informs the public of its policies and procedures by means, among others, of its Information Circulars (IC's), and GST/HST Memoranda. (GST: goods and services tax; HST: harmonized sales tax, i.e., the harmonization of federal and provincial sales taxes into one retail sales tax.) In particular, see: IC05-1, dated June 2010, entitled, Electronic Record Keeping, paragraphs 24, 26 and 28. Note that use of the National Standard cited in paragraph 26, Microfilm and Electronic Images as Documentary Evidence CAN/CGSB-72.11-93 is mandatory for, “Imaging and microfilm (including microfiche) reproductions of books of original entry and source documents …” Paragraph 24 recommends the use of the newer national standard, Electronic Records as Documentary Evidence CAN/CGSB-72.34-2005, “To ensure the reliability, integrity and authenticity of electronic records.” However, if this newer standard is given the same treatment by CRA as the older standard, it will be made mandatory as well. And similar statements appear in the GST Memoranda, Computerized Records 500-1-2, Books and Records 500-1. IC05-1. Electronic Record Keeping, concludes with the note, “Most Canada Revenue Agency publications are available on the CRA Web site www.cra.gc.ca under the heading ‘Forms and Publications.’”
29. There are more than 200 specific compliance tests that can be applied to determine if the principles of 72.34 are being complied with. The analysts—a combined team of records management and legal expertise—analyze: (1) the nature of the business involved; (2) the uses and value of its records for its various functions; (3) the likelihood and risk of the various types of its records being the subject of legal proceedings, or of their being challenged by some regulating authority; and (4) the consequences of the unavailability of acceptable records—for example, the consequences of its records not being accepted in legal proceedings. Similarly, in regard to the older National Standard of Canada, 72.11, there is a comparable series of more than 50 tests that can be applied to determine the state of compliance with its principles.
30. Electronic Records as Documentary Evidence CAN/CGSB-72.34-2005 (“72.34”), clause 5.4.3 c) at p. 17; and Microfilm and Electronic Images as Documentary Evidence CAN/CGSB-72.11-93 (“72.11”), paragraph 4.1.2 at p. 2, supra note 49.
31. 72.34, Clause 5.4.3, ibid.
32. “Admissibility” refers to the procedure by which a presiding judge determines if a record or other proffered evidence is acceptable as evidence according the rules of evidence. “Electronic discovery” is the compulsory exchange of relevant records by the parties to legal proceedings prior to trial.” As to the admissibility of records as evidence see: Ken Chasse, “The Admissibility of Electronic Business Records” (2010), 8 Canadian Journal of Law and Technology 105; and Ken Chasse, “Electronic Records for Evidence and Disclosure and Discovery” (2011) 57 The Criminal Law Quarterly 284. For the electronic discovery of records see: Ken Chasse, “Electronic Discovery—Sedona Canada is Inadequate on Records Management—Here's Sedona Canada in Amended Form,” Canadian Journal of Law and Technology 9 (2011): 13 5; and Ken Chasse, “Electronic Discovery in the Criminal Court System,” Canadian Criminal Law Review 14 (2010): 111. See also note 18 infra, and accompanying text.
33. For the province of Quebec, comparable provisions are contained in Articles 2831-2842, 2859-2862, 2869-2874 of Book 7 “Evidence” of the Civil Code of Quebec, S.Q. 1991, c. C-64, to be read in conjunction with, An Act to Establish a Legal Framework for Information Technology, R.S.Q. 2001, c. C-1.1, ss. 2, 5-8, and 68.
34. For the legislative jurisdiction of the federal and provincial governments in Canada, see The Constitution Act, 1867 (U.K.) 30 – 31 Victoria, c. 3, s. 91 (federal), and s. 92 (provincial), www.canlii.org/en/ca/laws/stat/30—31-vict-c-3/latest/30—31-vict-c-3.html.
35. The two provinces of Alberta and Newfoundland and Labrador do not have business record provisions in their Evidence Acts. Therefore “admissibility” would be determined in those jurisdictions by way of the court decisions that define the applicable common law rules; such decisions as, Ares v. Venner [1970] S.C.R. 608, 14 D.L.R. (3d) 4 (S.C.C.), and decisions that have applied it.
36. See for example, the Canada Evidence Act, R.S.C. 1985, c. C-5, ss. 31.1-31.8; Alberta Evidence Act, R.S.A 2000, c. A-18, ss. 41.1-41.8; (Ontario) Evidence Act, R.S.O. 1990, c. E.23, s. 34.1; and the (Nova Scotia) Evidence Act, R.S.N.S. 1989, c. 154, ss. 23A-23G. The Evidence Acts of the two provinces of British Columbia and Newfoundland and Labrador do not contain electronic record provisions. However, because an electronic record is no better than the quality of the record system in which it is recorded or stored, its “integrity” (reliability, credibility) will have to be determined under the other provincial laws that determine the admissibility of records as evidence.
37. The electronic record provisions have been in the Evidence Acts in Canada since 2000. They have been applied to admit electronic records into evidence, but they have not yet received any detailed analysis by the courts.
38. This is the wording used in, for example, s. 41.6 of the Alberta Evidence Act, s. 34.1(8) of the (Ontario) Evidence Act; and s. 23F of the (Nova Scotia) Evidence Act, supra note 10. Section 31.5 of the Canada Evidence Act, supra note 58, uses the same wording, the only significant difference being that the word “document” is used instead of “record.” For the province of Quebec, see sections 12 and 68 of, An Act to Establish a Legal Framework for Information Technology, R.S.Q., chapter C-1.1.
39. “Giving Value: Funding Priorities for UK Archives 2005–2010, a key new report launched by the National Council on Archives (NCA) in November 2005,” www.nationalarchives.gov.uk/documents/standards_guidance.pdf (accessed October 15, 2012).
40. DLM Forum Foundation, MoReq2010®: Modular Requirements for Records Systems—Volume 1: Core Services & Plug-in Modules, 2011, http://moreq2010.eu/ (accessed May 7, 2012, published in paper form as ISBN 978-92-79-18519-9 by the Publications Office of the European Communities, Luxembourg.
41. DLM Forum, Information Governance across Europe, www.dlmforum.eu/ (accessed December 14, 2010).
42. National Archives of Australia, “Australian and International Standards,” 2012, www.naa.gov.au/records-management/strategic-information/standards/ASISOstandards.aspx (accessed July 16, 2012).
43. E-mail to author from Marc Fresko, May 13, 2012.
44. National Archives of Australia, “Australian Government Recordkeeping Metadata Standard,” 2012, www.naa.gov.au/records-management/publications/agrk-metadata-standard.aspx (accessed July 16, 2012).
45. National Archives of Australia, “Australian and International Standards,” 2012, www.naa.gov.au/records-management/strategic-information/standards/ASISOstandards.aspx (accessed July 16, 2012).
46. International Organization for Standardization, ISO 19005-1:2005, “Document Management—Electronic Document File Format for Long-Term Preservation—Part 1: Use of PDF 1.4 (PDF/A-1),” www.iso.org/iso/catalogue_detail?csnumber=38920 (accessed July 23, 2012).
47. International Organization for Standardization, ISO 14721:2012, “Space Data and Information Transfer Systems Open Archival Information System—Reference Model,” www.iso.org/iso/iso_catalogue/catalogue_ics/catalogue_detail_ics.htm?csnumber=57284 (accessed November 25, 2013).
49. International Organization for Standardization, ISO 16363:2012, “Space Data and Information Transfer Systems—Audit and Certification of Trustworthy Digital Repositories,” www.iso.org/iso/iso_catalogue/catalogue_tc/catalogue_detail.htm?csnumber=56510 (accessed July 23, 2012).
50. International Organization for Standardization, ISO 22301:2012 “Societal Security—Business Continuity Management Systems—Requirements,” www.iso.org/iso/catalogue_detail?csnumber=50038 (accessed April 21, 2013).
51. International Organization for Standardization, “ISO Business Continuity Standard 22301 to Replace BS 25999-2,” www.continuityforum.org/content/news/165318/iso-business-continuity-standard-22301-replace-bs-25999-2 (accessed April 21, 2013).
52. BSI, “ISO 22301 Business Continuity Management,” www.bsigroup.com/en-GB/iso-22301-business-continuity (accessed April 21, 2013).
* This section is adapted with permission by EDRM.net, http://www.edrm.net/resources/guides/igrm (accessed January 24, 2014).
* This section is adapted with permission by EDRM.net, http://www.edrm.net/resources/guides/igrm (accessed January 24, 2014).
* This section was contributed by Ken Chasse J.D., LL.M., a records management attorney and consultant, and member of the Law Society of Upper Canada (Ontario) and of the Law Society of British Columbia, Canada.