One major issue when working with containers is their deprecation and maintenance costs. Too often, containers are built one day, shipped to production because they work, and forgotten there until the next rebuild (which may not happen anytime soon). Libraries are still libraries, and security fixes are pushed every day into distributions package repositories. Sysadmins are used to patch the systems; however, now it's a total anti-pattern to update a running container. Containers need to be rebuilt, exactly like developers are used to rebuilding applications with updated libraries to get rid of bugged code. The exception is that we are lucky enough to have tools that monitor each and every layer of our Docker images and tell us how and when they are vulnerable, allowing us to simply rebuild and redeploy them.
To step through this recipe, you will need:
- A working Docker installation
- A free account at Quay.io and/or a paid account at the Docker Hub
Using the free Quay.io account (by the CoreOS team), push an image to their Docker Registry service after logging in using docker login. Here's how to do this using an earlier image from this chapter:
$ docker tag sjourdan/nginx-docker-demo:1.0 quay.io/sjourdan/nginx-docker-demo:1.0 $ docker push quay.io/sjourdan/nginx-docker-demo:1.0 The push refers to a repository [quay.io/sjourdan/nginx-docker-demo] 82819c620e5d: Pushed d07a4f6d2067: Pushed
Note
Quay.io has a very nice security feature: as Docker stores passwords in plain text on the local workstation, it's possible to generate an encrypted password from the settings tab of your Quay.io account not only for Docker use, but also for Kubernetes, rkt, or Mesos. It's a much better option to use this encrypted password to log in to the service.
After a while, in the Repository Tags tab of our image, we'll get a SECURITY SCAN summary:

In this example, we have issues to investigate further:
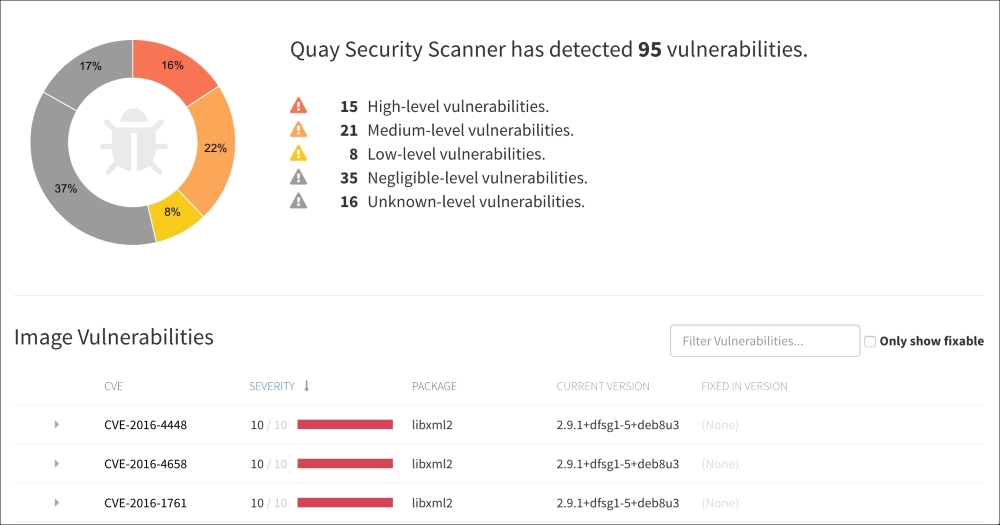
Many vulnerabilities are displayed, but don't be frightened. In fact, none are fixable in our case (click on Only show fixable to see what you can do). The reasons are multiple, such as no fix is available currently, the vulnerability doesn't concern the platform we're running on, and so on.
Here's a screenshot of a really vulnerable container and the Quay.io scanner giving helpful advice on the available fixes:

Quay.io Security Scanner will also send reminders by e-mail with a summary of the vulnerabilities found on all the containers it hosts on our account. So we don't have to worry too much about missing out on important security issues.
There's a similar feature on the Docker Hub that uses a paid account, though still in preview at the time of this writing. By default, Docker Security Scanning is not activated, so we have to navigate to the billing tab of the account's interface and tick it to enable it:

From now on, when a new Docker image is created or pushed, the system will scan it quickly and report issues, tag by tag. To access the report summary, just click on the Tag tab:

To see details (and the corresponding vulnerabilities), click on the tag number:

This layer has clear issues! But don't follow this blindly and double-check the said vulnerabilities. All the critical issues in this example only concern Apple platforms and we're running Linux containers.
Under the hood, the Quay Security Scanner is based on Clair. Clair is an open source static analysis vulnerability scanner by CoreOS that we can run ourselves or build tools upon. It currently handles Debian, Ubuntu, Alpine, Oracle, and Red Hat security data sources. It gives access to a simple API. Our custom tool can send each Docker image layer we're interested in and get the corresponding vulnerabilities or fixes.
- CoreOS Clair at https://github.com/coreos/clair/
