Chapter 1
Let’s Talk About Network Security
LO. These were the first two—and only—characters transferred between University of California, Los Angeles (UCLA) and Stanford Research Institute (SRI) when the very first ARPANET link was established between these two locations in 1969. It was an attempt to send the LOGIN command, but the system crashed. Who would have guessed that this was the birth of one of the most important tools of modern times: the Internet? Nevertheless, ARPANET continued to evolve and grow into an international network. By early 1990, especially with the invention of the World Wide Web (WWW) by Tim Berners-Lee, the Internet became an integral part of our lives. Initially ARPANET and then the Internet were designed to be government and government-body networks. The focus of early development was primarily inter-connectivity and reliability. Security was not top-of-mind for what was to be a closed network. Hence, most of the protocols the Internet is made up of do not have security built in.
As the Internet and networking in general grew in prominence, so did the opportunities for malicious actors to profit from them. Security was layered on to existing protocols by means of other protocols or security products. Adding security to these protocols would change them significantly. In addition, the cost and time needed to implement such new protocols were problematic. You don’t have to look further than IPv6 to understand how difficult it is to switch to newer protocols. Even though we have run out of assignable public IPv4 addresses, the shift to IPv6 is far from over. So, we are left with adding layers of security to our networks, and malicious actors are usually a few steps ahead of us.
With the advent of the Internet of Things (IoT), cloud computing, and bring-your-own-device (BYOD) initiatives, among other advances, our networks have changed drastically in recent times. IoT and BYOD have shifted the landscape from known and controlled devices connecting to networks to unknown and uncontrolled devices. With more applications moving to the cloud, a large percentage of traffic now bypasses the corporate intranet and goes through the Internet. As the landscape changes, the threats evolve. In 2016–2017, for example, we saw a big increase in IoT device availability and usage, but we also realized that most of these devices do not have any security built into them. It didn’t take long for someone to capitalize on that and create a botnet out of IoT devices. For example, the Mirai malware, which attacks IoT devices, was responsible for the biggest distributed denial-of-service (DDoS) attack yet known; the victim received close to 1 TB of traffic per second.
Cisco’s chairman, John Chambers, famously said, “There are only two types of companies: those that have been hacked, and those who don’t know they have been hacked.” The security problems and targets are not difficult to find either. Breaking into a network is seriously lucrative. In fact, it is so profitable that Cisco’s security research group, Talos, found that there is a 9-to-5 attack pattern in most cases. That is, malicious actors work the same hours as the good guys! To understand how high the stakes are for both sides, consider these two examples:
![]() The U.S. FBI estimates the losses attributable to the GameOver Zeus malware to be at least $100 million. More than 1 million devices were infected worldwide, and it took years and resources from 10 countries to eventually take it down.
The U.S. FBI estimates the losses attributable to the GameOver Zeus malware to be at least $100 million. More than 1 million devices were infected worldwide, and it took years and resources from 10 countries to eventually take it down.
![]() The CryptoLocker ransomware is estimated to have netted $27 million in ransom within two months of its release.
The CryptoLocker ransomware is estimated to have netted $27 million in ransom within two months of its release.
With critical systems such as banking, healthcare, and utilities becoming more connected, our security challenges have increased over the years. On the other hand, the malicious actors have evolved from early-day hackers whose intentions were mostly curiosity and bravado to modern-day hackers whose intentions range from financial gain to espionage and beyond. To effectively secure against these threats, it is important to understand not only what we are securing and how we are securing it but also who we are securing against.
Know Thy Enemy
To quote one of my favorite authors, Sun Tzu, “Know thy self, know thy enemy. A thousand battles, a thousand victories.” This advice applies well to network security. Understanding the threat to your network is a very big part of securing it. Hence, it is important to understand who you are securing your network against. Most malicious actors who will target your network fall into one of these categories:
![]() Black-hat hacker: The term hacker originally meant someone who exploited the weakness of systems in the spirit of exploration and curiosity. The media now uses it as a catch-all term to describe all malicious cyber actors. They are in fact referring to black-hat hackers, also known as crackers. These are people or groups that exploit the weaknesses of a system for profit. They commonly use known exploits, social engineering attacks such as phishing, and malware such as rootkits and Trojans to get inside a network.
Black-hat hacker: The term hacker originally meant someone who exploited the weakness of systems in the spirit of exploration and curiosity. The media now uses it as a catch-all term to describe all malicious cyber actors. They are in fact referring to black-hat hackers, also known as crackers. These are people or groups that exploit the weaknesses of a system for profit. They commonly use known exploits, social engineering attacks such as phishing, and malware such as rootkits and Trojans to get inside a network.
![]() Script kiddies: This is a derogatory term used to describe black-hat hackers who use easily available scripts and programs in their attacks. Simple denial-of-service (DoS) attacks, web server hacking using XSS, and SQL injections are favorites of script kiddies.
Script kiddies: This is a derogatory term used to describe black-hat hackers who use easily available scripts and programs in their attacks. Simple denial-of-service (DoS) attacks, web server hacking using XSS, and SQL injections are favorites of script kiddies.
![]() Organized criminal outfits: Criminal organizations have recently realized the revenue potential of cyber attacks. These actors are very well organized, with a strong arsenal of attacks as well as physical presence for money laundering around the world. The most infamous example is the Business Club, which was responsible for the GameOver Zeus malware.
Organized criminal outfits: Criminal organizations have recently realized the revenue potential of cyber attacks. These actors are very well organized, with a strong arsenal of attacks as well as physical presence for money laundering around the world. The most infamous example is the Business Club, which was responsible for the GameOver Zeus malware.
![]() Nation-state actors: Possibly the most sophisticated group on this list, nation-state actors are sponsored by governments. Their activities include espionage, attacks on infrastructure, and surveillance. These activities are done in the interest of the nation-state sponsoring them. Their arsenal includes undisclosed zero-days, highly sophisticated malware, and state-of-the-art social engineering tools. Stuxnet, an early example of malware targeting a physical infrastructure, is alleged to be the product of nation-state actors.
Nation-state actors: Possibly the most sophisticated group on this list, nation-state actors are sponsored by governments. Their activities include espionage, attacks on infrastructure, and surveillance. These activities are done in the interest of the nation-state sponsoring them. Their arsenal includes undisclosed zero-days, highly sophisticated malware, and state-of-the-art social engineering tools. Stuxnet, an early example of malware targeting a physical infrastructure, is alleged to be the product of nation-state actors.
![]() Hacktivists: Internet activists, or hacktivists, are groups of hackers who engage in activities to promote a political agenda. Their activities are designed to gather media attention, and they are quick to claim credit for their attacks. Defacing websites, executing DDoS attacks, and leaking documents or database contents are the most common activities for this group. Anonymous and LulzSec have been two of the most notable hacktivist groups in recent times.
Hacktivists: Internet activists, or hacktivists, are groups of hackers who engage in activities to promote a political agenda. Their activities are designed to gather media attention, and they are quick to claim credit for their attacks. Defacing websites, executing DDoS attacks, and leaking documents or database contents are the most common activities for this group. Anonymous and LulzSec have been two of the most notable hacktivist groups in recent times.
![]() Cyber terrorists: The primary focus of these actors is to create fear through their activities. They are usually motivated by religious or political beliefs and are associated with known terrorist outfits. They attack infrastructure, steal data such as identities of government employees, and deface websites with propaganda. Their skill levels can range from script kiddies to highly skilled black-hat hackers, but they are rarely as sophisticated as nation-state actors.
Cyber terrorists: The primary focus of these actors is to create fear through their activities. They are usually motivated by religious or political beliefs and are associated with known terrorist outfits. They attack infrastructure, steal data such as identities of government employees, and deface websites with propaganda. Their skill levels can range from script kiddies to highly skilled black-hat hackers, but they are rarely as sophisticated as nation-state actors.
![]() Insider threats: Insider threats are attackers who are part of your organization. Common sources of insider threats are disgruntled employees looking to exact revenge for perceived wrongdoing. These actors may not be as skilled at attacking a network as the other groups discussed here, but because they exploit the trust and access they already have, their actions are far more damaging. For example, a network admin can easily re-configure routers and switches on his or her last day at work to bring down the whole network. Similarly, a database admin can wipe whole databases and their backups and cause massive losses for an organization. These threats are often more possible and damaging than any that originate from outside the organization.
Insider threats: Insider threats are attackers who are part of your organization. Common sources of insider threats are disgruntled employees looking to exact revenge for perceived wrongdoing. These actors may not be as skilled at attacking a network as the other groups discussed here, but because they exploit the trust and access they already have, their actions are far more damaging. For example, a network admin can easily re-configure routers and switches on his or her last day at work to bring down the whole network. Similarly, a database admin can wipe whole databases and their backups and cause massive losses for an organization. These threats are often more possible and damaging than any that originate from outside the organization.
This list of potential threats is not exhaustive, but it provides you with a good understanding of what you face. It is important to recognize that these actors and their methods evolve continuously and at a fast pace—and so should your skills and your defenses against them. Defense is what the entirety of this series focuses on, but again, it is important to understand what you are protecting. Without the combined knowledge of the adversary and the self, you will not be able to choose the best defense.
Know Thy Self
What defines a threat? Is a robber a threat to an empty bank? A robber is not a threat in this case because there is nothing to steal. It is the presence of something valuable that makes a threat credible. The value and nature of a valuable define the risk posed by a threat, the nature of the threat, and the cost of defense. Similarly, you cannot define a threat to your network until you define the assets that you have to protect, the risks to those assets, and the costs of protecting or not protecting them. This analysis of an organization’s assets and risks is done when creating a security policy. Before we look at security policies, we need to define the key components of network security:
![]() Threat: A threat is a person or tool that can cause harm to an asset. The threat actors discussed in the preceding section or any tools such as viruses, worms, and other malware they use are collectively called a threat.
Threat: A threat is a person or tool that can cause harm to an asset. The threat actors discussed in the preceding section or any tools such as viruses, worms, and other malware they use are collectively called a threat.
![]() Vulnerability: A weakness or flaw in an asset or environment that a threat can exploit is called a vulnerability. For example, failing to password-protect your computer creates a vulnerability that may allow a threat to access documents stored on it.
Vulnerability: A weakness or flaw in an asset or environment that a threat can exploit is called a vulnerability. For example, failing to password-protect your computer creates a vulnerability that may allow a threat to access documents stored on it.
![]() Risk: The potential loss or damage that can result from a threat due to a vulnerability is called the risk. For example, if a threat shuts down your website, then the risk is the loss of revenue during and after the event.
Risk: The potential loss or damage that can result from a threat due to a vulnerability is called the risk. For example, if a threat shuts down your website, then the risk is the loss of revenue during and after the event.
![]() Mitigation: The measures taken to reduce a risk to an asset is called mitigation. All mitigation actions reduce risk and change the threat. For example, using a password to protect access to your computer mitigates the risk of unauthorized access by a threat.
Mitigation: The measures taken to reduce a risk to an asset is called mitigation. All mitigation actions reduce risk and change the threat. For example, using a password to protect access to your computer mitigates the risk of unauthorized access by a threat.
The key take-away here is that a risk can never be eliminated. Mitigation will always change the vulnerability, risk, and threat to an asset. For example, a computer protected by password is vulnerable to brute-force password cracking. This can be mitigated by a stronger password, but the computer will be vulnerable to unauthorized access through the security flaws in the operating system—and so on. Generally, a risk is mitigated only to the point where the cost of mitigation does not outweigh the risk itself. At that point, a risk is accepted instead of being mitigated.
Security Policy
As organizations get more reliant on technology and connectivity, their vulnerabilities and risks increase. In addition, changes in technology bring changes in risks, too. It is difficult for an organization to keep track of its assets and risks. Organizations also have to comply with various industry regulations and legislations, failing which they can be subject to severe penalties. This is where a security policy can help. A security policy is a high-level document that defines the organizational security requirements, principles, and practices created by executive-level management. The policy practically defines what security means for the organization. It contains sets of rules governing the security of assets, information, and people. It is important to remember that a security policy is very high level and does not contain implementation specifics. For example, a security policy may state that encryption is required for certain information but not that it requires 3DES for encryption. This level of detail allows flexibility in adopting new technology without requiring frequent changes to the security policy. The implementation details of a security policy are left to lower-level documents, such as procedures and guidelines.
Note While a security policy is much wider in scope, the discussion in this chapter is limited to network security.
While creating a security policy is an involved and time-consuming process, it can generally be broken down into five steps:
Step 1. Identify all assets that need to be protected.
Step 2. Identify risks and threats associated with each asset.
Step 3. Identify a risk mitigation strategy for each asset.
Step 4. Document and communicate findings to all stakeholders.
Step 5. Monitor and review continuously.
Depending on the size of the organization, the security policy can be one large document that covers all aspects, or it may be several individually focused policies. Because you are preparing for a Cisco exam, it is important to understand various areas of network security that should be part of a security policy, as defined by Cisco. With the definition of each policy, this chapter maps out Cisco products that help in implementing that policy to lay the groundwork for the later chapters. Remember that not every organization will have a need for all of these policies, and a security policy will not recommend a specific product because it is a high-level document. According to Cisco, the following areas of network security should be part of a security policy:
![]() Network access control (NAC): A NAC policy defines how to control access to your network such that only the right person or device can get the right access at the right time. It also defines compliance requirements that devices should meet before access is granted. Identity Services Engine (ISE) is a Cisco product that can be used to implement this policy.
Network access control (NAC): A NAC policy defines how to control access to your network such that only the right person or device can get the right access at the right time. It also defines compliance requirements that devices should meet before access is granted. Identity Services Engine (ISE) is a Cisco product that can be used to implement this policy.
![]() Antimalware: Malware is the primary threat vector in any network, so a policy to prevent, detect, and remediate malware is one of the most important security policies that an organization should have. Cisco’s Advanced Malware Protection (AMP) suite of products can be used to implement this policy.
Antimalware: Malware is the primary threat vector in any network, so a policy to prevent, detect, and remediate malware is one of the most important security policies that an organization should have. Cisco’s Advanced Malware Protection (AMP) suite of products can be used to implement this policy.
![]() Application security: Organizations require multiple applications to run their business. These applications may contain vulnerabilities that can be exploited. An application security policy defines the security requirements of these applications.
Application security: Organizations require multiple applications to run their business. These applications may contain vulnerabilities that can be exploited. An application security policy defines the security requirements of these applications.
![]() Behavioral analytics: This policy defines baselining and analytic requirements. Every network has baseline traffic patterns and user behavior. Malicious behavior can be identified by investigating deviations from the established baseline for any organization or network segment. The Stealthwatch product family from Cisco helps implement this policy.
Behavioral analytics: This policy defines baselining and analytic requirements. Every network has baseline traffic patterns and user behavior. Malicious behavior can be identified by investigating deviations from the established baseline for any organization or network segment. The Stealthwatch product family from Cisco helps implement this policy.
![]() Data loss prevention: Some information in any organization is meant for internal use only. Such data being sent outside the organization can cause irreparable harm. A data loss prevention policy defines the requirements around preventing loss of such data. Various Cisco security products, such as Web Security Appliance (WSA), Email Security Appliance (ESA), Firepower Next-Generation Firewall (NGFW), and Cloudlock can be used to implement this policy.
Data loss prevention: Some information in any organization is meant for internal use only. Such data being sent outside the organization can cause irreparable harm. A data loss prevention policy defines the requirements around preventing loss of such data. Various Cisco security products, such as Web Security Appliance (WSA), Email Security Appliance (ESA), Firepower Next-Generation Firewall (NGFW), and Cloudlock can be used to implement this policy.
![]() Email security: Email is the primary method of communication in and out of organizations. Email is also a primary threat vector for security breaches because it can facilitate phishing attacks as well as delivery of malware to the network. An email security policy defines acceptable use and security of email systems. Cisco ESA and Cloud Email Security combined with AMP can help implement this security policy.
Email security: Email is the primary method of communication in and out of organizations. Email is also a primary threat vector for security breaches because it can facilitate phishing attacks as well as delivery of malware to the network. An email security policy defines acceptable use and security of email systems. Cisco ESA and Cloud Email Security combined with AMP can help implement this security policy.
![]() Perimeter security: To meet operational requirements, the trusted internal network of an organization has to interface with untrusted networks such as the Internet or networks belonging to partners and vendors. A perimeter security policy defines how the perimeter of the trusted network is protected and how access is granted across to it. The Cisco Adaptive Security Appliance (ASA) and Firepower NFGW product families can be used to implement this policy.
Perimeter security: To meet operational requirements, the trusted internal network of an organization has to interface with untrusted networks such as the Internet or networks belonging to partners and vendors. A perimeter security policy defines how the perimeter of the trusted network is protected and how access is granted across to it. The Cisco Adaptive Security Appliance (ASA) and Firepower NFGW product families can be used to implement this policy.
![]() Intrusion prevention: Intrusion refers to an active attempt to exploit a vulnerability or violate a policy in a network. An intrusion prevention policy defines the intrusion detection, prevention, and reporting requirements of the organization. Cisco Firepower Next-Generation IPS (NGIPS) and Firepower Next-Generation Firewall (NGFW) product families can help implement an intrusion prevention policy.
Intrusion prevention: Intrusion refers to an active attempt to exploit a vulnerability or violate a policy in a network. An intrusion prevention policy defines the intrusion detection, prevention, and reporting requirements of the organization. Cisco Firepower Next-Generation IPS (NGIPS) and Firepower Next-Generation Firewall (NGFW) product families can help implement an intrusion prevention policy.
![]() Mobile device security: Mobile devices, with their increasing presence and corporate applications support, introduce credible threats in a network. A mobile device security policy defines the security posture and access control requirements for corporate and employee-owned mobile devices in the network. Cisco ISE and Meraki mobile device management product lines can help implement this policy.
Mobile device security: Mobile devices, with their increasing presence and corporate applications support, introduce credible threats in a network. A mobile device security policy defines the security posture and access control requirements for corporate and employee-owned mobile devices in the network. Cisco ISE and Meraki mobile device management product lines can help implement this policy.
![]() Network segmentation: Various segments on a network can require different security and access policies, generally based on the sensitivity of the systems and data residing in each segment. A network segmentation policy defines the requirements around segmenting different parts of the network. Cisco ISE, ASA, and Firepower NGFW, along with TrustSec, can be used to implement a network segmentation policy.
Network segmentation: Various segments on a network can require different security and access policies, generally based on the sensitivity of the systems and data residing in each segment. A network segmentation policy defines the requirements around segmenting different parts of the network. Cisco ISE, ASA, and Firepower NGFW, along with TrustSec, can be used to implement a network segmentation policy.
![]() Security information and event management (SIEM): Logs, events, and alarms from various security solutions in a network provide useful information. Analyzing them can help validate existing prevention solutions as well provide feedback for improvement. Events reported by security solutions should be investigated to ensure that threats have been eliminated and to assess any loss. A SIEM policy defines the requirement around collection, storage, correlation, and analysis of security information as well as security event management. Cisco security products integrate with various SIEM products to help implement this policy.
Security information and event management (SIEM): Logs, events, and alarms from various security solutions in a network provide useful information. Analyzing them can help validate existing prevention solutions as well provide feedback for improvement. Events reported by security solutions should be investigated to ensure that threats have been eliminated and to assess any loss. A SIEM policy defines the requirement around collection, storage, correlation, and analysis of security information as well as security event management. Cisco security products integrate with various SIEM products to help implement this policy.
![]() Remote access: Employees, vendors, or partners often require access to applications from outside the corporate network. Branch or remote locations also need access to the corporate network or data center in order to conduct business. Using a virtual private network (VPN) is one way to provide such access. This policy defines the requirements around providing secure remote access to employees, vendors, partners, and remote locations. Cisco routers, Firepower NGFW, and ASA, along with the AnyConnect VPN client, can be used to implement this policy.
Remote access: Employees, vendors, or partners often require access to applications from outside the corporate network. Branch or remote locations also need access to the corporate network or data center in order to conduct business. Using a virtual private network (VPN) is one way to provide such access. This policy defines the requirements around providing secure remote access to employees, vendors, partners, and remote locations. Cisco routers, Firepower NGFW, and ASA, along with the AnyConnect VPN client, can be used to implement this policy.
![]() Web security: Web traffic accounts for the majority of traffic in the network and is also the second biggest threat vector. A web security policy defines the requirements around acceptable web use, security of web traffic, and prevention against web-based threats. Cisco WSA, Cisco Secure Internet Gateway (SIG) (formerly known as Cloud Web Security [CWS]), and Cisco Umbrella (formerly known as OpenDNS) can be used to implement a web security policy.
Web security: Web traffic accounts for the majority of traffic in the network and is also the second biggest threat vector. A web security policy defines the requirements around acceptable web use, security of web traffic, and prevention against web-based threats. Cisco WSA, Cisco Secure Internet Gateway (SIG) (formerly known as Cloud Web Security [CWS]), and Cisco Umbrella (formerly known as OpenDNS) can be used to implement a web security policy.
![]() Wireless security: Switch ports providing access to a wired network are often protected by the physical security policies and measures employed by an organization. Because unauthorized persons will be prevented from entering a building, they will not be able to connect to the switch ports inside. Wireless network access, on the other hand, can cross physical security boundaries and hence presents a high risk. A wireless security policy defines the requirements around security and access control of the wireless network, including requirements related to wireless network access by employee-owned devices and guests. Cisco ISE can be used to implement a wireless security policy.
Wireless security: Switch ports providing access to a wired network are often protected by the physical security policies and measures employed by an organization. Because unauthorized persons will be prevented from entering a building, they will not be able to connect to the switch ports inside. Wireless network access, on the other hand, can cross physical security boundaries and hence presents a high risk. A wireless security policy defines the requirements around security and access control of the wireless network, including requirements related to wireless network access by employee-owned devices and guests. Cisco ISE can be used to implement a wireless security policy.
As you can see, defining assets, risks, and various requirements around security can be a challenging task. Even when broken down into simple steps and smaller pieces, creating a security policy is difficult. It is easier to know thy enemy than to know thy self! This is where security standards and frameworks come to the rescue.
Security Standards and Frameworks
Various government and private entities have realized that while it is increasingly important to have a security policy, creating an effective and comprehensive one is hard. Hence, they have published many standards and frameworks to help with creating and implementing security policies. You can use one or more of these frameworks as the basis of your own policy and customize as required. While there are many organizations around the world that publish and maintain such standards and frameworks, these are the two most important ones:
![]() International Organization for Standardization (ISO): ISO is an independent nongovernmental organization composed of representatives from 162 national standards organizations. ISO publishes standards that help establish quality requirements across products and services, ranging from manufacturing and technology to agriculture and healthcare. By following these standards and getting certified, organizations prove to their customers that their products, procedures, or services meet internationally accepted standards. Certification is optional. The standards can be used to simply improve quality within an organization without going through the certification process.
International Organization for Standardization (ISO): ISO is an independent nongovernmental organization composed of representatives from 162 national standards organizations. ISO publishes standards that help establish quality requirements across products and services, ranging from manufacturing and technology to agriculture and healthcare. By following these standards and getting certified, organizations prove to their customers that their products, procedures, or services meet internationally accepted standards. Certification is optional. The standards can be used to simply improve quality within an organization without going through the certification process.
![]() National Institute of Standards and Technology (NIST): NIST is a measurement standards laboratory. Even though it is part of the U.S. Department of Commerce, it is a non-regulatory organization. It provides measurements and standards for technology, including cybersecurity. Much as with ISO, standards from NIST can be used to certify products and services, or they can be used simply to improve quality.
National Institute of Standards and Technology (NIST): NIST is a measurement standards laboratory. Even though it is part of the U.S. Department of Commerce, it is a non-regulatory organization. It provides measurements and standards for technology, including cybersecurity. Much as with ISO, standards from NIST can be used to certify products and services, or they can be used simply to improve quality.
These two organizations and various others have published many security standards and frameworks. While any of them can be used to create a security policy, the two most common ones in use today—and the ones most relevant to the exam—are ISO/IEC 27001/27002 and NIST Cyber Security Framework (CSF).
ISO/IEC 27001 and 27002
ISO and the International Electrotechnical Commission (IEC) jointly publish the ISO/IEC 27000 series standards, which are collectively known as the “Information Security Management Systems (ISMS) Family of Standards.” This series contains 45 individual standards related to information security. Out of these 45, 27001 and 27002 are most relevant for our discussion:
![]() ISO/IEC 27001, “Information Security Management Systems—Requirements”: This standard provides the specifications for an information security management system and can be used as the framework for an organization’s security policy. If an organization implements the standard and is compliant with all requirements, it can apply to be audited and certified. Certification is not mandatory, and the standard can also be used only as a reference framework for a security policy.
ISO/IEC 27001, “Information Security Management Systems—Requirements”: This standard provides the specifications for an information security management system and can be used as the framework for an organization’s security policy. If an organization implements the standard and is compliant with all requirements, it can apply to be audited and certified. Certification is not mandatory, and the standard can also be used only as a reference framework for a security policy.
![]() ISO/IEC 27002, “Code of Practice for Information Security Controls”: This standard outlines the best practices for implementation of a very comprehensive list of controls in information security. It is used to implement the controls identified in a security policy. The standard is based on the principles of confidentiality, integrity, and availability (CIA), which are considered cornerstones of security:
ISO/IEC 27002, “Code of Practice for Information Security Controls”: This standard outlines the best practices for implementation of a very comprehensive list of controls in information security. It is used to implement the controls identified in a security policy. The standard is based on the principles of confidentiality, integrity, and availability (CIA), which are considered cornerstones of security:
![]() Confidentiality defines the capability to ensure that information in all its states is accessible only by authorized users. This is the most important and obvious aspect of a security system and also what most attackers aim to breach. Unauthorized access to information is the single biggest intent behind most attacks. Use of encryption and authentication are two primary ways to ensure confidentiality. For example, if data is not encrypted in transit, it can be captured on the wire using man-in-the-middle (MITM) attacks, resulting in loss of confidentiality.
Confidentiality defines the capability to ensure that information in all its states is accessible only by authorized users. This is the most important and obvious aspect of a security system and also what most attackers aim to breach. Unauthorized access to information is the single biggest intent behind most attacks. Use of encryption and authentication are two primary ways to ensure confidentiality. For example, if data is not encrypted in transit, it can be captured on the wire using man-in-the-middle (MITM) attacks, resulting in loss of confidentiality.
![]() Integrity defines the need to prevent unauthorized modification of information and systems in any state. Breached integrity is as bad as breached confidentiality. Encryption and authentication are also used to ensure integrity. Continuing the previous example, during a successful MITM attack, the attacker can not only breach confidentiality but also choose to modify information in transit—which results in loss of integrity as well.
Integrity defines the need to prevent unauthorized modification of information and systems in any state. Breached integrity is as bad as breached confidentiality. Encryption and authentication are also used to ensure integrity. Continuing the previous example, during a successful MITM attack, the attacker can not only breach confidentiality but also choose to modify information in transit—which results in loss of integrity as well.
![]() Availability defines the need to prevent loss of access to information or to a system. Information should always be readily available to authorized users. DoS or the larger-scale DDoS attacks are common methods that attackers use to disrupt availability.
Availability defines the need to prevent loss of access to information or to a system. Information should always be readily available to authorized users. DoS or the larger-scale DDoS attacks are common methods that attackers use to disrupt availability.
The latest revision of the ISO/IEC 27002 standard, published in 2013, is divided into 19 sections. The first 5 are introductory:
0. Introduction
1. Scope
2. Normative references
3. Terms and definitions
4. Structure of This Standard
The remaining 14 sections describe different security control types and their objectives:
5. Information Security Policies
6. Organization of Information Security
7. Human Resource Security
8. Asset Management
9. Access Control
10. Cryptography
11. Physical and Environmental Security
12. Operations Security
13. Communications Security
14. System Acquisition, Development and Maintenance
15. Supplier Relationships
16. Information Security Incident Management
17. Information Security Aspects of Business Continuity Management
18. Compliance
Going into detail about the sections of ISO/IEC 27002:2013 is beyond the scope of this book, as well as the CCIE exam, but it is important to map out what Cisco products and technologies can be used to implement controls described in some of the relevant sections. Table 1-1 lists relevant sections and Cisco products that can be used to implement controls specified in those sections. It is important to remember that the standard deals with a complete information security system and its management, so network security is only a part of it.
Table 1-1 ISO/IEC 27002:2013 and Cisco Security Products
Section |
Cisco Product |
Details |
8. Asset Management |
ISE |
Section 8.1.1 lists the controls for identification of assets. The profiling feature of ISE can be used to profile assets on the network. |
9. Access Control |
ISE |
Section 9.1.2 lists controls for access to networks and network services. ISE helps authenticate and authorize users requesting access to the network or network devices. |
10. Cryptography |
ASA, NGFW, routers |
Section 10 lists the controls for cryptography. Various Cisco products, such as ASA, NGFW, and routers, provide encryption using different types of VPN. |
12. Operations Security |
AMP, ISE, Umbrella, NGFW, ESA, WSA |
Section 12.2 lists the controls for protection against malware. For example, AMP provides protection against malware, and it can be integrated with NGFW, WSA, and ESA, or can be used as a standalone device in the network and on endpoints. Umbrella also prevents malware execution by preventing communication with the command and control infrastructure. Section 12.6 calls for vulnerability management. Posture validation with Cisco ISE can be used to ensure that operating systems and antimalware are updated with the latest patches and definitions. |
13. Communications Security |
ISE, NGFW, ASA |
Section 13.1 lists controls for network security management and segregation or segmentation in particular. ISE can be used to provide segmentation with TrustSec. Segmentation can also be achieved by using NGFW and ASA with or without TrustSec. |
16. Information Security Incident Management |
Stealthwatch, NGFW, NGIPS |
Section 16.1 lists controls for incident management. Stealthwatch, NGFW, and NGIPS generate, collect, and store event logs and analytical information that can be used to investigate incidents. |
NIST Cybersecurity Framework
NIST created the Cybersecurity Framework (CSF) based on the executive order of the president titled “Improving Critical Infrastructure Cybersecurity.” It is a voluntary framework developed in collaboration with private industries to provide guidance on cybersecurity risk. It helps organizations in assessing their current security profile and in determining the desired target profile.
It is important to understand that the CSF does not provide a list of specific security controls that an organization should implement. It only provides a common set of activities that an organization can use to identify and mitigate its risk. It draws on and references other standards, such as ISO 27002, for recommending controls.
The framework is divided into three parts:
![]() Core: The framework core is a set of cybersecurity activities, desired outcomes, and references applicable across the critical assets of an organization. It is organized into 5 functions: identify, protect, detect, respond, and recover. These functions are further divided into 22 categories, as shown in Table 1-2. These are further divided into 98 subcategories and references.
Core: The framework core is a set of cybersecurity activities, desired outcomes, and references applicable across the critical assets of an organization. It is organized into 5 functions: identify, protect, detect, respond, and recover. These functions are further divided into 22 categories, as shown in Table 1-2. These are further divided into 98 subcategories and references.
Table 1-2 NIST CSF Core Functions and Categories
Function Identifier |
Function |
Category Identifier |
Category |
ID |
Identify |
ID.AM ID.BE ID.GV ID.RA ID.RM |
Asset Management Business Environment Governance Risk Assessment Risk Management Strategy |
PR |
Protect |
PR.AC PR.AT PR.DS PR.IP PR.MA PR.PT |
Access Control Awareness and Training Data Security Information Protection Maintenance Protective Technology |
DE |
Detect |
DE.AE DE.CM DE.DP |
Anomalies and Events Continuous Monitoring Detection Processes |
RS |
Respond |
RS.RP RS.CO RS.AN RS.MI RS.IM |
Response Planning Communications Analysis Mitigation Improvements |
RC |
Recover |
RC.RP RC.IM RC.CO |
Recovery Planning Improvements Communications |
![]() Implementation Tiers: The framework implementation tiers describe the degree to which an organization has implemented controls for each category of the framework core. The tiers are divided into four increasing levels: partial, risk-informed, repeatable, and adaptive. An organization has to decide the current and desired levels of implementation for each category based on risk tolerance. Increasing tier levels do not necessarily indicate maturity; the goal of the framework is not to ensure that an organization is at Tier 4 for each category.
Implementation Tiers: The framework implementation tiers describe the degree to which an organization has implemented controls for each category of the framework core. The tiers are divided into four increasing levels: partial, risk-informed, repeatable, and adaptive. An organization has to decide the current and desired levels of implementation for each category based on risk tolerance. Increasing tier levels do not necessarily indicate maturity; the goal of the framework is not to ensure that an organization is at Tier 4 for each category.
![]() Profile: The framework comes together in the framework profiles. An organization selects the categories and subcategories that align with its business needs. Then it identifies the controls that are already in place to create the current profile. Next, it creates a desired state, or target profile. The current profile can then be used to support prioritization and measurement of progress toward the target profile, while factoring in other business needs, including cost-effectiveness and innovation. Profiles can be used to conduct self-assessments and communicate within an organization or between organizations.
Profile: The framework comes together in the framework profiles. An organization selects the categories and subcategories that align with its business needs. Then it identifies the controls that are already in place to create the current profile. Next, it creates a desired state, or target profile. The current profile can then be used to support prioritization and measurement of progress toward the target profile, while factoring in other business needs, including cost-effectiveness and innovation. Profiles can be used to conduct self-assessments and communicate within an organization or between organizations.
Going into further details about CSF is beyond the scope of this book and the exam, but it is important to map out Cisco products and technologies that can be used in each relevant category for the framework, as shown in Table 1-3.
Table 1-3 Cisco Security Products and NIST CSF
CSF Function |
CSF Category |
Cisco Products |
Identify |
Asset Management Risk Assessment |
ISE, NGFW, Stealthwatch Cognitive Threat Analytics, NGFW |
Protect |
Access Control Data Security Maintenance Protective Tech. |
ISE, NGFW, Umbrella All Cisco Security Products ISE with AnyConnect ISE, NGFW |
Detect |
Anomalies & Events Continuous Monitoring |
AMP, Stealthwatch, WSA/ESA, Umbrella, NGFW AMP, Stealthwatch, ESA, CTA, NGFW |
Respond |
Analysis Mitigation |
AMP, Stealthwatch, WSA, ESA, NGFW All Cisco Security Products |
Regulatory Compliance
While frameworks can be used to create a security policy, an organization must also take into consideration the regulatory compliance and laws that apply to the industries and locations in which it operates. Such laws are made to protect the industry and its consumers and offer specific guidelines to ensure security of information.
Various regulatory compliance and legislative acts apply to industries around the world. An organization needs to consider them while creating its security policies. There is usually a very heavy penalty associated with failure to comply with these laws. In this section, we briefly discuss two of the most important such regulations and legislative acts.
Health Insurance Portability and Accountability Act (HIPAA)
The Health Insurance Portability and Accountability Act (HIPAA) was enacted by the U.S. Congress in August 1996. It applies to the organizations in the healthcare industry. In particular, it states that any entity that creates, receives, transmits, or maintains protected health information in electronic form must make good-faith efforts to protect the data and the computing environment from known and reasonably anticipated threats and vulnerabilities. Such entities are also required to protect the confidentiality, integrity, and availability of such electronic data.
HIPAA is technology neutral and does not define controls to allow flexibility in adopting new technology. It provides standards and in some cases implementation specifications to comply, but most often, industry standards such as ISO 27002 and NIST CSF are used to meet the requirements of the act.
Note Cisco has published a compliance guide for HIPAA security rule design and implementation. Much of the information in this section is compiled from that guide. I strongly suggest reading the guide in preparation for the CCIE exam. It can be found at http://www.cisco.com/c/en/us/td/docs/solutions/Enterprise/Compliance/HIPAA/default.html.
Penalties associated with violation of HIPAA are severe and depend on the knowledge of and actions before and during the fact. On one end of the spectrum, if the covered entity had a reasonable amount of prevention in place and could not have known or avoided the violation, the penalty ranges from $100 to $50,000. On the other end of the spectrum, if the covered entity is found willfully negligent by not having enough protection in place or allowing the violation even after having knowledge of it, the penalty ranges from $50,000 to $1,500,000—plus possible imprisonment. Ignorance of the HIPAA rules cannot be used as an excuse for violation.
While the act in its entirety is beyond the scope of this book, Table 1-4 broadly classifies and maps the security requirements to Cisco security products and technologies.
Table 1-4 HIPAA and Cisco Security
HIPAA Security Requirement |
Cisco Security Product/Solution |
Notes |
Identity management and access control |
Cisco ISE, ASA, NGFW |
Identity management and access control to health information is a central theme in HIPAA. Cisco ISE can provide that by controlling access to the network. Further access control can be provided by ASA and NGFW. |
Segmentation |
Cisco ISE, TrustSec, ASA, NGFW |
Segmentation of clinical and administrative information is critical to applying effective security measures. Cisco ISE along with TrustSec-enabled enforcement devices such as ASA and NGFW can provide effective segmentation. |
Encryption |
Various VPN solutions on ASA, NGFW, and routers |
Encryption of data in transit, especially between covered entities, is a critical requirement. Various Cisco VPN solutions can be used to achieve that. |
Logging, audit, and monitoring |
Firepower NGFW and NGIPS with Firepower Management Center (FMC) |
The act requires logging, monitoring, and audit of data access as well as intrusion attempts. Cisco NGFW and NGIPS solutions provide strong intrusion prevention along with logging, monitoring, and audit capabilities with FMC. |
It is important to remember that Table 1-4 provides a generalized overview of the security requirements and corresponding Cisco security solutions. The actual design and implementation will depend on the size of the network and the organization.
Payment Card Industry Data Security Standard (PCI DSS)
The Payment Card Industry Data Security Standard (PCI DSS) is a standard for security mandated by most of the major credit card companies, including Visa, MasterCard, American Express, Discover, and JCB. This standard applies to any organization that processes, stores, or transmits credit card information. This is not a standard required by federal law but rather mandated by the credit card companies and administered by the Payment Card Industry Security Standards Council. Some states, however, directly reference either PCI DSS or an equivalent standard in their laws.
The PCI DSS standard has 6 goals, divided into 12 requirements:
![]() Build and Maintain a Secure Network
Build and Maintain a Secure Network
1. Install and maintain a firewall configuration to protect cardholder data.
2. Do not use vendor-supplied defaults for system passwords and other security parameters.
![]() Protect Cardholder Data
Protect Cardholder Data
3. Protect stored cardholder data.
4. Encrypt transmission of cardholder data across open, public networks.
![]() Maintain a Vulnerability Management Program
Maintain a Vulnerability Management Program
5. Use and regularly update antivirus software or programs.
6. Develop and maintain secure systems and applications.
![]() Implement Strong Access Control Measures
Implement Strong Access Control Measures
7. Restrict access to cardholder data by business need-to-know.
8. Assign a unique ID to each person with computer access.
9. Restrict physical access to cardholder data.
![]() Regularly Monitor and Test Network
Regularly Monitor and Test Network
10. Track and monitor all access to network resources and cardholder data.
11. Regularly test security systems and processes.
![]() Maintain an Information Security Policy
Maintain an Information Security Policy
12. Maintain a policy that addresses information security for employees and contractors.
You will notice that PCI DSS has fairly simple requirements, but one important point to remember is that PCI data often uses the same network infrastructure as other data in an organization. If the PCI data is not segmented, the whole network needs to be PCI DSS–compliant, which increases the cost and complexity of compliance. Hence, while the standard itself does not explicitly call for it, it is important to segment PCI data from other data. Segmentation can be achieved with traditional methods such as access lists and VLANs or with newer technologies, such as TrustSec.
Table 1-5 maps PCI DSS goals to relevant Cisco security products and technologies.
Table 1-5 PCI DSS and Cisco Security Product/Technologies
PCI DSS Goal |
Cisco Security Products/ Technologies |
Build and Maintain a Secure Network |
Cisco Firepower NGFW, Firepower NGIPS, ASA |
Protect Cardholder Data |
Cisco VPN technologies on NGFW, ASA, and routers |
Maintain a Vulnerability Management Program |
Cisco AMP |
Implement Strong Access Control Measures |
Cisco ISE, TrustSec |
Regularly Monitor and Test Networks |
NGFW, NGIPS, FMC, Stealthwatch |
Maintain an Information Security Policy |
N/A |
Security Models
So far in this chapter, we have discussed how to assess risks and create a security policy, taking into consideration regulatory requirements. Creating a security policy is just the first step in securing your organization. A security policy only indicates the requirements of the business and its management. It needs to be implemented to be of any use!
How do you effectively implement a security policy? The answer is by using security models. While it is not necessary to use a defined model, using one will make the implementation and auditing more effective and uniform. A security model helps convert requirements of a policy into a set of rules and regulations.
While an in-depth discussion is not part of the CCIE exam and this book, you should know some of the most common and widely accepted security models:
![]() Bell–LaPadula Model: This state machine model was introduced to enforce access control in government and military applications. This model is primarily focused on the confidentiality of data and controlled access to classified information.
Bell–LaPadula Model: This state machine model was introduced to enforce access control in government and military applications. This model is primarily focused on the confidentiality of data and controlled access to classified information.
![]() Biba Model: This lattice-based model was developed to focus on integrity of data. Data and subjects are grouped into ordered levels of integrity. The model is designed so that subjects may not write to objects in a higher level.
Biba Model: This lattice-based model was developed to focus on integrity of data. Data and subjects are grouped into ordered levels of integrity. The model is designed so that subjects may not write to objects in a higher level.
![]() Clark–Wilson Model: This model was developed to address integrity for commercial activities (whereas the previous two models were developed for government and military applications). The model uses a system of a three-part relationship known as a triple, consisting of a subject, a program, and an object. Within this relationship, a subject can only access an object through a program.
Clark–Wilson Model: This model was developed to address integrity for commercial activities (whereas the previous two models were developed for government and military applications). The model uses a system of a three-part relationship known as a triple, consisting of a subject, a program, and an object. Within this relationship, a subject can only access an object through a program.
![]() Lattice-Based Model: This mandatory access control (MAC)–based model uses a lattice to define the levels of security for subjects and objects. A subject can only access objects that have a security level equal to or lower than its own security level.
Lattice-Based Model: This mandatory access control (MAC)–based model uses a lattice to define the levels of security for subjects and objects. A subject can only access objects that have a security level equal to or lower than its own security level.
A lot of these security models were developed a long time ago for specific use cases. Changing network and security requirements have created a need for better and simpler security models. To address this need, Cisco created the SAFE architecture and model.
Cisco SAFE
The Cisco SAFE model provides a method for analyzing threats, risks, and policies across an organization and implementing controls. It takes into account that all organizations are not the same by providing a modular structure that can be customized for any type and size of organization.
The model divides the network into logical areas called places in the network (PINs), as shown in Figure 1-1.

Figure 1-1 Places in the Network, as Defined by Cisco SAFE
Each PIN is evaluated across a set of six operational functions, called secure domains, as shown in in Figure 1-2.
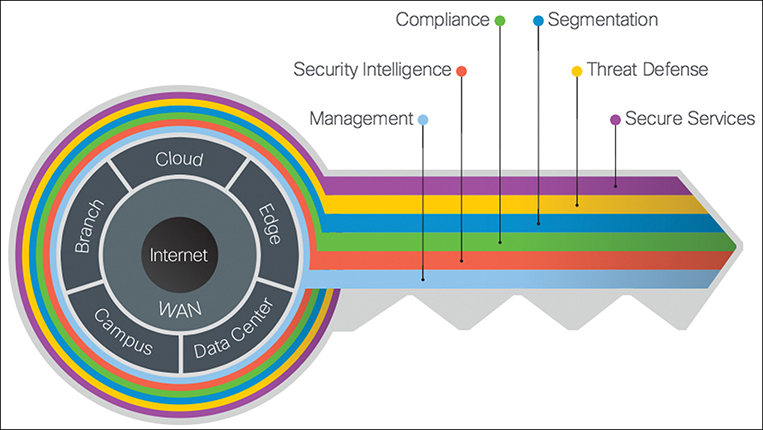
Figure 1-2 The Key to SAFE
Based on the PINs and security domain approach, the SAFE model defines a three-phased approach for building security in the network:
![]() Capability phase: Using business goals, security policy, risks, and threats in each PIN, justify which security capabilities are required.
Capability phase: Using business goals, security policy, risks, and threats in each PIN, justify which security capabilities are required.
![]() Architecture phase: Using the justified capabilities, arrange them in a logical architecture.
Architecture phase: Using the justified capabilities, arrange them in a logical architecture.
![]() Design phase: Using the architecture, create a design that is complete with a product list, configuration, services, and cost.
Design phase: Using the architecture, create a design that is complete with a product list, configuration, services, and cost.
SAFE PINs
As mentioned earlier, the SAFE model divides the network into six logical areas, or PINs. It is not necessary for each organization to have every area, but the model is designed to be modular. You can remove PINs that do not exist in your network. Each PIN represents the infrastructure commonly deployed in these areas, such as routers, switches, firewalls, and so on.
Each of the six PINs has a typical profile and associated threats:
![]() Branch: Branches present a unique security challenge due to their smaller size and larger number of locations. Providing a level of security in branches that is comparable to the campus or data center level is cost-prohibitive. This leaves branches more vulnerable and makes them prime targets. Typical threats in branches include point-of-sale malware, wireless infrastructure exploits such as rogue access points, and exploitation of trust.
Branch: Branches present a unique security challenge due to their smaller size and larger number of locations. Providing a level of security in branches that is comparable to the campus or data center level is cost-prohibitive. This leaves branches more vulnerable and makes them prime targets. Typical threats in branches include point-of-sale malware, wireless infrastructure exploits such as rogue access points, and exploitation of trust.
![]() Campus: Campuses contain a large number and many types of users, including employees and guests. Traditional methods of segmentation are used at the campus level, with very few internal security controls. There is often a lack of access control in the wired network within the campus. All these factors combined make campuses easy targets for phishing, malware propagation, unauthorized network access, and botnet infestation.
Campus: Campuses contain a large number and many types of users, including employees and guests. Traditional methods of segmentation are used at the campus level, with very few internal security controls. There is often a lack of access control in the wired network within the campus. All these factors combined make campuses easy targets for phishing, malware propagation, unauthorized network access, and botnet infestation.
![]() Data center: Data centers contain the crown jewels of an organization and hence get the biggest share of the security budget. However, the data center is also the most targeted PIN. In addition, data centers contain thousands of servers, segmented by application type, data classification, and so on, using traditional manual methods. Managing and auditing these segmentations is increasingly difficult. Typical threats seen in data centers are data exfiltration, malware propagation, and advanced persistent threats.
Data center: Data centers contain the crown jewels of an organization and hence get the biggest share of the security budget. However, the data center is also the most targeted PIN. In addition, data centers contain thousands of servers, segmented by application type, data classification, and so on, using traditional manual methods. Managing and auditing these segmentations is increasingly difficult. Typical threats seen in data centers are data exfiltration, malware propagation, and advanced persistent threats.
![]() Edge: The edge is the most critical PIN in terms of business importance as well as security risk. It is the primary ingress and egress point for traffic to and from the Internet. It is very susceptible to DDoS attacks. Other threats that are common to this PIN are data exfiltration, MITM attacks, and web server vulnerability exploits.
Edge: The edge is the most critical PIN in terms of business importance as well as security risk. It is the primary ingress and egress point for traffic to and from the Internet. It is very susceptible to DDoS attacks. Other threats that are common to this PIN are data exfiltration, MITM attacks, and web server vulnerability exploits.
![]() Cloud: The cloud is the new frontier, bringing high risk along with high cost savings. Security in the cloud is dictated by service-level agreements (SLAs) with the provider and requires regular audits and risk assessments. The primary threats in this PIN are DDoS and MITM attacks, loss of access, data loss, and web server vulnerabilities.
Cloud: The cloud is the new frontier, bringing high risk along with high cost savings. Security in the cloud is dictated by service-level agreements (SLAs) with the provider and requires regular audits and risk assessments. The primary threats in this PIN are DDoS and MITM attacks, loss of access, data loss, and web server vulnerabilities.
![]() Wide area network: The WAN connects other PINs, such as branch, campus, and data centers, together. In a large organization with hundreds of locations, managing security and quality of service (QoS) on the WAN is challenging. Typical threats seen in this PIN are malware propagation, exploitation of trust, unauthorized network access, and MITM attacks.
Wide area network: The WAN connects other PINs, such as branch, campus, and data centers, together. In a large organization with hundreds of locations, managing security and quality of service (QoS) on the WAN is challenging. Typical threats seen in this PIN are malware propagation, exploitation of trust, unauthorized network access, and MITM attacks.
Secure Domains
The SAFE model divides the operational side of security into six secure domains. Every secure domain applies to each PIN in an organization. An evaluation of all the secure domains across each PIN provides a list of security capabilities that are required. These are the six secure domains defined by Cisco SAFE:
![]() Management: This refers to centralized management of devices and systems. Centralized management is essential for consistent security policy, vulnerability patching, security application updates, and alerting. Some of the capabilities within this domain are policy configuration, time synchronization, patch management, and logging/reporting.
Management: This refers to centralized management of devices and systems. Centralized management is essential for consistent security policy, vulnerability patching, security application updates, and alerting. Some of the capabilities within this domain are policy configuration, time synchronization, patch management, and logging/reporting.
![]() Security intelligence: This refers to global aggregation of emerging malware and threats to provide timely detection. A threat protection infrastructure is as good as the security intelligence it receives. The infrastructure needs to be able to dynamically enforce new policies as threats emerge and change. Some of the capabilities within this domain are threat intelligence, malware sandboxing, and posture assessment.
Security intelligence: This refers to global aggregation of emerging malware and threats to provide timely detection. A threat protection infrastructure is as good as the security intelligence it receives. The infrastructure needs to be able to dynamically enforce new policies as threats emerge and change. Some of the capabilities within this domain are threat intelligence, malware sandboxing, and posture assessment.
![]() Compliance: This refers to controls that need to exist to satisfy internal and external compliance requirements, such as those for HIPAA and PCI DSS. Some of the capabilities in this domain include virtual private networks, firewalls, and intrusion prevention systems.
Compliance: This refers to controls that need to exist to satisfy internal and external compliance requirements, such as those for HIPAA and PCI DSS. Some of the capabilities in this domain include virtual private networks, firewalls, and intrusion prevention systems.
![]() Segmentation: This refers to segmentation of data, devices, and users. Traditional manual segmentation uses a combination of network addressing, VLANs, and access lists. Advanced segmentation is identity-aware, dynamic, and automated.
Segmentation: This refers to segmentation of data, devices, and users. Traditional manual segmentation uses a combination of network addressing, VLANs, and access lists. Advanced segmentation is identity-aware, dynamic, and automated.
![]() Threat defense: This refers to the ability to detect, prevent, eliminate, or contain cyber threats. Modern-day threats are evasive and persistent. Correlation of network traffic telemetry, contextual information, and reputation data is required to detect such threats. Some of the capabilities in this domain include intrusion prevention, flow and behavior analysis, antimalware systems, and application visibility controls.
Threat defense: This refers to the ability to detect, prevent, eliminate, or contain cyber threats. Modern-day threats are evasive and persistent. Correlation of network traffic telemetry, contextual information, and reputation data is required to detect such threats. Some of the capabilities in this domain include intrusion prevention, flow and behavior analysis, antimalware systems, and application visibility controls.
![]() Secure services: This refers to technologies such as access control, VPNs, and secure email services. This domain adds security on top of services that are inherently insecure, such as email, network access, and collaboration. Some of the capabilities in this domain include email security, web application firewalls, and VPNs.
Secure services: This refers to technologies such as access control, VPNs, and secure email services. This domain adds security on top of services that are inherently insecure, such as email, network access, and collaboration. Some of the capabilities in this domain include email security, web application firewalls, and VPNs.
Attack Continuum
Cisco SAFE defines three phases of an attack—before, during, and after—together called the attack continuum:
![]() Before: In this phase of the continuum, you need to know the asset being protected and the threat against which you are defending. Establishing policies and implementing prevention to reduce risk belong in this phase.
Before: In this phase of the continuum, you need to know the asset being protected and the threat against which you are defending. Establishing policies and implementing prevention to reduce risk belong in this phase.
![]() During: This phase defines the abilities and actions that are required when an attack gets through. Analysis and incident response are some of the typical activities associated with this phase.
During: This phase defines the abilities and actions that are required when an attack gets through. Analysis and incident response are some of the typical activities associated with this phase.
![]() After: This phase defines the ability to detect, contain, and remediate after an attack. If an attack was successful, any lessons learned need to be incorporated into the existing security solution.
After: This phase defines the ability to detect, contain, and remediate after an attack. If an attack was successful, any lessons learned need to be incorporated into the existing security solution.
For each secure domain in every PIN, you need to define and implement capabilities such that each phase of the continuum is covered.
Figure 1-3 shows various Cisco products and solutions that work across the attack continuum.

Figure 1-3 Cisco Products and Solutions Across the Attack Continuum
Integrating Security Solutions
The threats that current-day networks face are advanced, persistent, and evolving continuously. To protect against them, network and security solutions are becoming more complex. Complexity leads to inefficiency and increased cost. A typical large organization uses multiple security products from multiple vendors. Some organizations use up to 70 different products to secure their networks. Each of these products has different information in different management consoles. In the event of an attack, you have to look at multiple consoles and correlate information manually to even determine that you are under attack.
Most of the recent high-profile cyber attacks have had one thing in common: Security systems detected those attacks, but the event logs were lost in a flood of other logs and went undetected. Why?
To understand the complexity of incidence response, consider an example. Let’s say you are looking at logs from the IPS in your organization, and you come across an attack that happened seven days ago. The only identifying information in the logs is the IP address of the internal host that was the target of the attack. To find out which host and user had that IP address from your internal DHCP range, you will need to go through the DHCP server logs—assuming that your organization stores such logs and you have access to them. From the DHCP logs, you will get a MAC address for the machine—but you will not know what user was logged on during the time of the attack. However, if your organization enforces network access control, you may be able to find that information from the access control system logs. In the absence of a network access control system, you will need to find out where the MAC address is currently connected and what that switch port is connected to. Finally, you will get a physical location of the device and, when you walk to the location, the identity of the user.
This example shows how difficult it can be to respond to and contain an attack. Now multiply the effort by the hundreds of events per day, and you begin to understand how incident response can become slow and ineffective.
To deal with the threats we face today, our security solutions need to evolve and integrate. Multiple security products and solutions contain contextual information about an event. When those products and solutions are integrated, they share this data to be correlated. Such integrations and correlation have a number of benefits:
![]() Better indicators of compromise: Not every event requires immediate remediation. In some cases, remediation may not be required at all. When security products such as IPSs analyze an event in relation to the context of the target or source, they can provide better indicators of compromise. This results in faster response to top threats. For example, consider Windows malware being downloaded by a machine running Linux. Without contextual information about the operating system, this event would be a high-severity event.
Better indicators of compromise: Not every event requires immediate remediation. In some cases, remediation may not be required at all. When security products such as IPSs analyze an event in relation to the context of the target or source, they can provide better indicators of compromise. This results in faster response to top threats. For example, consider Windows malware being downloaded by a machine running Linux. Without contextual information about the operating system, this event would be a high-severity event.
![]() Event logs with contextual data: When security products receive and store contextual data with event logs, responding to events—even days later—becomes much easier. For example, if the username is available in an event log, reaching out to the end user for remediation is easier.
Event logs with contextual data: When security products receive and store contextual data with event logs, responding to events—even days later—becomes much easier. For example, if the username is available in an event log, reaching out to the end user for remediation is easier.
![]() Increased effectiveness: With correlation of events and contextual information, the effectiveness of event detection increases drastically. Considering again the example of a Linux machine downloading Windows malware, an IPS with contextual information about the operating system can ignore that event instead of generating a false-positive event log.
Increased effectiveness: With correlation of events and contextual information, the effectiveness of event detection increases drastically. Considering again the example of a Linux machine downloading Windows malware, an IPS with contextual information about the operating system can ignore that event instead of generating a false-positive event log.
![]() Automated response: When security products are integrated, they can work together to contain and remediate an event automatically. This drastically reduces the time it takes to contain the event. With a lower rate of false positives, the risk associated with automated response is also reduced. For example, consider an IPS that detects malicious activity from an internal endpoint. It can reach out to the network access control system to quarantine the endpoint.
Automated response: When security products are integrated, they can work together to contain and remediate an event automatically. This drastically reduces the time it takes to contain the event. With a lower rate of false positives, the risk associated with automated response is also reduced. For example, consider an IPS that detects malicious activity from an internal endpoint. It can reach out to the network access control system to quarantine the endpoint.
To further understand the benefit of integration of security systems, let’s revisit the previous example of tracing down the user associated with an event that is seven days old. This time, assume that the network access control system in the organization is integrated with the IPS, and it provides contextual information, including username. With this integration in place, you would have the IP address, MAC address, and username in the event log on the IPS. There would be no need to look at the DHCP server or any other logs. The time and effort taken to find the username associated with the event would be reduced to zero!
Integration of security products has begun as vendors have realized its importance. Cisco is leading this charge with multiple open standards drafts and integration between all its security products. Relevant chapters in this book and in the companion book, Integrated Security Technologies and Solutions, Volume II, will introduce integration technologies. For example, an entire chapter in Volume II is dedicated to showing how various Cisco security products integrate with each other.
Summary
In this chapter, you have learned about the threats facing today’s networks and efforts required to protect against them. It all starts with identifying your assets and risks. A security policy helps in documenting risks and prevention requirements. Standards and frameworks provide help in creating a good security policy that meets the various regulations your organization may be subject to. A security model helps implement that security policy uniformly. Finally, you have learned that various security products in the organization should be integrated to provide effective security against advanced threat.
References
“GameOver Zeus Botnet Disrupted: Collaborative Effort Among International Partners,” https://www.fbi.gov/news/stories/gameover-zeus-botnet-disrupted
“U.S. Leads Multi-National Action Against GameOver Zeus Botnet and Cryptolocker Ransomware, Charges Botnet Administrator,” https://www.fbi.gov/news/pressrel/press-releases/u.s.-leads-multi-national-action-against-gameover-zeus-botnet-and-cryptolocker-ransomware-charges-botnet-administrator
“Security Policy Roadmap: Process for Creating Security Policies,” https://www.sans.org/reading-room/whitepapers/policyissues/security-policy-roadmap-process-creating-security-policies-494
“About NIST,” https://www.nist.gov/about-nist
“Framework for Improving Critical Infrastructure Cybersecurity,” https://www.nist.gov/sites/default/files/documents/cyberframework/cybersecurity-framework-021214.pdf
“SAFE Overview Guide: Threats, Capabilities, and the Security Reference Architecture,” http://www.cisco.com/c/dam/en/us/solutions/collateral/enterprise/design-zone-security/safe-overview-guide.pdf
