2
Introduction to IoT Security
Anca D. Jurcut Pasika Ranaweera and Lina Xu
Abstract
In a world with “things” and devices interconnected at every level, from wearables to home and building automation, to smart cities and infrastructure, to smart industries, and to smart‐everything, the Internet of Things (IoT) security plays a central role with no margin for error or shortage on supply. Securing, including authentication of these devices, will become everyone's priority, from manufacturers to silicon vendors (or IP developers), to software and application developers, and to the final consumer, the beneficiaries of the security “recipe” that will accompany these IoT products. Together, all consumers of these products need to adapt to the market demands, innovate, and improve processes, grasp new skills and learn new methods, raise awareness and embrace new training and curricula programs.
In this chapter, we provide a thorough survey and classification of the existing vulnerabilities, exploitable attacks, possible countermeasures as well as access control mechanisms including authentication and authorization. These challenges are addressed in detail considering both the technologies and the architecture used. Furthermore, this work also focuses on IoT intrinsic vulnerabilities as well as the security challenges at every layer. In addition, solutions for remediation of the compromised security, as well as methods for risk mitigation, with prevention and suggestions for improvement are discussed.
Keywords: internet of things; security; attacks; countermeasures; authentication; authorization
2.1 Introduction
The rapid proliferation of the Internet of Things (IoT) into diverse application areas such as building and home automation, smart transportation systems, wearable technologies for healthcare, industrial process control, and infrastructure monitoring and control is changing the fundamental way in which the physical world is perceived and managed. It is estimated that there will be approximately 30 billion IoT devices by 2020. Most of these IoT devices are expected to be of low‐cost and wireless communication technology based, with limited capabilities in terms of computation and storage. As IoT systems are increasingly being entrusted with sensing and managing highly complex eco‐systems, questions about the security and reliability of the data being transmitted to and from these IoT devices are rapidly becoming a major concern.
It has been reported in several studies that IoT networks are facing several security challenges [1–7] including authentication, authorization, information leakage, privacy, verification, tampering, jamming, eavesdropping, etc. IoT provides a network infrastructure with interoperable communication protocols and software tools to enable the connectivity to the internet for handheld smart devices (smart phones, personal digital assistants [PDAs] and tablets), smart household apparatus (smart TV, AC, intelligent lighting systems, smart fridge, etc.), automobiles, and sensory acquisition systems [1]. However, the improved connectivity and accessibility of devices present major security concerns for all the parties connected to the network regardless of whether they are humans or machines. The infiltration launched by the Mirai malware on the Domain Name System (DNS) provider Dyn in 2016 through a botnet‐based Distributed Denial of Service (DDoS) attack to compromise IoT devices such as printers, IP cameras, residential gateways, and baby monitors represents the fertile ground for cyber threats in the IoT domain [82]. Moreover, the cyber‐attack launched at the Ukrainian power grid in 2015 targeting the Supervisory Control and Data Acquisition (SCADA) system caused a blackout for several hours and is a prime example of the gravity of resulting devastation possible through modern day attacks [2]. The main reasons for the security challenges of current information‐centric automated systems is their insecure unlimited connectivity with the internet and the non‐existent access control mechanisms for providing secure and trustworthy communication. Furthermore, the problem of vulnerabilities in IoT systems arises because of the physical limitations of resource‐constrained IoT devices (in terms of computing power, on‐board storage and battery‐life), lack of consensus/standardization in security protocols for IoT, and widespread use of third‐party hardware, firmware, and software. These systems are often not sufficiently secure; especially when deployed in environments that cannot be secured/isolated by other means. The resource constraints on typical IoT devices make it impractical to use very complex and time‐consuming encryption/decryption algorithms for secure message communication. This makes IoT systems highly susceptible to various types of attacks [1,3–7]. Furthermore, addressing the security vulnerabilities in the protocols designed for communication is critical to the success of IoT [8–12,97,98].
This chapter focuses on security threats, attacks, and authentication in the context of the IoT and the state‐of‐the‐art IoT security. It presents the results of an exhaustive survey of security attacks and access control mechanisms including authentication and authorization issues existing in IoT systems, its enabling technologies and protocols, while addressing all levels of the IoT architecture. We surveyed a wide range of existing works in the area of IoT security that use a number of different techniques. We classify the IoT security attacks and proposed countermeasures based on the current security threats, considering all three layers: perception, network, and application. This study aims to serve as a useful manual of existing security threats and vulnerabilities within the IoT heterogeneous environment and proposes possible solutions for improving the IoT security architecture. State‐of‐the‐art IoT security threats and vulnerabilities have also been investigated, in terms of application deployments such as smart utilities, consumer wearables, intelligent transportation, smart agriculture, industrial IoT, and smart city have been studied. The insights presented on authentication and authorization aspects for the comprehensive IoT architecture are the prime contributions of this chapter.
The remainder of this chapter is organized as follows. Section 2.2 provides the IoT classification of attacks and their countermeasures according to the IoT applications and different layers of the IoT infrastructure. Section 2.3 addresses the importance of authentication with respect to security in IoT and presents in detail the existing authentication and authorization issues at all layers. Section 2.4 introduces other security features and their related issues. Additionally, solutions for remediation of the compromised security, as well as methods for risk mitigation, with prevention and suggestions for improvement discussed in the same section. A discussion on the authentication mechanisms in the IoT domain, considering the most recent methodologies, has been presented in Section 2.5. Section 2.6 introduces future research directives such as blockchain, 5G, fog and edge computing, quantum, AI and network slicing. Finally, Section 2.7 concludes this study.
2.2 Attacks and Countermeasures
Security is defined as a process to protect a resource against physical damage, unauthorized access, or theft, by maintaining a high confidentiality and integrity of the asset's information and making information about that object available whenever needed. The IoT security is the area of endeavor concerned with safeguarding connected devices and networks in the IoT environment. IoT enables the improvement of several applications in various fields, such as, smart cities, smart homes, healthcare, smarts grids, as well as other industrial applications. However, introducing constrained IoT devices and IoT technologies in such sensitive applications leads to new security challenges.
IoT is relying on connectivity of myriads of devices for its operation. Hence, the possibility of being exposed to a security attack is highly probable. In Information Technology (IT), an attack is an attempt to destroy, expose, alter, disable, steal, or gain unauthorized access to an asset. For example, cryptographic security protocols are key components in providing security services for communication over networks [10]. These services include data confidentiality, message integrity, authentication, availability, nonrepudiation, and privacy [3]. The proof of a protocol flaw is commonly known as an “attack” on a protocol and it is generally regarded as a sequence of actions performed by a dishonest principal, by means of any hardware or software tool, in order to subvert the protocol security goals. An IoT attack is not much different from an assault against an IT asset. What is new is the scale and relative simplicity of attacks in the IoT – millions and billions of devices are a potential victim of traditional style cyber‐attacks, but on a far greater scale and often with limited or no protection.
The most prevalent devices connected to serving IoT applications for infotainment purposes are smart TVs, webcams, and printers. A vulnerability analysis has been conducted in [81] on these devices using Nessus1 tool to observe that approximately 13% of the devices out of 156 680 were vulnerable which were further classified as critical, high, medium, and low. The vulnerabilities that exist, for example, MiniUPnP, Network Address Translation Port Mapping Protocol (NAT‐PMP) detection, unencrypted telnet, Simple Network Management Protocol (SNMP) agents, Secure Shell (SSH) weak algorithms and File Transfer Protocol (FTP) inherited by webcams, smart TVs and printers are further identified based on manufacturer models.
In this section, we present the results of our study on the existing vulnerabilities, exploitable attacks and possible countermeasures in the context of the IoT and the state‐of‐the‐art IoT security. We surveyed a wide range of existing work in the area of IoT security that use different techniques. We classified the IoT security attacks and the proposed countermeasures based on the current security threats, considering all three layers: Perception, Network, and Application. Figure 2.1 illustrates the typical architecture of IoT and entities which are considered under each layer. Table 2.1 summarizes the taxonomy of attacks and viable solutions of IoT categorized under each layer. These attacks and their corresponding solutions will be further discussed below.
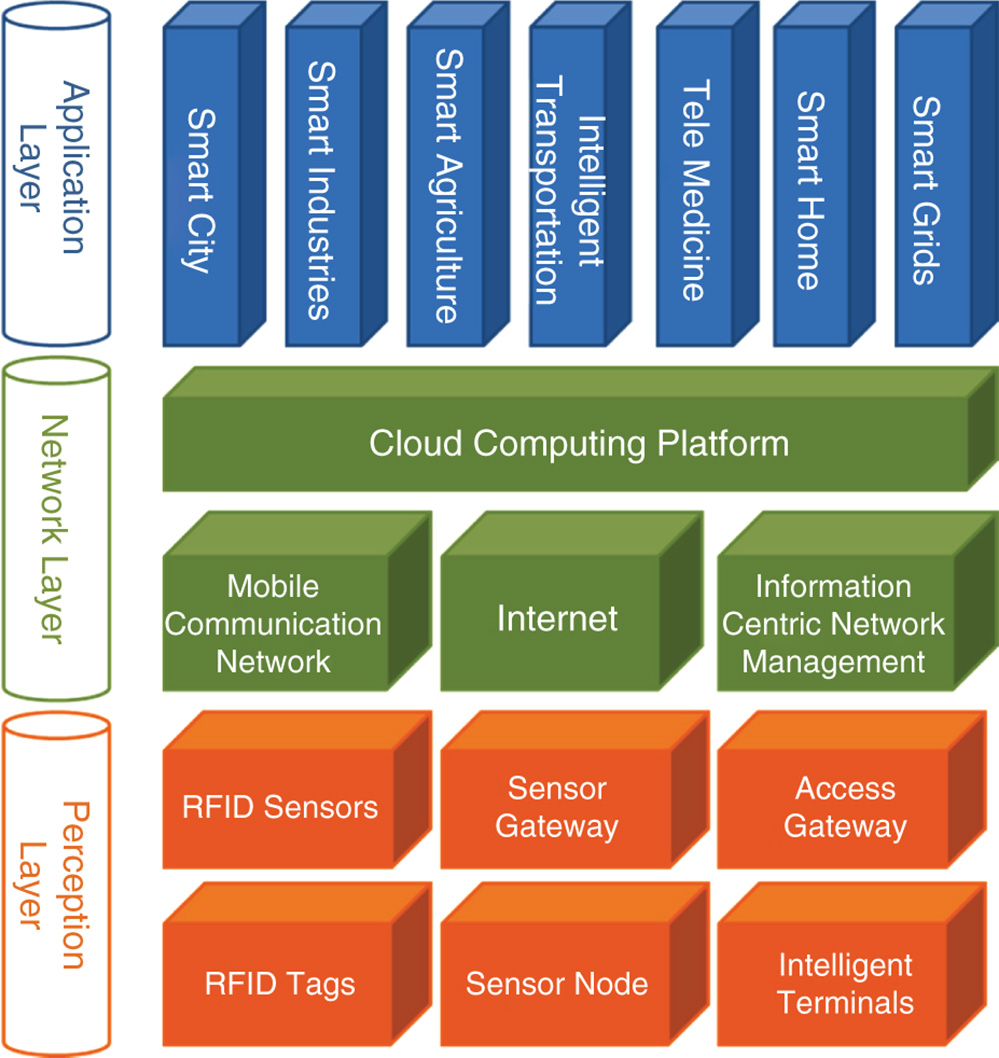
Figure 2.1 IoT architecture.
Table 2.1 Taxonomy of attacks and solutions in IoT layers.
| Layer/component | Attacks | Solutions | |
| a. | Perception Layer | ||
|
Perception Nodes RFID |
Tracking, DoS, repudiation, spoofing, eavesdropping, data newness, accessibility, self‐organization, time management, secure localization, tractability, robustness, privacy protection, survivability, and counterfeiting [13]. | Access control, data encryption which includes non‐linear key algorithms, IPSec protocol utilization, cryptography techniques to protect against side channel attack [9], [14], Hashed‐based access control [15], Ciphertext re‐encryption to hide communication [16], New lightweight implementation using SHA‐3 appointed function Keccak‐f (200) and Keccak‐f (400) [17] | |
| Sensor nodes | Node subversion, node failure, node authentication, node outage, passive information gathering, false node message corruption, exhaustion, unfairness, sybil, jamming, tampering, and collisions [18,19] | Node authentication, Sensor Privacy | |
| Sensor Gateways | Misconfiguration, hacking, signal lost, DoS, war dialing, protocol tunneling, man‐in‐the‐middle attack, interruption, interception, and modification fabrication [20] | Message Security, Device Onboard Security, Integrations Security [21] | |
| b. | Network layer | ||
| Mobile Communication | Tracking, eavesdropping, DoS, bluesnarfing, bluejacking, bluebugging alteration, corruption, and deletion [1], [5], [38] | Developing secure access control mechanisms to mitigate the threats by employing biometrics, public‐key crypto primitives and time changing session keys. | |
| Cloud Computing | Identity management, heterogeneity which is inaccessible to an authentic node, data access controls, system complexity, physical security, encryption, infrastructure security and misconfiguration of software [22] |
Identity privacy – Pseudonym [23–25], group signature [24], connection anonymization [26,30] Location privacy – Pseudonym [23–25], one‐way trapdoor permutation [25,27] Node compromise attack – Secret sharing [27–29], game theory [26], population dynamic model [27] Layer removing/adding attack – Packet transmitting witness [25,27,30], aggregated transmission evidence [27] Forward and backward security – Cryptographic one‐way hash chain [23,24] Semi‐trusted/malicious cloud security – (Fully) homomorphic encryption [31], zero knowledge proof [32] |
|
| Internet | Confidentiality, encryption, viruses, cyberbullying, hacking, identity theft, reliability, integrity, and consent [33] | Identity Management for confidentiality [34], Encryption schemes for confidentiality of communication channels [35], Cloud based solutions to establish secure channels based on PKI for data and communication confidentiality [35] | |
| c. | Application Layer | Data privacy, Tampering Privacy, Access control, disclosure of information [18] | Authentication, key agreement and protection of user privacy across heterogeneous networks [1], Datagram Transport Layer Security (DTLS) for end‐to‐end security [36], Information Flow Control [28] |
2.2.1 Perception Layer
The devices belonging to the perception layer are typically deployed in Low‐power and Lossy networks (LLNs), where energy, memory, and processing power are constricted compared to the localization of network nodes in conventional internet platforms [1]. Therefore, including secure public key encryption‐based authentication schemes would not be feasible because they require high computational power and storage capacity. Hence, developing a lightweight cryptographic protocol would be a challenging task when scalability, context‐awareness, and ease of deployment must also be considered [2].
There are several problems and attacks to be considered for the perception layer. We will be addressing these as shown in Table 2.1 and also by discussing the existing problems and attacks for perception nodes, sensor nodes and sensor gateways.
2.2.1.1 Perception Nodes
Radio frequency identification (RFID) nodes and tags are typically used as perception nodes. RFID tags could be subjected to Denial of Service (DoS – from radio frequency interference), repudiation, spoofing, and eavesdropping attacks in the communication RF channel [1,6,13]. Moreover, reverse engineering, cloning, viruses (the SQL injection attack in 2006), tracking, killing tag (using a pre‐defined kill command to disable a tag), block tag (employing a jammer such as a Faradays' cage) and side‐channel attacks through power analysis are attacks which could compromise the RFID physical systems [84]. These attacks are feasible because of the low resources of RFID devices and comparatively weaker encryption/encoding schemes. Solutions to overcome these vulnerabilities and the corresponding exploitable attacks include access control, data encryption which includes non‐linear key algorithms, IPSec protocol utilization, cryptography techniques to protect against side‐channel attacks [9,14], hashed‐based access control [15], ciphertext re‐encryption to hide communication [16], new lightweight implementation using SHA‐3 appointed function Keccak‐f (200) and Keccak‐f (400) [17].
2.2.1.2 Sensor Nodes
Sensor nodes, such as ZigBee, possess additional resources compared to RFID devices with a controller for data processing and interoperability of sensor components, a Radio Frequency (RF) transceiver, a memory, the power source and the sensing element [1]. Even though the sensor nodes follow a fairly secure encryption scheme due to the elevated resources, attacks such as node tampering, node jamming, malicious node injection, Sybil, and collisions [18,19] could exploit the vulnerabilities due to the nature of transmission technology and remote/distributed localization of them. A malware exploiting a flaw in the radio protocol of ZigBee caused a Save Our Souls (SOS) code illumination in smart Philips light bulbs as a demonstration of weakness in sensor node systems in 2016 [82]. Additionally, GPS sensors are vulnerable to jamming or data‐level and signal‐level spoofing which results in Time Synchronization Attacks (TSAs) targeted on Phasor Measurement Units (PMUs) of various IoT deployments that rely on GPS for locating or navigation‐based services [85]. Possible countermeasures for such attacks are node authentication and sensor privacy techniques.
2.2.1.3 Gateways
Sensory gateways are responsible for checking and recording various properties such as temperature, humidity, pressure, speed, and functions of distributed sensor nodes. User access, network expansion, mobility, and collaboration are provided using sensor gateways.
These channels are also vulnerable to several attacks such as misconfiguration, hacking, signal lost, DoS, war dialing, protocol tunneling, man‐in‐the‐middle attack, interruption, interception, and modification fabrication [20]. Moreover, perception layer devices could be subjected to Side‐Channel Attacks (SCA) such as Differential Power Analysis (DPA), Simple Power Analysis (SPA), timing, and acoustic cryptanalysis [6]. To ensure security with respect to sensory gateways; message security, device on board security and integrations security are suitable proposed solutions [21].
2.2.2 Network Layer
Network Layer facilitates the data connectivity to perception layer devices for accomplishing the functionality of various applications in the Application layer. Because this layer is a connectivity provider for other layers, there are probable security flaws which would compromise the operations of the entire IoT architecture.
2.2.2.1 Mobile Communication
Mobile devices are the main interfaces of human interaction for IoT technology which range from smart phones, PDAs to mini‐PCs. The state‐of‐the‐art for mobile devices are extensively resourceful with their location services, biometric sensors, accelerometer/gyroscope, extended memory allocations, etc. The connectivity options range from RF, Low Rate Wireless Personal Area Networks (LR‐WPAN/IEEE 802.15.4), Near Field Communication (NFC), Wireless Fidelity (Wi‐Fi) to Bluetooth. However, these devices are vulnerable to DoS, sinkhole, bluesnarfing, bluejacking, blue bugging, alteration, corruption, deletion of data, and traffic analysis attacks [1,5,6,38]. In addition, mobile devices are also vulnerable for phenomena such as cloning, spoofing, and various battery draining attacks explained in [83]. Even the technologies LR‐WPAN, Bluetooth, and Wi‐Fi are vulnerable to data transit attacks [82]. However, current standards of mobile devices have the means to improve the security through development of secure access control mechanisms to mitigate threats by employing biometrics, public‐key crypto primitives, and time‐changing session keys.
2.2.2.2 Cloud Computing
A cloud computing platform is the prime entity in IoT for centralized processing and storage facilitation for IoT applications [37]. Through cloud computing, IoT applications can enable higher computing power with unlimited storage capacity for a low cost, while maintaining versatile accessibility. Reliance on standalone dedicated server‐based services is superseded by remote cloud‐based server farms with outsourced services. However, outsourcing information to be stored in a remote location could raise security concerns. Privacy preservation is the most inevitable issue with cloud computing among other flaws such as physical security, anonymity, data access control failure, identity management, and direct tampering of the cloud servers [1,22]. Several security solutions have been proposed in different areas for clouds including: (i) Identity privacy – Pseudonym [23], [24], [25], group signature [24], connection anonymization [26,30]; (ii) Location privacy – Pseudonym [23–25], one‐way trapdoor permutation [25,27]; (iii) Node compromise attack – Secret sharing [27–29], game theory [26], population dynamic model [27]; (iv) Layer removing/adding attack – Packet transmitting witness [25,27,30], aggregated transmission evidence [27] (v) Forward and backward security – Cryptographic one‐way hash chain [23,24]; (vi) Semi‐trusted/malicious cloud security – (Fully) homomorphic encryption [31], zero knowledge proof [32].
2.2.2.3 Internet
The term Internet stands for the holistic global networking infrastructure which scopes from private, public, academic, cooperate networks to government networks [1]. The connectivity through the Internet is formulated by Transmission Control Protocol/Internet Protocol (TCP/IP) and secured through various protocols such as Secure Socket Layer (SSL)/Transmission Layer Security (TLS), IPSec, and SSH. In IoT, however, Datagram Transport Layer Security (DTLS) is used as the communication protocol [1,37]. Since the Internet is accessible for everyone, the amount and nature of vulnerabilities outweigh the effectiveness of existing secure communication protocols [3–5,7,8,10,11] due to its implosive access capacity. Probable attacks are viruses, worms, hacking, cyber bullying, identity theft, consent, and DDoS [1,33]. Countermeasures to overcome these attacks include Identity Management for confidentiality [34], Encryption schemes for confidentiality of communication channels [35], Cloud‐based solutions to establish secure channels based on Public Key Infrastructure (PKI) for data and communication confidentiality [35].
2.2.3 Application Layer
As illustrated in Figure 2.2, possible applications for IoT are expanded into every industry available in the current era, in addition to myriads of non‐industrial applications developed for automation purposes. In general, feasible attacks on the IoT application layer could be represented in two forms. They are software‐based and encryption‐based attacks. In the software attacks, most attacks are based on malicious software agents, apart from the phishing attacks, where the attacker reveals the authentication credentials of the user by impersonating as a trusted authority. Malware, worms, adware, spyware, and Trojans are highly probable occurrences with the heterogeneity of IoT applications and their broader services [6]. Encryption‐based attacks are the approaches taken to exploit the procedural nature of the cryptographic protocols and their mathematical model through extensive analysis. Cryptanalytic attacks, ciphertext only attacks, known plaintext attacks, and chosen plaintext attacks exemplify such possible threats [18].

Figure 2.2 IoT applications.
There are several solutions proposed in the literature for the security of IoT applications such as authentication, key agreement and protection of user privacy across heterogeneous networks [1], DTLS for end‐to‐end security [36], and information flow control [28]. The countermeasures for software‐based authentication should be taken for mitigating attacks such as phishing attacks; through the verification of the identity of malicious adversaries before proceeding.
2.2.3.1 Smart Utilities – Smart Grids and Smart Metering
Smart Grids are the future of energy distribution for all industrial and residential sectors. IoT plays a major role in smart grids for establishing the communication and monitoring protocols with consumers of energy. Smart grid is a decentralized energy grid with the ability to coordinate the electricity production in relation to the consumption or consumption patterns of the consumer. These systems are featuring monitoring technology called as Advanced Metering Infrastructure (AMI)/smart metering/net metering; which can measure and update the power consumption parameters to both entities in real time [39]. Additionally, smart grids are incorporating renewable energy sources commissioned in the vicinity of the consumer to cater the bidirectional energy flow for mitigating energy deficiencies [1].
Figure 2.3 illustrates a Smart Grid Architectural Model (SGAM) proposed by the coordinated group of European Committee for Standardization – European Committee for Electrotechnical Standardization – European Telecommunications Standards Institute (CEN‐CENELEC‐ETSI), which offers a framework for smart grid use cases [76]. This architecture formulates three dimensions which amalgamate five functional interoperability layers with energy sector domains and zones that account for power system management [77]. This holistic framework is capable of reinforcing the design stages of the smart energy systems. The IoT technologies could be amalgamated with the SGAM framework to establish the bi‐directional communication.

Figure 2.3 Smart grid architectural model.
All the monitoring applications are developed with IoT infrastructure, with grid controlling access granted to the grid, controlling officers for pursuing configurations while the consumers can only visualize the consumption details via a mobile device. The information circulated through the AMI may pose a privacy concern for consumers for disseminating information regarding their habits and activities, where the impact could be severe for industries. Due to the heterogeneous nature of communication equipment deployed with IoT, and rapidly increasing population and industries, it would cause scalability issues for security. Smart grids are distributed across the power serving area and are, therefore, exposed to adversaries.
As the energy distribution system is the most critical infrastructure that exists in an urban area, the tendency to convert prevailing wired power‐line communication (sending data over existing power cables) based controlling and monitoring channels to the wireless medium, with the introduction of IoT technologies, would expose the entire system to unintended security vulnerabilities. The intruders, using the proper techniques, could perpetuate AMI interfaces stationed at every household or industrial plant. Once access is granted to the hostile operators, potential outcomes can be devastating from disrupting the level of energy flow from a local grid substation to overloading the nuclear reactor of a power station. The availability of the grid could be compromised from IP spoofing, injection, and DoS/DDoS attacks [39]. Thus, access controlling for devices used in AMI and grid‐controlling systems should be secured with extra countermeasures.
2.2.3.2 Consumer Wearable IoT (WIoT) Devices for Healthcare and Telemedicine
IoT‐based healthcare systems are the most profitable and funded projects in the entire world. This is mainly due to the higher aggregate of aging people and the fact that health is the most concerning aspect of human life. A sensory system embedded with actuators is provided for individuals to use as a wearable device (i.e. wearable Internet of Things [WIoT] device), illustrated in Figure 2.4. A WIoT device can be used for tracking and recording vitals such as blood pressure, body temperature, heart rate, blood sugar, etc., [39]. This data can be conveyed and stored in a cloud as a Personal Health Record (PHR) to be accessed by the user and the assigned physicians.

Figure 2.4 WIoT devices.
Since the data handled in IoT‐based healthcare is personal, privacy is the most demanding security issue. Hence, the access control mechanism for wearable devices as well as for PHRs must be well secured. However, employing strong crypto primitives for enhancing the authentication protocols of PHRs is possible as they are also stored in cloud environments. Hence, the same privacy concerns presented in Section 2.3.2.2 under cloud computing apply. Moreover, a method for assuring anonymity of patients should be developed in case the PHRs are exposed to external parties, because they are stored in Cloud Service Providers (CSPs). Wearable devices also face the resource scarcity issues for battery power, memory, and processing level [39]. Thus, a lightweight protocol for authentication and access control should be employed [101]. Similar to all other IoT applications, heterogeneous wearable devices produced by different manufacturers would employ diverse technologies for developing communication protocols. Thus, developing a generic access control policy would be extremely challenging.
2.2.3.3 Intelligent Transportation
Intelligent Transportation Systems (ITS) are introduced to improve transportation safety and decrease traffic congestions while minimizing environmental pollution. In an ITS system, there are four main components; vehicles, roadside stations, ITS monitoring centers and security systems [39]. All information extracted from vehicular nodes and roadside stations are conveyed to the ITS monitoring center for further processing; while the security subsystem is responsible for maintaining overall security. The entire system could be considered as a vehicular network, where the communication channels are established between Vehicle‐to‐Vehicle (V2V), Vehicle‐to‐Infrastructure (V2I), Vehicle‐to‐Pedestrian (V2P), and Vehicle‐to‐Grid (V2G) [39]. These communication links are implemented using technologies like RFID and Dedicated Short Range Communication (DSRC) for launching a large Wireless Sensor Network (WSN) [1]. The vehicular nodes and the entire data storing and monitoring infrastructure form a viable IoT deployment.
Figure 2.5 illustrates an ITS model, which enables communication among vehicular entities traveling through different mediums (airborne, land, and marine) with various technologies such as satellite, mobile, Wireless Local Area Network (WLAN), etc. Such a system would enable services like real‐time updated navigation, roadside assistance, automated vehicular diagnostics, accident alerting system and self‐driving cars [78]. Thus, massive divergence in the applicability of ITS deployment raises the requirement for a ubiquitous wireless connectivity with access points.

Figure 2.5 Intelligent transportation system.
As mentioned above, a larger number of entry points to a vehicular network makes it vulnerable to diverse attacks which can be targeted toward many sources [39]. At the same time, the privacy of drivers should be ensured from external observers, though drivers are not participating in any authentication activity. Authentication mechanisms are initiated between V2V interfaces where they can be exploited by an invader impersonating another vehicle or a roadside station. Therefore, a mechanism to verify the identity of the vehicles or roadside stations should be developed with a proper authentication mechanism employing a Trusted Third Party (TTP).
In some V2V communication systems, an On Board Diagnostic (OBD) unit is utilized to extract information directly from the Engine Control Unit (ECU) [1]. The OBD port could be used to manipulate the engine controls of a vehicle and could then be remotely accessed via the systems being developed. Thus, securing the access to the OBD port is vital.
2.2.3.4 Smart Agriculture
Agriculture is the most crucial industry in the world as it produces food and beverages by planting crops such as corn, rice, wheat, tea, potatoes, oats, etc. With the rapid worldwide population growth accounting for resource depletion, pollution, as well as the scarcity of human labor; agriculture is becoming an demanding industry. Automation is the most probable alternative for improving the effectiveness of the agriculture industry. Thus, IoT could play a vital role in such automation. IoT infrastructure could be deployed to perform climate/atmospheric, crop‐status monitoring and livestock tracking. Climatic sensors, water/moisture level sensors and chemical concentration/acidity sensors along with visual sensors could be deployed for crop‐status monitoring, while automated water and fertilizer dispersing mechanisms are in place within the bounds of the plantation. Additionally, livestock tracking is another aspect of smart farming implemented through the deployment of Local Positioning Systems (LPSs) on farm animals.
This type of a smart system would provide benefits such as the ability to utilize the fertilizer and water usage while maximizing crop production through mitigated effects of climatic deficiencies. The fruition science and “Hostabee” are two live cases of smart agriculture solutions used currently by the plantation industry [78].
Because of the diverse nature of sensor devices used in smart agriculture applications, integrating them into a holistic system may raise concerns about the compatibility of technologies among the variety of manufacturers and those protocols in which communication is established. As the plantations or fields are extending to larger areas, the number of IoT‐enabled sensory systems to be deployed will be immense. Handling the data flow of such a large number of individual sensors with different data representations dispersed throughout a broad geographical region exerts the requirement for a communication technology with a higher coverage and moderate data rates which could not be satisfied by low‐range communication technologies such as Bluetooth or NFC. However, DSRC would be a suitable technology to create a WSN with smart agriculture sensors, as it is compatible with ITSs.
As the IoT devices are disseminated across a larger geographical extent, the probability of any IoT device being compromised is high as they are exposed. Perception level attacks are probable with these devices as they are sensory nodes and would have limited resources for both processing and storing information. The spoofing, impersonation, replay and Man‐in‐the‐Middle (MiM) attacks are probable with this application [80]. This raises the requirement for a proper authentication scheme as all perception level attacks could be mitigated using such a countermeasure.
2.2.3.5 Industrial IoT (IIoT)
M2M‐based automation systems are quite common for industries such as oil and gas manufacturers. These industries are vast and the machinery employed is massive, expensive, and poses a significant risk to machine operators. Functions such as oil exploration by drilling, refining, and distributing are all conducted using automated machinery controlled through Programmable Logic Controllers (PLCs) based on SCADA systems. Although, the current M2M infrastructure is ideal for controlling the machinery, remote monitoring and accessibility is limited while a proper data storage and processing mechanism for decision making is not yet available. Thus, the requirement for IoT arises to improve operational efficiency by optimizing control of robots, reducing downtime through predictive and preventive maintenance, increasing productivity and safety through real‐ time remote monitoring of assets [78]. IoT sensor nodes could be deployed at the machinery while monitoring tools could be integrated without affecting the operation of SCADA systems. Hence, SCADA systems could be optimized to enhance productivity.
The Smart Factories term is an adaptation of Industrial Internet of things (IIoT), introduced as “Industry 4.0” to represent the Fourth Industrial Revolution (4IR) [79]. This standard signifies a trend of automation and data exchange in manufacturing industries which integrate Cyber‐Physical Systems (CPS), IoT, and Cloud Computing based Data analytics [78,79]. The interoperability, information transparency, technical assistance and decentralized decision making are the design principles of Industry 4.0 standard. BOSCH has developed connected hand‐held tools which could monitor location, current user, and task‐at‐hand; analyzed and utilized for improving the efficiency in industrial labor [78]. Thus, the deployment of IoT across industry is imminent.
The security of industrial applications is a major concern, as any hostile intrusion could result in a catastrophic occurrence for both machinery and human operators. The SCADA systems are no longer secure (e.g. Considering the recent events [2]) due to their isolated localization and operation. However, main controlling functions are maneuvered within the control station located inside the industrial facility, while limited egress connectivity is maintained via satellite links with VSAT (Very Small Aperture Terminal) or microwave in the case of offshore or any other industrialized plants of such nature.
Due to their offline nature, the probability of any online intrusion is minimal. Though, any malicious entity such as a worm or a virus injected to the internal SCADA network could compromise the entire factory. Once inserted into the system, the intention of the malicious entity would be to disrupt the operations of the facility and its machinery. Thus, limiting the possibility for any malicious insurgence from the internal network and employing effective Intrusion Detection System (IDS) to detect malicious entities, would be the most suitable countermeasure for this application.
2.2.3.6 Smart Buildings, Environments, and Cities
Smart city is a holistically expanded inclusion of smart buildings and smart environments along with other smart automation systems formed to improve the quality of life for residents in a city. This is, in fact, the most expandable version of any IoT application in terms of cost for infrastructure deployment and geographical extent. In this concept, as shown in Figure 2.6, sensors are deployed throughout the building, environment, or the city for the purpose of extracting data of varied parameters such as temperature, humidity, atmospheric pressure, air density/air quality, noise level, seismic detection, flood detection, and radiation level. CCTV streams and LPSs would be a valuable input for smart building and smart cities to detect intrusions, monitor traffic and emergencies. All other smart systems explained in the previous sections are, in fact, subsystems of a functional smart city.
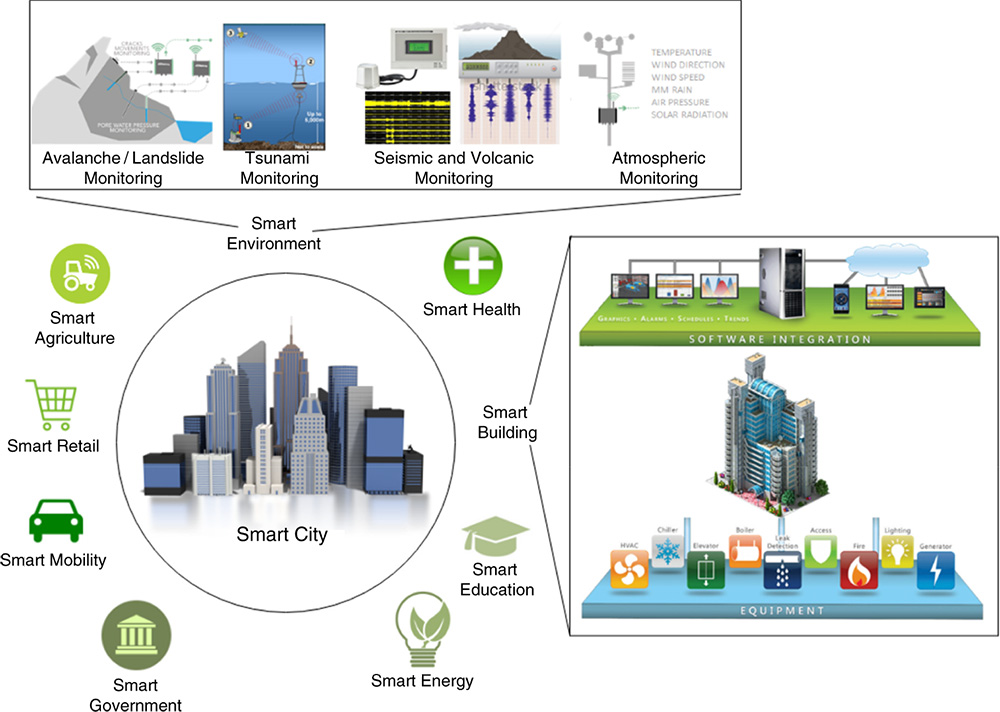
Figure 2.6 Smart city concept.
Due to various parameters to be gathered from the sensory acquisitions, heterogeneity is immense and the implementation is arduous [39]. At the same time, management of the gathered Big Data content is not scalable. Thus, providing security for all the applications in smart cities would be extremely challenging. Most of the Big Data content extracted from the sensors is forwarded to clouds through M2M authentication. Because of large data transmissions, cryptographic schemes should be lightweight and the authentication mechanism should be dynamic. DoS or DDoS attacks are most probable and could be mitigated with a strong authentication mechanism [1]. Individual sensors could be compromised resulting in the initiation of fake emergencies and access control methods should be improved to avoid such inconsistencies at the sensor level.
The paper [40] introduces applications of IoT with specific focus on smart homes. The study presented in [40] claims that although smart homes are offering comfortable services, security of data and context‐oriented privacy are also a major concern of these applications. The security and privacy issues in IoT applications have also been studied in [41].
2.3 Authentication and Authorization
Authentication and access control mechanisms hold a great deal of significance in IoT. Without a proper mechanism for access control, entire IoT architecture could be compromised, as IoT devices are highly reliant on the trustworthiness of the other components to which they are connected. Thus, a proper access control mechanism is paramount to mitigate the flaws in the current IoT infrastructure.
Access control mechanisms are comprised of two stages (Figure 2.7) [1]: (i) Authentication and (ii) Authorization.

Figure 2.7 Typical access control System.
2.3.1 Authentication
Authentication is the process of verifying the identity of an entity [2]. The entity to be verified could either be human or a machine. Authentication is the first phase of any access control mechanism which can determine the exact identity of the accessing party in order to establish the trust of the system. In most cases, authentication is initiated between a human and a machine in a process to log into the internet banking portal by entering the credentials. However, in this scenario, the access‐seeking entity does not have a guarantee regarding the identity of the access granting entity. In order to overcome this concern, mutual‐authentication should be established between the entities, by verifying the identity of the access‐granting entity with the involvement of a TTP, such as a Certificate Authority (CA) [2]. CAs are globally recognized institutions which are responsible for issuing and maintaining secure digital certificates of web entities registered under them. These certificates are imperative for the operation of all modern day authentication protocols such as SSL/TLS, IPSec, and HTTPS.
The process of authentication is merely facilitating credentials of an entity to the access granting system, which are unique to that entity and could only be possessed by them. This mechanism could be enabled with or without a TTP. The credentials used are often categorized as factors. The authentication schemes' accuracy and efficiency depend on the number of factors engaged in the mechanism. The types of factors are listed below.
- Knowledge factor – passwords, keys, PINs, patterns
- Possession factor – Random Number Generators (RNG), ATM card, ID card
- Inherence factor – Biometrics such as fingerprint, palm print, iris, etc.
Recent innovations in embedding biometric sensors to smart handheld devices have enabled the possibility of using multi‐factor multi‐mode (if more than one bio metric is used for verification) Human‐to‐Machine (H2M) authentication protocols for IoT devices. However, Machine‐to‐Machine (M2M) authentication can only be conducted using cryptographic primitives. Moreover, including strong cryptographic primitives (PKI, Hashing, Timestamps, etc.) for the authentication protocols involved is crucial in order to ensure data confidentiality, integrity, and availability; as the credentials being conveyed are highly sensitive and unique for the authenticating entity.
2.3.2 Authorization
Authorization is the process of enforcing limits and granting privileges to the authenticated entities [42]. In simple terms, this is determining the capabilities of an entity in the system. In order for an entity to be authorized for performing any action, the identity of that entity should be verified first through authentication. According to Figure 2.7, an administrator usually configures the authorization database for granting access and rights to system resources. Each resource is assigned with different rights such as read, write, and execute. Depending on the level of authorization (clearance) being set by the administrator, each authenticated entity can perform different actions on resources. A typical access control system has a policy for granting rights. These policies could vary from Discretionary Access Control (DAC), Mandatory Access Control (MAC) or a Multi‐Level Security (MLS) model such as Role Based Access Control (RBAC) [42]. In DAC, the administrator specifies the rights, while in MAC there are rules set by the system for assigning rights for subjects. Clearances are granted according to the role of the authenticated entity (Roles: course coordinator, lecturer, or student in a university) in RBAC.
2.3.3 Authentication at IoT Layers
Authentication is the most critical security requirement in IoT for preserving user identity and mitigating the threats mentioned in the previous sections. With each IoT application, more hardware devices are introduced to be integrated to the IoT network. The authentication is the mechanism used to ensure the connectivity of those components to the existing ones. Authentication mechanisms involve cryptographic primitives for transmitting credentials securely. The strength of the scheme is entirely dependent on the crypto primitives being used. However, developing a generic solution would not be feasible, because differing layers attribute different requirements in IoT and the resources available for processing, memory, and energy are diverse. Therefore, we will discuss the authentication requirements for each layer.
2.3.3.1 Perception Layer
The Perception layer includes all the hardware devices or the machines to extract data from IoT environments. In most cases, the authentication initiates as M2M connections. Thus, in this layer, authentication could be conducted either as peer authentication or origin authentication [1]. In peer authentication, validation occurs between IoT routing peers, preliminary to the routing information exchanging phase; while validating the route information by the connected peer IoT devices with its source is origin authentication. This method enhances the security in M2M communication. Though as mentioned previously, devices in Perception layer are inheriting inadequate resources for generating strong cryptographic primitives.
2.3.3.1.1 Perception Nodes
These nodes are distributed across the IoT environment. Mostly, they are RFID tags and RFID readers/sensors, where few RFID tags are connected to a RFID reader. The connection establishment between RFID tags and the reader does not involve an authentication mechanism and would be vulnerable if the RFID tags could be cloned. An Identity Based Encryption (IBE) scheme was proposed by [39] for establishing secure communication channels between RFID tags. Due to resource scarcity, an authentication protocol might be implemented using techniques such as Elliptic Curve Cryptography (ECC) based Diffie‐Hellman (DH) key generation mechanism [1]. The generated keys, once they are transmitted to each end, could be used as the shared symmetric key for information transferring via the medium securely [42]. However, MiM attacks are still feasible and could be solved by employing the ephemeral DH method; changing the ECC DH exponents for each connection establishment as a session key.
2.3.3.1.2 Sensor Nodes and Gateways
Sensor nodes face the similar security flaws as the perception nodes. Thus, deploying a proper authentication scheme could eliminate the possibility of being exposed at a very low level. However, sensors are much more intelligent and resourceful than perception nodes. Hence, M2M authentication could be established as peer authentications and the origin authentication could be established via the sensor gateway. Similarly, to the perception nodes, ECC‐based DH key exchange would be ideal for sensor nodes, where the ephemeral exponents are facilitated by the sensor gateway acting as a TTP. Identity validation of the sensor gateway should be conducted prior to any data transfer. Even though using certificates for identity determination is not practical, a similar parameter such as a serial number could be used when registering the sensor node in the IoT environment and all the identities are stored in the sensor gateway for validation. Sensor gateway should also possess a unique identity for mutual authentication to be established between the sensor node and the gateway. Moreover, countermeasures such as integrity violation detection (using Hashed Message Authentication Code – HMAC or Cipher Block Chaining Mandatory Access Control – CBC‐MAC) and timestamps should be employed with the authentication protocols involved.
2.3.3.2 Network Layer
IoT network layer is integrated on top of the existing TCP/IP internet protocols. In this section, we discuss the significance of the authentication for the components of the network layer.
2.3.3.2.1 Mobile Communication
Security for mobile communication at the network layer was not a critical necessity until the inception of IoT, as most of the mobile applications were relying on the inbuilt security protocols of the corresponding mobile technology (such as Global System for Mobile Communication – GSM, Wireless Code Division Multiple Access – WCDMA, High Speed Packet Access – HSPA or Long Term Evolution – LTE). With IoT, inbuilt authentication schemes are no longer foolproof, considering the potentiality for integrating technologies embedded in addition to the mobile technologies. Current security level and comprised resources (such as processor, memory, and operating system) in mobile devices are adequate for designing tamper resistance authentication protocols at the network layer [5]. However, the existing key generation algorithms used in TCP/IP protocols for generating large and costly asymmetric keys (Rivest Shamir Adleman (RSA), ElGamal, or Paillier), are still not feasible to be used with mobile devices. Thus, generating unbreachable and lightweight keys would be the most challenging task in mobile communication.
Yao et al. [96] proposed a lightweight no‐pairing Attribute Based Encryption (ABE) scheme based on ECC that is designed for handheld devices. Even though the improved mathematical complexity and linear relationship of the number of attributes with computational overhead are improving the robustness of the proposed ABE scheme, scalability of the scheme would be highly questionable with enormous amount of IoT devices. IBE schemes are also adoptable, if taking the identity parameter as the mobile number or the user Social Security Number (SSN) for developing the authentication scheme integrating with ECC [39].
Current mobile devices include different biometric sensors for extracting biometrics such as fingerprint, iris, facial, and voice imprints. Biometrics can be used as unique keys that could be used for authentication and can be employed with H2M authentication. As the majority of the mobile devices at operation in an IoT environment are handled by a human user, the authentication design and key generation could be based on biometrics. The security of the biometrics schemes could be enhanced using several biometrics (multi‐mode) integrated into multi‐factor authentication schemes. These biometrically generated keys could be used as the signatures of each mobile entity, for the verification of their identities and, for conveying a secure session key among the communicating parties with proper encryption schemes. Additionally, authentication credentials should be checked for probable integrity violations in order to avoid MiM attacks.
2.3.3.2.2 Cloud Computing
Clouds are the storage facility of IoT architecture and they are quite resourceful in terms of memory and processing [37]. Thus, authentication should employ strong keys that are generated using public‐key algorithms such as RSA or ElGamal, which are inviolable cryptographic primitives if the executing authentication mechanism are computationally feasible with the available resources. A symmetric key (Advanced Encryption Standard [AES], Triple Data Encryption Standard (TDES), etc.) to be used in data transferring between the IoT devices and the cloud could be generated and shared among the entities engaged in communication. Existing CAs could be used to validate the identity of the parties involved in communication via mutual authentication schemes for establishing the trust.
However, the main concern in cloud computing is privacy of the user data. A strong authentication scheme does not ensure the misuse of information by the CSP. Thus, approaches such as blockchain and homomorphism should be considered for enhancing the privacy. The authentication schemes would be more secure in these schemes, as blockchain support pseudonymity (the nodes are identified from hashes or public keys – CA not required and simplify the authentication scheme) and the homomorphism facilitates an additional layer of encryption to secure the communication [39].
Authorization techniques in clouds should be also be considered, as accessing the information in the clouds is vital for the IoT design. Existing access control mechanisms such as RBAC and MAC are no longer scalable or interoperable. Thus, a novel method called Capability‐Based Access Control (CapBAC), which uses capability‐based authority tokens to grant privileges to entities was proposed by Kouicem et al. [39].
2.3.3.2.3 The Internet
Even though authentication in most applications on the Internet is pursued by either SSL or IPSec protocols; IoT uses the DTLS as its communication protocol. However, the dependability of CAs for validating authentication parties still exists. Chinese CA WoSign was issuing certificates for false subjects in 2016, leaving an easier access to systems through wrongfully validated certificates for the attackers [2]. This happens when the trust of the system is centralized into a single entity. Thus, distributed access control schemes such as OpenPGP (widely used for email encryption) have formidable odds in succeeding in IoT infrastructure. Hokeun et al. in [2] introduces a locally centralized and globally distributed network architecture called Auth. Auth is to be deployed in edge devices for providing authorization services for locally registered entities, by storing their credentials and access policies in its database. Since the other instances of Auth are being distributed globally in the network, this maintains the trust relationships among them for granting authorizations for IoT devices acting as a gateway. Providing a solution to the trust issue of CAs is the main concern for the Internet, as the security level in existing protocols is quite adequate.
2.3.3.3 Application Layer
Heterodyne nature of the IoT predicates the requirement for different approaches of access control mechanisms for different applications. Most of the existing application layer H2M authentication schemes are two‐factor authentication schemes, while the M2M ones are web based such as in SSL. The applicability and effectiveness of existing schemes are evaluated for each IoT application, since a generic solution is infeasible.
2.3.3.3.1 Smart Utilities – Smart Grids and Smart Metering
When using proper techniques, the intruders could perpetuate AMI interfaces stationed at every household or industrial plant. Once the access is granted to the hostile operators, potential outcomes could be devastating, from disrupting the level of energy flow from a local grid substation to overloading the nuclear reactor of a power station. Thus, access to the smart grids should only be granted to the local grid operator and the monitoring center, avoiding any interfacing through the AMI access points. Local‐grid operator authentication mechanism could be employed with a two‐factor authentication scheme with a username, password, and RNG. A biometric scheme could be used depending on the availability of biometric extraction devices. As the controlling access is given to the operator, an authorization scheme such as RBAC should be employed, as scalability concern does not exist due to the limited number operators available for a smart grid. An M2M authentication interface is executed between the smart grid and monitoring center for information access. Existing security protocols such as SSLs could be used for authentication.
The access to AMI meter could be given to the residential consumer for the purpose of monitoring statistics. This access could also be based on two‐factor authentication or biometrics as access is only given to read the data and not to manipulate it. Smart Grid has the ability to access the AMI meter through M2M authentication and should be secured with strong crypto primitives for preventing any MiM information extraction. Certificates should be issued to all the smart grids by a CA and identities should be validated preferably via a mutual authentication scheme when establishing a grid‐to‐grid communication channel. A mechanism should be embedded with an authentication protocol to validate the AMI units for detecting possible tampering scenarios.
2.3.3.3.2 Consumer Wearable IoT (WIoT) Devices for Healthcare and Telemedicine
In a telemedicine system, the parties to grant access are solely the patients and their physicians. Thus, access should be limited. Authentication protocols should be always H2M when accessing the information, while M2M authentication operates when updating sensory information from wearable devices to the server. Access to the patient should be granted in a two‐factor authentication scheme if a PC is being used for access. If the patient is using a mobile device to access the server, three‐factor authentication scheme could be employed by integrating biometrics. Though, storing all the credentials including biometric templates at the authentication database would not be scalable with expanded healthcare services. Still, authentication should be thorough because accessing PHRs is private and confidential. Cloud servers' access to physicians could be granted from a two‐factor authentication scheme. Storing and accessing PHRs at the cloud could be secured using the blockchain concept to counter any obvious privacy concerns with CSPs. An IBE scheme could be adopted to enhance the message transferring in the authentication protocol.
2.3.3.3.3 Intelligent Transportation and Logistics
Since the vehicles attribute high mobility, the connectivity of an established wireless link across vehicular entities may vary rapidly. Hence, the availability of a consecutive/fixed inter‐link would be uncertain. Thus, dynamic handover mechanisms should be adopted between vehicular nodes for maintaining a consistent connection with each communicating vehicular node. Hence, those handover‐based connections might require a lightweight approach for authentication as they are highly dynamic.
Each vehicle should have an Identity‐based private key (embedded with its credentials – chassis no., registration no., manufacturer, model, etc.). However, the keys should be generated from an IBE or ABE lightweight mechanism unlike public‐key encryption schemes which require costly resources to generate. Authentication protocols are more likely to be M2M mechanisms, where the machines are the vehicles. Therefore, verifying the identity of each vehicular node engaged in communication is paramount to avoid malicious node invasions through a TTP‐based identity verification. An ECC‐based ephemeral DH scheme could be employed for establishing a shared symmetric session key once the authentication phase is concluded following validation of vehicle identities. All V2V, V2I, V2G, and Vehicle to Cloud (V2C) connections could be implemented in the same manner.
Additional to the approaches discussed earlier, Software Defined Networks (SDN) and Blockchain concepts are highly recommended to ensure the security requirements in the Application layer [1,39].
2.3.3.3.4 Smart Agriculture
As mentioned in the previous section regarding attacks, agriculture IoT devices intrinsically require a lightweight authentication protocol as they are vulnerable to external intervention and sparse resources with perception level nodes. With a lesser resourced platform, implementing a mutual‐authentication scheme would be questionable. In [80], a logic based on the Burrows‐Abadi‐Needham (BAN) modal logic was proposed and tested using Automated Validation Information Security Protocol Application (AVISPA) for verification, which was validated for MiM and replay attacks. However, a frequently changing session key usage is a vital necessity to prevent perception level attacks. This session key establishment could be employed with a technique such as ephemeral DH or ECC for lesser resource utilization.
2.3.3.3.5 IIoT
Most IIoT processes are M2M due to their automated platforms. Further, IIoT process operations are continuous as their work cycles might extend to hours. With the amount of controlling data flowing through the communication channels, simultaneous authentication of each sensory node might lessen the efficiency of the entire smart factory. Thus, a methodology for a scheduled authentication scheme, which does not affect industrial performance, should be established. However, the authentication at each sensory node could be evaded, as there could be hundreds of minor sensors connected to massive machines, which would not be feasible for authentication of each node frequently. Only the control information transfer of machines that is subject to authentication, as a single controlling command, could continuously last for hours. These authentication phases could employ heavy cryptographic primitives as there is no scarcity of computational resources.
2.3.3.3.6 Smart Buildings, Environments, and Cities
Designing a generic authentication protocol for smart cities is not practically feasible. This concept is formed from an entity such as a smart home, inadequate security measures could compromise the privacy of users at any level of use [81]. However, this application could be visualized from the perspective of the three layers in IoT. Similar methods proposed for access control in the perception layer could be adopted for the sensory system in smart environments. The Network layer accompanies all the internet integrated data connections and routing devices along with severs (clouds), in addition to the mobile devices. Mobile devices could use three‐factor authentication schemes incorporated with web‐based SSL or DTLS protocols, while cloud servers and routing nodes could be authenticated with cryptographically generated keys. Authentication protocols in smart cities are likely to change with the requirements and applications, as all other applications mentioned under this section are sub‐applications of a smart city.
2.4 Other Security Features and Related Issues
IoT systems have their own generalized features and requirements regardless of the diversified nature of its applications such as heterogeneity, scalability, Quality of Service (QoS)‐aware, cost minimization due to large‐scale deployment, self‐management including self‐configuration, self‐adaptation, self‐discovery, etc. The last, but not least, general feature/requirement of an IoT system is to provide a secure environment to gain robustness against communication attacks, authentication, authorization, data‐transfer confidentiality, data/device integrity, privacy, and to form a trusted secure environment [43]. IoT systems are fundamentally different from other transitional WSN systems [44] in many ways. (i) The diversity of the types of applications, the capabilities, and attributes of the IoT devices and deployed environments (ii) The holistic design of the system is mostly driven by the applications and it is essential to consider who the users are, what are the purposes and expected outcomes of the applications, etc. An IoT system is required to manage a large variety of devices, technologies, and service environments as the system itself is highly heterogeneous, where the connected IoT devices or equipment can range from simple temperature sensors to high‐resolution smart cameras. The communication, computing, and power capability of each device can be unique and unique from others. These resource and interoperability constraints limit the feasibility for a standard security solution.
2.4.1 The Simplified Layer Structure
The traditional Open Systems Interconnection (OSI) has Seven layers: (i) The Physical Layer (Layer 1) is responsible for the transmission and reception of wire level data. (ii) The Data Link Layer (Layer 2) is responsible for link establishment and termination, frame traffic control, sequencing, acknowledgment, error checking, and media access management. (iii) The Network Layer (Layer 3) is implemented for routing of network traffic. (iv) The Transport Layer (Layer 4) is responsible for message segmentation, acknowledgement, traffic control, and session multiplexing. (v) The Session Layer (Layer 5) is responsible for session establishment, maintenance, and termination. (vi) The Presentation Layer (Layer 6) is responsible for character code translation, data conversion, compression, and encryption. (vii) The Application Layer (Layer 7) includes resource sharing, remote file access, remote printer access, network management, and electronic messaging (email). Since IoT systems normally have a huge variety, ranging from the choice of the hardware to the type of applications, the traditional seven network layers are simplified to three layers: perception layer, networking layer and application layer, as shown in Figure 2.1. The perception layer can be seen as the combination of the traditional physical layer and the MAC layer. It can include 2D bar code labels and readers, RFID tags and reader‐writers, camera, GPS, sensors, terminals, and sensor network. It is the foundation for the IoT system [45]. The networking layer is responsible for the data transmission and communication inside the system and with the external Internet. It should be aware of the different underlying networks no matter whether it is wired, wireless, or cellular. It can provide support for different communication modes including base station, access point based or Machine‐to Machine type based. The application layer provides services to the end users and collects data from different scenarios. IoT has high potential to implement smart and intelligent application for any scenario in nearly every field. This is mainly because IoT can offer both (i) data collection through sensing over natural phenomena, medical parameters, or user habits and (ii) data analysis and predictive modeling for tailored services. Such applications will cover aspects including personal, social, societal, medical, environmental, and logistics, having a profound impact on both the economy and society [43]. The perception and network layer together are considered the foundation for the whole IoT system. Together, these two layers provide the backbone and fundamental infrastructure of an IoT system. However, the architecture design and detailed implementation can normally only be confirmed after knowing the application layer design. Where the system will be deployed, what size the field will be and what kind of data will be collected are all issues involved in the applications, but highly affect the decision making on the perception layer and network layer.
2.4.2 The Idea of Middleware
Researchers from academia and industry are exploring solutions to enhance the development of IoT from three main perspectives: scientific theory, engineering design, and user experience [46]. These activities can enrich the technologies for IoT, but also increase the complexities, when implementing such a system in the real world. For this reason, the concept of IoT middleware has been introduced and many systems are already available [47–51]. However, when describing the formal definition for IoT middleware, researchers have different understandings. In some circumstance, IoT middleware is equivalent to IoT Operating System (OS). In general, middleware can simplify and accelerate a development process by integrating heterogeneous computing and communication devices, as well as supporting interoperability within the diverse applications and services [52]. Most existing implementations for middleware are designed for WSN and not for a service‐oriented IoT system. Though, certain IoT‐Specific middleware exists [53,54]. In reality, middleware is often used to bridge the design gap between the application layer and the lower infrastructure layers. The requirements for middleware service for the IoT can be categorized into functional and non‐functional groups. Functional requirements capture the services or functions such as abstractions and resource management [55]. Non‐functional requirements capture QoS support or performance issues such as energy efficiency and security [56].
The Internet of Everything (IoE) aims to connect the objects, buildings, roads and cities and also to make the platform accessible. However, this feature will significantly increase the vulnerabilities of the system and, the inherent complexity of the IoT further complicates the design and deployment of efficient, interoperable, and scalable security mechanisms. It has been clearly stated that all typical security issues (authentication, privacy, nonrepudiation, availability, confidentiality, integrity) exist across all layers and the entire function box to a certain degree. However, when implementing security solutions, different layers of a variety of systems will have specialized priorities [78].
An essential task of the middleware is to provide secure data transmission between the upper and lower layers. For inner system communication, it should guarantee that the data passed to the application layer from the infrastructure is safe and reliable to use – integrity. Integrity in this scenario involves maintaining the consistency, accuracy, and trustworthiness of data over the transmission. Conversely, the middleware should also ensure that the control comments and queries from the applications/end users are verified and it is harmless for the system to take actions – non‐repudiation. Non‐repudiation features ensure that users cannot deny the authenticity of their signature for their documents and footprints for their activities. In addition, the middleware must protect the data transmission and information exchange between the upper and lower layers from illegal external access by any arbitrary user. The data must not be disclosed to any unauthorized entities – confidentiality.
2.4.3 Cross‐Layer Security Problem
It has been frequently argued that although layered architectures have been a great success for wired networks, they are not always the best choice for wireless networks. To address this problem, a concept of cross‐layer design is proposed and it is becoming popular. This concept is based on an architecture where different layers can exchange information in order to improve the overall network performance. A substantial amount of work has been carried out on state‐of‐the‐art cross‐layer protocols in the literature recently [57]. Security can be considered as one of the most critical QoS features in IoT systems. Wireless broadcast communication is suffering security risks more than others while multi‐hop wireless communication is in a worse situation, as there is no centralized trusted authority to distribute a public key in a multi‐hop network because of the nature of its distribution. Current proposed security approaches may be effective in a particular security issue in a specific layer. However, there still exists a strong need for a comprehensive mechanism to prevent security problems in all layers [58]. Security issues like availability need to be addressed not only at each layer, but a good cross‐layer design and communication is encouraged. IoT systems are generally large and complex systems with many interconnections and dependencies, such as in smart cities [59].
If the availability of any of the three layers (perception, network, and application) fails, the availability of the whole system collapses. The lower layer infrastructure must protect itself from malicious behavioral patterns and harmful control from unauthorized users. The application layer should be available for all authorized users continuously without any service overloading‐type interruption from unauthorized users.
2.4.4 Privacy
As the new European General Data Protection Regulation (GDPR)2 has become enforceable on the 25 May 2018, protecting user data and securing user privacy are urgent and predominant issues to be solved for any IoT application. Users' data can neither be captured nor used without their awareness. Privacy has the highest priority for all existing and future application development, including IoT systems [100]. User identities must not be identifiable nor traceable. Under the new legislation, data processing must involve:
- Lawful, fair, and transparent processing – emphasizing transparency for data subjects.
- Purpose limitation – having a lawful and legitimate purpose for processing the information in the first place.
- Data minimization – making sure data is adequate, relevant and limited, and organizations are sufficiently capturing the minimum amount of data needed to fulfill the specified purpose.
- Accurate and up‐to‐date processing – requiring data controllers to make sure information remains accurate, valid, and fit for purpose.
- Limitation of storage in a form that permits identification – discouraging unnecessary data redundancy and replication.
- Confidential and secure – protecting the integrity and privacy of data by making sure it is secure (which extends to IT systems, paper records and physical security)
- Accountability and liability – the demonstrating compliance. As a well‐known statement in security, there are security issues at all perception, network, and application layers.
Some other security problems can be addressed effectively and efficiently on a certain layer level, such as implementing privacy components on the application layer. In a healthcare system, patients should be totally aware who is collecting and using their data. They also should have control over the data and who they want to share it with, as well as how and where their data is being used. The applications should provide services and interface to allow users to manage their data. Users must have tools that allow them to retain their anonymity in this super‐connected world. The same scenario can be applied to systems such as smart home, smart transportation, etc. IoT applications may collect users' personal information and data from their daily activities. Many people would consider that data or information predicted from the data as private. Exposure of this information could have an unwanted or negative impact on their life. The use of the IoT system should not cause problems of privacy leaking. Any IoT applications which do not meet with these privacy requirements could be prohibited by law. The IoT system must seriously consider the implementation of privacy by the 7 data protection principles, providing user‐centric support for security and privacy from its very own foundations [60].
2.4.5 Risk Mitigation
Mitigating the risk of an intrusion attempt or attack against an IoT device is not an easy thing to do. Having a higher degree of security protection at every level will discourage the attacker to pursue his/her goals further, by causing a higher amount of effort and time needed versus the benefits. Mitigation needs to start with prevention, by involving every actor in the market, from manufacturers to consumers and lawmakers, and to make them understand the impact of the IoT security threats in a connected world. Another way to mitigate risk is to keep abreast of the times by improving and innovating, from the ground up, and by finding new methods and designs to outgrow the shortcomings of the market.
2.5 Discussion
Authentication for IoT is a paramount necessity for securing and ensuring the privacy of users, simply due to the fact that an impregnable access control scheme would be impervious for any attack vector originating outside of the considered trust domain, as explained in the previous sections of this chapter. Authentication schemes in IoT applications are generally implemented at the software level, where it exposes unintentional hardware and design vulnerabilities [82]. This fact constitutes the requirement of a holistic approach for securing access to the systems via the employment of impregnable authentication schemes. However, developing a generic authentication scheme to counter all possible attack scenarios would be improbable and an arduous attempt due to the heterogeneity of the IoT paradigm. A layered approach that identifies the distinct authentication requirement is desired to formalize a holistic trust domain.
For perception level entities, IBE or ECC would be ideal authentication schemes to generate commendable cryptographic credentials with available resources. The mobile entities, where actual users are interfacing to IoT systems are storing personalized credentials such as photos, medical stats, access to CCTV systems, GPS location (GPS), daily routines, financial statistics, banking credentials, emergency service status and online account statistics, are emphasizing the need for privacy preservation at this level. As proposed in Section 2.3.3.1.1, adopting IBE, ABE, ECC, or biometric‐based mechanisms should ensure security. Novel mechanisms such as CapBAC could be employed to launch a scalable access control scheme for cloud computing platforms for IoT applications. However, the potential for deploying edge computing paradigms in the edge of the network indemnifies the cloud computing services from external direct access, as the access control would be migrated to the edge along with the service platform. The internet technologies of IoT‐enabled systems are more secured than the perception level and mobile level entities with the deployed protocols such as DTLS, SSL, and IPSec. Due to the dependency of a CA or TTP for employing such strong and secure protocols, the future of Internet security enhancements would be focused on developing distributed access control schemes to eliminate the single point of failure. Each IoT application composes different devices and systems to accomplish the intended outcome which attributes diverse protocols in hardware and software. Thus, the authentication schemes should be application specific and context aware of resource constraints associated with the diversified deployments. As privacy is the main concern on IoT to be ensured through impregnable access control schemes, the GDPR initiative is a timely solution established to constrict the IoT service providers (both software and hardware) from developing and marketing products with vulnerabilities.
Current researches have focused on developing novel methods for authentication in the IoT domain. We are briefly introducing a few of these recent approaches to demonstrate the state‐of‐the‐art technologies.
In [86], Ning et al. has proposed an aggregated proof‐based hierarchical authentication (APHA) scheme to be deployed on existing Unit IoT and Ubiquitous IoT (U2IoT) architecture. Their scheme employs two cryptographic primitives; homomorphic functions and Chebyshev polynomials. The proposed scheme has been verified formally using Burrows‐Abadi‐Needham (BAN) logic. However, the scalability of the scheme with the extent of multiple units has not been verified with a physical prototype.
There are various initiatives on Physical Unclonable Functions (PUF) to be used for IoT device authentication. A PUF is an expression of an inherent and unclonable instance‐specific unique feature of a physical object which serves as a biometric for non‐human entities, such as IoT devices [89]. Hao et al. are proposing a Physical Layer (PHY) End‐to‐End (E2E) authentication scheme which generates an IBE‐based PHY‐ID which acts as a PUF with unclonable PHY features RF Carrier Frequency Offset (CFO) and In‐phase/Quadrature‐phase Imbalance (IQI) extracted from collaborative nodes in a Device to Device (D2D) IoT deployment [87]. This mechanism is ideal for perception‐level nodes to be impervious to impersonation or malicious node injection attacks, as it is using physical measurements which are unique for each entity and for its location of operation in generating an identity for devices. However, the proposed scheme relies on a TTP called Key Generation Center (KGC). KGC generates the asymmetric key credentials for the nodes in its contact. The reachability of a certain KGC is limited due to the low power D2D connectivity. Thus, multiple KGCs deployed to accomplish the coverage should be managed with a centralized control entity. This enables the attack vectors on decentralized KGC entities. Moreover, the reliance on CFO and IQI features require the nodes to be stationary. This would be an issue considering most IoT devices are mobile and their RF‐based characteristics vary in a timely manner. Aman et al. proposed a PUF‐based authentication protocol for scenarios when an IoT device is connecting with a server and a D2D connectivity focused on its applicability in vehicular networks. Authentication is based on a Challenge Response Pair (CRP), where the outcome of the CRP is correlated with the physical microscopic structure of the IoT device, which emphasizes its unique PUF attributes with the inherent variability of the fabrication process in Integrated Circuits (ICs). The proposed protocol was analyzed using Mao and Boyd logic, while Finite State Machine (FSM) and reachability analysis techniques have been adopted for formal verification. Even though the performance of the protocol has been analyzed in terms of computational complexity, communication overhead and storage requirement, its scalability with simultaneous multiple IoT device connections to the server have not been addressed. However, this approach would be a feasible solution for V2E applications as the PUF could be successfully integrated with vehicles.
A human‐gait pattern based on the biometric extraction scheme WifiU has been proposed in [88] as a case study that uses Channel State Information (CSI) of the received Wi‐Fi signals for determining the gait pattern of the person carrying the transmitter. The gait patterns are becoming a novel biometric mode and this solution is a cost‐effective approach which does not employ any floor sensors or human wearables. However, the applicability of WifiU for IoT devices raises concerns over scalability, accuracy of the gait‐pattern extraction from CSI, reliability of CSI measurement and Wi‐Fi interference. Chauhan et al. in [90] proposes a Recurrent Neural Network (RNN) based on human breath print authentication system for mobile, wearable, and IoT platforms employing a derived breath print as a biometric through acoustic analysis. Even though this approach depicts a viable biometric solution for human interfacing IoT applications, the breath print extraction would be dependent on the health, climatic circumstances and physical stability of the user.
If the proposed authentication schemes are not fully holistically applicable for IoT deployments, optimum solutions at different layers and specific applications could be aggregated to form an impregnable access control system, where the interconnectivity across them should be maintained by decentralized trust domain managers. However, the access control mechanism optimum for each application should be investigated for each case in order to ensure robustness.
2.6 Future Research Directions
This section proposes several new research approaches and directions that could have a high impact for the future of the IoT security.
2.6.1 Blockchain
The blockchain is a distributed database of online records. Typically used in financial transactions for the Bitcoin cryptocurrency, the peer‐to‐peer blockchain technology records transactions without exception, in exchange, to form an online ledger system. Blockchain technologies are immutable, transparent, trustworthy, fast, decentralized, and autonomic, providing solutions that can be public, consortium, or private. Due to the success of Bitcoin, people are now starting to apply blockchain technologies in many other fields, such as financial markets, supply chain, voting, medical treatment and security for IoT [61,99]. There are expectations that blockchain will revolutionize industry and commerce and drive economic change on a global scale [62].
Blockchain technology leads to the creation of secure mesh networks, where IoT devices will interconnect while avoiding threats such as impersonation or device spoofing. As more legitimate nodes register on the blockchain network, devices will identify and authenticate each other without a need for central brokers and certification authorities. The network will scale to support more and more devices without the need for additional resources [63].
Smart contracts open the way to defining a new concept, a decentralized autonomous organization (DAO), sometimes labeled as a Decentralized Autonomous Corporation, an organization that runs through rules maintained on a blockchain. The legal status of this new brand of business organization is rather seen as a general partnership, meaning that its participants could bear unlimited legal liability. Ethereum blockchain, for example, is a public blockchain network optimized for smart contracts that use its cryptocurrency, called Ether (ETH). There is a huge interest in Ethereum, as a blockchain technology for the future. In 2017, Enterprise Ethereum Alliance was formed and already counts close to 250 members, like Samsung, Microsoft, J.P.Morgan, Toyota, ING, Consensys, BP, Accenture and many others. Etherum has become the second highest traded cryptocurrency in 2017, after Bitcoin, with a volume of transactions for over half of million euros in a single 24‐hour period.
As with each disruptive concept that turns into an effective offering, the blockchain model is not perfect and has its flaws and shortcomings. Scalability is one of the main issues, considering the tendency toward centralization with a growing blockchain. As the blockchain grows, the nodes in the network require more storage, bandwidth, and computational power to be able to process a block, which currently leads to only a handful of the nodes being able to process a block. Computing power and processing time is another challenge, as the IoT ecosystem is very diverse and not every device will be able to compute the same encryption algorithms at the desired speed. Storage of a continuously increasing ledger database across a broad range of smart devices with small storage capabilities, such as sensors, is yet another hurdle. The lack of skilled people to understand and develop the IoT‐blockchain technologies together is also a challenge. The lack of laws and a compliance code to follow by manufacturers and service providers is not helping both the IoT and blockchain to take off as expected.
IOTA solves some problems that the blockchain does not. One of them is centralization of control. As history shows, small miners create big groups to reduce the variation of the reward. This activity leads to concentration of power, computational, and political, in possession of just a handful of pool operators and gives them the ability to apply a broad spectrum of policies, like filtering on or postponing certain transactions.
2.6.2 5G
For the first time in history, LTE has brought the entire mobile industry to a single technology footprint resulting in unprecedented economies of scale. The converged footprint of LTE has made it an attractive technology baseline for several segments that had traditionally operated outside the commercial cellular domain. There is a growing demand for a more versatile M2M platform. The challenge for industrial deployment of IoT is the lack of convergence across the M2M architecture design that has not materialized yet. It is expected that LTE will remain as the baseline technology for wide‐area broadband coverage also in the 5G area. The realization of 5G network is affecting many IoT protocols' initial design, especially at perception and network layers [64,102]. Mobile operators now aim to create a blend of pre‐existing technologies covering 2G, 3G, 4G, WiFi, and others to allow higher coverage and availability, as well as higher network density in terms of cells and devices with the key differentiator being greater connectivity as an enabler for M2M services [65]. 3GPP standard/5G‐based backhaul has become a popular solution for connectivity problems in IoT systems. Munoz et al. indicates that the next generation of mobile networks (5G), will need not only to develop new radio interfaces or waveforms to cope with the expected traffic growth but also to integrate heterogeneous networks from End‐to‐End (E2E) with distributed cloud resources to deliver E2E IoT and mobile services [66]. Fantacci et al. has provided a backhaul solution through mobile networks for smart building applications [67]. The proposed network architecture will improve services for users and will also offer new opportunities for both service providers and network operators. As 5G has become available and is being adopted as the main backhaul infrastructure for IoT system, it will play a huge role in IoT perception and networking layers [68]. 5G has moved the focus to a user‐centric service from a network‐centric service unlike 4G and 3G. With massive multiple‐input and multiple‐output (MIMO) technologies deployed in 5G, network selection and rapid handovers are becoming essential in terms of supporting QoS and Quality‐of‐user Experience (QoE) aware services [69]. The handover between different network interfaces should be authenticated and the information exchange during the handover should be protected and private. Currently, SDN is considered as the mainstream for a higher efficiency through its centralized control capability in the 5G communication process [70]. With SDN, the control logic is removed from the underlying infrastructures to a management platform. Software and policies can be implemented on the central SDN controller to provide consistent and efficient management over the whole 5G network. One advanced and beneficial feature offered by SDN is that it can separate the control plane and data source by abstract, the control logic from the underlying switches and routers to the centralized SDN controller [71]. To address the Machine Type Communication (MTC) in IoT systems based on 5G network, several approaches are available [72,73]:
- A higher level of security for devices is achievable by utilizing new security mechanisms being embedded with Subscriber Identity Module (SIM).
- It is recommended to implement and employ physical‐layer security adopting RF fingerprinting.
- Using asymmetric security schemes to transfer the burden of required computations to the network domain or gateways with high computing capabilities.
2.6.3 Fog and Edge Computing
Although powerful, the cloud model is not the best choice for environments where internet connectivity is limited or operations are time‐critical. In scenarios such as patient care, milliseconds have fatal consequences. As in the vehicle‐to‐vehicle communications, the prevention of collisions and accidents relies on the low latency of the responses. Cloud computing is not consistently viable for many IoT applications, and so, it is replaced by fog computing. Fog computing, also known as fogging, is a decentralized computing infrastructure in which the data, compute, storage, and applications split in an efficient way between the data source and the cloud.
Fog computing extends cloud computing and services alike, to the edge of the network, by bringing the advantages and the power of the cloud to where the data initially arise. The main goal of fogging is to improve efficiency and also to reduce the quantity of data that moves to the cloud for processing, analysis, and storage. In fogging, data processing takes place in a router, gateway, or data hub on a smart device, which sends it further to sources for processing and return transmission, therefore reducing the bandwidth payload to the cloud.
The back‐and‐forth communication between IoT devices and the cloud can negatively affect the overall performance and security of the IoT asset. The distributed approach of fogging addresses the problem of the high amount of data coming from smart sensors and IoT devices, which would be costly and time‐consuming to send to the cloud each time. Among other benefits, fog computing offers better security by protecting the fog nodes with the same policy, controls, and procedures used in other parts of the IT environment and by using the same physical safety and cyber security solutions [74]. Fog networking complements cloud computing and allows for short‐term analytics at the edge while the cloud performs resource‐intensive, longer‐term analytics. Computation moves even closer to the edge and becomes deeply‐rooted in the very same devices that created the data initially, and so, generates even greater possibilities for M2M intelligence and interactions.
The movement of computation from the fog to the actual device opens the path‐to‐edge computing. That is a distributed architecture in which the processing of client data takes place at the outer edge of the network, in the proximity of the originating source. Mobile computing, low cost of computer components and the absolute quantity of IoT devices drive the move toward edge computing. Time‐sensitive data is processed at the point of origin by an intelligent and resource‐capable device or sent to a broker server located in close geographical proximity to the client. Less time‐sensitive data travels to the cloud for historical analysis, big data analytics, and long‐term storage. One of the greatest benefits of edge computing is that it removes network bottlenecks by improving time to action and response time down to milliseconds, while also conserving network resources.
The edge computing concept is not without its flaws though. Edge computing raises a high amount of security, licensing and configuration challenges and concerns. The vulnerability to some attack vectors like malware infections and security exploits increases because of the nature of the distributed architecture. Smart clients can have hidden licensing costs, where the base version of an edge client might initially have a low price, additional functionalities could be licensed separately and will drive the price up. Also, decentralized and poor device management leads to configuration drift by the administrators. They can inadvertently create security holes by not consistently updating the firmware or by failing to change the default password on each edge device [75].
2.6.4 Quantum Security, AI, and Predictive Data Analytics
With the technological advancements of quantum computing, Artificial Intelligence (AI), and cognitive systems, and with the continuous development and mass adoption of IoT ecosystem, the current security practices and methodologies will become a part of the past. Quantum computing, not only can it break through any form of security that is known to humankind, but it can also offer the solution to finding the formula for tight security. IoT will vastly benefit from these technology advancements, especially from the quantum mechanics science on a microchip. Further research is recommended, once the technology matures and evolves, to discover how the security of the future impacts on things around and especially on the IoT ecosystem.
2.6.5 Network Slicing
Network slicing is the concept of slicing a physical network into several logical planes to facilitate the various IoT services to customize their differentiated on‐demand services with the same physical network [91]. The main aim of this paradigm is to reinforce different service requirements such as latency, bandwidth, and reliability of heterogeneous IoT applications to utilize the resources such as storage, computing, and bandwidth of the IoT device platforms [92]. The complexity of the IoT service integration with core network resources could be alleviated using a standardized network slicing mechanism as proposed by the Next Generation Mobile Network (NGMN). A typical network slicing process could be described under three layers, namely service instance layer, network slice instance layer and resource layer which follow the principles automation, isolation, customization, elasticity, programmability, end‐to‐end, and hierarchical abstraction [94].
The evolvement of the network slicing concept has reached the depths of 5G Information Centric Networking (ICN) model, which consists of five functional planes (FPs), namely; FP1 – service business plane, FP2 – service orchestration and management plane, FP3 – IP/ICN orchestrator plane, FP4 – domain service orchestration and management plane and FP5 – infrastructure plane. FP1 interfaces with external 5G users in providing various service Application Programme Interfaces (APIs) which realize the objective and relevant services to accomplish that objective with inputs such as service type, demand patterns, Service Level Agreements (SLAs)/QoS/QoE requirements. The service requests forwarded by FP1 are communicated to the FP3 as service requirements by FP2. The FP3 interfaces with a domain controller to virtualize compute, storage, and network resources to meet the service requirements conveyed from FP2. FP4 supports the management of IP and ICN services belonging to different technological domains such as 4G/5G Radio Access Network (RAN), Multi‐Protocol Label Switching (MPLS) and edge technologies, while FP5 enables the service rules in end‐to‐end manner.
The entities operating in network slicing infrastructure, such as network slice manager and host platforms are attributing the vulnerabilities exploitable by impersonation attacks, DoS, SCA attacks and the interoperability of different security protocols and policies [93]. An IoT user may access different slices depending on both the requirements and the intended outcomes. Thus, the access granting control for different slices is a critical juncture in the perspective of security. The plausibility for isolating the slices for constricting the deliberate hacking attempts at resources operating at each plane should be focused. Due to the facts that a network slice is a composite of the actual physical infrastructure and the processes should be dynamic, adaptive, and flexible for servicing the intended functions, the assurance of user confidentiality, privacy, integrity, and availability are challenging. However, authentication is the most effective mechanism to be used for enhancing the robustness of the network slices toward attacks. Among the 5G Security –as‐a‐Service (SaaS) concepts, micro‐segmentation, deception of the attacker and AI deployments for monitoring, attack detection and remediation are emerging initiatives for securing network slices [95].
2.7 Conclusions
IoT technology is the most discussed paradigm in the research community these days. Its potential to connect all the devices in the world and to create a large information system that would offer services to improve the quality of human beings exponentially has made the concept much more popular. The integration of various technologies and devices with different architectures are creating interoperability issues with the components in the IoT architecture. These issues and the highly diversified type of services are creating security concerns which disperse into all three layers of IoT architecture: Perception, Network, and Application. Hence, the security measures to be taken should be developed while analyzing the threats and vulnerabilities at each layer.
Mitigating risks associated with security breaches are possible, if security receives consideration from early product planning and design, and if some basic prevention mechanisms are in place. Enactment and standardization will simplify the manufacturing and development processes, give the market an incentive for mass‐adoption and also increase the security posture of IoT products and services. Security will have to be inbuilt so that IoT can withstand a chance against the threats that technological advancements will bring.
References
- 1 Alaba, F., Othman, M., Hashem, I., and Alotaibi, F. (2017). Internet of things security: a survey. Journal of Network and Computer Applications 88: 10–28.
- 2 Kim, H. and Lee, E.A. (2017). Authentication and authorization for the internet of things. IT Professional 19 (5): 27–33.
- 3 Jurcut, A., Coffey, T., Dojen, R., and Gyorodi, R. (2008). Analysis of a key‐establishment security protocol. Journal of Computer Science and Control Systems 2008: 42–47.
- 4 Jurcut, A.D., Coffey, T., and Dojen, R. On the prevention and detection of replay attacks using a logic‐based verification tool. In: Computer Networks, vol. 431 (eds. A. Kwiecień, P. Gaj and P. Stera), 128–137. Switzerland: Springer International Publishing.
- 5 Jurcut, A.D., Liyanage, M., Chen, J. et al. (2018). On the security verification of a short message service protocol. Presented at the. In: 2018 IEEE Wireless Communications and Networking Conference (WCNC). Barcelona, Spain: (April, 2018).
- 6 Deogirikar, J. and Vidhate, A. (2017). Security attacks in IoT: a survey. In: 2017 International Conference on I‐SMAC (IoT in Social, Mobile, Analytics and Cloud). Coimbatore, India: (February 2017).
- 7 Pasca, V., Jurcut, A., Dojen, R., and Coffey, T. (2008). Determining a parallel session attack on a key distribution protocol using a model checker. In: ACM Proceedings of the 6th International Conference on Advances in Mobile Computing and Multimedia (MoMM '08) Linz, Austria (24–26 November). New York, USA: ACM.
- 8 Jurcut, A.D., Coffey, T., and Dojen, R. (2017). A novel security protocol attack detection logic with unique fault discovery capability for freshness attacks and interleaving session attacks. IEEE Transactions on Dependable and Secure Computing https://doi.org/10.1109/TDSC.2017.2725831.
- 9 Liyanage, M., Braeken, A., Jurcut, A.D. et al. (2017). Secure communication channel architecture for software defined Mobile networks. Journal of Computer Networks 114: 32–50.
- 10 Jurcut, A., Coffey, T., and Dojen, R. (2014). Design requirements to counter parallel session attacks in security protocols. Presented at the. In: 12th IEEE Annual Conference on Privacy, Security and Trust (PST'14). in Toronto Canada (July 2014).
- 11 Jurcut, A.D., Coffey, T., and Dojen, R. (2014). Design guidelines for security protocols to prevent replay & parallel session attacks. Journal of Computers & Security 45: 255–273.
- 12 Jurcut, A.D., Coffey, T., and Dojen, R. (2012). Symmetry in security protocol cryptographic messages – a serious weakness exploitable by parallel session attacks. Presented at the . In: 7th IEEE International Conference on Availability, Reliability and Security (ARES'12). Prague, Czech Republic: (August 2012).
- 13 Jing, Q., Vasilakos, A.V., Wan, J. et al. (2014). Security of the internet of things: perspectives and challenges. Wireless Networks 20 (8): 2481–2501.
- 14 Zhao, K. and Ge, L. (2013). A survey on the internet of things security. Presented at the. In: 2013 9th International Conference on Computational Intelligence and Security (CIS). in Leshan, China (December 2013).
- 15 Weis, S.A., Sarma, S.E., Rivest, R.L., and Engels, D.W. (2004). Security and privacy aspects of low‐cost radio frequency identification systems. In: Security in Pervasive Computing (eds. D. Hutter, G. Muller, W. Stephan and M. Ullmann), 201–212. Springer.
- 16 Kumar, T., Liyanage, M., Ahmad, I. et al. (2018). User privacy, identity and trust in 5G. In: A Comprehensive Guide to 5G Security (eds. M. Liyanage, I. Ahmad, A.B. Abro, et al.), 267. Wiley.
- 17 Kavun, E.B. and Yalcin, T. (2010). A lightweight implementation of keccak hash function for radio‐frequency identification applications. In: International Workshop on Radio Frequency Identification: Security and Privacy Issues. New York, USA (23–24 June 2015): Springer.
- 18 Zhang, Y., Shen, Y., Wang, H. et al. (2015). On secure wireless communications for IoT under eavesdropper collusion. IEEE Transactions on Automation Science and Engineering 13 (3): 1281–1293.
- 19 Massis, B. (2016). The internet of things and its impact on the library. New Library World 117 (3/4): 289–292.
- 20 Liu, Y., Cheng, C., Gu, T. et al. (2016). A lightweight authenticated communications scheme for a smart grid. IEEE Transactions on Smart Grid 7 (3): 1304–1313.
- 21 Kumar, T., Porambage, P., and Ahmad, I. (2018). Securing gadget‐free digital services. Computer 51 (11): 66–77.
- 22 Horrow, S. and Anjali, S. (2012). Identity management framework for cloud based internet of things. In: Proceedings of the First International Conference on Security of Internet of Things, SecurIT' 12. Kollam, India (17–19 August 2012): ACM.
- 23 Lin, X., Sun, X., Wang, X. et al. (2008). TSVC: timed efficient and secure vehicular communications with privacy preserving. IEEE Transactions on Wireless Communications 7 (12): 4987–4998.
- 24 Lin, X. and Li, X. (2013). Achieving efficient cooperative message authentication in vehicular ad hoc networks. IEEE Transactions on Vehicular Technology 62 (7): 3339–3348.
- 25 Zhou, J., Dong, X., Cao, Z. et al. (2015). 4S: a secure and privacy‐preserving key management scheme for cloud‐assisted wireless body area network in m‐healthcare social networks. Information Sciences 314: 255–276.
- 26 Sen, J. (2011). Privacy preservation Technologies in Internet of things. In: Proceedings of International Conference on Emerging Trends in Mathematics, Technology, and Management, (18–20 November 2011).
- 27 Zhou, J., Dong, X., Cao, Z. et al. (2015). Secure and privacy preserving protocol for cloud‐based vehicular DTNs. IEEE Transactions on Information Forensics and Security 10 (6): 1299–1314.
- 28 Roman, R., Alcaraz, C., Lopez, and Sklavos, N. (2011). Key management systems for sensor networks in the context of the internet of things. Computers and Electrical Engineering 37 (2): 147–159.
- 29 Zhou, J., Cao, Z., Dong, X. et al. (2015). TR‐MABE: White‐Box Traceable and Revocable Multi‐Authority Attribute‐Based Encryption and Its Applications to Multi‐Level Privacy‐Preserving e‐Heathcare Cloud Computing Systems. IEEE INFOCOM.
- 30 Lu, R., Lin, X., Zhu, H. et al. (2010). Pi: a practical incentive protocol for delay tolerant networks. IEEE Transactions on Wireless Communications 9 (4): 1483–1492.
- 31 Paillier, P. (1999). Public key cryptosystems based on composite degree residuosity classes. In: Eurocrypt '99 Proceedings of the 17th international conference on Theory and application of cryptographic techniques. Prague, Czech Republic (2–6 May 1999): ACM.
- 32 Groth, J. and Sahiai, A. (2008). Efficient noninteractive proof systems for bilinear groups. In: Advances in Cryptology®EUROCRYPT. Istanbul, Turkey (13–17 April 2008): Springer.
- 33 Akhunzada, A., Gani, A., Anuar, N.B. et al. (2016). Secure and dependable software defined networks. Journal of Network and Computer Applications 61: 199–221.
- 34 Miorandi, D., Sicari, S., De Pellegrini, F., and Chlamtac, C. (2012). Internet of things: vision, applications and research challenges. Ad Hoc Networks 10 (7): 1497–1516.
- 35 Porambage, P., Okwuibe, J., Liyanage, M. et al. (2018). Survey on multi‐access edge computing for internet of things realization. IEEE Communication Surveys and Tutorials 20 (4): 2961–2991.
- 36 Garcia‐Morchon, O., Hummen, R., Kumar, S. et al. (2012) Security considerations in the ip‐based internet of things, draft‐garciacore‐security‐04.
- 37 Singh, J., Pasquier, T., Bacon, J. et al. (2015) Twenty security considerations for cloud‐supported internet of things.
- 38 Bekara, C. (2014). Security issues and challenges for the IoT‐based smart grid. Procedia Computer Science 34: 532–537.
- 39 Kouicem, D., Bouabdallah, A., and Lakhlef, H. (2018). Internet of things security: a top‐down survey. Journal of Computer Networks 141: 199–121.
- 40 Desai, D. and Upadhyay, H. (2014). Security and privacy consideration for internet of things in smart home environments. International Journal of Engineering Research and Development 10 (11): 73–83.
- 41 Kumar, J.S. and Patel, D.R. (2014). A survey on internet of things: security and privacy issues. International Journal of Computer Applications 90 (11).
- 42 Stamp, M. (2011). Information Security, 2e. Hoboken, N.J: Wiley.
- 43 Borgia, E. (2014). The internet of things vision: key features, applications and open issues. Computer Communications 54: 1–31.
- 44 Xu, L., Collier, R., and O'Hare, G.M.P. (2017). A survey of clustering techniques in wsns and consideration of the challenges of applying such to 5g iot scenarios. IEEE Internet of Things Journal 4: 1229–1249.
- 45 Wu, M., Lu, T.‐J., Ling, F.‐Y. et al. (2010). Research on the architecture of internet of things. In: 2010 3rd International Conference on Advanced Computer Theory and Engineering (ICACTE). Chengdu, China: (20–22 August 2010).
- 46 Feki, M.A., Kawsar, F., Boussard, M., and Trappeniers, L. (2013). The internet of things: the next technological revolution. Computer 46: 24–25.
- 47 Contiki. http://www.contiki-os.org (accessed 16 July 2019).
- 48 Brillo. https://developers.google.com/brillo (accessed 16 July 2019).
- 49 Tinyos. http://www.tinyos.net (accessed 16 July 2019).
- 50 Openwsn. http://openwsn.atlassian.net (accessed 16 July 2019).
- 51 Riot. http://www.riot-os.org (accessed 16 July 2019).
- 52 Porambage, P., Manzoor, A., Liyanage, M. et al. (2019). Managing Mobile Relays for Secure E2E Connectivity of Low‐Power IoT Devices. IEEE Consumer Communications & Networking Conference, Las Vegas, USA (11–14 January 2010). IEEE.
- 53 Perera, C., Jayaraman, P.P., Zaslavsky, A. et al. (2014). Mosden: an internet of things middleware for resource constrained mobile devices. In: 47th Hawaii International Conference on System Sciences. Hawaii, USA (6–9 January 2014): IEEE.
- 54 Zhou, H. (2012). The Internet of Things in the Cloud: A Middleware Perspective, 1e. Boca Raton, FL, USA: CRC Press, Inc.
- 55 Xu, L., Lillis, D., O'Hare, G.M., and Collier, R.W. (2014). A user configurable metric for clustering in wireless sensor networks. In: SENSORNETS. Lisbon, Portugal (7–9 January 2014): SciTePress.
- 56 Ngu, A.H., Gutierrez, M., Metsis, V. et al. (2017). Iot middleware: a survey on issues and enabling technologies. IEEE Internet of Things Journal 4: 1–20.
- 57 Srivastava, V. and Motani, M. (2005). Cross‐layer design: a survey and the road ahead. IEEE Communications Magazine 43: 112–119.
- 58 Zhang, Q. and Zhang, Y.Q. (2008). Cross‐layer design for qos support in multihop wireless networks. Proceedings of the IEEE 96: 64–76.
- 59 Zanella, A., Bui, N., Castellani, A. et al. (2014). Internet of things for smart cities. IEEE Internet of Things Journal 1: 22–32.
- 60 Roman, R., Zhou, J., and Lopez, J. (2013). On the features and challenges of security and privacy in distributed internet of things. Computer Networks 57 (10): 2266–2279.
- 61 Lin, I., I.C. and Liao, T.C. (2017). A survey of blockchain security issues and challenges. International Journal of Network Security 19: 653–659.
- 62 Underwood, S. (2016). Blockchain beyond bitcoin. Communications of the ACM 59: 15–17.
- 63 How blockchain can change the future of IoT (2016). https://venturebeat.com/2016/11/20/how-blockchain-can-change-the-future-of-iot (accessed 16 July 2019).
- 64 Chiang, M. and Zhang, T. (2016). Fog and iot: an overview of research opportunities. IEEE Internet of Things Journal 3: 854–864.
- 65 Liyanage, M., Ahmad, I., Abro, A.B. et al. (eds.) (2018). A Comprehensive Guide to 5G Security. Wiley.
- 66 Munoz, R., Mangues‐Bafalluy, J., Vilalta, R. et al. (2016). The cttc 5g end‐to‐end experimental platform: integrating heterogeneous wireless/optical networks, distributed cloud, and iot devices. IEEE Vehicular Technology Magazine 11: 50–63.
- 67 Fantacci, R., Pecorella, T., Viti, T., and Carlini, C. (2014). A network architecture solution for efficient iot wsn backhauling: challenges and opportunities. IEEE Wireless Communications 21: 113–119.
- 68 Ahmad, I., Kumar, T., Liyanage, M. et al. (2018). Overview of 5G security challenges and solutions. IEEE Communications Standards Magazine 2 (1): 36–43.
- 69 Xu, L., Xie, J., Xu, X., and Wang, S. (2016). Enterprise lte and wifi interworking system and a proposed network selection solution. In: 2016 ACM/IEEE Symposium on Architectures for Networking and Communications Systems (ANCS). Santa Clara, USA (17–18 March 2016): ACM/IEEE.
- 70 Liyanage, M., Gurtov, A., and Ylianttila, M. (eds.) (2015). Software Defined Mobile Networks (SDMN): Beyond LTE Network Architecture. New York: Wiley.
- 71 Liyanage, M., Abro, A.B., Ylianttila, M., and Gurtov, A. (2016). Opportunities and challenges of software‐defined mobile networks in network security. IEEE Security and Privacy 14 (4): 34–44.
- 72 Tehrani, M.N., Uysal, M., and Yanikomeroglu, H. (2014). Device‐to‐device communication in 5g cellular networks: challenges, solutions, and future directions. IEEE Communications Magazine 52: 86–92.
- 73 Shariatmadari, H., Ratasuk, R., and Iraji, S. (2015). Machine‐type communications: current status and future perspectives toward 5g systems. IEEE Communications Magazine 53: 10–17.
- 74 Fog Computing and the Internet of Things: Extend the Cloud to where the Things Are. http://www.cisco.com/c/dam/en_us/solutions/trends/iot/docs/computing-overview.pdf (accessed 25 June 2019).
- 75 Rouse, M. (2016). Edge computing. http://searchdatacenter.techtarget.com/definition/edge-computing. (accessed 25 June 2019).
- 76 CEN‐CENELEC‐ETSI Smart Grid Coordination Group. (2014). SGCG/M490/G Smart Grid Set of Standards Version 3.1, Oct‐2014. ftp://ftp.cencenelec.eu/EN/EuropeanStandardization/HotTopics/SmartGrids/SGCG_Standards_Report.pdf (accessed 25 June 2019).
- 77 Ahmad, I., Kumar, T., Liyanage, M. et al. (2018). Towards gadget‐free internet services: a roadmap of the naked world. Telematics and Informatics 35 (1): 82–92.
- 78 Rajakaruna, A., Manzoor, A., Porambage, P. et al. (2018). Lightweight Dew Computing Paradigm to Manage Heterogeneous Wireless Sensor Networks with UAVs. arXiv preprint arXiv:1811.04283.
- 79 Rahimi, H., Zibaeenejad, A. and Safavi, A.A. (2018). A Novel IoT Architecture based on 5G‐IoT and Next Generation Technologies. GlobeCom‐IoT. https://arxiv.org/ftp/arxiv/papers/1807/1807.03065.pdf (accessed 25 June 2019).
- 80 Srilakshmi, A., Rakkini, J., Sekar, K.R., and Manikandan, R. (2018). A comparative study on internet of things (IoT) and its applications in smart agriculture. Pharmacognosy Journal 10 (2): 260–264.
- 81 Williams, R., McMahon, E., Samtani, S. et al. (2017). Identifying vulnerabilities of consumer internet of things (IoT) devices: a scalable approach. In: 2017 IEEE International Conference on Intelligence and Security Informatics (ISI). Beijing, China (22–24 July 2017): IEEE.
- 82 Frustaci, M., Pace, P., Aloi, G., and Fortino, G. (2018). Evaluating critical security issues of the IoT world: present and future challenges. IEEE Internet of Things Journal 5 (4): 2483–2495.
- 83 Fiore, U., Castiglione, A., De Santis, A., and Palmieri, F. (2017). Exploiting battery‐drain vulnerabilities in mobile smart devices. IEEE Transactions on Sustainable Computing 2 (2): 90–99.
- 84 Xiao, Q., Gibbons, T., and Lebrun, H. (2009). RFID technology. Security Vulnerabilities, and Countermeasures https://doi.org/10.5772/6668 : https://www.researchgate.net/publication/221787702_RFID_Technology_Security_Vulnerabilities_and_Countermeasures (accessed 25 June 2019).
- 85 Khalajmehrabadi, A., Gatsis, N., Akopian, D., and Taha, A. (2018). Real‐time rejection and mitigation of time synchronization attacks on the global positioning system. IEEE Transactions on Industrial Electronics 65 (8): 6425–6435.
- 86 Ning, H., Liu, H., and Yang, Y. (2015). Aggregated‐proof based hierarchical authentication scheme for the internet of things. IEEE Transactions on Parallel and Distributed Systems 26 (3): 657–667.
- 87 Hao, P., Wang, X., and Shen, W. (2018). A collaborative PHY‐aided technique for end‐to‐end IoT device authentication. IEEE Access 6: 42279–42293.
- 88 Shahzad, M. and Singh, M.P. (2017). Continuous authentication and authorization for the internet of things. IEEE Internet Computing 21 (2): 86–90.
- 89 Aman, M.N., Chua, K.C., and Sikdar, B. (2017). Mutual authentication in IoT systems using physical unclonable functions. IEEE Internet of Things Journal 4 (5): 1327–1340.
- 90 Chauhan, J., Seneviratne, S., Hu, Y. et al. (2018). Breathing‐based authentication on resource‐constrained IoT devices using recurrent neural networks. Computer 51 (5): 60–67.
- 91 Ni, J., Lin, X., and Shen, X.S. (2018). Efficient and secure service‐oriented authentication supporting network slicing for 5G‐enabled IoT. IEEE Journal on Selected Areas in Communications 36 (3): 644–657.
- 92 Ravindran, R., Chakraborti, A., and Amin, S. (2017). 5G‐ICN: delivering ICN services over 5G using network slicing. IEEE Communications Magazine 55 (5): 101–107.
- 93 Harel, R., and Babbage, S. (2016). 5G Security Recommendations Package #2: Network Slicing, published by NGMN Alliance, Ver. 01. https://www.ngmn.org/fileadmin/user_upload/160429_NGMN_5G_Security_Network_Slicing_v1_0.pdf (accessed 25 June 2019).
- 94 Siriwardhana, Y., Porambage, P., Liyanage, M. et al. (2019). Micro‐Operator driven Local 5G Network Architecture for Industrial Internet. IEEE Wireless Communications and Networking Conference, Marrakech, Morocco (15–18 April 2019). IEEE.
- 95 Dotaro, E. (2018). 5G Network Slicing and Security. IEEE SDN newsletter, https://sdn.ieee.org/newsletter/january-2018/5g-network-slicing-and-security (accessed 25 June 2019).
- 96 Yao, X., Chen, Z., and Tian, Y. (2015). A lightweight attribute‐based encryption scheme for the internet of things. Future Generation Computer Systems 49: 104–112.
- 97 Kumar, T., Braeken, A., Liyanage, M., and Ylianttila, M. (2017). Identity privacy preserving biometric based authentication scheme for naked healthcare environment. In: 2017 IEEE International Conference on Communications (ICC). Paris, France (21–25 May 2017): IEEE.
- 98 Braeken, A., Liyanage, M., and Jurcut, A.D. (2019). Anonymous lightweight proxy based key agreement for IoT (ALPKA). Wireless Personal Communications 106 (2): 1–20.
- 99 Manzoor, A., Liyanage, M., Braeken, A. et al. (2018). Blockchain based Proxy Re‐Encryption Scheme for Secure IoT Data Sharing. IEEE International Conference on Blockchain and Cryptocurrency (ICBC 2019), Seoul, South Korea (14–17 May 2019). IEEE.
- 100 Liyanage, M., Salo, J., Braeken, A. et al. (2018). 5G privacy: scenarios and solutions. In: 2018 IEEE 5G World Forum (5GWF). Silicon Valley, USA (9–11 July 2018): IEEE.
- 101 Kumar, T., Braeken, A., Jurcut, A.D., Liyanage, M., and Ylianttila, M. (2019). AGE: Authentication in Gadget-Free Healthcare Environments. Information Technology and Management Journal, Springer US.
- 102 Xu, L., Jurcut, AD., and Ahmadi, H. (2019). Emerging Challenges and Requirements for Internet of Things in 5G. 5G‐Enabled Internet of Things. CRC Press.
