There are different ways of detecting if an application is protected by a WAF or IDS; being blocked and/or blacklisted after launching an attack is the worst of all, so we will use Nmap and wafw00f to identify whether our target is behind a WAF before going all in:
- Nmap includes a couple of scripts to test for the presence of a WAF in all of the detected HTTP ports. Let's try some on our vulnerable vm_1:
# nmap -sT -sV -p 80,443,8080,8081 --script=http-waf-detect 192.168.56.11
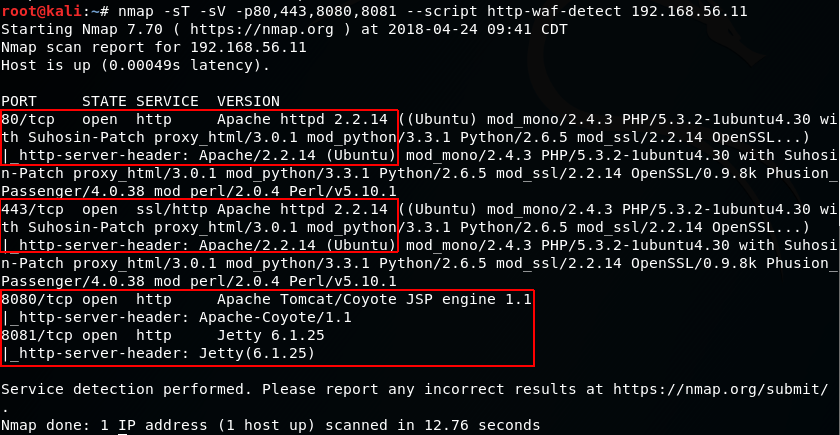
It seems like we don't have a WAF protecting this server
- Now, let's try the same command on a server that actually has a firewall protecting it. Here, we will use example.com as a made-up name; however, you may try it over any protected server:
# nmap -p 80,443 --script=http-waf-detect www.example.com

- There is another script in Nmap that can help us to identify the WAF being used more precisely. The script is http-waf-fingerprint:
# nmap -p 80,443 --script=http-waf-fingerprint www.example.com
- Another tool that Kali Linux includes to help us in detecting and identifying a WAF is wafw00f. Suppose www.example.com is a WAF-protected site:
# wafw00f www.example.com

