CHAPTER 17
Managing Network Connections
Networking is a critical part of modern computing. Fortunately, most Linux distributions can often create a network connection automatically; however, sometimes this process doesn't work, or you may need to tweak the connection or debug problems when they occur. This chapter therefore covers network configuration.
I begin by describing some basic network features that you must understand to properly manage your network configuration. I then describe the process of configuring a network connection. A few tests will help you track down and correct problems, so I explain them in case you run into difficulties. Finally, I explore the dark side to networking: the undesirables of the Internet and how to keep them out of your computer.
 Understanding network features
Understanding network features Configuring a network connection
Configuring a network connection Testing your network connection
Testing your network connection Protecting your system from the bad guys
Protecting your system from the bad guys
Understanding Network Features
Networking involves numerous protocols and technologies that interact in complex ways. Although modern networks and OSs make it easy for users to set up their computers, at least compared to 10 or 20 years ago, doing anything but the simplest configuration requires understanding the key networking protocols and technologies. To begin, I present the following mini-glossary of networking terms:
![]() DNS The Domain Name System (DNS) is a global network of servers that translate between hostnames and IP addresses (both described shortly). Most computers are configured to use a DNS server, which is a server that performs DNS lookups.
DNS The Domain Name System (DNS) is a global network of servers that translate between hostnames and IP addresses (both described shortly). Most computers are configured to use a DNS server, which is a server that performs DNS lookups.
Other means of name resolution exist but are impractical for handling more than a few dozen computers.
DHCP The Dynamic Host Configuration Protocol (DHCP) is a way for most computers on a network to obtain configuration information from another computer (the DHCP server) on the network. DHCP is the key to today's easy network configuration. It's described in more detail shortly, in the section “Deciding Whether to Use DHCP.”
Other methods of wired networking exist, but most are either obsolete or are used in very high-speed, long-distance, or other capacities.
Ethernet This is the wired network hardware that's most often used today. Ethernet comes in several varieties, the most common of which use cables that resemble telephone wires but with broader plugs. Common speeds range from 10 megabits per second (Mbps) to 1 gigabit per second (Gbps, or gigabit Ethernet), although faster speeds are available.
Hostname This is a name that a computer uses for the benefit of humans. Hostnames consist of a computer portion and a network portion. For instance, in lunokhod.luna.edu, lunokhod is the machine name and luna.edu is the network name.
Internet Used generically (with a lowercase i), the word internet refers to a network of networks, connected via routers (described shortly). With a capital I, the word Internet refers to the globe-spanning network with which you're no doubt familiar. The Internet is the largest internet ever created.
![]() IP address An Internet Protocol (IP) address is a number that's assigned to a computer for network addressing purposes. You can think of an IP address as being like a street address or telephone number. Computers communicate with each other via IP addresses. In the past, four-byte IPv4 addresses have dominated; however, the pool of IPv4 addresses has recently been depleted, so many new installations now use 16-byte IPv6 addresses. IP addresses are broken down into two parts: a machine portion and a network portion. The network portion may be used in routing (see router), whereas the machine portion identifies a computer on a given network. This breakdown into machine and network addresses is accomplished via a network mask, as described next.
IP address An Internet Protocol (IP) address is a number that's assigned to a computer for network addressing purposes. You can think of an IP address as being like a street address or telephone number. Computers communicate with each other via IP addresses. In the past, four-byte IPv4 addresses have dominated; however, the pool of IPv4 addresses has recently been depleted, so many new installations now use 16-byte IPv6 addresses. IP addresses are broken down into two parts: a machine portion and a network portion. The network portion may be used in routing (see router), whereas the machine portion identifies a computer on a given network. This breakdown into machine and network addresses is accomplished via a network mask, as described next.
Network mask A network mask (mask or netmask for short) is a way to distinguish between the network and machine portions of an IP address. The netmask defines the individual bits of an IP address that belong to each part of the address. This can be done by giving each bit of the machine address a binary 1 value and expressing the result as a number (such as 255.255.0.0 or 255.255.255.0) for an IPv4 address or by specifying the number of bits in the machine portion of the address (as in 16 or 24).
![]() Router A router (also known as a gateway) connects two or more networks together. Your desktop or server computer is likely to connect directly to a handful of other computers, including a router. The router links to another network, which in turn links to another, and so on. To contact a computer on another network, your computer communicates through the router. Homes and small businesses often use small broadband routers to connect to the Internet. Such devices perform routing and have built-in DNS, DHCP, and other useful servers.
Router A router (also known as a gateway) connects two or more networks together. Your desktop or server computer is likely to connect directly to a handful of other computers, including a router. The router links to another network, which in turn links to another, and so on. To contact a computer on another network, your computer communicates through the router. Homes and small businesses often use small broadband routers to connect to the Internet. Such devices perform routing and have built-in DNS, DHCP, and other useful servers.
Several alternatives to TCP/IP exist, such as AppleTalk, NetBEUI, and IPX/SPX. TCP/IP, however, is the most common network protocol, and the one that underlies the Internet.
TCP/IP The Transmission Control Protocol/Internet Protocol (TCP/IP) is a set of standards that underlie most modern network communications at the software level.
Wi-Fi This term applies to the most common forms of wireless networking, more properly known as IEEE 802.11. Several variants are available that differ in speed. The section “Creating a Wi-Fi Connection,” later in this chapter, describes Wi-Fi configuration in more detail.
The process of creating a network connection is one of assigning the computer an IP address and an associated netmask. Using the IP address, the computer can communicate with other computers on the local network—that is, anything that doesn't require a router as an intermediary. In most cases, you'll want to tell the computer about the network's router so that it can communicate with computers on other network segments (often including the entire Internet). Giving your computer the IP address of a DNS server will enable you to specify computer hostnames rather than IP addresses, which is a highly desirable feature. Thus, these four features—the IP address, the netmask, the router's IP address, and the DNS server's IP address—constitute the basic network configuration features.
In most cases, DHCP can dish out these four features. This can make network configuration fairly automatic, as you'll see in this chapter. If your network doesn't support DHCP, though, you'll need to contact your network's administrator to obtain the critical configuration information. In some cases, you'll need still more information. For instance, if you're using Wi-Fi, you'll need to know the Wi-Fi network's name and perhaps its password.
Configuring a Network Connection
In most cases, your network connection will come up automatically (or very nearly so). Sometimes, though, you'll have to manually adjust the configuration, or simply activate it. If available, automatic configuration is handled via DHCP, so I begin by describing it in more detail. I then cover a topic that's applicable to only some systems: configuring Wi-Fi. If you use it, you must configure Wi-Fi before setting other network options. Once Wi-Fi is configured, the rest of the network setup procedure is much like that for wired networks. I then provide an example of using GUI tools for network configuration; these tools are easy to use and can handle most situations. Finally, I cover text-based configuration tools, which provide a great deal of power that you might need to use in certain settings.
Deciding Whether to Use DHCP
As noted earlier, a computer requires, at a minimum, two pieces of information to connect to a typical network: an IP address and a netmask. IP addresses for a router and a DNS server are practical necessities on most networks, although in some cases you can do without one or both. Some networks require additional configuration details.
DHCP can deliver information even to computers without an IP address by using lower-level addressing methods.
Configuring every computer on a large network with all of this information can be time-consuming. Worse, it can lead to problems caused by human errors, such as typos in IP addresses. For this reason, most networks provide a DHCP server, which can provide this information to other computers.
Depending on the configuration of the server, DHCP can be used to deliver IP addresses in one of two ways:
 In a fixed way so that each computer receives the same IP address every time it boots
In a fixed way so that each computer receives the same IP address every time it boots Dynamically so that a single computer might receive different IP addresses on different boots
Dynamically so that a single computer might receive different IP addresses on different boots
If you're configuring a home or small office network with a broadband router, the router almost certainly includes a DHCP server that you can use. Consult its documentation for details.
Which is used is a policy detail for your network administrator. You needn't be concerned with it, except to know that a computer configured via DHCP isn't necessarily guaranteed to receive the same IP address on each boot. This fact can have important implications. For instance, it's generally easiest and most reliable to configure a server computer if it has a fixed IP address. Thus, as a matter of policy, server computers are often configured without using DHCP, even if workstations on the same network use DHCP. This isn't always the case, though—as already noted, DHCP can deliver a fixed address to some or all computers, so the DHCP server's administrator can configure a network's servers in this way.
As a practical matter, unless you're configuring your own small private network, you should ask your network administrator whether to use DHCP for a new computer. If the answer is no, you should ask for an IP address, the netmask, the router's IP address, and the DNS server's IP address.
Creating a Wi-Fi Connection
Wi-Fi connections are most often used on laptop and smaller portable computers, since using such devices without a physical network cable is often desirable. Some desktop computers, though, have Wi-Fi capabilities, and you may want to use them.
The procedure described here is equivalent to plugging an Ethernet cable into an Ethernet port. This procedure might or might not set up TCP/IP options.
Before proceeding further, be aware that you must have access to a Wi-Fi network. If you're configuring a computer to connect to a broadband router that you've purchased and set up, consult the router's documentation to learn how to locate the router's critical information, such as the service set identifier (SSID; that is, the Wi-Fi network's name, which may be distinct from the TCP/IP network's name) and the password it uses. If you're trying to connect to a business network or a public network, consult the network administrator to obtain this information.
Whatever the computer type, the easiest method of configuring your Wi-Fi connection is to use the GUI. Details of how to do this vary from one distribution to another. As an example, consider doing the task in Fedora:
- Open the System Settings tool by clicking your name in the upper-right corner of the desktop and selecting System Settings from the resulting menu or by typing gnome-control-center at a shell prompt.
- Click the Network item in the System Settings Hardware section.
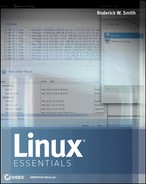
- Click Wireless in the list on the left side of the Network window. The window will change to resemble Figure 17.1.
If you don't see a Wireless option, you may lack Linux drivers for your Wi-Fi hardware. Consult the sidebar “Obtaining Wi-Fi Drivers” for advice on resolving this problem.
FIGURE 17.1 You can adjust the most common network settings from the Network item in the System Settings menu.
- Click the inverted caret to the right of the Network Name field to access a pull-down menu with a list of networks.
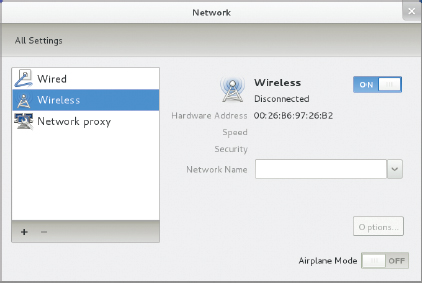
- Select your network from the list. If the network requires authentication, a dialog box like the one shown in Figure 17.2 will appear.
- Type your network's password in the Password field, and then click Connect.
FIGURE 17.2 If your Wi-Fi network requires authentication, you must enter a password before you can begin using it.
The word Disconnected in the Network window (Figure 17.1) should change to read Connecting, followed by Connected. Depending on your network's configuration, you may also see an IP address, the default route, and the DNS server's IP address appear in the window. If so, the computer is now completely configured for network access—the utility has automatically performed the tasks described in the section “Using a Network Configuration GUI,” later in this chapter. If not, though, you may need to perform additional configuration tasks, such as manually setting an IP address. It's also possible that the Wi-Fi connection has failed.
WI - FI SECURITY
Because Wi-Fi data are carried over radio waves, it's easy for the transmissions to be intercepted. Somebody sitting in a car outside of a building can often gain access to a Wi-Fi network, which poses three problems:
 An intruder can intercept data passing over the network, possibly gaining access to sensitive files, acquiring credit card numbers, and so on.
An intruder can intercept data passing over the network, possibly gaining access to sensitive files, acquiring credit card numbers, and so on. An intruder may be able to launch attacks on your computers from behind any firewall you maintain to protect yourself from outsiders.
An intruder may be able to launch attacks on your computers from behind any firewall you maintain to protect yourself from outsiders. An intruder can use your network access to attack other computers or to conduct illegal activities such as pirating movies, music, or software. This not only consumes your network bandwidth, but if the activities are detected, you will fall under suspicion!
An intruder can use your network access to attack other computers or to conduct illegal activities such as pirating movies, music, or software. This not only consumes your network bandwidth, but if the activities are detected, you will fall under suspicion!
For these reasons, you should secure any Wi-Fi network you manage. Three security levels are available (four if you count none at all):
WEP The Wired Equivalent Privacy (WEP) is a very weak encryption protocol. Methods of breaking into a WEP-encrypted network are well known, making this method essentially worthless.
WPA Wi-Fi Protected Access (WPA) security provides improved encryption and authentication tools compared to WEP.
WPA2 WPA2 is WPA's replacement, and it provides still more improvements in encryption and authentication.
Several variants on each of these encryption methods are available. For instance, WPA and WPA2 provide both personal and enterprise options, the latter requiring a more complex setup with a dedicated authentication server. Typically, you set the encryption method in a broadband router or wireless access point (WAP). Clients then detect the method in use and present appropriate options, such as the password prompt shown earlier in Figure 17.2.
Public Wi-Fi connections might not use any of these protocols. You can use such connections, but be aware that any data you send or receive might be visible to others.
The GUI method of establishing a Wi-Fi connection is almost always the easiest method to use. If you need to fine-tune the connection, though, you can use various tools to probe for and manage Wi-Fi links. Here are the two most important of these tools:
You might use iwlist scan to locate public Wi-Fi networks in a coffee shop or hotel, followed by an iwconfig command to connect to a network you've found.
iwlist This command can identify nearby Wi-Fi networks. Type iwlist scan or iwlist scanning as root to obtain a list of nearby networks. This command produces a great deal of technical data, though. You're probably most interested in the network names, which appear in the output following the string ESSID, so typing iwlist scan | grep ESSID will pare down the output.
iwconfig This utility connects and disconnects you from specific networks. It uses many options, and you may need to study its man page to fully understand it. In most cases, though, typing something like iwconfig wlan0 essid NoWires channel 1 mode Managed key s:N1mP7mHNw will do the trick. This example connects to the NoWires network running on channel 1 using the password N1mP7mHNw.
OBTAINING WI - FI DRIVERS
Unfortunately, Linux driver support for Wi-Fi hardware is fairly weak. If you don't see your Wi-Fi hardware when you try to configure it, you may need to track down suitable drivers. You can begin this task with a tool called lspci, which is described in Chapter 5, “Managing Hardware.” Type this command with no options to see a list of available hardware and search that list for a wireless network adapter. For instance, my own laptop's lspci output includes the following line:
This line identifies the Wi-Fi adapter as a Realtek RTL8191SEvB. A search on Realtek's Web site turns up a driver; however, this driver has to be compiled locally, which is a topic that's beyond the scope of this book. You also might not be lucky enough to find a driver in this way.
An alternative to using a native Linux driver is to use a Windows driver. This unusual option is possible using a package called ndiswrapper (http://ndiswrapper.sourceforge.net), which enables you to install Windows Wi-Fi drivers in Linux. Unfortunately, not all distributions provide ndiswrapper in their standard package sets, but you can usually find a binary package in an add-on repository. Similar functionality is provided by the Linuxant DriverLoader software (http://www.linuxant.com/driverloader/), which is less popular than ndiswrapper but is still worth considering.
If all other options fail, you may need to buy new networking hardware. Many USB Wi-Fi adapters are available, but you should research them to find one that has good Linux support. You can also replace the built-in adapters on some laptops.
Using a Network Configuration GUI
If you've configured a Wi-Fi link but it hasn't obtained an IP address, or if you need to set up a wired network connection, you'll have to set up the TCP/IP networking options. You can do this via text-mode tools, as described later, in “Using Text-Based Tools,” or you can use GUI tools. The latter option is easier for new users, but the GUI tools vary from one distribution to another. As an example, the procedure for configuring Fedora using GUI tools is as follows:
- Open the System Settings tool by clicking your name in the upper-right corner of the desktop and selecting System Settings from the resulting menu or by typing gnome-control-center at a shell prompt.
- Click the Network item in the System Settings Hardware section.
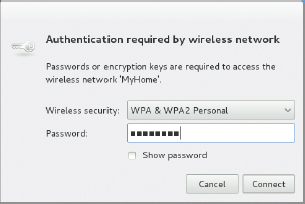
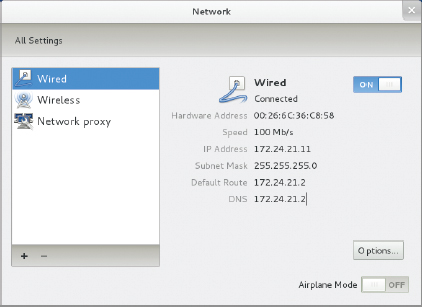
- Select the network device from the list on the left side of the window. The result should resemble Figure 17.3; however, this figure shows a properly configured network link that has no obvious problems. If your network link isn't working, it might read Disconnected rather than Connected or it might otherwise show significantly different information.
- Click Options to adjust your network settings.
FIGURE 17.3 Network connections usually set themselves up automatically, but sometimes they don't.
You can configure a computer for both IPv4 and IPv6. To do so manually, however, you must have both IPv4 and IPv6 addresses.
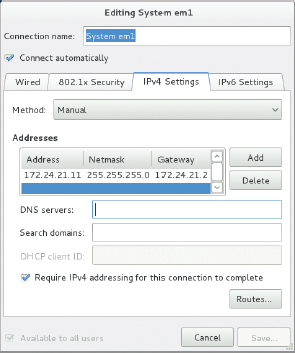
- Select the IPv4 Settings or IPv6 Settings tab, depending on whether your network uses IPv4 or IPv6. The result resembles Figure 17.4, which shows a partially configured manual IPv4 setup.
FIGURE 17.4 You can set key TCP/IP features after clicking Options in the Network window.
- Select the connection method using the Method button. The Automatic (DHCP) and Manual options are the most common, but a few more obscure options are available, too. You can disable a network connection by selecting Disabled.
- If you're using DHCP, you can type your computer's DHCP client ID in the DHCP Client ID field. Some networks use this information to assign the computer a hostname or a fixed IP address. If your network administrator hasn't given you this information, you can leave this field blank.
- To perform manual configuration, select Manual in the Method button and enter the remaining information. You enter an IP address, netmask, and router address by clicking the Add button, whereupon suitable fields in the Addresses section of the dialog box become available.
- When you're done making changes, click Save.
If all goes well, your Network dialog box should change to show an IP address, subnet mask, default route, and DNS server address—although some networks omit some of these items.
Using Text-Based Tools
Although the GUI network configuration tools are easy to use and work well most of the time, sometimes you must use a more flexible set of text-based tools. These tools include the following:
![]() ifconfig This program brings up or shuts down a network connection by associating an IP address and network mask to a piece of network hardware.
ifconfig This program brings up or shuts down a network connection by associating an IP address and network mask to a piece of network hardware.
![]() route This program adjusts the computer's routing table, which determines through which network device specific network packets are sent.
route This program adjusts the computer's routing table, which determines through which network device specific network packets are sent.
![]() /etc/resolv.conf This file contains the IP addresses of up to three DNS servers as well as the name of the computer's Internet domain and of other domains that should be searched when the user omits a domain name from a hostname.
/etc/resolv.conf This file contains the IP addresses of up to three DNS servers as well as the name of the computer's Internet domain and of other domains that should be searched when the user omits a domain name from a hostname.
A DHCP client A DHCP client program, such as dhclient or dhcpcd, can often configure a network connection automatically. You simply type the program's name, perhaps followed by a network device name.
Don't confuse dhcpcd, a DHCP client, with dhcpd, a DHCP server.
Distribution-specific network scripts The ifconfig, route, and DHCP client programs produce temporary changes to the computer's network configuration. If you want to make permanent changes, you must store your settings in a configuration file. The name and format of this file varies from one distribution to another. For instance, in Fedora it's /etc/sysconfig/network-scripts/ifcfg-netname, where netname is the name of the network device; in Debian or Ubuntu, it's /etc/network/interfaces.
The ifconfig and route commands are both quite complex; however, their basic use is fairly straightforward. Suppose you want to assign the IP address 192.168.29.39/24 to the eth0 network device and tell it to use 192.168.29.1 as the router. The following two commands would do the trick:
# ifconfig eth0 up 192.168.29.39 netmask 255.255.255.0 # route add default gw 192.168.29.1
You can instead take down a connection by using down rather than up with ifconfig, delete routes by using del rather than add with route, and so on. Consult these programs' man pages for details.
Some distributions use dhclient by default, but others use dhcpcd. If you don't know which to use, try both.
If your network uses DHCP, you can type dhclient netname or dhcpcd netname to bring up the netname interface and configure it using DHCP. Manually typing this command can be handy if you're trying to debug a network problem related to DHCP or if your network's DHCP configuration has changed and temporarily broken connectivity for some computers.
NETWORK DEVICE NAMES
Traditionally, Linux has given the first Ethernet device a name of eth0 and subsequent devices names of eth1 and so on. Similarly, Wi-Fi devices have acquired names of the form wlan0 and up. Fedora, however, has begun deviating from this scheme, starting with version 15. This makes it harder to predict the device names of Ethernet devices from one computer to another. The goal is to make the device names more stable between reboots on computers with multiple network interfaces. Such systems are often routers or servers with multiple network links, and they typically require specific configurations on specific interfaces. If the device name changes from one boot to another—which can happen if network cards happen to be discovered in different order on different boots—problems can ensue.
You can learn your network device names by typing ifconfig with no options. (You can even do this as a normal user.) The result includes one or more blocks of output like the following:
In this example, em1 is the device name—it prominently begins this block of output. The name lo refers to a loopback device, which is used for certain local access procedures, so you can ignore it if you want to find your network hardware's device name.
If you're configuring your network settings manually, you should enter your DNS name server data and your network name into /etc/resolv.conf. A sample of this file appears in Listing 17.1.
Listing 17.1: A sample /etc/resolv.conf configuration file
domain luna.edu search example.com example.org nameserver 192.168.1.2 nameserver 10.78.102.1 nameserver 10.78.221.1
Three keywords identify DNS resolution features in /etc/resolv.conf:
/etc/resolv.conf supports additional keywords, but they're seldom used. Consult its man page for details.
domain You identify your computer's default domain name on this line. The primary effect is that the computer searches for hostnames without domain names in this domain. For example, in Listing 17.1, if you specify a hostname of lunokhod, the computer will find the IP address of lunokhod.luna.edu.
search You can have the computer search for hostnames in additional domains by specifying them on a search line, with domains separated by spaces or tabs. You can specify up to six domains in this way. Be aware, however, that adding domains to the search path is likely to slow down hostname lookup.
nameserver This keyword identifies DNS server computers by IP address. You can specify multiple servers by including multiple nameserver lines, up to the maximum of three.
If you want to manually adjust your permanent network configuration, you can do so by editing the network configuration file, such as /etc/sysconfig/network-scripts/ifcfg-netname on a Fedora system. Listing 17.2 shows a sample of this file.
Listing 17.2: A sample network configuration file
DEVICE=“em1” BOOTPROTO=“static” IPADDR=192.168.29.39 NETMASK=255.255.255.0 NETWORK=192.168.29.0 BROADCAST=192.168.29.255 GATEWAY=192.168.29.1 ONBOOT=yes NM_CONTROLLED=“yes” HWADDR=00:26:6C:36:C8:58 TYPE=Ethernet DEFROUTE=yes PEERDNS=yes PEERROUTES=yes IPV4_FAILURE_FATAL=yes IPV6INIT=no NAME=“System em1” UUID=1dad842d-1912-ef5a-a43a-bc238fb267e7
Some of these options have purposes that you can figure out based on their names, and you can adjust as necessary. If you don't understand an option, it's best to leave it alone. Some specific features you may want to attend to include the following:
 If you want to use DHCP, change the BOOTPROTO line to read BOOTPROTO=“dhcp” rather than BOOTPROTO=“static” and remove the lines from IPADDR through GATEWAY.
If you want to use DHCP, change the BOOTPROTO line to read BOOTPROTO=“dhcp” rather than BOOTPROTO=“static” and remove the lines from IPADDR through GATEWAY. If you want to keep the network link from starting up automatically when the computer boots, change ONBOOT to no. Users will then have to manually activate the network whenever they want to use it.
If you want to keep the network link from starting up automatically when the computer boots, change ONBOOT to no. Users will then have to manually activate the network whenever they want to use it.
Forcing users to start their network connections can limit the computer's use of network resources, such as IP addresses if your network uses DHCP.
 The NETWORK and BROADCAST options are both derived from the IP address (IPADDR) and netmask (NETMASK). The NETWORK address is the network portion of the IP address but with binary 0 values substituted for the host-specific part of the IP address. The BROADCAST address is similar, but it substitutes binary 1 values for the host-specific part of the address.
The NETWORK and BROADCAST options are both derived from the IP address (IPADDR) and netmask (NETMASK). The NETWORK address is the network portion of the IP address but with binary 0 values substituted for the host-specific part of the IP address. The BROADCAST address is similar, but it substitutes binary 1 values for the host-specific part of the address.
If you're running Debian, Ubuntu, or some other distribution that uses a different network configuration file, you'll have to track down that file and modify it. The format may vary from the file shown in Listing 17.2, too, although the entries you must change are usually fairly obvious. If in doubt, consult distribution-specific documentation.
The ifup and ifdown commands bring up or take down a network connection based on the settings in your configuration file. Thus, after you change these settings, you may want to type ifdown netname followed by ifup netname. The result should be a network link that reflects the new settings. Be aware, however, that this procedure may disconnect network clients and servers.
Testing Your Network Connection
In most cases, your network connection will work fine from the moment you start it. Sometimes, though, you may need to diagnose problems, either because you can't get the connection to work at all or because a formerly working connection has stopped working. In the following pages, I describe several types of network tests: checking your routing table, testing basic connectivity, testing to locate where a break in connectivity has occurred, testing DNS functioning, and testing the network's status.
Checking Your Routing Table
![]() Earlier, I described using the route command to set the default route on a computer. You can check that your route is sensible by using the same command. In most cases, typing route alone will do the job:
Earlier, I described using the route command to set the default route on a computer. You can check that your route is sensible by using the same command. In most cases, typing route alone will do the job:
$ route Kernel IP routing table Destination Gateway Genmask Flags Metric Ref Use Iface 192.168.29.0 * 255.255.255.0 U 0 0 0 eth0 127.0.0.0 * 255.0.0.0 U 0 0 0 lo default 192.168.29.1 0.0.0.0 UG 0 0 0 eth0
The routing table of a typical workstation or even server is quite simple and can be automatically configured. Network routers often require complex routing tables, though.
This shows that data destined for 192.168.29.0 (that is, any computer with an IP address between 192.168.29.1 and 192.168.29.254) goes directly over eth0. The 127.0.0.0 network is a special interface that “loops back” to the originating computer. Linux uses this for some internal networking purposes. The last line shows the default route, which describes what to do with everything that doesn't match any other entry in the routing table. This line identifies the default route's gateway system as 192.168.29.1. If it's missing or misconfigured, some or all traffic destined for external networks, such as the Internet, won't make it beyond your local network segment.
Testing Basic Connectivity
![]() The most basic network test is ping, which sends a simple network packet to the system you name (via IP address or hostname) and waits for a reply. In Linux, ping continues sending packets once every second or so until you interrupt it with a Ctrl+C keystroke. You can instead specify a limited number of tests via the -c num option. Here's an example of its output:
The most basic network test is ping, which sends a simple network packet to the system you name (via IP address or hostname) and waits for a reply. In Linux, ping continues sending packets once every second or so until you interrupt it with a Ctrl+C keystroke. You can instead specify a limited number of tests via the -c num option. Here's an example of its output:
This command sent four packets and waited for their return, which occurred quite quickly (in an average of 0.295 ms) because the target system was on the local network. A few common problem patterns can help you diagnose where a network problem resides:
 If you can ping local systems but not remote systems, the problem is probably in your router or in an improper router specification.
If you can ping local systems but not remote systems, the problem is probably in your router or in an improper router specification. If you can ping by IP address but not by name, the problem is most likely with your DNS server or DNS configuration.
If you can ping by IP address but not by name, the problem is most likely with your DNS server or DNS configuration. If you can't ping at all, even by IP address, then you probably have a fundamental configuration problem.
If you can't ping at all, even by IP address, then you probably have a fundamental configuration problem.
Finding Breaks in Connectivity
A step up from ping is the traceroute command, which sends a series of three test packets to each computer between your system and a specified target system. Listing 17.3 shows a sample of traceroute's output.
Listing 17.3: A sample traceroute output
$ traceroute -n 10.1.0.43 traceroute to 10.1.0.43 (10.1.0.43), 30 hops max, 52 byte packets 1 192.168.1.2 1.021 ms 36.519 ms 0.971 ms 2 10.10.88.1 17.250 ms 9.959 ms 9.637 ms 3 10.9.8.173 8.799 ms 19.501 ms 10.884 ms 4 10.9.8.133 21.059 ms 9.231 ms 103.068 ms 5 10.9.14.9 8.554 ms 12.982 ms 10.029 ms 6 10.1.0.44 10.273 ms 9.987 ms 11.215 ms 7 10.1.0.43 16.360 ms * 8.102 ms
The -n option to this command tells it to display target computers' IP addresses rather than their hostnames. This can speed up the process a bit, particularly if you're having DNS problems, and it can sometimes make the output easier to read—but you may want to know the hostnames of problem systems because they can help you pinpoint who's responsible for a problem.
The output of traceroute can be diagnostic in several ways:
 Typically, times increase with increasing hop numbers. This is normal, and aside from some variability in the example output, you can see this pattern in Listing 17.3.
Typically, times increase with increasing hop numbers. This is normal, and aside from some variability in the example output, you can see this pattern in Listing 17.3. Variable times on a single hop can indicate that a router is overloaded or that some other intermittent issue is causing variability in the times. You can see this factor at play in several hops in Listing 17.3, and particularly in hops 1 and 4. Such issues may result in variable performance but should not cause network sessions to time out or otherwise fail completely.
Variable times on a single hop can indicate that a router is overloaded or that some other intermittent issue is causing variability in the times. You can see this factor at play in several hops in Listing 17.3, and particularly in hops 1 and 4. Such issues may result in variable performance but should not cause network sessions to time out or otherwise fail completely. Sometimes a response to a packet is never received. This condition is indicated by an asterisk (*) in a time field, as in the second packet for hop 7 in Listing 17.3.
Sometimes a response to a packet is never received. This condition is indicated by an asterisk (*) in a time field, as in the second packet for hop 7 in Listing 17.3.
Some routers block all traceroute data. If your trace-route output contains nothing but asterisks past a certain point, you may have run into such a system.
 A dramatic jump in times can indicate a great physical distance between routers. Ignoring the middle time of 36.519 ms in the first hop of Listing 17.3, you can see such a jump in the change from hop 1 to hop 2. In the case of Listing 17.3, this indicates the link from the local network to the Internet service provider's network. Even bigger jumps in time are common on intercontinental links. Such jumps are not necessarily signs of misconfiguration that needs to be fixed, but they can influence network performance, particularly for highly interactive protocols such as remote login tools or network-enabled gaming.
A dramatic jump in times can indicate a great physical distance between routers. Ignoring the middle time of 36.519 ms in the first hop of Listing 17.3, you can see such a jump in the change from hop 1 to hop 2. In the case of Listing 17.3, this indicates the link from the local network to the Internet service provider's network. Even bigger jumps in time are common on intercontinental links. Such jumps are not necessarily signs of misconfiguration that needs to be fixed, but they can influence network performance, particularly for highly interactive protocols such as remote login tools or network-enabled gaming.
Among other things, traceroute is helpful in determining whether a problem in network connectivity exists in a network for which you're responsible. For instance, the variability in the first hop of Listing 17.3 could indicate a problem on the local network, but the lost packet associated with the final destination most likely is not a local problem. If the trouble link is within your jurisdiction, you can check the status of the problem system, nearby systems, and the network segment in general.
Testing DNS
DNS problems can cause networking to fail almost as badly as can a physically cut cable. Because both people and many network tools rely on hostnames, if DNS resolution doesn't work, the network becomes nearly useless.
![]() You can test your network's DNS server by using a number of tools, such as host, dig, and nslookup. These tools are similar in many ways, and they all enable you to look up a hostname by typing the command's name followed by a hostname:
You can test your network's DNS server by using a number of tools, such as host, dig, and nslookup. These tools are similar in many ways, and they all enable you to look up a hostname by typing the command's name followed by a hostname:
The nslookup program is deprecated, meaning that developers plan to eventually remove it from common use, but it's available at the moment.
$ hostwww.sybex.com www.sybex.com has address 208.215.179.220
This example shows normal name resolution. In this case, the hostname links directly to just one IP address. In some cases, you may find notices about aliases or multiple IP addresses. This is also normal, at least for some sites. If the command takes a long time to respond or complains about a timeout or an inability to reach servers, though, it means that your computer's DNS configuration is wrong.
Recall that /etc/ resolv.conf contains the IP addresses of your network's DNS servers. They're identified on nameserver lines.
You can add the IP address of a specific DNS server, as in host www.whitehouse.gov 192.168.39.7 to test the 192.168.39.7 server. If your computer is configured to use multiple DNS servers, you can test each one individually in this way. Perhaps one is unreliable or incorrect, in which case you might want to remove it from your configuration. Be aware, though, that if you remove a DNS server from /etc/resolv.conf on a computer that's configured via DHCP, your change will eventually be undone by DHCP. If this is a recurring problem, you should probably consult your network administrator.
Although host is a useful tool for performing basic hostname lookups, the dig utility (or the deprecated nslookup) can perform more complex queries and can return more information about a hostname, domain, or IP address. This makes dig a useful tool for advanced network diagnostics, but at the cost of ease of use; it's harder for a novice to interpret dig's output.
Checking Your Network Status
![]() Another useful diagnostic tool is netstat. This is something of a Swiss Army knife of network tools because it can be used in place of several others, depending on the parameters it's passed. It can also return information that's not easily obtained in other ways. Some examples include the following:
Another useful diagnostic tool is netstat. This is something of a Swiss Army knife of network tools because it can be used in place of several others, depending on the parameters it's passed. It can also return information that's not easily obtained in other ways. Some examples include the following:
Interface information Pass netstat the --interface or -i parameter to obtain information about your network interfaces similar to what ifconfig returns. (Some versions of netstat return information in the same format, but others lay out the information differently.)
Routing information You can use the --route or -r parameter to obtain a routing table listing similar to what the route command displays.
Small broadband routers use NAT. If you have such a device, chances are your desktop and laptop systems needn't be configured to do so themselves.
Masquerade information Pass netstat the --masquerade or -M parameter to obtain information about connections mediated by Linux's Network Address Translation (NAT) features, which often go by the name IP masquerading. NAT enables a Linux router to “hide” a network behind a single IP address. This can be a good way to stretch limited IPv4 addresses.
Program use Some versions of netstat support the --program (or -p) parameter, which attempts to provide information about the programs that are using network connections. This attempt isn't always successful, but it often is, so you can see what programs are making outside connections.
Open ports When used with various other parameters, or without any parameters at all, netstat returns information about open ports and the systems to which they connect.
All connections The --all or -a option is used in conjunction with others. It causes netstat to display information about the ports that server programs open to listen for network connections, in addition to already-open connections.
Keep in mind that netstat is a powerful tool, and its options and output aren't entirely consistent from one distribution to another. You may want to peruse its man page and experiment with netstat to learn what it can do.
Protecting Your System from the Bad Guys
Networks provide many useful features for their users. Unfortunately, they also provide many risks. Network security is a complex topic, and I can provide only a few basic tips to help you prevent your system from being compromised. Here are some of the most important things you can do:
Shut down unused servers. Linux's major security vulnerabilities aren't in worms and viruses, as they are with Windows; in Linux, the risks center around outsiders breaking into your computer by abusing server programs that you run. Therefore, it's important that you don't run servers unnecessarily. Some distributions automatically install and run servers, such as the Secure Shell (SSH), the Apache Web server, or a mail server such as sendmail or Postfix. The most thorough way to remove a server is to uninstall it using your package system (described in Chapter 9, “Using Programs and Processes”)—but you must issue the command to uninstall the relevant package rather than to install it.
Firewalls can run on one computer to protect just it or on a router to protect a whole network.
Enable a firewall. A firewall is a program or system setting that polices network transactions, allowing or disallowing them based on programmed criteria. Most Linux distributions enable firewalls by default, but you may want to adjust their settings for your specific needs.
Use good passwords. Chapter 14, “Creating Users and Groups,” describes how to select a good password. If your computer runs a login server of any type, setting a good password can minimize the risk of an outsider breaking in by guessing your password.
Be suspicious. You should be suspicious of untrusted sources of data. Phishing (attempting to extract sensitive data from users by posing as some trusted individual or organization) and similar attacks can dupe individuals into giving up passwords, financial data, and so on. Although malicious software (or malware) for Linux is rare, it would be easy to produce. You're best off sticking to official software sources and remembering that e-mails, Web sites, and other communications can be faked.
Keep your software up to date. Chapter 9 describes the package management tools you can use to keep your system up to date. It's best to regularly check your system for software updates, since many such updates fix security bugs—problems that can be exploited by outsiders or by legitimate but malicious users to take over your computer.
Networking is integral to today's computers, and Linux provides excellent networking capabilities. In most cases, your computer will detect your network and configure itself automatically; however, sometimes you must manually create an advanced configuration or override an incorrect automatic configuration. You may also need to test your network configuration to determine where a problem lies—in an IP address setting, in a DNS configuration, or elsewhere. Unfortunately, networks can be abused as well as used, so you must remain vigilant against those who would break into your computer and use it for their own purposes. A few steps, such as keeping your software updated, can greatly minimize the risks.
SUGGESTED EXERCISES
 On a small private network that you control or in a lab environment under the supervision of an instructor, reconfigure a computer that normally uses DHCP to use its assigned IP address in a static fashion. Test the connection, and then switch back to DHCP. Do not perform this test on a work or school network that's used for normal purposes; misconfiguration of a computer's IP address can cause problems for other computers.
On a small private network that you control or in a lab environment under the supervision of an instructor, reconfigure a computer that normally uses DHCP to use its assigned IP address in a static fashion. Test the connection, and then switch back to DHCP. Do not perform this test on a work or school network that's used for normal purposes; misconfiguration of a computer's IP address can cause problems for other computers. Back up your /etc/resolv.conf file and then edit the original so that its nameserver lines point to computers that don't run DNS servers. Test your network configuration by attempting to access remote servers using ping, a Web browser, and other utilities. Observe the types of failures that result. When you're done, restore the original file.
Back up your /etc/resolv.conf file and then edit the original so that its nameserver lines point to computers that don't run DNS servers. Test your network configuration by attempting to access remote servers using ping, a Web browser, and other utilities. Observe the types of failures that result. When you're done, restore the original file.
REVIEW QUESTIONS
- You want to set up a computer on a local network via a static TCP/IP configuration, but you lack a gateway address. Which of the following is true?
- Because the gateway address is necessary, no TCP/IP networking functions will work.
- TCP/IP networking will function, but you'll be unable to convert host-names to IP addresses, and vice versa.
- You'll be able to communicate with machines on your local network segment but not with other systems.
- The computer won't be able to tell which other computers are local and which are remote.
- You'll be able to use the computer as a network server system, but not as a network client.
- Which of the following types of information are returned by typing ifconfig eth0? (Select all that apply.)
- The names of programs that are using eth0
- The IP address assigned to eth0
- The hardware address of eth0
- The hostname associated with eth0
- The gateway with which eth0 communicates
- The ping utility responds normally when you use it with an IP address but not when you use it with a hostname that you're positive corresponds to this IP address. What might cause this problem? (Select all that apply.)
- The route between your computer and its DNS server may be incorrect.
- The target computer may be configured to ignore packets from ping.
- The DNS configuration on the target system may be broken.
- Your computer's hostname may be set incorrectly.
- Your computer's DNS configuration may be broken.
- True or false: IPv4 addresses are four bytes in length.
- True or false: The /etc/resolv.conf file tells the computer whether to use DHCP for its network configuration.
- True or false: You can check the current status of your routing table by typing route at a shell prompt.
- The _________ program serves as a multi-purpose network tool; it can do many of the same things as ifconfig, route, and several others.
- The traditional name for the first Ethernet interface in Linux (but not in recent versions of Fedora) is _________.
- A _________ is a program or system configuration that blocks or enables network access to, from, or through a computer based on criteria you specify.