Terms you’ll need to understand:
✓ | User account |
✓ | Local user |
✓ | Domain user |
✓ | Administrator account |
✓ | Guest account |
✓ | Standard account |
✓ | User Account Control (UAC) |
Techniques/concepts you’ll need to master:
✓ | Describe the differences between standard, administrator, and guest accounts. |
✓ | Using the User Accounts console, create and manage users. |
✓ | Describe the purpose of UAC and how it affects users using the computer. |
✓ | Using the Control Panel, enable or disable UAC. |
✓ | Using local policies, configure UAC. |
✓ | Configure legacy software to work with Windows Vista. |
To keep a system secure, you need to use user accounts, which provide accountability and the ability to give rights and permissions to individuals. If your computer has many users, you can then use groups to simplify the assigning of rights and permissions by assigning users to groups and assign the rights and permissions to those groups. To make your system secure, Windows Vista introduced User Account Control (UAC) to help protect against malware that may attack your system at any time by expanding what a standard user can do on a system without becoming an administrator.
Microsoft Windows Vista workstations can be configured as a member of a workgroup or domain. When a workstation is configured as a member of a workgroup, user access and security are configured on the workstation itself. Each computer maintains its own security database, which includes its own local user accounts and groups. If a user on one computer needs to access resources on other computers, a user account must be created on each computer. The user and group information is not shared with other computers.
A domain is a logical group of computers that define a security boundary. A domain uses one database known as Active Directory, which is stored on one or more domain controllers. It gives the ability to share its common security and user and group account information for all computers with the domain. When a user logs on to the domain, that user can access resources throughout the domain with the same logon (single sign-on). The domain allows for centralized network administration of all users, groups, and resources on the network.
A user account enables a user to log on to a computer or domain with an identity that can be authenticated and authorized for access to the resources of the computer or domain. Because the user account is meant to be assigned to one and only one user, it allows you to assign rights and permissions to a single user and enables you to track what users are doing (accountability).
Note
It is highly recommended that all users who log on to the network should have their own unique user account and password.
Two general types of user accounts are defined in Windows Vista:
Local user accounts. User accounts defined on a local computer, which have access to the local computer only. You add or remove local user accounts with the Control Panel’s User Accounts options or the Local Users and Groups utility. Local Users and Groups is accessible through the Computer Management console, a Microsoft Management Console (MMC) tool, which is found in Administrative Tools.
Domain user accounts. User accounts defined in the Active Directory. Through single sign-on, these accounts can access resources throughout a domain/forest. When a computer is a member of an Active Directory domain, you can create domain user accounts using Active Directory Users and Computers. This MMC tool is available on the Administrative Tools menu when you install the Windows Server Administrator Tools (Adminpak.msi) on your Windows Vista computer.
A local user account allows users to log on at and gain resources on only the computer where they create such an account. The user account tells Windows which files and folders the user can access, which changes the user can make to the computer, and the user’s personal preferences, such as desktop background or color theme. User accounts enable the sharing a computer between several people, with each user having personal files and settings. Each person accesses his user account with a username and password.
Every Windows Vista computer has local computer accounts, regardless of whether the computer is a member of a workgroup or a domain. When you install Windows Vista, the operating system installs default user accounts, which are managed using the Local Users and Groups console. The key accounts you’ll see are the following:
Administrator. Administrator is a predefined account that provides complete access to files, directories, services, and other facilities on the computer. You can’t delete this account.
Guest. Guest is designed for users who need one-time or occasional access. Although guests have only limited system privileges, you should be careful about using this account because it opens the system up to potential security problems. The risk is so great that the account is initially disabled when you install Windows Vista.
The built-in administrator account is disabled by default in Windows Vista on new installations. If Windows Vista determines during an upgrade from Windows XP that the built-in administrator is the only active local administrator account, Windows Vista leaves the account enabled and places the account in Admin Approval mode. The built-in administrator account, by default, cannot log on to the computer in Safe mode.
Windows Vista also provides groups, which you use to grant permissions to similar types of users and to simplify account administration. If a user is a member of a group that can access a resource, that particular user can access the same resource. Therefore, you can give a user access to various work-related resources just by making the user a member of the correct group.
When you create additional accounts in Windows Vista using the Control Panel, you choose between three different kinds of accounts:
Standard
Administrator
Guest
Each account type gives the user a different level of control over the computer.
The standard account is the account to use for everyday computing. A standard user account lets you use most of the capabilities of the computer, but permission from an administrator is required if you want to make changes that affect other users or the security of the computer. You can use most programs that are installed on the computer, but you can’t install or uninstall software and hardware, delete files that are required for the computer to work, or change settings on the computer that affect other users. If you’re using a standard account, some programs might require you to provide an administrator password before you can perform certain tasks.
The administrator account provides the most control over the computer, and should only be used when necessary. It lets you make changes that will affect other users. Administrators can change security settings, install software and hardware, and access all files on the computer. Administrators can also make changes to other local user accounts.
Note
When you create an administrator user, it adds the user to the Administrators group. When you create a standard user, it adds the user to the Users group.
When you set up Windows, you’ll be required to create a user account. This account is an administrator account that enables you to set up your computer and install any programs that you would like to use. After you have finished setting up your computer, we recommend that you use a standard user account for your day-to-day computing.
Exam Alert
Because the administrator account has access to all network resources on the computer, it is always more secure to use a standard user account rather than an administrator account.
The guest account is primarily for people who need temporary access to the computer. It is for users who don’t have a permanent account on your computer or domain. It enables people to use your computer without having access to your personal files. People using the guest account can’t install software or hardware, change settings, or create a password.
Note
By default, the administrator account and guest account are disabled on new installations of Windows Vista. Therefore, you must enable these accounts before they can be used.
All user accounts are identified with a logon name. In Windows Vista, this logon name has two parts: the username and the user computer or domain in which the user account exists. If you have a computer called PC1 and the username is User1, the full logon name for Windows Vista is PC1User1. Of course, User1 can log on to his local workstation and access local resources, but would not be able to access domain resources.
When working with domains, the full logon name can be expressed in two different ways:
The user account name and the full domain name separated by the at (@) symbol. For example, the full logon name for User1 in the Acme.com domain is [email protected].
The user account name and the domain separated by the backslash symbol (). For example, the full logon name for User1 in the Acme domain is AcmeUser1.
While Windows Vista represents a user with an user account, administrators as well as users see the user account represented by a user name for easy identification. Windows Vista identifies the user account by using the user account’s security identifier (SID). A SID is a unique identifier that is automatically generated when a user account is created and consists of a computer or domain security ID prefix combined with a unique relative ID for the user. Having a unique identifier allows administrators to change a user’s username while keeping all settings, permissions, and rights associated with the account. Because each user account has a unique security identify, an administrator can delete an account without worrying that someone might gain access to resources just by re-creating an account.
To provide security, user accounts should have passwords. Passwords are authentication strings for an account and may consist of upper- and lowercase characters, digits, and special characters.
Exam Alert
It is recommended that all local computer accounts have passwords. If an account is created without a password, anyone can log on to the account from the console, and there is no protection for the account. However, a local account without a password cannot be used to remotely access a computer.
The User Accounts console accessed through the Control Panel provides an easy way to manage user accounts. If you want more advanced control, use the Users and Groups console (which is also part of the Computer Management console).
For a computer that is a member of a workgroup, you can create a local user account on a computer by following these steps:
In the Control Panel, click Add or Remove User Accounts under the User Accounts heading. This displays the Manage Accounts page. The Manage Accounts page lists all configurable user accounts on the local computer by account type and with configuration details. If an account has a password, it is listed as being password protected. If an account is disabled, it is listed as being off.
Click Create a New Account to display the Create New Account page.
Enter the name of the local account. This name is displayed on the Welcome screen and Start menu.
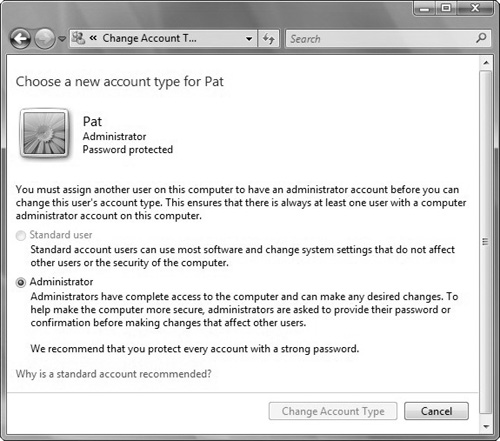
Set the type of account as either Standard User or Administrator. To give the user full permissions on the local computer, select Administrator (see Figure 6.1).
If a user needs to be able to log on locally to a computer and has an existing domain account, you can grant the user permission to log on locally by completing the following steps:
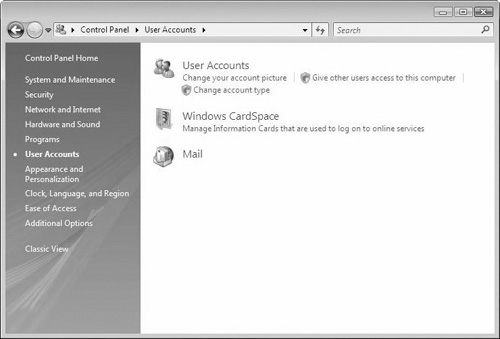
In the Control Panel, click User Accounts. On the User Accounts page, click the Give Other Users Access to This Computer link. This displays the User Accounts dialog box (see Figure 6.2). The User Accounts dialog box lists all configurable user accounts on the local computer by account type and with group membership details.
Click Add. This starts the Add New User Wizard.
You are creating a local computer account for a user with an existing domain account. Enter the user’s domain account name and domain in the fields provided.
Using the options provided, select the type of user account: Administrator, Standard User, or Other. An other account is created as a member of the specific group you choose. To give the user the permissions of a specific group, select Other, and then select the desired group.
Click Finish.
To change the account type for a local computer user, follow these steps:
In the Control Panel, click Add or Remove User Accounts under the User Accounts heading. This displays the Manage Accounts page.
Click the account you want to change and then click Change the Account Type.
On the Change the Account Type page, set the level of access for the user as either Standard User or Administrator and then click Change the Account Type.
In a domain, you can change the account type for a local computer user by completing the following steps:
In the Control Panel, click User Accounts. On the User Accounts page, click the Change the Account Type link. This displays the User Accounts dialog box.
On the Users tab, click the user account you want to work with and then click Properties.
In the Properties dialog box, select the Group Membership tab.
Select the type of account as Standard User or Administrator. Or select Other and then select the desired other group.
Click OK twice.
When the computer is not part of a domain (workgroup configuration), local users are created without passwords by default. Therefore, if you click the account name on the Welcome screen on an account that does not have a password, you will automatically be logged in.
To create a password for a local user account, follow these steps:
Log on as the user whose password you want to create. In the Control Panel, click Add or Remove User Accounts under the User Accounts heading, to display the Manage Accounts page.
All user accounts available on the machine are shown, and you must click the account you want to work with. To prevent possible data loss, this should be the same as the account under which you are currently logged on. Any account that has a current password is listed as password protected. Any account without this label doesn’t have a password.
Click Create a Password. Enter a password, and then confirm it. Afterward, enter a unique password hint. The password hint is a word or phrase that can be used to obtain the password if it is lost. This hint is visible to anyone who uses the computer.
Click Change Password.
In a workgroup, you can remove a user’s local account and effectively deny logon by completing these steps:
Log on as a user with local administrator privileges. In the Control Panel, click Add or Remove User Accounts under the User Accounts heading, to display the Manage Accounts page.
Click the account you want to remove.
Before deleting the account, you have the opportunity to save the contents of the user’s desktop and Documents folder to a folder on the current user’s desktop. To save the user’s documents, click Keep Files. To delete the files, click Delete Files.
Confirm the account deletion by clicking Delete Account. Keep in mind that in a domain, unless further restrictions apply with regard to logon workstations, a user might still be able to gain access to the workstation by logging on with a domain account.
To access the Users and Groups in the Computer Management console, follow these steps:
Click the Start button.
Click Control Panel.
Click System and Maintenance.
Click Administrative Tools.
Click Computer Management.
Double-click Local Users and Groups.
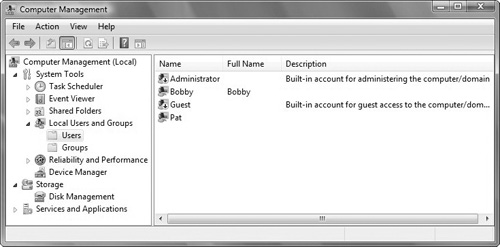
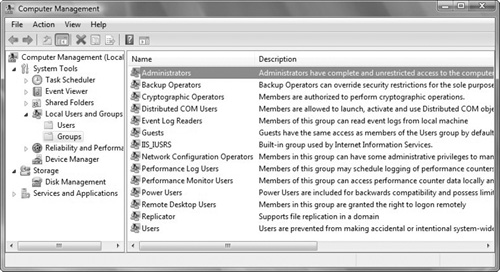
Select either Users or Groups (see Figures 6.3 and 6.4).
“Need to know” is a basic security concept that says information should be limited to only those individuals who require it. When planning for how you assign the rights and permissions to the network resources, follow these two main rules:
Give the rights and permissions for the user to do his job.
Don’t give any additional rights and permissions that a user does not need.
Although you want to keep these resources secure, you want to make sure that users can easily get what they need. For example, give users access to the necessary files, and give them only the permissions they need. If they need to read a document but don’t need to make changes to it, they need to have only the read permission. Apply the rule of least privilege; that is, give a person or group only the required amount of access and nothing more.
When you run earlier versions of Windows, including Windows XP, and you log on with an administrative account, every task that you execute and every process that runs in the account’s session run as an as administrator with elevated privileges. Because the elevated privileges give access to everything, it opens the possibility of human error, which can cause problems in Windows functionality or data loss and may allow malicious software to access any part of the computer. Unfortunately, most legacy applications (and even new applications) were not (or are not) designed to work without full administrator privileges.
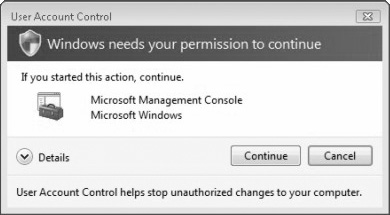
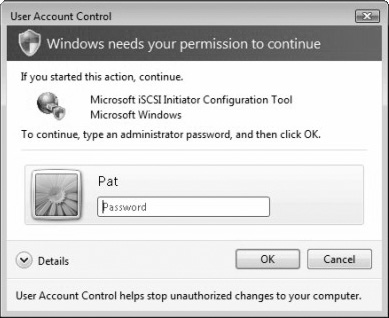
User Account Control (UAC) is a feature in Windows that can help prevent unauthorized changes to your computer. If you are logged on as an administrator, UAC asks you for permission (see Figure 6.5); if you are logged on as a standard user, UAC will ask you for an administrator password before performing actions that could potentially affect your computer’s operation or change settings that affect other users (see Figure 6.6). When you see a UAC message, read it carefully, and then make sure the name of the action or program that’s about to start is one that you intended to start.
To keep track of a user’s access, when a standard user logs in to Windows Vista, a token is created that contains only the most basic privileges assigned. When an administrator logs in, two separate tokens are assigned. The first token contains all privileges typically awarded to an administrator, and the second is a restricted token similar to what a standard user would receive. User applications, including the Windows shell, are then started with the restricted token, resulting in a reduced-privilege environment even under an administrator account. When an application requests elevation or is run as administrator, UAC prompts for confirmation and, if consent is given, starts the process using the unrestricted token.
The following additional privileges have been granted to standard user accounts so that users can carry out more tasks without requiring administrative permissions or rights:
View system clock and calendar
Change time zone
Install Wired Equivalent Privacy (WEP) to connect to secure wireless networks
Change display settings
Change power management settings
Install fonts
Add printers and other devices that have the required drivers installed on computer or are provided by an IT administrator
Create and configure a virtual private network connection
Download and install updates using UAC-compatible installer
In addition, extra services have been created to automate certain tasks. They include an ActiveX installer, which administrators can use to pre-approve sites from which users can install ActiveX controls, and a disk defragmenter, which runs as a scheduled process to optimize disk performance.
Tasks that will trigger a UAC prompt, if UAC is enabled, include the following:
Changes to files in %SystemRoot% or %ProgramFiles%
Installing and uninstalling applications
Installing device drivers
Installing ActiveX controls
Installing Windows Updates
Changing settings for Windows Firewall
Changing UAC settings
Configuring Windows Update
Adding/removing user accounts
Changing a user’s account type
Configuring parental controls
Running Task Scheduler
Restoring backed-up system files
Viewing/changing another user’s folders and files
When your permission or password is needed to complete a task, UAC will alert you with one of the following messages:
Windows needs your permission to continue. A Windows function or program that can affect other users of this computer needs your permission to start. Check the name of the action to ensure that it’s a function or program you want to run.
A program needs your permission to continue. A program that’s not part of Windows needs your permission to start. It has a valid digital signature indicating its name and its publisher, which helps to ensure that the program is what it claims to be. Make sure that this is a program that you intended to run.
An unidentified program wants access to your computer. An unidentified program is one that doesn’t have a valid digital signature from its publisher to ensure that the program is what it claims to be. This doesn’t necessarily indicate danger (because many older, legitimate programs lack signatures). However, use extra caution and only allow this program to run if you obtained it from a trusted source, such as the original CD or a publisher’s website.
This program has been blocked. This is a program that your administrator has specifically blocked from running on your computer. To run this program, you must contact your administrator and ask to have the program unblocked. Of course, it is recommended that you log on to your computer with a standard user account most of the time. With a standard user account, you can run standard business applications such as a word processor or spreadsheet, surf the Internet, or send e-mail. When you want to perform an administrative task, such as installing a new program or changing a setting that will affect other users, you don’t have to switch to an administrator account. Windows will prompt you for permission or an administrator password before performing the task.
To help protect your computer, you can create standard user accounts for all the users who share the computer. When someone who has a standard account tries to install software, Windows will ask for an administrator account’s password so that software can’t be installed without your knowledge and permission.
Some legacy applications will not run on Windows Vista because of some compatibility problems. Starting with Windows XP, Windows includes a Program Compatibility Wizard to configure Windows to run a program under an older Windows environment. For example, if you have a program that will run under only Windows 9x, you can configure Windows to run that program under the Windows 95 environment. This means that when Windows XP is running this application, it will pretend to be a Windows 95 system. The wizard also allows you to try different settings, such as switching the display to 256 colors and the screen resolution to 640x480 pixels.
To start the Program Compatibility Wizard, right-click the executable file that you are using to start the program, select Properties, and select the Compatibility tab. Enable the Run This Program in Compatibility Mode option and select the appropriate operating system environment.
An application that is made to be 100 percent compatible with Windows Vista is designed to work with UAC to keep the system secure by requesting privilege elevation as necessary. If you have an older application that requires administrative permissions to run, you can use the Application Compatibility tab to select the Run This Program as an Administrator option, which will allow the application to use the UAC system to request privilege escalation. This setting applies only to the account of the currently logged-on user, and no other users are affected by it. You can only configure this option if you have administrator privileges. If you need to have an application run as an administrator for all users, you can use the Show Settings for All Users option on the Application Compatibility tab.
UAC can be enabled or disabled for any individual user account. If you disable UAC for a user account, you lose the additional security protections UAC offers and put the computer at risk. To enable or disable UAC for a particular user account, follow these steps:
In the Control Panel, click User Accounts.
On the User Accounts page, click the Turn User Account Control On or Off link.
You can now enable or disable UAC for the currently logged-on user account. Disable UAC by clearing the Use User Account Control (UAC) to Help Protect Your Computer check box. Enable UAC by selecting the Use User Account Control (UAC) to Help Protect Your Computer check box.
Click OK.
When prompted to restart the computer, click Restart Now or Restart Later, as appropriate, for the changes to take effect.
Besides enabling or disabling UAC, you can control the behavior of the UAC by using local or group policies. Local policies are managed from each local computer, whereas group policies are managed as part of Active Directory. Table 6.1 shows the settings found in local and group policies.
Table 6.1. UAC Policy Settings Available in the Policy Editor Snap-In
Policy | Security Settings |
|---|---|
Admin Approval Mode for the Built-In Administrator Account | Enabled |
Disabled (Default) | |
Behavior of the Elevation Prompt for Administrators in Admin Approval Mode | Elevate without prompting Prompt for credentials Prompt for consent (Default) |
Behavior of the Elevation Prompt for Standard Users | Automatically deny elevation requests Prompt for credentials (Default) |
Detect Application Installations and Prompt for Elevation | Enabled (Default) |
Disabled | |
Only Elevate Executables That Are Signed and Validated | Enabled |
Disabled (Default) | |
Only Elevate UIAccess Applications That Are Installed in Secure Applications | Enabled (Default) |
Disabled | |
Run All Administrators in Admin Approval Mode | Enabled (Default) |
Disabled | |
Switch to the Secure Desktop When Prompting for Elevation | Enabled (Default) |
Disabled | |
Virtualize File and Registry Write Failures to Per-User Locations | Enabled (Default) |
Disabled |
To change the behavior of the UAC message for administrators in Admin Approval mode, follow these steps:
Click Start, All Programs, Accessories, Run. Then, enter secpol.msc in the Open box and click OK.
If UAC is currently configured in Admin Approval mode, the UAC message will appear. Click Continue.
From the Local Security Policy tree, click Local Policies, and then double-click Security Options.
Scroll down and double-click User Account Control: Behavior of the Elevation Prompt for Administrators in Admin Approval Mode.
From the drop-down menu, select one of the following settings:
Elevate without Prompting. In this case, applications that have been marked as administrator applications, and applications detected as setup applications, will automatically run with the full administrator access token. All other applications will automatically run with the standard user token.
Prompt for Credentials. In this case, to give consent for an application to run with the full administrator access token, the user must enter administrator credentials. This setting supports compliance with Common Criteria or corporate policies.
Prompt for Consent. This is the default setting.
Click Apply.
To change the UAC message behavior for standard users, follow these steps:
Click Start, All Programs, Accessories, Run. Then, enter secpol.msc in the Open text box and click OK.
If UAC is currently configured to prompt for administrator credentials, the UAC message will appear. Click Continue.
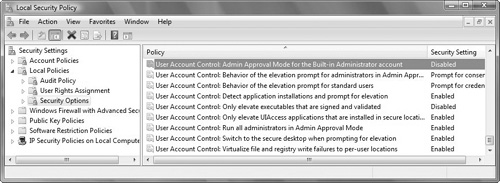
From the Local Security Policy tree, click Local Policies, and then double-click Security Options (see Figure 6.7).
Scroll down and double-click User Account Control: Behavior of the Elevation Prompt for Standard Users.
From the drop-down menu, select one of the following settings:
Automatically Deny Elevation Requests. In this case, administrator applications will not be able to run. The user should see an error message from the application that indicates a policy has prevented the application from running.
Prompt for Credentials. This is the default setting. In this case, for an application to run with the full administrator access token, the user must enter administrator credentials.
Click Apply.
Answers D and E are correct. Installing a device driver and installing an application require administrative permission. Therefore, UAC will prompt you to make sure it is something that you want done. Answers A, B, and C are incorrect because standard users can do these. | |
Answer B is correct. UAC is used to prevent unauthorized changes to the computer. Answer A is incorrect because the Computer Management console is used to manage the computer, including managing volumes, using the Event Viewer, and managing local users and groups. Answer C is incorrect because the Windows Firewall will help block unwanted packets from getting to your computer. Answer D is incorrect because the Event Viewer is used to look at warning and error messages and the security logs. | |
Answer C is correct. The UAC will ask for permission to continue when you are performing tasks that require you to be an administrator, to make sure that they are tasks that you really want completed. Answer A is incorrect because the Windows Firewall prevents unwanted packets from the outside. Answer B is incorrect because NT File System (NTFS) permissions help protect the files on an NTFS volume. Answer D is incorrect because the Internet Sharing console does not exist. | |
Answer D is correct. To configure legacy applications to run under Windows Vista, you can right-click an executable and open the Properties dialog box. From there, you can specify what environment to run under and if necessary specify whether the application can run under an administrator account. | |
Answer D is correct. The message is generated by the User Account Control, which you can configure by using local or group policies. Answer A is incorrect because the Power Users group is left behind from Windows 2000 and XP for backward compatibility. Answer B is incorrect because all standard user accounts should already be a member of the Users group. Answer C is incorrect because turning off the firewall would not get rid of the message. | |
Answer D is correct. You need to edit the Local Security Policy to not prompt during installs by disabling the Detect Application Installations and Prompt for Elevation Setting. This will allow applications to be installed without prompting for the administrative credentials. Answer A is incorrect because you don’t want to give administrative permission. Answer B is incorrect because turning off UAC will stop protecting the system. Answer C is also incorrect because parental controls cannot be used when a computer is connected to a domain. | |
Answer A is correct. Some users are not having the problem, whereas others are. Therefore, you need to focus on what is different from those accounts; in this case, you need to add those users to the administrator group. Answer B is incorrect because they would not get logged on to the system with the wrong username and password. Answer C is incorrect because all users would be affected if the application runs as a standard user. Answer D is incorrect because the Application service does not exist. | |
Answers A and B are correct. The Control Panel user accounts and the Computer Management console, specifically under Users and Groups, are used to add and manage user accounts. Answer C is incorrect because Active Directory Users and Computers console is used to manage domain user accounts. Answer D is incorrect because the Users and Groups Administrator console does not exist. | |
Answer C is correct. A domain is a logical unit group of computers and network that define a security boundary and which use one database known as Active Directory to store relevant security information. Answer A is incorrect because the Active Directory is the directory service. Answer B is incorrect because a workgroup is only used to easily access other computers within the workgroup. Each computer contains its own database of user accounts and does not provide single sign-on. Answer D is incorrect because the domain controller is used to provide Active Directory. | |
Answer A and B is correct. For new installations, the administrator and guest account is disabled by default. Answers C and D are incorrect because these accounts are not found on a Windows Vista machine unless they are created. |
Stanek, William R., Introducing Microsoft Windows Vista (Redmond, Washington: Microsoft Press, 2006).
Tulloch, Mitch, Tony Northrup, Jerry Honeycutt, Ed Wilson, Ralph Ramos, and the Windows Vista Team, Windows Vista Resource Kit (Pro. Resource Kit) (Redmond, Washington: Microsoft Press, 2007).
For more information about UAC, visit http://technet.microsoft.com/en-us/windowsvista/aa905108.aspx.